Hello, this is a very interesting and relevant topic for successful work.
To get data from your pos terminal, you can use the following methods:
1. Download a free topical virus from a virus storage site and infect your pos terminal. Configure and study the transfer of customer data from your device to a computer or mobile phone. Sites where you can download Trojan viruses are listed in the next topic.
2. Buy a working vSkimmer and install it in your post terminal. Set up data transfer to your device.
Some additional information:
POS terminal infection Infection of POS terminals (Point Of Sale - point of sale), hardware and software systems for trading or automated workstations of a cashier is a cybercriminal activity aimed at stealing bank card data and further withdrawing funds.
Classification of methods of infecting POS terminals
Malicious programs for POS terminals can be distinguished by the volume of tasks being solved and the nature of the information stolen.
RAM scrapers
Writing the contents of RAM is a mandatory part of almost all programs for infecting POS terminals, since during a transaction all data from a bank card is processed in RAM. Basic RAM scrapers record information from memory and send it to the attacker's server for further offline analysis, while more advanced versions are able to independently extract data from the magnetic stripes of bank cards from the general stream.
RAM scraper and keylogger
Such programs, in addition to analyzing the RAM, also record all keystrokes, fixing PIN codes and other entered information. Since all transactions are carried out via a computer or mobile device, the development of malicious code often does not take place from scratch: cybercriminals modify already created Trojans and viruses by adding RAM scrapers to them to steal data from bank cards. Accordingly, such instances may contain rootkits to hide traces of activity or backdoors for remote access, and steal other information. In particular, the well-known malicious agent vSkimmer collects information about the operating system used, users, and GUID.
Object of influence
When it comes to infecting POS terminals, malware is not injected into the card reader, but into the computer or mobile device that controls it. Although all transmitted transaction data is encrypted, the information from the magnetic stripe of the card arrives in unencrypted form and is already encrypted on the computer.
Evolution of POS malware
This vulnerability is used by criminals. The programs for scanning the RAM, embedded in the system, constantly analyze the contents of the latter and read the card data. The number, expiration date, owner's name, PIN-code, CVV and CVC recorded on the magnetic stripe are sufficient to make a clone with which you can withdraw money and pay for purchases. In addition, this data allows you to pay for online orders where the presentation of physical cards is not required. Chip cards are better protected: they encrypt payment information with a chip before being sent to the POS terminal, and intercepting it is useless. However, the magnetic stripe is also there, and its data can still be copied. In this case, the criminal will not be able to withdraw money from the ATM (there is no chip), but he will be able to use the clone as a means of payment if the reader in the store works only with a strip. However, in this case, traces remain for law enforcement agencies, and therefore criminals prefer to copy cards without chips.
Sources of threat
A POS terminal can be infected with malware in several ways: via the Internet using exploits, via a USB interface to which an infected medium is connected, by replacing a secure POS terminal with an infected one, via spam with a Trojan downloader. A program that steals passwords can be entered into the system on purpose. Bank data is of great value, and an unscrupulous or offended employee, having agreed with a cybercriminal, will easily introduce a malicious agent into the system. The third major source of threat is companies that install and remotely service POS terminals. In theory, in such firms, the security system should be organized at the highest level, but in practice this is not always true. There are known cases when, having cracked the password of the remote administrator of POS terminals, attackers at once gained access to the banking data of millions of users.
Threat analysis
For a simple bank card holder, the main danger of POS-terminals being infected is that he is not able to prevent it. A person uses the card, assuming normal operation of the system, but if it performs unauthorized operations, then the user will not be able to find out about it. To reduce the risk, you can abandon the card, which contains only a magnetic stripe, in favor of a more secure chip one and regularly monitor the status of your accounts, track all transactions in order to immediately take action if any suspicions arise. If we talk about the owners of POS terminals, then from their point of view there are no direct losses: after all, the data is stolen not from the company, but from the cardholders. However, reputational losses and customer outflow can result in millions of damage, and therefore any company must take the necessary measures to protect the banking data of its customers.
All POS computers must be equipped with effective antivirus software, and the system software must be up to date. The list of installed programs itself should be limited, and the computer should not be used for other tasks not related to transactions. The same applies to the owners of mobile POS terminals. For such purposes, it is better to purchase a second smartphone, using it only to transfer money, and communicate, take selfies and other photos, launch media files - on another device. Access to POS-terminals, authorization on them should be allowed only to those employees who directly work with them. Within the system, a clear delineation of rights is required with the prohibition to install or modify computer software for unprivileged accounts. Each user must have their own complex password.
Finally, in addition to working with the terminal, cashiers and other tellers should be trained in information security rules. As already mentioned, the methods of distributing malicious programs for trading devices do not differ from the methods of infecting other computers, and in many cases the penetration of Trojan horses and viruses is due to the carelessness and frivolity of users; compliance with cyber hygiene greatly complicates the activities of intruders.
Trojan.MWZLesson - a Trojan for POS terminals
For many years, POS terminals have remained a tasty morsel for virus writers, since they are used by numerous merchants around the world to make payments using bank plastic cards. Doctor Web's specialists examined another Trojan capable of infecting payment terminals, which turned out to be a modification of another malicious program well known to our virus analysts.
A POS Trojan added to the Dr.Web virus databases under the name
Trojan.MWZLesson, after its launch, registers itself in the branch of the system registry responsible for starting applications. Its architecture includes a module that scans the RAM of the infected device for the presence of bank card tracks in it. The cybercriminals borrowed this code from another malicious program designed to infect POS terminals known as Trojan.PWS.Dexter. The Trojan transfers the detected tracks and other intercepted data to the command and control server.
Trojan.MWZLesson can intercept GET and POST requests sent from an infected machine by Mozilla Firefox, Google Chrome or Microsoft Internet Explorer - the Trojan duplicates these requests to the command and control server belonging to the attackers. In addition, this malware can execute the following commands:
- CMD - transfers the received directive to the CMD command interpreter;
- LOADER - downloads and runs the file (dll - using the regsrv utility, vbs - using the wscript utility, exe - the direct launch is performed);
- UPDATE - update command;
- rate - sets the time interval of communication sessions with the management server;
- FIND - search for documents by mask;
- DDOS - start a DDoS attack using the http flood method.
Trojan.MWZLesson exchanges data with the control center via the HTTP protocol, while the packets that the Trojan sends to the remote server are not encrypted, but the malware uses a special cookie parameter in them, in the absence of which the C&C server ignores requests from the Trojan.
While studying the internal architecture of
Trojan.MWZLesson, virus analysts from Doctor Web came to the conclusion that they were familiar with this Trojan, since they had encountered part of its code earlier in another malicious program. It turned out to be
BackDoor.Neutrino.50, a truncated and shortened version of which, in fact, is
Trojan.MWZLesson.
BackDoor.Neutrino.50 is a multifunctional backdoor that uses exploits for the CVE-2012-0158 vulnerability during its distribution. Cases of downloading this malicious program from various sites hacked by cybercriminals have been recorded. When
BackDoor.Neutrino.50 islaunched, itchecks for the presence of virtual machines in its environment, if any, the Trojan displays an error message "An unknown error occurred. Error - (0x [random number])", after which
BackDoor.Neutrino.50 deletes itself from the system.
In addition to the functions of a Trojan for POS terminals, this backdoor has the ability to steal information from Microsoft's mail client, as well as credentials for accessing resources via FTP using a number of popular ftp clients. In addition to directives typical for
Trojan.MWZLesson, the
BackDoor.Neutrino.50 Trojan can execute other commands, in particular, it is capable of carrying out several types of DDoS attacks, deleting some other malicious programs running on the infected machine, and can also try to infect computers. available on the local network.
The signatures of these Trojans have been added to the Dr.Web virus databases, so they pose no threat to users of our anti-virus products.
Experts have identified several new malware samples for POS terminals
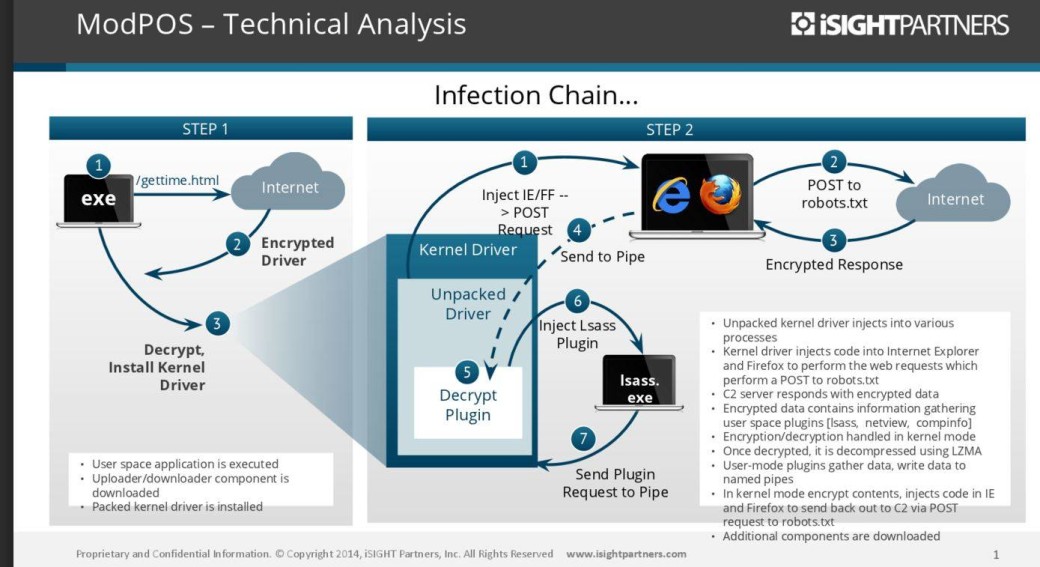
The pre-holiday season has come, the number of purchases has increased, and with it the risk of running into an unsafe PoS terminal has grown. Experts report the detection of several samples of malware that infects payment device systems. Experts generally called the ModPOS virus one of the most complex in its class.
The specialists of iSight Partners, who discovered ModPOS, called the malware "PoS malware on steroids" and one of the most difficult representatives of the "genre". And this is the opinion of a company that has been analyzing this kind of malware for over eight years! According to iSight Partners, in a massive campaign aimed at undisclosed major US retailers, ModPOS stole several million dollars from credit and debit cards.
The malware has remained out of sight of virus analysts since 2013. It is almost impossible to find references to this malware even on hacker forums.
It took the iSight Partners team more than three weeks to reverse engineer the program, and only after that they were able to get to the three ModPOS kernel modules. For comparison, recently it took their colleagues about half an hour to "open" the Cherry Picker PoS malware . ISight Partners writes that "an incredibly talented author did a great job" creating ModPOS. The company believes that the author of the virus is a resident of Eastern Europe.
The experts also report that it took "a lot of time and money" to develop each of the ModPOS kernel modules. Each of the modules behaves like a rootkit, which further complicates their analysis and reverse engineering.
To communicate with C&C servers, the malware uses 128- and 256-bit encryption and requests a unique key for each client. Because of this, it is almost impossible to understand what data was stolen. Other PoS malware typically transmits information in clear text without resorting to encryption.
A less complex, but very insidious representative of the PoS malware family was discovered by specialists from InfoArmor. The virus, dubbed Pro PoS, weighs only 76 KB. Oddly enough, this volume was enough to accommodate the functions of a rootkit and outwit virus analysts. The virus is also supposedly created by East European hackers (see screenshot below).
Pro PoS uses a polymorphic engine, that is, each malware build has a new signature. This avoids detection and overcomes security systems. InfoArmor experts warn that at the moment Pro PoS is actively used to attack major Canadian and American retail chains.
Pro PoS received its last update on November 27, 2015, and its price increased at the same time. Today, a six-month malware license costs $ 2,600.
New threats for old PoS terminals
It would seem that not so long ago the world learned about threats specially designed for unusual computers filled with real money - ATMs. Several years have passed, and the ranks of "unusual computers" have replenished with new devices for trading and accepting payment cards - PoS terminals (point of sales, point of sale).
2013 was marked by an incident that affected US residents: the data of more than 40 million bank cards and information on more than 70 million customers of a large retail chain Target fell into the hands of cybercriminals. During the investigation, it turned out that the cause of the incident was not the compromise of the payment processing system or the company's servers, but the infected cash registers and PoS terminals. Malicious software installed on them by cybercriminals intercepted payment data in the device's RAM in plain text. In 2014, the situation with terminals was repeated in another retail chain, Home Depot, and led to data leaks from 56 million cards.
These incidents have shown that cybercriminals are not only closely monitoring the trends in technology and devices for receiving and processing payments, but also continuously developing specialized malicious software to steal valuable financial data.
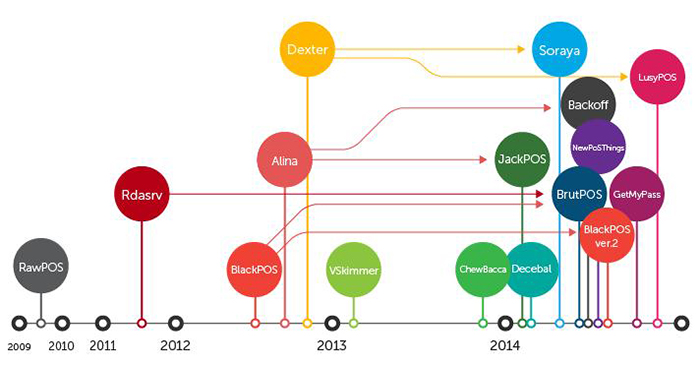
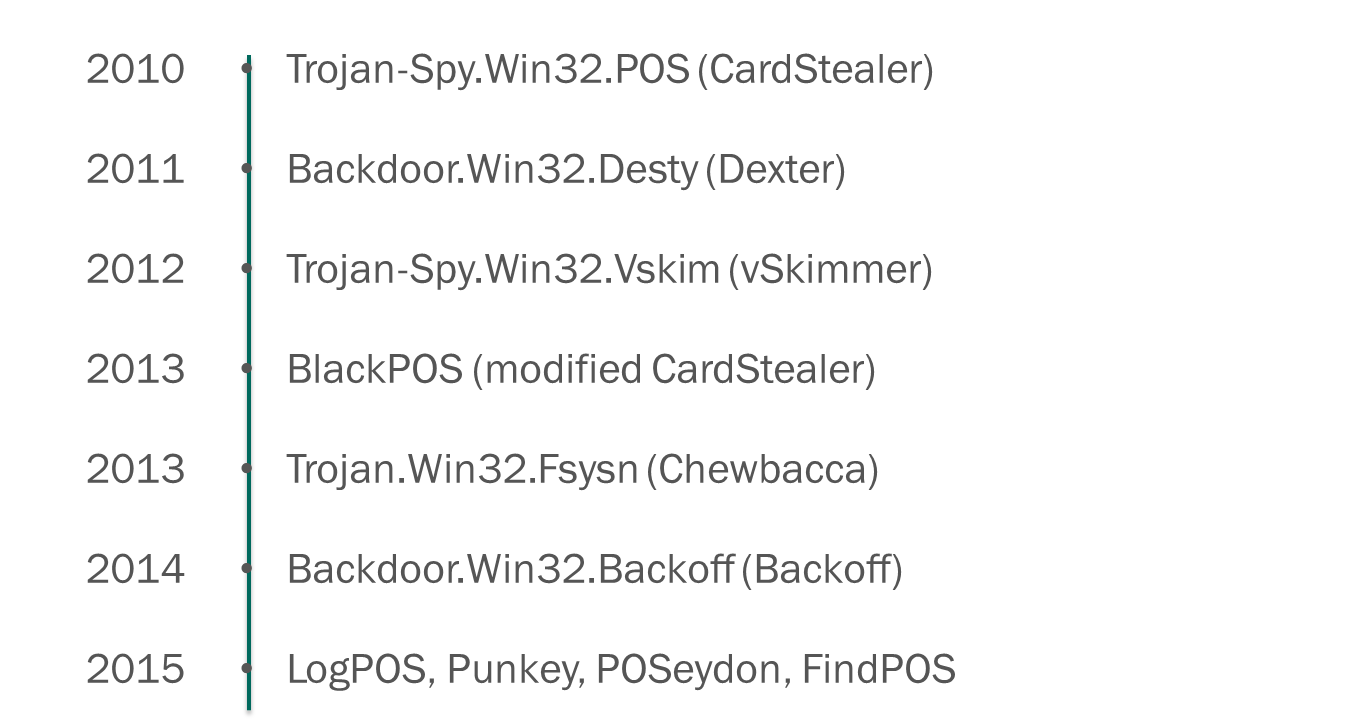
Before large-scale retail hacks, the problem of malware for PoS terminals was not so much ignored as it simply did not attract public and media attention, despite the fact that PoS malware has attacked various enterprises since at least 2010. For example, back in 2010, the world learned about
Trojan-Spy.Win32.POS (also known as CardStealer), which looked for payment card details on an infected workstation and transmitted the found information to the cybercriminals' server. Since then, antivirus experts have discovered more and more instances of malware designed to steal payment data from PoS terminals every year.
Timeline of threat detection for PoS terminals (source: Kaspersky Lab)
Currently, the infection of PoS terminals has already gone beyond pinpoint attacks, and cybercriminals have received a new foothold for the implementation of threats, which allows them to get closest to other people's money.
General purpose OS against specific malware
The life of attackers is somewhat simplified by the fact that PoS devices are actually ordinary computers that can also be used (and are sometimes used, especially in small businesses) for "general purposes", including surfing the Net and checking email. This means that in some cases criminals can gain remote access to such devices.
The
Dexter malware, discovered in 2012, stole bank card details by attacking POS terminals running Windows. It infiltrated the iexplore.exe system process, read the RAM and looked for payment data sufficient to make a fake plastic card (owner's name, account number, expiration date and card number, including the issuer code, class and type of card, and so on), then sent the collected information to a remote server controlled by the attackers.
Examples of commands that Dexter received from the command and control server
During its existence, Dexter has managed to hit hundreds of PoS systems in well-known retail chains, hotels, restaurants, as well as in private parking lots. And as you might guess, most of the victims' workstations were running the Windows XP operating system.
Another notorious example is the threat dubbed
Backoff. This PoS Trojan is designed to steal card information from payment terminals. Like Dexter, this malware reads the RAM of a PoS terminal to obtain payment card details. In addition, some versions of Backoff contained a component for intercepting keyboard input (keylogger), presumably in case it ends up not on a PoS terminal, but on a regular workstation, which can also be used for payments (which means that the user will enter valuable information from the keyboard).
Points of sale in "non-trade" places
Currently, PoS devices can wait for their users not only in retail chains, supermarkets or hotels. Parks and streets are full of parking payment terminals for all kinds of vehicles and cozy "booths" for fast recharging of a mobile device. Airports and train stations offer help information and pay for tickets through various devices. In cinemas, there are terminals for buying and booking tickets for film shows. In clinics and government agencies, visitors are greeted with electronic queues and receipt printing devices. In some places, even toilets are equipped with payment terminals!
At the same time, not all of these devices are sufficiently well protected. For example, in the summer of 2014, experts from an antivirus company discovered configuration flaws in parking terminals that allowed them to compromise devices and, as a result, user data (including payment).
The application for parking meters operating on the basis of the operating system of the Windows family allows the user to register and get help information about the location of the parking meter and other bicycle parking lots. The display of all this, as well as bars, cafes and other objects, is implemented using the Google widget. The user does not have the ability to minimize the full-screen application and go beyond it, however, it is precisely in it that lies the configuration flaw that allows you to compromise the device: in the lower right corner of the widget there are links "Report a bug", "Privacy" and "Terms of use", after clicking on which will launch the Internet Explorer browser.
An example of exploiting vulnerabilities in a parking meter application
The use cases for such configuration flaws depend only on the imagination of the attacker. For example, an attacker can extract an administrator password stored in clear text in memory. You can also get a snapshot of the bike parking app's memory. It may then be possible to extract the personal information of its users from it: name, e-mail address and phone number - such a database of verified addresses and phone numbers will be of particular value on the black market of cybercriminals. An attacker can also install a keylogger that intercepts all the entered data and sends it to a remote server, or, by adding fields for entering additional data, implement an attack scenario that will result in the receipt of even more personal data.
Default deny
Financial institutions and organizations operating PoS terminals should pay more attention to protecting their devices, and not only the security of their hardware, but also the security of their operating systems, as well as the entire network information infrastructure. This will be helped by means of protection that have long been used in corporate networks, and specialized solutions for ensuring the security of embedded systems.
Point of sale equipment is no less valuable to the owner than a lone ATM in a shopping center for the owner bank. And if the owners of ATMs with each new incident understand better that it is necessary to protect devices, then many owners of PoS terminals still pay for their carelessness. Deny by default and full disk encryption are not innovative methods, but they are still effective at protecting the iron bag of money.
Analyzing malware created for POS terminals
The malware authors do not stand still, but constantly invent new schemes to replenish their wallets. In this article, we will look at a new trend in the field of virus writing - malware for POS terminals.
What is a POS terminal?
POS is translated as point of sale, that is, the place where the client pays for goods or services. POS terminals represent a wide class of devices, and its implementation depends only on the imagination of manufacturers. For example, there are POS terminals based on the iPad. So far, virus writers for POS terminals have mastered only one platform - Windows, so this article will focus on malware specifically for that platform.
Why are POS terminals interesting to cybercriminals? The answer is simple - acquiring, that is, payment by credit card. Despite the fact that the data security standards of the payment card industry prohibit the storage of complete card data after a successful transaction, virus writers have still found a way to get their hands on it. The fact is that in order to authorize the purchase, the POS terminal must somehow contact the processing center, and all this time the card data is in the memory of the POS terminal. This is what the attackers decided to take advantage of. Once again, I repeat that there are a lot of POS terminal implementations and this attack will not be successful on all devices.
Attackers are interested in track1 and track2 - data recorded on magnetic tape. This data contains the owner's name, card code, expiration date and other intimate information. Having track1 / track2 is enough to make a clone of a plastic card.
Dexter
In December 2012, the Israeli company Seculert announced a new malware it had detected on hundreds of POS systems around the world. One of the interesting details is that over 30% of server versions of Windows were found among the infected systems. The company provides a cloud service that helps identify malicious activity on an enterprise's network by analyzing log files generated by various software or hardware proxies (Blue Coat, Squid, and others). Unsurprisingly, she was the first to spot this threat .
Consider the files whose hashes were published by Seculert. The files are packed with a fairly popular cryptor, which uses the XPXAXCXK signature during the decompression process. This cryptor is widely used to hide from signature detection. And therefore, it is also well studied, a static unpacker has even been written for it .
However, to unpack it manually, it is enough to set a breakpoint on the VirtualAlloc WinAPI functions and trace the code until the unpacked PE file is found in one of the allocated memory regions.
After removing the cryptor, we find that three of the four files are completely identical. The size of the first variant is only 24 KB, the file was compiled using Visual Studio, the compilation date is August 30, 2012, according to the data from the PE header. The second, more recent version was compiled on October 16, 2012, and its size is 44 KB.
Now closer to the functionality itself. The first thing Dexter does is try to inject its body and create a thread in the Internet Explorer process. Next, the malware copies itself to% APPDATA% using a random name, and is also registered in the registry key for startup. Dexter launches its own threads, which are responsible for keeping the autorun key in the registry, searching for data and injecting it into the IE process. Finally, control is passed to the code that establishes the connection and sends the collected data to the server.
To communicate with the server, Dexter uses the HTTP protocol, data is transmitted using a POST request. Before sending data to the server, Dexter encrypts it using the XOR operation and base64 algorithm. The following information is sent to the server:
- page - bot identifier;
- ump - collected track data;
- unm - username;
- cnm - computer name;
- query - operating system version;
- spec - "bitness" of the operating system (32 vs 64);
- opt is the time elapsed from the previous user input of information. Retrieved using the GetLastInputInfo WinAPI function;
- view - a list of all processes running on the infected system;
- var is a unique string for each build;
- val is a random string, used as a decryption key.
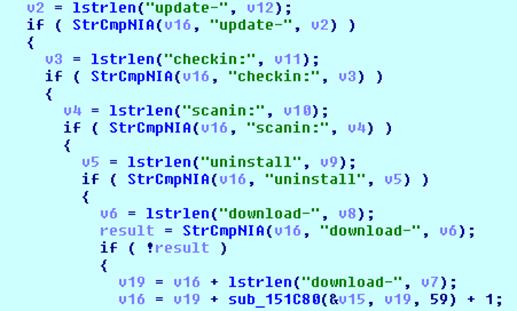
The server sends a response to this POST request, the header of which contains a cookie with a command to execute for the client. The command is encrypted with the same algorithm as the request. An early version of Dexter only supports two commands:
- checkin - setting the delay period between requests to the server;
- scanin - sets the delay period between attempts to find track data in memory. In a later version, three more were added to these two commands:
- update - update from the specified URL;
- uninstall - remove yourself from the infected computer;
- download - download and launch a file from the URL specified in the command.
In general, Dexter has a classic set of functionality for a Trojan. The only thing that makes it unique among many similar malware is its focus on stealing plastic card data. The search for track2 goes in the following sequence:
- A list of processes is compiled. System and 64-bit processes are excluded from the list.
- The WinAPI function VirtualQueryEx checks the availability of memory regions.
- An attempt is made to read memory from available regions using the ReadProcessMemory WinAPI function.
- The read buffer is searched for the = symbol, and it is also checked that there is a string of a certain length, consisting of digits, to the right and left of the symbol. The ability to store a string in both ANSI and Unicode is taken into account.
- The numbers to the left of the = symbol are checked using the Luna algorithm. If the check is passed, the data is copied into a special buffer, from where it will later be sent to the server.
- After a certain period, all steps are repeated, this period can be set by a command from the server.
A later version of Dexter searches for track1 using a similar algorithm.
vSkimmer
This malware is considered to be a follower of Dexter. VSkimmer added a simple anti-debug, executed using standard WinAPI functions, and writing its own process to trusted Windows firewall processes. VSkimmer searches for processes using approximately the same algorithm as Dexter, but the author did not reinvent the wheel and used regular expressions to search.
However, among other things, vSkimmer also has interesting functionality. Obviously, the main difficulty for cybercriminals is to infect the computer that is used in the POS terminal. From such a computer, they usually do not go to sites, and sometimes there is no Internet at all on it. In this case, you can infect your computer with the help of an insider in your organization. This is the mode of operation that was added to vSkimmer. If the infected computer does not have an Internet connection, the malware writes all the accumulated data to a special file. When a USB drive with a volume label KARTOXA007 is connected to the computer, vSkimmer copies all the collected information to the drive into the dmpz.log file.
The author of this malware has a good sense of humor - apparently, this can explain that the PCICompliant / 3.33 value is used as the User-Agent when connecting to the server. PCI Compliant is the name given to a terminal that fully complies with the data security standards of the payment card industry.
Are the ideas of these viruses so new?
Despite all the noise raised in the media and the Internet in early 2013, a similar attack pattern was demonstrated in 2010 by Trustwave employees at DEF CON 18. In their report "Malware Freakshow 2", Trustwave employees demonstrated malware that can extract applications from memory track1 / track2. Presentation slides are available
here.
Conclusion
Despite their primitiveness, the considered malicious programs successfully cope with the tasks assigned to them. However, in the future we may witness the use of more sophisticated software aimed at stealing data from POS terminals.
History of success
In May 2011, an official charge was brought against four Romanian citizens of stealing data on plastic cards of US residents using POS terminals. According to the indictment, from 2008 to May 2011, Romanian attackers infiltrated more than 150 POS terminals of one of the fast food restaurant chains, as well as POS terminals of other companies. In total, hackers managed to steal more than 80 thousand data on plastic cards. In order to install their malware on POS terminals, hackers brute-force passwords for pcAnywhere, a program used to remotely control a computer.