Tomcat
Professional
- Messages
- 2,695
- Reaction score
- 1,058
- Points
- 113
A new phishing kit allows you to steal your account unnoticed using modern methods.
Resecurity specialists have discovered a new V3B phishing kit that targets customers of European banks.
According to a report from Resecurity, a group of cybercriminals are selling the V3B phishing kit via Telegram. One of the group's members, known under the pseudonym "Vssrtje", started the campaign in March 2023. The cost of the kit varies from $130 to $450 per month.
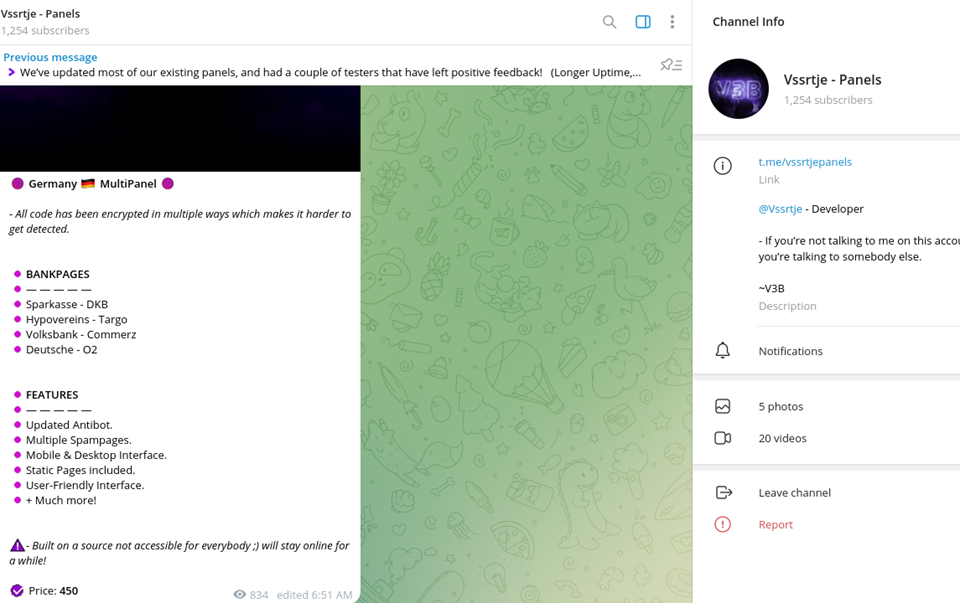
So far, the V3B suite has attracted more than 1,255 experienced cybercriminals involved in fraud, including social engineering, SIM swapping schemes, and banking fraud. The V3B phishing kit targets more than 54 financial institutions in the European Union.
The V3B phishing kit is capable of intercepting sensitive information, including credentials and OTP codes (one-time passwords), using social engineering techniques. The kit consists of two components: a Scenario-Based Credential Interception System (V3B) and authorization pages for online banking.
The kit is based on a custom CMS and includes templates in several languages (Finnish, French, Italian, Polish, and German). V3B simulates authentication and verification processes in online banking and e-commerce systems in the EU. V3B also has advanced features such as updatable tokens, anti-bot measures, mobile and desktop interfaces, live chat, and OTP/TAN/2FA support.
Phishing code is also obfuscated (using JavaScript) in several ways to avoid detection by anti-phishing systems and search engines, and to protect the source code from signature analysis.
Through real-time interaction with victims, the V3B phishing kit allows fraudsters to gain unauthorized access or facilitate fraudulent transactions. The phishing kit uses the Telegram API as a communication channel to transmit intercepted data to the fraudster, warning him about the successful completion of the attack.
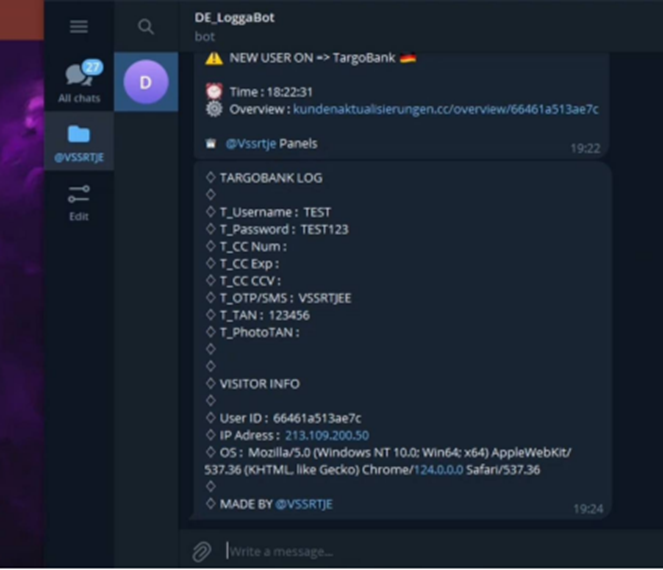
One of the most notable features is a trigger for generating a QR code request. Many popular services, such as WhatsApp, Discord, and TikTok, offer a QR code login form, making them vulnerable to this type of attack. V3B uses a browser extension to get QR codes from the service's website, and then redirects the victim to a phishing site. If the victim scans the code, the attacker gains access to the account.
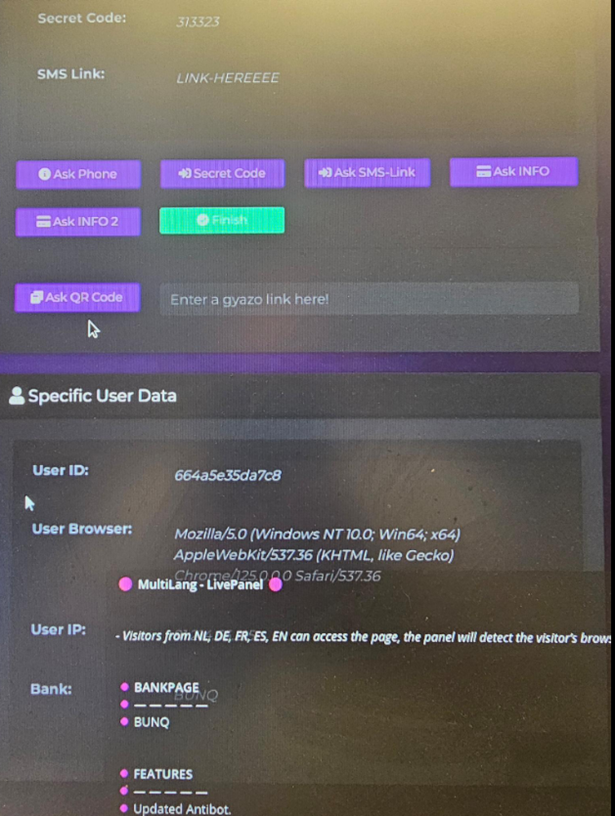
Of course, the technologies used by banks to authenticate customers may vary. However, the fact that fraudsters have started implementing support for alternative verification mechanisms, rather than relying solely on traditional SMS-based methods, may confirm the challenges that fraud prevention teams will face when dealing with account hijacking of both physical and legal clients.
To protect yourself from V3B phishing kit attacks, carefully check the email sender's address, do not enter personal data on unfamiliar sites, and enable multi-factor authentication (MFA) for additional security.
Resecurity specialists have discovered a new V3B phishing kit that targets customers of European banks.
According to a report from Resecurity, a group of cybercriminals are selling the V3B phishing kit via Telegram. One of the group's members, known under the pseudonym "Vssrtje", started the campaign in March 2023. The cost of the kit varies from $130 to $450 per month.

So far, the V3B suite has attracted more than 1,255 experienced cybercriminals involved in fraud, including social engineering, SIM swapping schemes, and banking fraud. The V3B phishing kit targets more than 54 financial institutions in the European Union.
The V3B phishing kit is capable of intercepting sensitive information, including credentials and OTP codes (one-time passwords), using social engineering techniques. The kit consists of two components: a Scenario-Based Credential Interception System (V3B) and authorization pages for online banking.
The kit is based on a custom CMS and includes templates in several languages (Finnish, French, Italian, Polish, and German). V3B simulates authentication and verification processes in online banking and e-commerce systems in the EU. V3B also has advanced features such as updatable tokens, anti-bot measures, mobile and desktop interfaces, live chat, and OTP/TAN/2FA support.
Phishing code is also obfuscated (using JavaScript) in several ways to avoid detection by anti-phishing systems and search engines, and to protect the source code from signature analysis.
Through real-time interaction with victims, the V3B phishing kit allows fraudsters to gain unauthorized access or facilitate fraudulent transactions. The phishing kit uses the Telegram API as a communication channel to transmit intercepted data to the fraudster, warning him about the successful completion of the attack.

One of the most notable features is a trigger for generating a QR code request. Many popular services, such as WhatsApp, Discord, and TikTok, offer a QR code login form, making them vulnerable to this type of attack. V3B uses a browser extension to get QR codes from the service's website, and then redirects the victim to a phishing site. If the victim scans the code, the attacker gains access to the account.

Of course, the technologies used by banks to authenticate customers may vary. However, the fact that fraudsters have started implementing support for alternative verification mechanisms, rather than relying solely on traditional SMS-based methods, may confirm the challenges that fraud prevention teams will face when dealing with account hijacking of both physical and legal clients.
To protect yourself from V3B phishing kit attacks, carefully check the email sender's address, do not enter personal data on unfamiliar sites, and enable multi-factor authentication (MFA) for additional security.
