Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,488
- Points
- 113
A Trojan program (Trojan) is a malicious agent, the main difference of which from a classic virus is its propagation method: it usually penetrates the system under the guise of a regular, legitimate program, which is the reason for the tradition of calling it a "Trojan horse". After penetration, it is capable of many things: it can collect information about the device and its owner, steal data stored on a computer, block access to user information, disable the operating system, etc.
Trojan classification
One of the classification options is to divide into the following types:
1. RAT (Remote Access / Administration Tool)
2. Ransomware
3. Cryptographers (Ciphers)
4. Boot loaders (Downloaders)
5. Deactivators of protection systems
6. Bankers
7. DDoS Trojans
RAT is a spyware trojan. Once installed on the system, it provides an attacker with a wide range of options: capturing video from the victim's screen, accessing the file system, recording video from a webcam and sound from a microphone, stealing browser identification files (cookies), installing other programs, etc. Examples include DarkComet or AndroRAT.
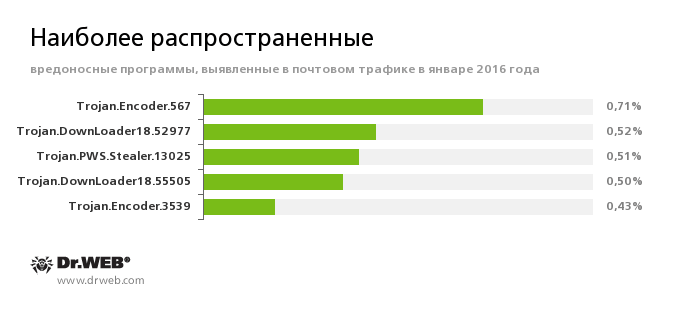
Ransomware is a form of malicious objects that block access to a system or data, threaten the user with deleting files from a computer or spreading the victim's personal data on the Internet, and demanding a ransom payment to avoid such negative consequences. An example of this behavior is the WinLock family.
Cryptographers (Ciphers) is an advanced form of ransomware that uses cryptography as a means to block access. Whereas in the case of an ordinary "winlocker" it was possible to simply remove the malicious program and thereby regain access to information, here the destruction of the ransomware itself does nothing - the encrypted files remain inaccessible. However, in some cases, antivirus software can recover data. An example of a ransomware is CryZip.
Boot loaders (Downloaders) are a type of malicious agent designed to download other programs or files from the Internet. An example is Nemucode. Protection System Deactivators are Trojans that remove or stop antiviruses, firewalls, and other security tools.
Bankers are a type of Trojan horse that specializes in stealing bank data (account number, PIN, CVV, etc.).
DDoS Trojans (bots) are malicious programs that are used by hackers to form a botnet in order to carry out denial of service attacks.
All Trojans are loaded into the system under the guise of legitimate software. They can be specially uploaded by cybercriminals to cloud data storage or file-sharing resources. Also, Trojans can enter the system by installing them by an insider during physical contact with a computer. In addition, they are often disseminated through spam mailings.
Target of Trojans
Most often, the target of such a malicious agent is an ordinary PC and its user, but incidents are also possible in a corporate environment. There is the potential for spamming to infect multiple computers to form a botnet. Some Trojans are embedded in legitimate software and do not interfere with its functioning; thus, the victim does not even notice their actions in the system. In addition to personal computers, an attacker can infect mobile devices in order to spy on the victim or to steal their confidential information.
Source of threat
The source of the threat can be file sharing and torrent trackers, to which the attacker has downloaded malware disguised as legitimate software, fake websites, spam mailings, etc. An important rule for protection is not to click on dubious links or run suspicious programs. Most Trojan horses are successfully detected by anti-virus and anti-spyware software. Law enforcement agencies can install Trojans on a suspect's computer or other devices in order to collect information and evidence. The intelligence of many countries uses such means for espionage. In general, Trojans are very widespread due to the fact that there are a huge number of different tools for creating them. For example, there are utilities that allow you to add a malicious agent to existing legal software.
Risk analysis
Both home and corporate users are at risk. Trojan horses may pose a serious threat to the victim (RAT, bankers), or may not interact with it in any way (DDoS Trojans). Many of them are difficult to detect, since they are embedded in the code of a legal program and do not interfere with its functioning. A characteristic feature of a Trojan is autorun: as a rule, it needs to be launched automatically at system startup or when a user logs on. Another sign is a slow computer. The Trojan puts a load on the processor (especially DDoS Trojans), which can slow down the PC and increase the CPU temperature. If the anti-virus software does not help, then the only reliable way out is to reinstall the OS or contact a specialist.
Trojan classification
One of the classification options is to divide into the following types:
1. RAT (Remote Access / Administration Tool)
2. Ransomware
3. Cryptographers (Ciphers)
4. Boot loaders (Downloaders)
5. Deactivators of protection systems
6. Bankers
7. DDoS Trojans
RAT is a spyware trojan. Once installed on the system, it provides an attacker with a wide range of options: capturing video from the victim's screen, accessing the file system, recording video from a webcam and sound from a microphone, stealing browser identification files (cookies), installing other programs, etc. Examples include DarkComet or AndroRAT.

Ransomware is a form of malicious objects that block access to a system or data, threaten the user with deleting files from a computer or spreading the victim's personal data on the Internet, and demanding a ransom payment to avoid such negative consequences. An example of this behavior is the WinLock family.
Cryptographers (Ciphers) is an advanced form of ransomware that uses cryptography as a means to block access. Whereas in the case of an ordinary "winlocker" it was possible to simply remove the malicious program and thereby regain access to information, here the destruction of the ransomware itself does nothing - the encrypted files remain inaccessible. However, in some cases, antivirus software can recover data. An example of a ransomware is CryZip.
Boot loaders (Downloaders) are a type of malicious agent designed to download other programs or files from the Internet. An example is Nemucode. Protection System Deactivators are Trojans that remove or stop antiviruses, firewalls, and other security tools.
Bankers are a type of Trojan horse that specializes in stealing bank data (account number, PIN, CVV, etc.).
DDoS Trojans (bots) are malicious programs that are used by hackers to form a botnet in order to carry out denial of service attacks.
All Trojans are loaded into the system under the guise of legitimate software. They can be specially uploaded by cybercriminals to cloud data storage or file-sharing resources. Also, Trojans can enter the system by installing them by an insider during physical contact with a computer. In addition, they are often disseminated through spam mailings.
Target of Trojans
Most often, the target of such a malicious agent is an ordinary PC and its user, but incidents are also possible in a corporate environment. There is the potential for spamming to infect multiple computers to form a botnet. Some Trojans are embedded in legitimate software and do not interfere with its functioning; thus, the victim does not even notice their actions in the system. In addition to personal computers, an attacker can infect mobile devices in order to spy on the victim or to steal their confidential information.
Source of threat
The source of the threat can be file sharing and torrent trackers, to which the attacker has downloaded malware disguised as legitimate software, fake websites, spam mailings, etc. An important rule for protection is not to click on dubious links or run suspicious programs. Most Trojan horses are successfully detected by anti-virus and anti-spyware software. Law enforcement agencies can install Trojans on a suspect's computer or other devices in order to collect information and evidence. The intelligence of many countries uses such means for espionage. In general, Trojans are very widespread due to the fact that there are a huge number of different tools for creating them. For example, there are utilities that allow you to add a malicious agent to existing legal software.
Risk analysis
Both home and corporate users are at risk. Trojan horses may pose a serious threat to the victim (RAT, bankers), or may not interact with it in any way (DDoS Trojans). Many of them are difficult to detect, since they are embedded in the code of a legal program and do not interfere with its functioning. A characteristic feature of a Trojan is autorun: as a rule, it needs to be launched automatically at system startup or when a user logs on. Another sign is a slow computer. The Trojan puts a load on the processor (especially DDoS Trojans), which can slow down the PC and increase the CPU temperature. If the anti-virus software does not help, then the only reliable way out is to reinstall the OS or contact a specialist.





