Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,231
- Points
- 113
A set of malicious APK files dubbed "BadPack" is making it difficult to detect malware in apps for the Android mobile operating system . Researchers blame BadPack for the recent successful attacks by operators of banking Trojans like TeaBot.
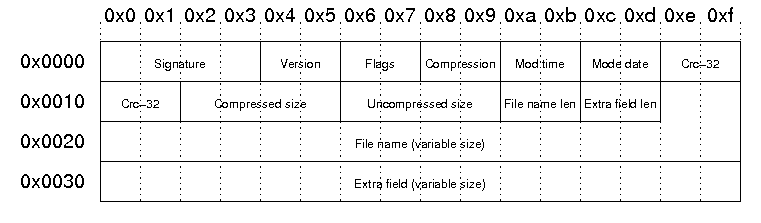
BadPack's peculiarity is that it modifies the header of the compressed APK file. This approach makes it difficult for reverse engineering tools to work.
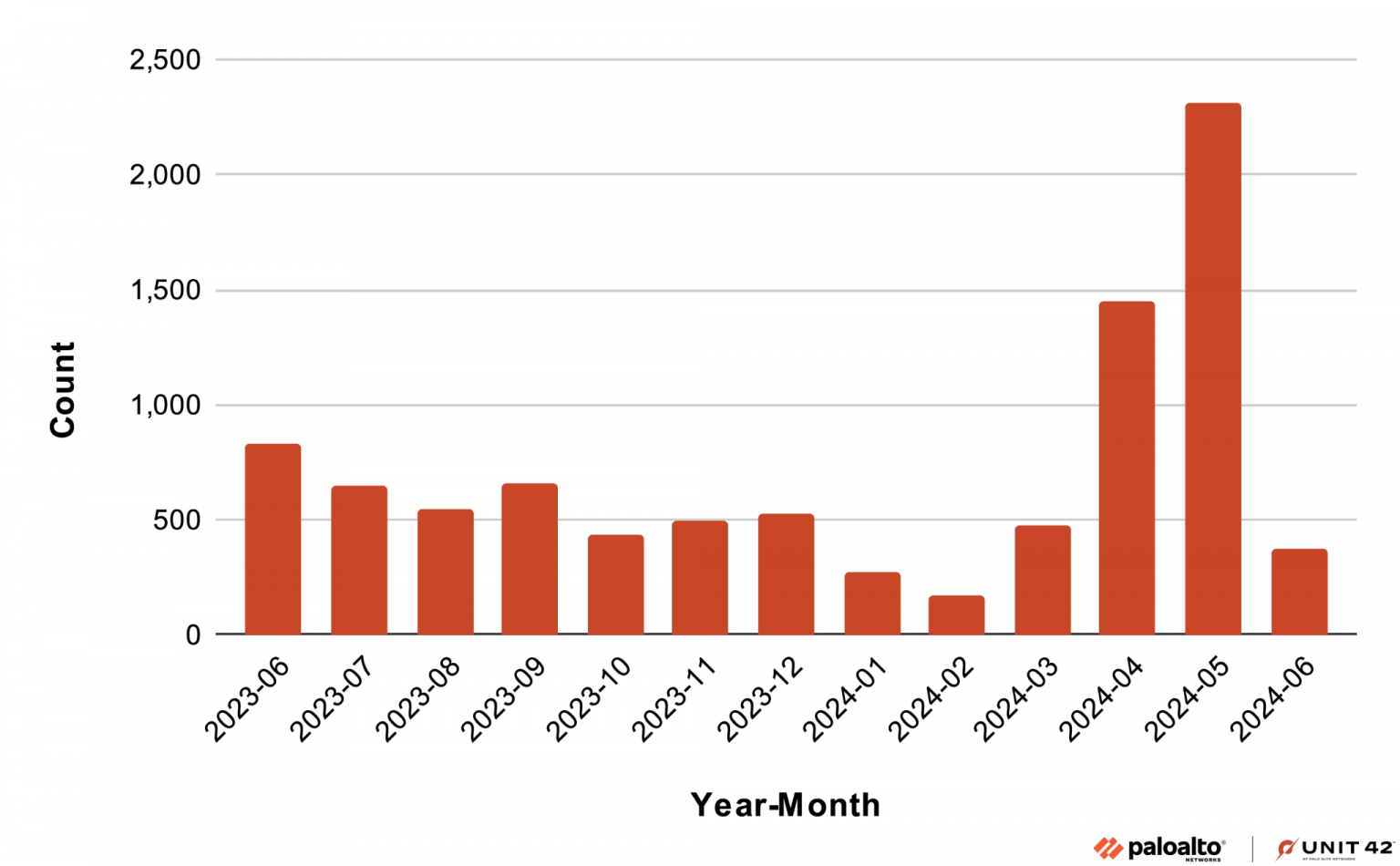
The team of specialists Unit 42 (owned by Palo Alto Networks) points to statistics for last year in a new report: researchers managed to detect about 9,200 BadPack samples in Android programs.
Some of these applications were quite safely placed in the official Google Play Store. Although later Google announced that it had removed all the mentioned malicious software.
BadPack may be the reason for the difficulties that experts face when analyzing Android malware.
To make the sample analysis more difficult, the attackers change the ZIP header of the BadPack APK file. This is used by many well-known Android Trojans: TeaBot, BianLian and Cerberus.
By modifying the header structure, cybercriminals cause the APK file to throw an error when unpacking and decoding the AndroidManifest.xml file.
Source
BadPack's peculiarity is that it modifies the header of the compressed APK file. This approach makes it difficult for reverse engineering tools to work.
The team of specialists Unit 42 (owned by Palo Alto Networks) points to statistics for last year in a new report: researchers managed to detect about 9,200 BadPack samples in Android programs.

Some of these applications were quite safely placed in the official Google Play Store. Although later Google announced that it had removed all the mentioned malicious software.
BadPack may be the reason for the difficulties that experts face when analyzing Android malware.
"APK files using BadPack are a good example of the growing sophistication of malware in APK format. As a challenge for security analysts, BadPack once again highlights the need for continuous development of countermeasure tools," explains Lee Wei Yong of Unit 42.
To make the sample analysis more difficult, the attackers change the ZIP header of the BadPack APK file. This is used by many well-known Android Trojans: TeaBot, BianLian and Cerberus.
By modifying the header structure, cybercriminals cause the APK file to throw an error when unpacking and decoding the AndroidManifest.xml file.

"This method causes a chain reaction of errors during the static analysis process. As a result, the file cannot be read and processed," notes Lee Wei Yong.
Source
