Hacker
Professional
- Messages
- 1,043
- Reaction score
- 846
- Points
- 113
The content of the article
Among the commercial three, a separate niche is occupied by stealers and a similar spiver. It is not surprising: other people's secrets have always been valuable. Today we will talk about spyware trojans available for free sale, about their features, functionality and methods of fighting this universal evil. Let's start, perhaps. Sister, scalpel!
N0F1L3
Stiler with such a difficult to pronounce name was actively sold on the Web until the author was not interested in stern people in uniform. The first version of the Trojan was written in .NET, the second, named N0F1L3v2, in C #. Troy specialized in stealing passwords from Chrome, Opera, Yandex, Torch, Amiga, Cometa and Orbitum browsers.

This is how N0F1L3 was sold
The styler was put up for sale on several forums at a very modest price, and in two versions: for $ 15 and $ 45, respectively. The author merged the sources for $ 600. The first release required .NET 2.0 to work, carried the sqlite3.dll library with me and dropped the required file of this lib to the disk in accordance with the Windows bit depth. He saved the stolen passwords to a text file with HTML markup directly on the infected machine, and then uploaded it to the server.
The second version differed from the first by the absence of dependencies, thanks to which it could theoretically work on a clean system. In addition, she learned how to tyrit information from Firefox, which the first modification of N0F1L3 never mastered. The styler collected cookies, autofill form data and passwords from browsers, copied files with the extensions .doc, .docx, .txt and .log from the desktop. From the popular FileZilla FTP client, it hijacked files filezilla_recentservers.xmland filezilla_sitemanager.xml. Troy also tried to steal crypto wallets BTC, BCN, DSH, ETH, LTC, XMR, ZEC, after which he shoved all this wealth into local folders and uploaded it to the control server as an archive.
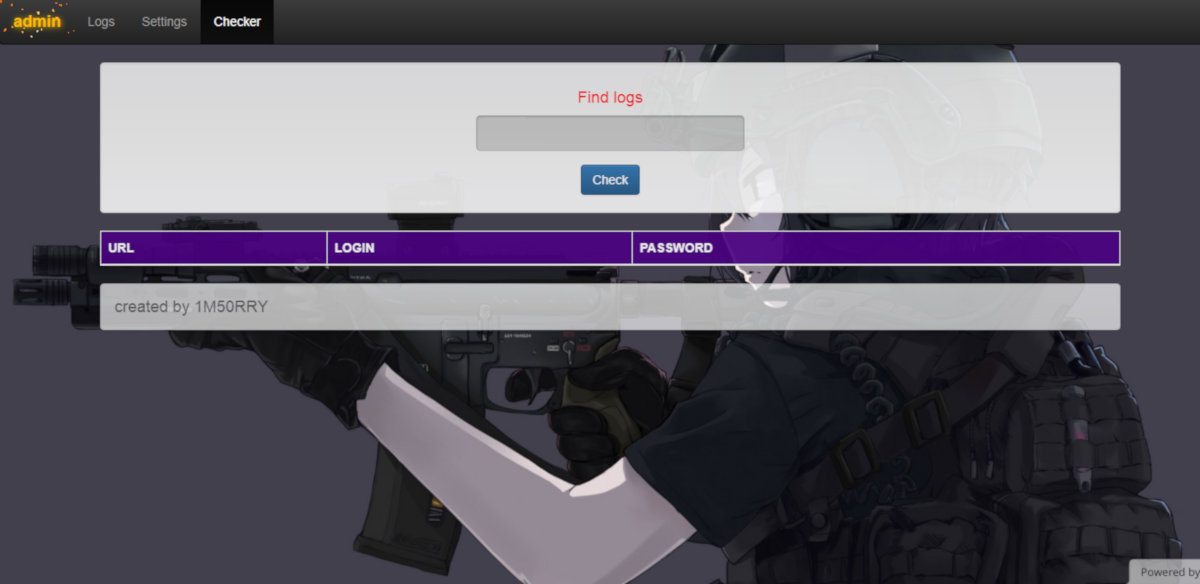
Admin panel N0F1L3
N0F1L3 is equipped with an admin panel written in PHP, where you can view trojan statistics and its logs. The author did not just sell the stealer, but also offered other commercial services related to it to anonymous users: updates, adding support for other browsers, and solving all sorts of technical problems. It is not surprising that soon well-wishers began to actively resell N0F1L3 on many popular and not very popular sites, and after the author started having problems with the law, the stealer was posted to the public. Sources and builds of this Trojan of varying degrees of freshness can be found on thematic boards today.
Detection methods
All versions of N0F1L3 and its numerous modifications are excellently scorched by antiviruses, but if you, the username, do not use them in principle, it is not at all difficult to detect the presence of a stealer in the system. An earlier modification of the Trojan saves the stolen file in a file %LOCALAPPDATA%\f.txt, its presence will accurately indicate to you the fact of infection. N0F1L3v2 creates %TEMP%a folder with the names of speakers Browsers, Wallets, Filesand Directory, in the first usually lie files from browsers pulled out infoy - Passwords.txt, Cookie.txt, CC.txtand Autofill.txt. N0F1L3 does not know how to hide in the system, so it is a matter of technique to burn it.
Kratos
Another "stealak-forte" by the same author, named either after a titan from Greek mythology, or after the hero of the toy God of War, which is more likely. Troy was almost completely rewritten in C ++, although a significant part of the functions in his code begins with an anti-debugging insert in assembler, which checks the state of a field BeingDebuggedin the PEB structure. This structure is created in the memory of the process when it starts and contains information about the environment, loaded modules, and other useful data. By the offset byte ptr [rax+2]in this structure, there is a flag that allows you to determine that the Trojan's process is running under the debugger and terminate it.

Himself so
In addition to the functions already implemented by its predecessors, Kratos is able to take screenshots (the picture is saved %TEMP%under the name screenshot.bmp) and copy files from the Telegram client folder %AppData%\Telegram Desktop\tdata. In addition, the stealer consults the registry looking for a branch [HKCU\Software\Valve\Steam]. Having found it, by the contents of the key, SteamPathit determines the installation location of the Steam client, and then pulls files from there config\config.vdf, config\loginusers.vdfand config\SteamAppData.vdf. Kratos packs everything stolen into an archive and sends it to the management server with a POST request.

Admin panel Kratos
Kratos uses the admin panel, which is generally similar to N0F1L3 (except that the default background image is not so cute). The developer himself sold his creation for 5,000 rubles, but on all well-known sites, anonymous users were quickly found, ready to give up builds for 1,500 and even a little cheaper - for a like, a sim, a review or a plus sign in a turnip. And after the author's deanon and the sad events that followed, the stealer appeared in the public and completely free. As a result, Kratos has crawled across your Internet like cockroaches in a student hostel, periodically crawling out of secluded cracks here and there. The dust was ineffective, it can only be burned out with napalm.
Detection methods
Antivirus detects this Trojan once or twice. Determine the presence of "Kratos" in the system is possible by the presence in %TEMP%the same folder as that of the N0F1L3, except that they added the directory Telegramand Steamwith obvious content.
AZORult
This is the name of a commercial stealer widely known in narrow circles, which has an impressive set of functionality. Troy is able to steal saved passwords, form data and cookies from 33 different browsers, the names of a good half of which I first saw in the advertising description of this very stealer. The Trojan's admin panel has a special converter that allows you to view the contents of cookies in JSON format.
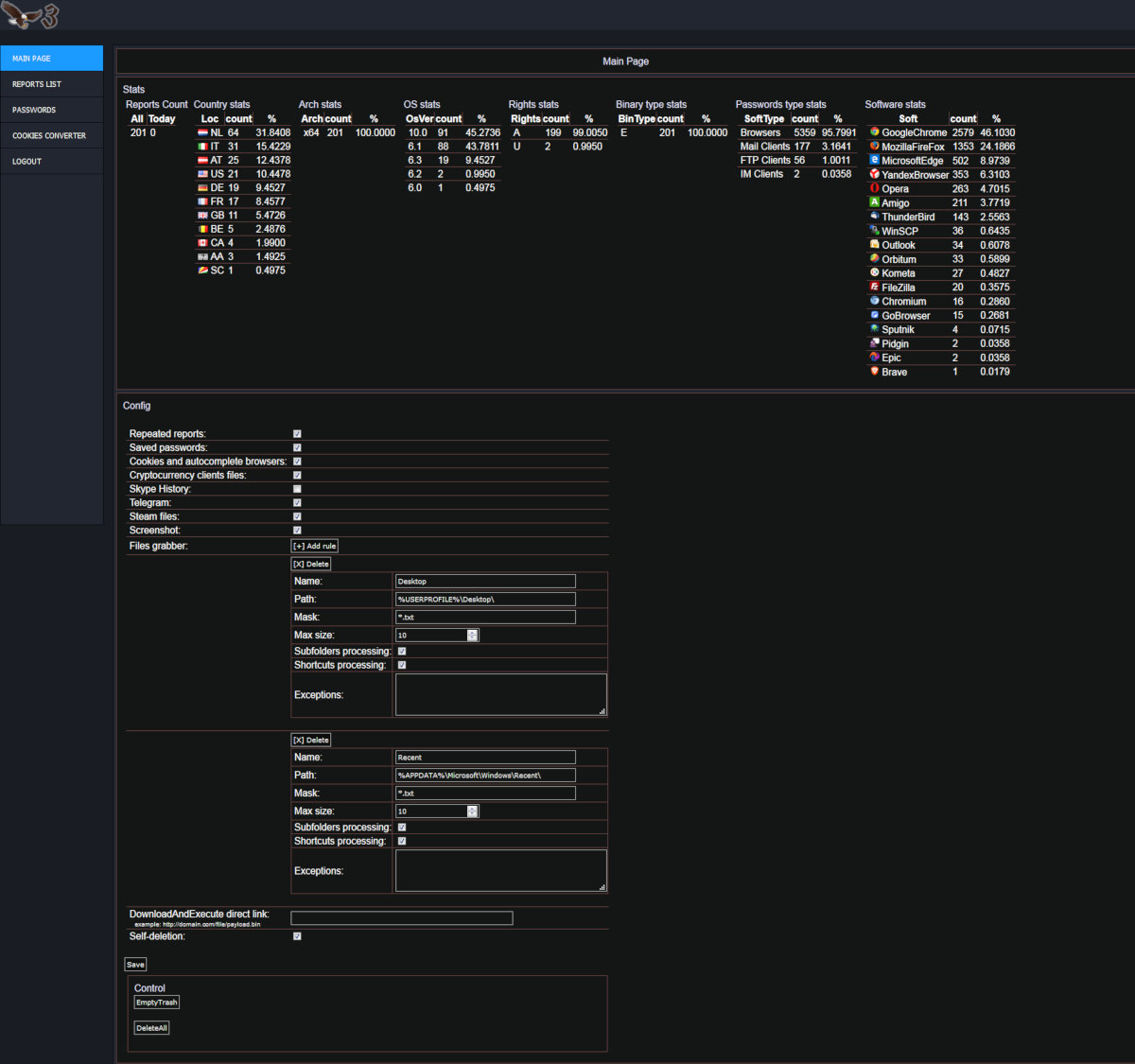
Admin panel AZORult
AZORult can pull passwords from Outlook and Thunderbird email clients, FileZilla and WinSCP FTP clients, Pidgin and Psi / Psi + IM clients. From Skype, he is able to copy correspondence, from Telegram - session identifiers, from the Steam client - ssfnand vdf. The list of cryptocurrencies whose wallets AZORult is able to steal is quite impressive: it has 38 names (about half of which don't tell me anything personally either, lol).
Among the capabilities of the stealer are not only banalities like taking screenshots - he also knows how to search an infected machine for files by name, size or mask with recursive bypass of nested directories, is able to collect information about the software environment and hardware configuration (including geolocation, a list of installed applications, etc. running processes), as well as download and run the specified file from the command and control server. Troy has an automatic self-deletion function after sending a report, if it is enabled in the admin panel, and is able to work with servers if they use a .bit domain. The uncompressed executable file takes about 110 KB, and under the packer it can be easily reduced to 40. Such is the combine at the price of $ 100.

This is how AZORult is sold
Last October, the author rolled out a Trojan update that allows you to pack the stealer into a Word or Excel document, and when you try to open it, an infection occurs. And at the beginning of this year, there were cases of distribution of the stealer under the guise of the Google Update utility, signed, which is typical, with a valid certificate.
Detection methods
A lot of interesting things can be found under the hood of AZORult. The name of the control server is stored in the stealer's body in encrypted form, Base64 with an arbitrary dictionary and RC4 is used for encryption, the key of which is also hardcoded by the author. To connect to the server, AZORult uses sockets, while the data sent to the server and the received responses are poxored. The architectural stealer consists of several functional modules, which are included according to the config obtained from the admin panel.
Since the builders for AZORult are widespread on the Internet, and they repack it with enviable regularity, not all of its samples are fired by antiviruses. However, the Trojan has one characteristic feature: it stores downloaded and required libraries in a folder %appdata%\1Mo\, the creation of which can be considered one of the sure signs of infection.
Eredel
A commercial stealer in C # with a fairly standard set of functions: stealing cookies and passwords from Chromium-based browsers, creating screenshots, copying files from the FileZilla and Telegram folders, as well as images, archives and documents that the user inadvertently forgot on the desktop. Management - from the traditional web admin panel.
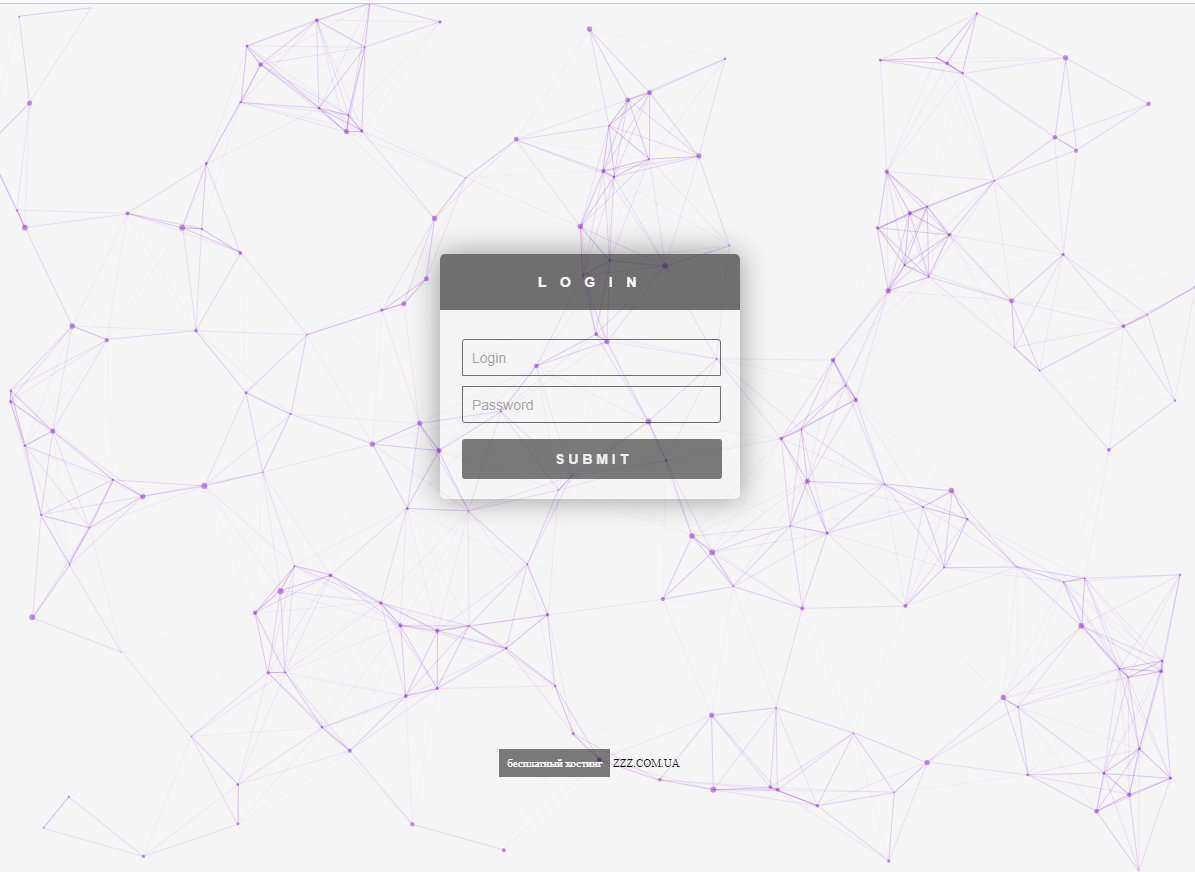
Admin panel Eredel
Of the interesting features of Eredel, it is worth noting only the presence of a special Telegram bot, with which you can set up a Troy. The styler is sold at different sites at a price of 2,500 rubles.
Detection methods
Due to not too regular "cleaning" Eredel is perfectly detected by the most popular antiviruses, so it is not always rational to bother with its "manual" capture. The styler creates in a %TEMP%folder with a name that is a hexadecimal sequence (for example, 0deb54d04c2140bb95d9d3f4919184aa), in which the screen.jpgscreenshot file is saved , and folders with distinguished names desktopand are located cookies. If these signs of infection are present, you can proceed to root out the malware, and the best place to start is by deleting the contents of temporary directories.
Kpot
A small non-resident triple, the uncompressed binary of which is slightly less than 90 KB. It is written in C / C ++ with anti-debugging inserts in assembler, which definitely reminds Kratos. Troy can take screenshots, steal cookies, passwords, and saved autofill data from Chromium-based and Mozilla-based browsers, and from MSIE 6-11 pulls only stored authorization data. At the same time, a stealer of Mozilla uses TinySQL to parse files key3.dband extract signons.sqlitepasswords from there.
Kpot can steal crypto wallets Bitcoin, Namecoin, Monero, Electrum, Ethereum and Bytecoin, accounts from Psi, Psi + and Pidgin messengers, Skype correspondence, session files from Telegram, Discord voice messenger and Battle.Net client, files ssfn, config.vdfand loginusers.vdffrom Steam, and See also logins and passwords for FTP connections from FileZilla, WinSCP, wsFtp and Total Commander.
One of the Trojan's capabilities is the ability to search for files by name, size and mask, not only on local drives, but also on network drives - however, in the version known to me, it was not possible to give it such a command from the admin panel. Everything that has been acquired by back-breaking labor is packed into a .cab archive by the stealer and uploaded to the control server.
The developer has provided the ability to load and run using the loadpe executable file, the link to which is indicated in the control panel. In 32-bit versions of Windows, the binary is launched in the context of the process from which it was called, and in 64-bit versions, the triple launches the command line and injects the application into the cmd.exe process.
Once launched, the stealer sends information about the infected computer to the control server: operating system version, data on screen resolution, number of cores and processor type, amount of RAM, local time and time zone, and also reports the IP address of the network interface. They control the trojan using a web panel.

Admin panel Kpot
The price of a stealer build on themed boards is $ 65, while the troop does not work in the CIS: apparently, the author believes that the principle of "no injured - no statements" will protect both himself and the users of this software from prosecution by law enforcement officers. However, as practice shows (at least the same case with the developer Kratos), this does not work at all.
Detection methods
During operation, the trojan creates a %TEMP%bunch of files in the folder with names consisting of ten digits, and then deletes them. It is quite difficult to catch it manually if the antivirus did not catch the Trojan, but you can see the stealer's work using the traffic analyzer communicating with the command server. In one of the most common samples, C&C was located at seeyouonlineservice.com.
Arkei
Arkei is one of the most widely used commercial stealers on the market. The executable file occupies only 96 KB, while the Trojan implements a set of functions that is quite standard for such software. Among them - sending information about the hardware and software environment to the control server, copying files from the desktop, creating a screenshot, collecting saved forms, logins, passwords, history and cookies from browsers (there are sixteen in the list of supported versions), stealing Bitcoin wallets, and Ethereum, data from the FileZilla FTP manager, as well as downloading and launching an arbitrary file on the infected machine, which, upon a command from the admin panel, the trooper can write to autoload by modifying the registry.

Arkei sale announcement
To control the stealer, the delivery set includes a web admin panel, and the retail price of the Trojan was 3000 rubles. Since February 2019, Arkei seems to have stopped updating, but the project, as far as I know, continues to live in the guise of a private stealer.
Detection methods
Like other similar Trojans, Arkei copies the executable file to the folder of the Local Settings\Tempcurrent user, under whose account it was launched. He saves the loot in a folder %PROGRAMDATA%, creating there a directory with a name containing a sequence of fourteen characters, and in it - a subfolder \files\. It contains text files with saved passwords, browser history, cookies and other data. Troy is well detected by the main antiviruses, many by the packer.
Pony
This stealer is not as popular with malware as its competitors, although the law enforcement agencies recently arrested a villain who was involved in creating admin panels, including for this Trojan.
Pony sources can be found on GitHub if you want to. Troy can steal information from browsers based on Chromium and Mozilla, a bunch of FTP clients (there are several dozen in the list) and mail clients PocoMail, IncrediMail, The Bat !, Outlook, Mozilla Thunderbird. He can also steal wallets of the most common cryptocurrencies. In general, the standard set, no surprises.
Detection methods
The low demand for "goodies" is probably due, among other things, to the fact that the stealer is available in the public, which means that there is zero point of privacy in it and about the same tenths.
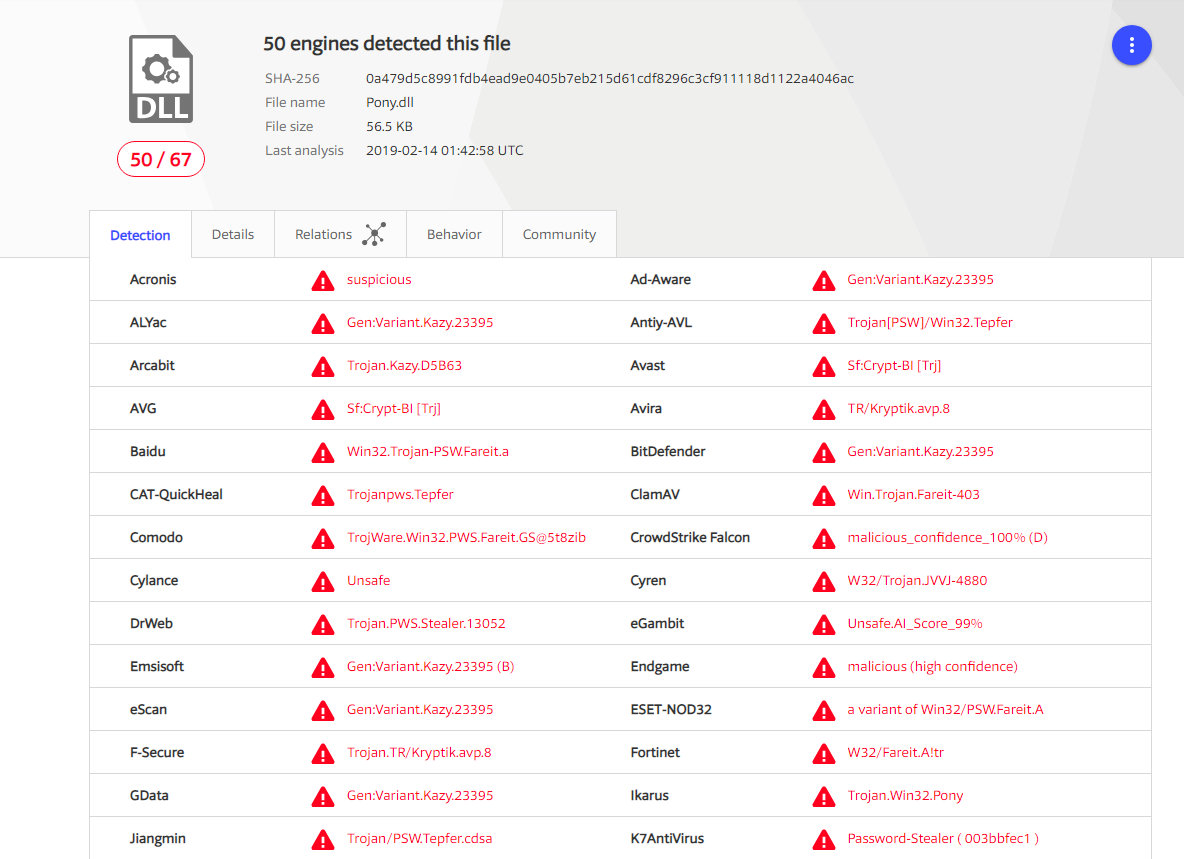
Pony detects
The Trojan's anti-viruses are known, appreciated and loved. However, the availability of sources opens up a wide scope for creativity for understanding people.
Predator The Thief
A styler with such a pompous name weighs about 430 KB; you can buy it in online markets for $ 30. The package includes a Trojan build, an admin panel, a manual for setting it up, a warranty card and headphones.
Predator The Thief Sale Announcement
In addition to the standard functions (taking screenshots, stealing forms, passwords and history from browsers, collecting files from the desktop and from FTP clients, as well as receiving sessions from Telegram),Perdator Predator can save a snapshot from the built-in webcam of an infected device, which happens very important if it suddenly occurs to you to watch your ex. This function is perhaps the only interesting feature of this wonderful software.
Detection methods
There are many modifications of this stealer in the wild, most of which are well known to all modern antiviruses. When launched, the trojan creates a C:\Documents and Settings\<USER>\Application Data\file in the folder with a name consisting of a long hexadecimal character sequence and starts it using schtasks.exe. He keeps the loot in a folder %APPDATA%\roaming\ptst\.
Instead of an afterword
To paraphrase the classic, we can say that all commercial stealers are similar to each other, but each works in its own way. The range of such programs is very wide, so people who trade in computer espionage will always be able to find something to their liking. It is only important not to forget that the development, distribution and use of malware is a criminal offense for which the current legislation provides for severe liability. Some people only think about it when it’s too late.
- N0F1L3
- Kratos
- AZORult
- Eredel
- Kpot
- Arkei
- Pony
- Predator The Thief
- Instead of an afterword
Among the commercial three, a separate niche is occupied by stealers and a similar spiver. It is not surprising: other people's secrets have always been valuable. Today we will talk about spyware trojans available for free sale, about their features, functionality and methods of fighting this universal evil. Let's start, perhaps. Sister, scalpel!
N0F1L3
Stiler with such a difficult to pronounce name was actively sold on the Web until the author was not interested in stern people in uniform. The first version of the Trojan was written in .NET, the second, named N0F1L3v2, in C #. Troy specialized in stealing passwords from Chrome, Opera, Yandex, Torch, Amiga, Cometa and Orbitum browsers.

This is how N0F1L3 was sold
The styler was put up for sale on several forums at a very modest price, and in two versions: for $ 15 and $ 45, respectively. The author merged the sources for $ 600. The first release required .NET 2.0 to work, carried the sqlite3.dll library with me and dropped the required file of this lib to the disk in accordance with the Windows bit depth. He saved the stolen passwords to a text file with HTML markup directly on the infected machine, and then uploaded it to the server.
The second version differed from the first by the absence of dependencies, thanks to which it could theoretically work on a clean system. In addition, she learned how to tyrit information from Firefox, which the first modification of N0F1L3 never mastered. The styler collected cookies, autofill form data and passwords from browsers, copied files with the extensions .doc, .docx, .txt and .log from the desktop. From the popular FileZilla FTP client, it hijacked files filezilla_recentservers.xmland filezilla_sitemanager.xml. Troy also tried to steal crypto wallets BTC, BCN, DSH, ETH, LTC, XMR, ZEC, after which he shoved all this wealth into local folders and uploaded it to the control server as an archive.

Admin panel N0F1L3
N0F1L3 is equipped with an admin panel written in PHP, where you can view trojan statistics and its logs. The author did not just sell the stealer, but also offered other commercial services related to it to anonymous users: updates, adding support for other browsers, and solving all sorts of technical problems. It is not surprising that soon well-wishers began to actively resell N0F1L3 on many popular and not very popular sites, and after the author started having problems with the law, the stealer was posted to the public. Sources and builds of this Trojan of varying degrees of freshness can be found on thematic boards today.
Detection methods
All versions of N0F1L3 and its numerous modifications are excellently scorched by antiviruses, but if you, the username, do not use them in principle, it is not at all difficult to detect the presence of a stealer in the system. An earlier modification of the Trojan saves the stolen file in a file %LOCALAPPDATA%\f.txt, its presence will accurately indicate to you the fact of infection. N0F1L3v2 creates %TEMP%a folder with the names of speakers Browsers, Wallets, Filesand Directory, in the first usually lie files from browsers pulled out infoy - Passwords.txt, Cookie.txt, CC.txtand Autofill.txt. N0F1L3 does not know how to hide in the system, so it is a matter of technique to burn it.
Kratos
Another "stealak-forte" by the same author, named either after a titan from Greek mythology, or after the hero of the toy God of War, which is more likely. Troy was almost completely rewritten in C ++, although a significant part of the functions in his code begins with an anti-debugging insert in assembler, which checks the state of a field BeingDebuggedin the PEB structure. This structure is created in the memory of the process when it starts and contains information about the environment, loaded modules, and other useful data. By the offset byte ptr [rax+2]in this structure, there is a flag that allows you to determine that the Trojan's process is running under the debugger and terminate it.

Himself so
In addition to the functions already implemented by its predecessors, Kratos is able to take screenshots (the picture is saved %TEMP%under the name screenshot.bmp) and copy files from the Telegram client folder %AppData%\Telegram Desktop\tdata. In addition, the stealer consults the registry looking for a branch [HKCU\Software\Valve\Steam]. Having found it, by the contents of the key, SteamPathit determines the installation location of the Steam client, and then pulls files from there config\config.vdf, config\loginusers.vdfand config\SteamAppData.vdf. Kratos packs everything stolen into an archive and sends it to the management server with a POST request.

Admin panel Kratos
Kratos uses the admin panel, which is generally similar to N0F1L3 (except that the default background image is not so cute). The developer himself sold his creation for 5,000 rubles, but on all well-known sites, anonymous users were quickly found, ready to give up builds for 1,500 and even a little cheaper - for a like, a sim, a review or a plus sign in a turnip. And after the author's deanon and the sad events that followed, the stealer appeared in the public and completely free. As a result, Kratos has crawled across your Internet like cockroaches in a student hostel, periodically crawling out of secluded cracks here and there. The dust was ineffective, it can only be burned out with napalm.
Detection methods
Antivirus detects this Trojan once or twice. Determine the presence of "Kratos" in the system is possible by the presence in %TEMP%the same folder as that of the N0F1L3, except that they added the directory Telegramand Steamwith obvious content.
AZORult
This is the name of a commercial stealer widely known in narrow circles, which has an impressive set of functionality. Troy is able to steal saved passwords, form data and cookies from 33 different browsers, the names of a good half of which I first saw in the advertising description of this very stealer. The Trojan's admin panel has a special converter that allows you to view the contents of cookies in JSON format.

Admin panel AZORult
AZORult can pull passwords from Outlook and Thunderbird email clients, FileZilla and WinSCP FTP clients, Pidgin and Psi / Psi + IM clients. From Skype, he is able to copy correspondence, from Telegram - session identifiers, from the Steam client - ssfnand vdf. The list of cryptocurrencies whose wallets AZORult is able to steal is quite impressive: it has 38 names (about half of which don't tell me anything personally either, lol).
Among the capabilities of the stealer are not only banalities like taking screenshots - he also knows how to search an infected machine for files by name, size or mask with recursive bypass of nested directories, is able to collect information about the software environment and hardware configuration (including geolocation, a list of installed applications, etc. running processes), as well as download and run the specified file from the command and control server. Troy has an automatic self-deletion function after sending a report, if it is enabled in the admin panel, and is able to work with servers if they use a .bit domain. The uncompressed executable file takes about 110 KB, and under the packer it can be easily reduced to 40. Such is the combine at the price of $ 100.

This is how AZORult is sold
Last October, the author rolled out a Trojan update that allows you to pack the stealer into a Word or Excel document, and when you try to open it, an infection occurs. And at the beginning of this year, there were cases of distribution of the stealer under the guise of the Google Update utility, signed, which is typical, with a valid certificate.
Detection methods
A lot of interesting things can be found under the hood of AZORult. The name of the control server is stored in the stealer's body in encrypted form, Base64 with an arbitrary dictionary and RC4 is used for encryption, the key of which is also hardcoded by the author. To connect to the server, AZORult uses sockets, while the data sent to the server and the received responses are poxored. The architectural stealer consists of several functional modules, which are included according to the config obtained from the admin panel.
Since the builders for AZORult are widespread on the Internet, and they repack it with enviable regularity, not all of its samples are fired by antiviruses. However, the Trojan has one characteristic feature: it stores downloaded and required libraries in a folder %appdata%\1Mo\, the creation of which can be considered one of the sure signs of infection.
Eredel
A commercial stealer in C # with a fairly standard set of functions: stealing cookies and passwords from Chromium-based browsers, creating screenshots, copying files from the FileZilla and Telegram folders, as well as images, archives and documents that the user inadvertently forgot on the desktop. Management - from the traditional web admin panel.

Admin panel Eredel
Of the interesting features of Eredel, it is worth noting only the presence of a special Telegram bot, with which you can set up a Troy. The styler is sold at different sites at a price of 2,500 rubles.
Detection methods
Due to not too regular "cleaning" Eredel is perfectly detected by the most popular antiviruses, so it is not always rational to bother with its "manual" capture. The styler creates in a %TEMP%folder with a name that is a hexadecimal sequence (for example, 0deb54d04c2140bb95d9d3f4919184aa), in which the screen.jpgscreenshot file is saved , and folders with distinguished names desktopand are located cookies. If these signs of infection are present, you can proceed to root out the malware, and the best place to start is by deleting the contents of temporary directories.
Kpot
A small non-resident triple, the uncompressed binary of which is slightly less than 90 KB. It is written in C / C ++ with anti-debugging inserts in assembler, which definitely reminds Kratos. Troy can take screenshots, steal cookies, passwords, and saved autofill data from Chromium-based and Mozilla-based browsers, and from MSIE 6-11 pulls only stored authorization data. At the same time, a stealer of Mozilla uses TinySQL to parse files key3.dband extract signons.sqlitepasswords from there.
Kpot can steal crypto wallets Bitcoin, Namecoin, Monero, Electrum, Ethereum and Bytecoin, accounts from Psi, Psi + and Pidgin messengers, Skype correspondence, session files from Telegram, Discord voice messenger and Battle.Net client, files ssfn, config.vdfand loginusers.vdffrom Steam, and See also logins and passwords for FTP connections from FileZilla, WinSCP, wsFtp and Total Commander.
One of the Trojan's capabilities is the ability to search for files by name, size and mask, not only on local drives, but also on network drives - however, in the version known to me, it was not possible to give it such a command from the admin panel. Everything that has been acquired by back-breaking labor is packed into a .cab archive by the stealer and uploaded to the control server.
The developer has provided the ability to load and run using the loadpe executable file, the link to which is indicated in the control panel. In 32-bit versions of Windows, the binary is launched in the context of the process from which it was called, and in 64-bit versions, the triple launches the command line and injects the application into the cmd.exe process.
Once launched, the stealer sends information about the infected computer to the control server: operating system version, data on screen resolution, number of cores and processor type, amount of RAM, local time and time zone, and also reports the IP address of the network interface. They control the trojan using a web panel.

Admin panel Kpot
The price of a stealer build on themed boards is $ 65, while the troop does not work in the CIS: apparently, the author believes that the principle of "no injured - no statements" will protect both himself and the users of this software from prosecution by law enforcement officers. However, as practice shows (at least the same case with the developer Kratos), this does not work at all.
Detection methods
During operation, the trojan creates a %TEMP%bunch of files in the folder with names consisting of ten digits, and then deletes them. It is quite difficult to catch it manually if the antivirus did not catch the Trojan, but you can see the stealer's work using the traffic analyzer communicating with the command server. In one of the most common samples, C&C was located at seeyouonlineservice.com.
Arkei
Arkei is one of the most widely used commercial stealers on the market. The executable file occupies only 96 KB, while the Trojan implements a set of functions that is quite standard for such software. Among them - sending information about the hardware and software environment to the control server, copying files from the desktop, creating a screenshot, collecting saved forms, logins, passwords, history and cookies from browsers (there are sixteen in the list of supported versions), stealing Bitcoin wallets, and Ethereum, data from the FileZilla FTP manager, as well as downloading and launching an arbitrary file on the infected machine, which, upon a command from the admin panel, the trooper can write to autoload by modifying the registry.

Arkei sale announcement
To control the stealer, the delivery set includes a web admin panel, and the retail price of the Trojan was 3000 rubles. Since February 2019, Arkei seems to have stopped updating, but the project, as far as I know, continues to live in the guise of a private stealer.
Detection methods
Like other similar Trojans, Arkei copies the executable file to the folder of the Local Settings\Tempcurrent user, under whose account it was launched. He saves the loot in a folder %PROGRAMDATA%, creating there a directory with a name containing a sequence of fourteen characters, and in it - a subfolder \files\. It contains text files with saved passwords, browser history, cookies and other data. Troy is well detected by the main antiviruses, many by the packer.
Pony
This stealer is not as popular with malware as its competitors, although the law enforcement agencies recently arrested a villain who was involved in creating admin panels, including for this Trojan.
Pony sources can be found on GitHub if you want to. Troy can steal information from browsers based on Chromium and Mozilla, a bunch of FTP clients (there are several dozen in the list) and mail clients PocoMail, IncrediMail, The Bat !, Outlook, Mozilla Thunderbird. He can also steal wallets of the most common cryptocurrencies. In general, the standard set, no surprises.
Detection methods
The low demand for "goodies" is probably due, among other things, to the fact that the stealer is available in the public, which means that there is zero point of privacy in it and about the same tenths.

Pony detects
The Trojan's anti-viruses are known, appreciated and loved. However, the availability of sources opens up a wide scope for creativity for understanding people.
Predator The Thief
A styler with such a pompous name weighs about 430 KB; you can buy it in online markets for $ 30. The package includes a Trojan build, an admin panel, a manual for setting it up

Predator The Thief Sale Announcement
In addition to the standard functions (taking screenshots, stealing forms, passwords and history from browsers, collecting files from the desktop and from FTP clients, as well as receiving sessions from Telegram),
Detection methods
There are many modifications of this stealer in the wild, most of which are well known to all modern antiviruses. When launched, the trojan creates a C:\Documents and Settings\<USER>\Application Data\file in the folder with a name consisting of a long hexadecimal character sequence and starts it using schtasks.exe. He keeps the loot in a folder %APPDATA%\roaming\ptst\.
Instead of an afterword
To paraphrase the classic, we can say that all commercial stealers are similar to each other, but each works in its own way. The range of such programs is very wide, so people who trade in computer espionage will always be able to find something to their liking. It is only important not to forget that the development, distribution and use of malware is a criminal offense for which the current legislation provides for severe liability. Some people only think about it when it’s too late.
