Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,330
- Points
- 113
Chinese hackers were able to quietly inject viruses into the target's systems.
According to a new report from Volexity, in mid-2023, the Chinese group Evasive Panda hacked into the systems of an Internet service provider in order to distribute malicious software updates to the company's customers.
In the discovered campaign, Evasive Panda attacked an international non-governmental organization (NGO) in mainland China using MgBot. The backdoor was distributed through updates to the legitimate Tencent QQ app.
Malicious updates were the result of the "DNS Spoofing" method at the ISP level. StormBamboo introduced malware through the HTTP automatic update mechanism and changed responses for hosts. The DNS records were changed to point to the attackers server in Hong Kong. The hosts were later used as C2 servers.
The attack is quite simple: vulnerable update mechanisms are used to deliver MgBot (Windows) or MACMA (macOS), depending on the operating system used. Volexity reported the attack to the provider, which investigated and rebooted various key devices, after which the campaign immediately stopped.
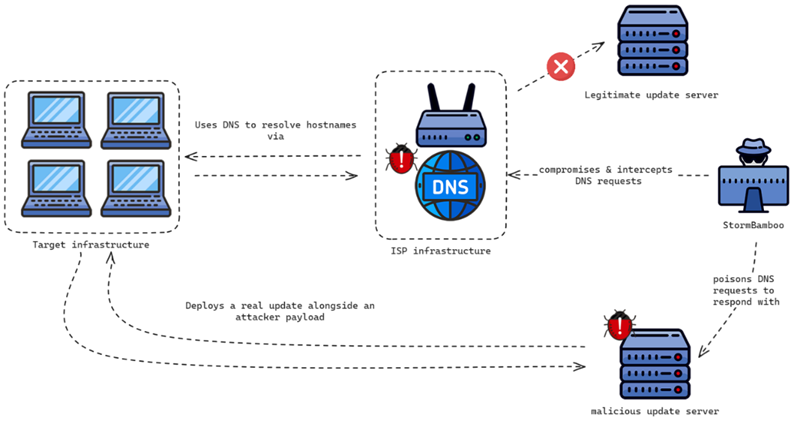
Evasive Panda Infection Chain
In one case, a malicious extension for Google Chrome was also installed on a macOS device that modified the Secure Preferences file. The extension was allegedly intended to load a page in Internet Explorer compatibility mode, but its main purpose was to steal browser cookies and send them to the attacker's Google Drive account.
Also, in one of the latest cases, attackers used vulnerable automatic update mechanisms in the victims ' software, which made it possible to distribute malware without any user interaction. A legitimate application requested updates via HTTP and received a fake configuration file with a URL for downloading the malicious installer. For example, the 5KPlayer app automatically checked for a new version of the YoutubeDL component every time it was launched, and Evasive Panda spoofed the configuration file, pointing to the attackers server with a modified update.
Evasive Panda (Bronze Highland, Daggerfly, StormBamboo) has been engaged in cyber espionage since 2012, using MgBot (POCOSTICK) and Nightdoor (NetMM, Suzafk) backdoors to steal confidential information. The group was recently credited with using macOS malware called MACMA, which has been found in the wild since 2021.
Source
According to a new report from Volexity, in mid-2023, the Chinese group Evasive Panda hacked into the systems of an Internet service provider in order to distribute malicious software updates to the company's customers.
In the discovered campaign, Evasive Panda attacked an international non-governmental organization (NGO) in mainland China using MgBot. The backdoor was distributed through updates to the legitimate Tencent QQ app.
Malicious updates were the result of the "DNS Spoofing" method at the ISP level. StormBamboo introduced malware through the HTTP automatic update mechanism and changed responses for hosts. The DNS records were changed to point to the attackers server in Hong Kong. The hosts were later used as C2 servers.
The attack is quite simple: vulnerable update mechanisms are used to deliver MgBot (Windows) or MACMA (macOS), depending on the operating system used. Volexity reported the attack to the provider, which investigated and rebooted various key devices, after which the campaign immediately stopped.

Evasive Panda Infection Chain
In one case, a malicious extension for Google Chrome was also installed on a macOS device that modified the Secure Preferences file. The extension was allegedly intended to load a page in Internet Explorer compatibility mode, but its main purpose was to steal browser cookies and send them to the attacker's Google Drive account.
Also, in one of the latest cases, attackers used vulnerable automatic update mechanisms in the victims ' software, which made it possible to distribute malware without any user interaction. A legitimate application requested updates via HTTP and received a fake configuration file with a URL for downloading the malicious installer. For example, the 5KPlayer app automatically checked for a new version of the YoutubeDL component every time it was launched, and Evasive Panda spoofed the configuration file, pointing to the attackers server with a modified update.
Evasive Panda (Bronze Highland, Daggerfly, StormBamboo) has been engaged in cyber espionage since 2012, using MgBot (POCOSTICK) and Nightdoor (NetMM, Suzafk) backdoors to steal confidential information. The group was recently credited with using macOS malware called MACMA, which has been found in the wild since 2021.
Source
