How a prayer festival became a perfect trap in the hands of cyber villains.
A Chinese-linked cybercriminal group known under the pseudonym Evasive Panda has launched a series of cyber attacks on users associated with the Tibetan community. The first attacks of this series were recorded by researchers in September last year, and the Sino-Tibetan confrontation in cyberspace itself has been going on for a very,very long time .
During attacks on the software supply chain, as well as attacks like Watering Hole, attackers used the already known backdoor called MgBot, as well as the previously undocumented Nightdoor implant.
Cyberattacks were reported by ESET specialists. According to them, hackers compromised at least three websites using the above-mentioned methods, as well as the software of a specific company specializing in the development of dictionaries for translating from Tibetan.
The attacks target users from India, Taiwan, Hong Kong, Australia, and the United States. Evasive Panda is alleged to have used the annual Kagyu Monlam festival as a convenient excuse to attack the Tibetan community.
Evasive Panda has been active since 2012 and is also known as Bronze Highland and Daggerfly. Earlier, in April 2023, this group was already accused of attacking an international private organization in China using MgBot.
In the latest series of attacks, hackers compromised the Kagyumonlam website ("kagyumonlam[.]org") by installing a script that checks the IP address of a potential victim. If the IP address matches one of the target ranges, the user is shown a fake page with an error and a suggestion to download the" fix "called " Fix". certificate.exe".
Running this file activates a long chain of infection, the final stage of which is the deployment of malware that has the ability to collect information about the system, the list of installed applications and running processes, create a reverse shell, perform file operations, and even delete itself from the infected system.
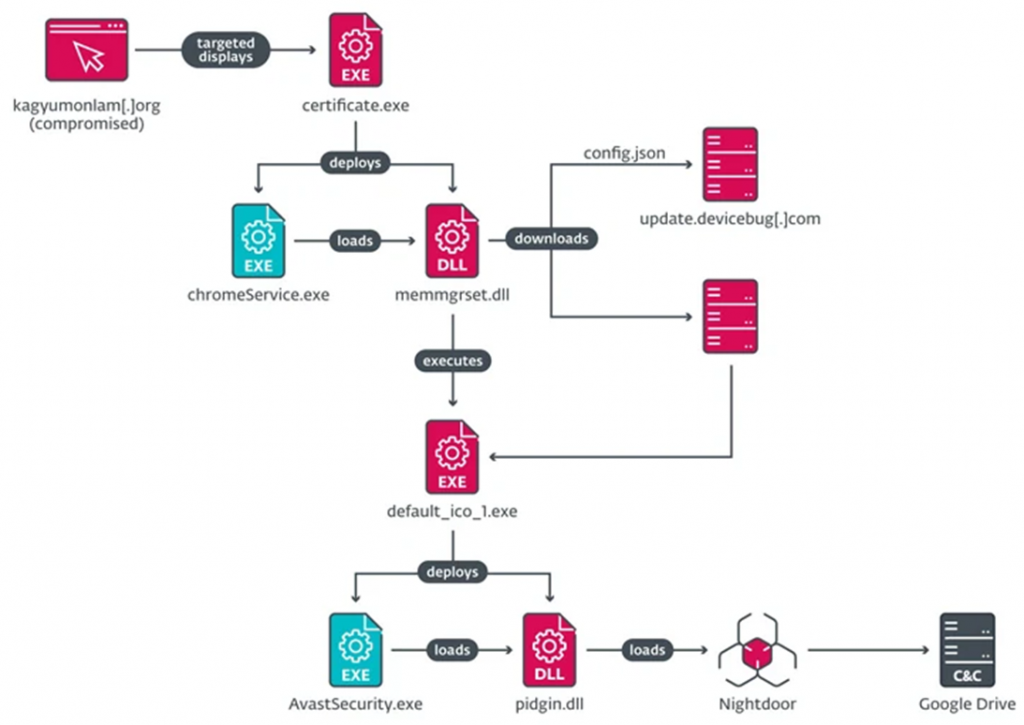
Executable files for Windows and macOS run the Nightdoor implant, which then uses the Google Drive API for C2 interaction.
The malicious operation also included hacking the website of the Indian company Monlam IT ("monlamit[.]com") and distributing infected installers of Tibetan translation software.
In addition, hackers used the same website and the Tibet News website ("tibetpost[.]net") to host downloadable malicious files, including two full-featured backdoors for Windows and an unknown amount of malware for macOS.
ESET noted that the attackers used several loaders, droppers, and backdoors, including MgBot, which is exclusively used by Evasive Panda, hence the corresponding attribution.
Hacker groups like Evasive Panda have no moral limitations and are ready to deliver a crushing blow under any convenient pretext. The Kagyu Monlam prayer festival, which is of great importance to the Tibetan Buddhist community, was no exception and was used by hackers to spread malware and steal confidential data.
A Chinese-linked cybercriminal group known under the pseudonym Evasive Panda has launched a series of cyber attacks on users associated with the Tibetan community. The first attacks of this series were recorded by researchers in September last year, and the Sino-Tibetan confrontation in cyberspace itself has been going on for a very,very long time .
During attacks on the software supply chain, as well as attacks like Watering Hole, attackers used the already known backdoor called MgBot, as well as the previously undocumented Nightdoor implant.
Cyberattacks were reported by ESET specialists. According to them, hackers compromised at least three websites using the above-mentioned methods, as well as the software of a specific company specializing in the development of dictionaries for translating from Tibetan.
The attacks target users from India, Taiwan, Hong Kong, Australia, and the United States. Evasive Panda is alleged to have used the annual Kagyu Monlam festival as a convenient excuse to attack the Tibetan community.
Evasive Panda has been active since 2012 and is also known as Bronze Highland and Daggerfly. Earlier, in April 2023, this group was already accused of attacking an international private organization in China using MgBot.
In the latest series of attacks, hackers compromised the Kagyumonlam website ("kagyumonlam[.]org") by installing a script that checks the IP address of a potential victim. If the IP address matches one of the target ranges, the user is shown a fake page with an error and a suggestion to download the" fix "called " Fix". certificate.exe".
Running this file activates a long chain of infection, the final stage of which is the deployment of malware that has the ability to collect information about the system, the list of installed applications and running processes, create a reverse shell, perform file operations, and even delete itself from the infected system.

Executable files for Windows and macOS run the Nightdoor implant, which then uses the Google Drive API for C2 interaction.
The malicious operation also included hacking the website of the Indian company Monlam IT ("monlamit[.]com") and distributing infected installers of Tibetan translation software.
In addition, hackers used the same website and the Tibet News website ("tibetpost[.]net") to host downloadable malicious files, including two full-featured backdoors for Windows and an unknown amount of malware for macOS.
ESET noted that the attackers used several loaders, droppers, and backdoors, including MgBot, which is exclusively used by Evasive Panda, hence the corresponding attribution.
Hacker groups like Evasive Panda have no moral limitations and are ready to deliver a crushing blow under any convenient pretext. The Kagyu Monlam prayer festival, which is of great importance to the Tibetan Buddhist community, was no exception and was used by hackers to spread malware and steal confidential data.
