Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Your home router may not be connecting to where you want it to go.
Black Lotus Labs discovered a new variant of the TheMoon malware targeting SOHO offices and IoT devices in 88 countries, which has already infected nearly 7,000 ASUS routers.
TheMoon is linked to Faceless, an anonymous proxy service that uses infected devices to route traffic from cybercriminals who want to hide their actions. IcedID and SolarMarker malware campaigns already use this network to mask their online activity.
During the detected campaign, almost 7,000 devices were compromised in a week, and the main target was ASUS routers. Attackers most likely used known vulnerabilities in the firmware or brute-force methods to gain access to devices.
Once the device is penetrated, the malware sets certain rules for filtering traffic and tries to contact the C2 server for further instructions. In some cases, the server may load additional components to scan vulnerable servers or to proxy traffic.
Faceless is a proxy service for cybercriminals that operates without a customer verification process and accepts payments exclusively in cryptocurrency. To protect their infrastructure, Faceless operators restrict infected devices from communicating with a single server for the entire period of infection.
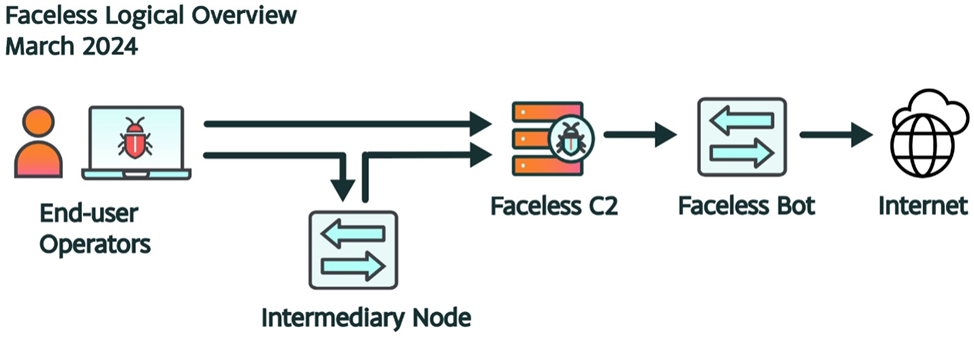
How the proxy service works
A study by Black Lotus Labs shows that about 30% of infections last more than 50 days, and 15% are detected and eliminated in less than 48 hours.
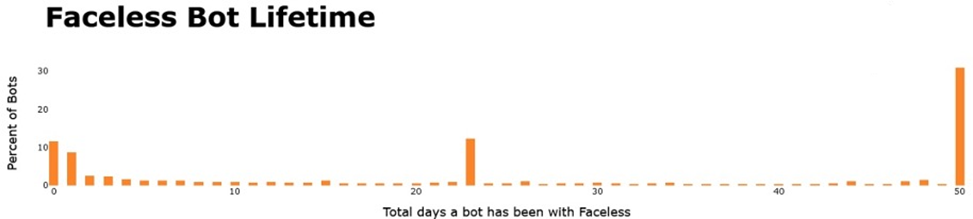
Lifetime of infected devices
Despite the clear link between TheMoon and Faceless, the two operations represent separate cybercrime ecosystems, as not all malware infections become part of the Faceless botnet.
To protect against such threats, it is recommended to use complex passwords and update the device firmware to the latest version that fixes known flaws. If the device is outdated and no longer supported by the manufacturer, you should replace it with a new model with active support. As a rule, signs of device infection include connection problems, overheating, and suspicious changes in settings.
Black Lotus Labs discovered a new variant of the TheMoon malware targeting SOHO offices and IoT devices in 88 countries, which has already infected nearly 7,000 ASUS routers.
TheMoon is linked to Faceless, an anonymous proxy service that uses infected devices to route traffic from cybercriminals who want to hide their actions. IcedID and SolarMarker malware campaigns already use this network to mask their online activity.
During the detected campaign, almost 7,000 devices were compromised in a week, and the main target was ASUS routers. Attackers most likely used known vulnerabilities in the firmware or brute-force methods to gain access to devices.
Once the device is penetrated, the malware sets certain rules for filtering traffic and tries to contact the C2 server for further instructions. In some cases, the server may load additional components to scan vulnerable servers or to proxy traffic.
Faceless is a proxy service for cybercriminals that operates without a customer verification process and accepts payments exclusively in cryptocurrency. To protect their infrastructure, Faceless operators restrict infected devices from communicating with a single server for the entire period of infection.

How the proxy service works
A study by Black Lotus Labs shows that about 30% of infections last more than 50 days, and 15% are detected and eliminated in less than 48 hours.

Lifetime of infected devices
Despite the clear link between TheMoon and Faceless, the two operations represent separate cybercrime ecosystems, as not all malware infections become part of the Faceless botnet.
To protect against such threats, it is recommended to use complex passwords and update the device firmware to the latest version that fixes known flaws. If the device is outdated and no longer supported by the manufacturer, you should replace it with a new model with active support. As a rule, signs of device infection include connection problems, overheating, and suspicious changes in settings.

