Dangerous malware called Erbium has appeared on the Internet. This is an identity theft tool that targets your passwords, bank card details, cookies, cryptocurrency wallets, and possibly more. Due to its rapid spread and widespread availability in the future, it could be adapted to infect computers in new ways and steal other data.
The malware is mainly spread through pirated games and cheats/cracks for games. Malware pretends to be a hacked program or game, and people themselves download it through a free file hosting service, such as a torrent. It is also distributed through spear phishing, links in emails, malicious advertising, exploit kits, and even malware downloaders themselves. There are already thousands of options for how it can penetrate a computer. One of the reasons for the malware's rapid spread is that Erbium is a so-called "malware as a service" (MaaS), meaning that essentially anyone can start sending out a virus by paying its developers a subscription.
This is another feature of the malware - it even has a referral system and customer support service that answers questions from young and not so young hackers. A subscription that provides access to the malware control panel initially cost only $9 per week (more precisely, 500 rubles). But its growing popularity has caused the price to rise to $100 per month.
The business is built on mass, and there is even a discount that allows you to subscribe for a whole year for $1,000. This is much cheaper than “subscribing” to other similar viruses, such as RedLine, which contributes to the rapid spread of this exploit. For the money, Erbium subscribers get updates, customer support and malware with a full set of tools. Due to the abundance of functions, low prices and “customer-centricity”, this nasty thing is quickly gaining popularity in the hacker community.
Should we be afraid?
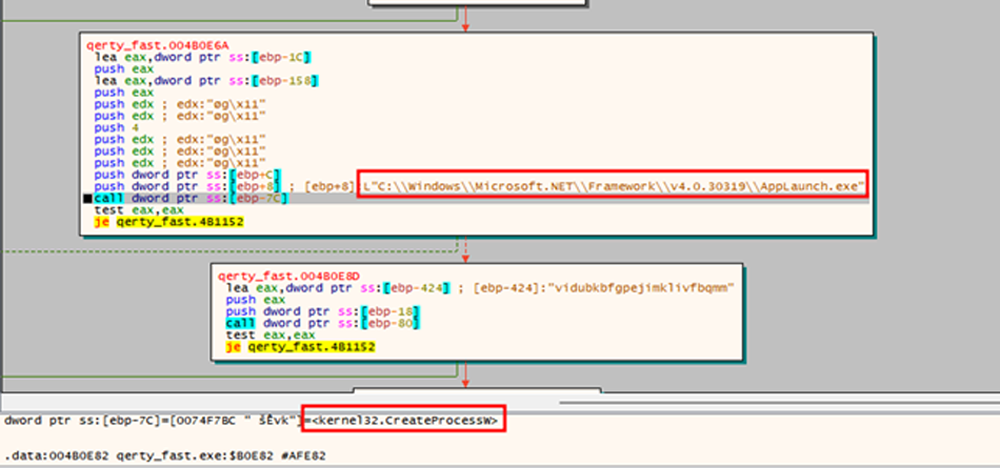
The malware was initially discovered on dark web forums by threat hunting and cyber intelligence company Cyfirma. According to her, Erbium was first posted by a Russian-speaking user at the end of July and even then was able to collect data from most modern popular browsers, obtaining passwords, cookies and credit card information. According to the creators, they developed Erbium for several months. Since its release, the malware has received several updates and has become more dangerous.Subsequently, the malware code was also deeply analyzed by DuskRise, which deals with the cybersecurity of remote employees. Here you can read about how the attack is carried out, what processes are affected, what is at risk, how the stolen information is then collected, and so on.

According to them, Erbium can attack cryptocurrency users by stealing data from users’ digital wallets, both cold and running through a browser extension. The malware hacks the accounts of Exodus, Atomic, Bytecoin, Ethereum and dozens of other wallets. It is known to be able to obtain two-factor authentication codes from several 2FA and password managers.
All browser data is also stolen, such as logins, cookies, history and wallet information, and data from plugins. Information is stolen from Steam, Discord, FTP clients, Telegram and cold wallets on the desktop. The malware can also take screenshots.
Once the data has been stolen, it is transmitted to attackers around the world via the built-in API system, and operators see an overview of what was found on each infected host in the Erbium dashboard.
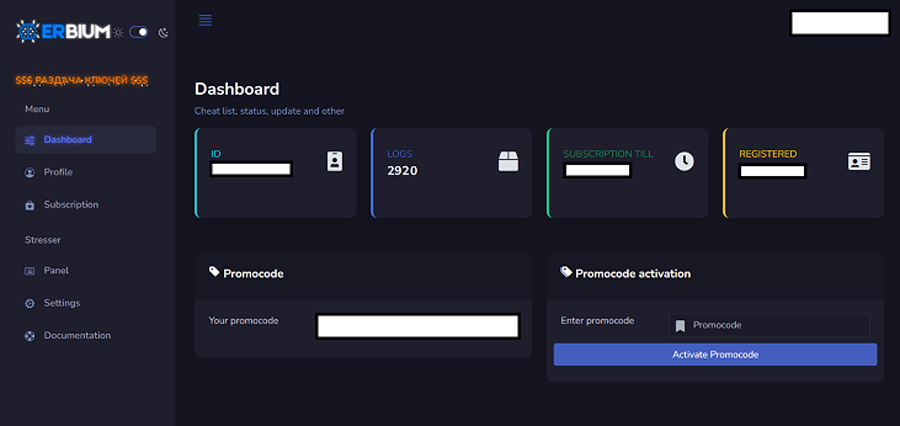
The malware uses three URLs to connect to this panel, including the content delivery network (CDN) Discord, which is generally heavily abused by malware operators.
How to avoid infection
The best and most effective way to avoid such malware is, of course, not to download illegally hacked games, cracks and various bots. So far, the malware penetrates victim systems mainly through launching files from torrents and file hosting sites. Another way is to make sure that you have a good antivirus and it is updated (the first patches from Erbium are promised in a few days). It is also recommended to conduct a preventive scan of your computer for viruses and malware to make sure that nothing new has been introduced in recent days.Even if you haven’t downloaded or launched anything from torrents, you shouldn’t relax. Most likely, the malware will be distributed through other methods, if they have not already started. Several thousand attackers are already working with it; it is a fairly widespread phenomenon. According to DuskRise, the malware was detected during numerous attacks on targets located in the USA, Colombia, France, India, Italy, Malaysia, Lebanon, Portugal, Romania, Spain, Turkey and Vietnam.
