Man
Professional
- Messages
- 3,222
- Reaction score
- 1,215
- Points
- 113

There is a common misconception among ordinary users that the microphone can be turned off by pressing a button in the program. Of course, this is not true. The only way to reliably turn it off is to disconnect the physical electrical circuit that transmits the signal or supplies power. For example, this could be a toggle switch on the motherboard or a button on the microphone itself.
However, nothing prevents the native program from removing sound from the microphone and transmitting it to the server even after pressing the “Mute” button. Some programs do this.
In Windows 10, the VCA audio recording path looks like this.
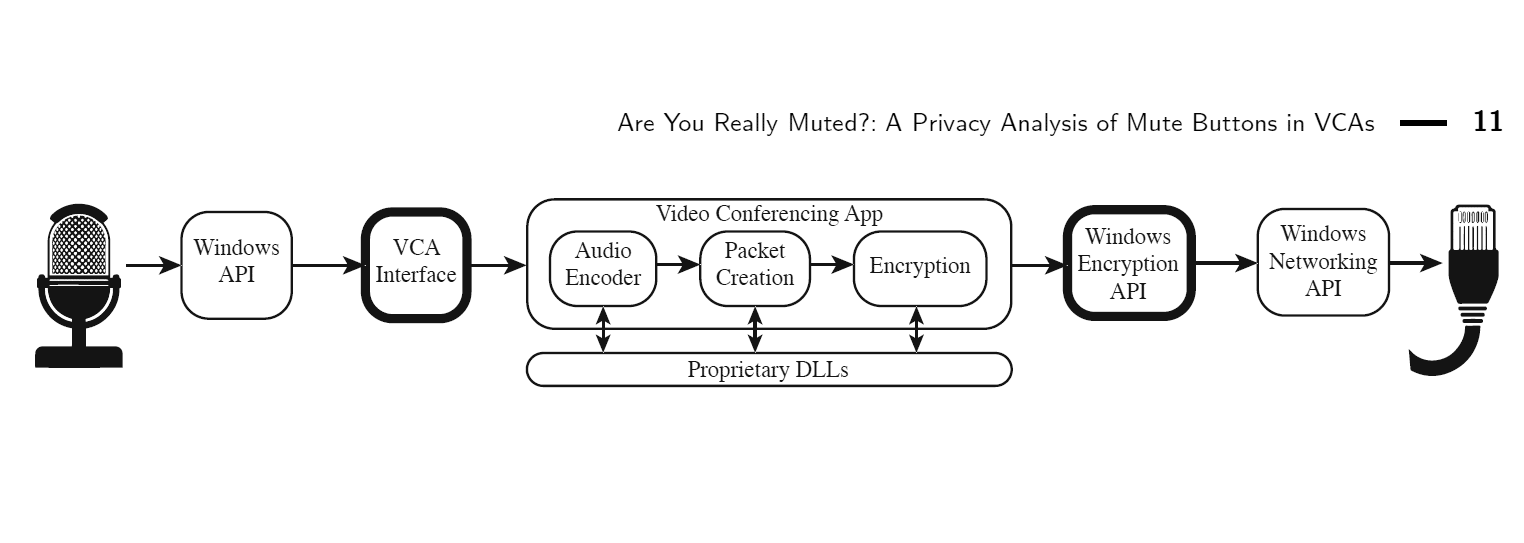
Fig. 1. VCA audio data pipeline in Windows
Last year, engineers from the University of Wisconsin-Madison, together with colleagues from the University of Chicago, experimentally confirmed the hypothesis that teleconferencing programs can record sound after pressing “Mute”.
The specialists tested ten different videoconferencing applications. All of them are divided into two large groups:
- Native clients (Windows, Linux, macOS)
- web clients
Here is a list of the clients studied, including native versions (+/−) and web versions (c). As you can see, one of the Linux clients could not be tested, all the others were tested:
| Application | Windows | Linux | macOS |
|---|---|---|---|
| Zoom (corporate) | + | + | + |
| Slack | + | + | + |
| MS Teams/Skype | + | - | + |
| Google Meet | V | V | V |
| Cisco Webex | + | V | + |
| BlueJeans | + | V | + |
| WhereBy | V | V | + |
| GoToMeeting | + | V | + |
| Jitsi Meet | + | V | + |
| Discord | V | + | V |
One computer had a Logitech QuickCam Pro 9000 webcam installed, and the other had a Logitech C920S Pro HD 1080p webcam.
Traffic interception
The authors of the paper write that intercepting calls from the main process to a proprietary DLL using tools like IDA Pro and x64dbg is not very reliable, because they often cause the application to crash. And since each VCA has its own set of DLLs, it is impossible to set up a standard pipeline for checking all applications. Existing tools like TaintDroid can do this on older versions of Android, but reliable tracing is difficult in native clients for Windows and macOS.
Therefore, data collection hooks were connected to two parts of the data pipeline, which are highlighted in bold in Fig. 1 (in native Windows programs). If we see that after pressing the “Mute” button, data 1) came from the microphone and 2) is sent to the server, this is enough to confirm the original hypothesis.
Information leak
Research results:
- Absolutely all native video conferencing clients retain access to the original audio stream after pressing the “Mute” button.
- Web clients do not have such access due to the implementation of "software mute" in Chromium and WebRTC.
- With the exception of Webex, no VCA abuses access to microphone audio data and sends it to the server. In Mute mode, they only check microphone state flags such as silent, data discontinuityand timestamp error. After the publication of the research paper, Cisco representatives clarified that they remove data from the microphone for the convenience of the user (the “Mute notification” feature), and Webex was fixed in January 2022.
The researchers were also able to prove that involuntary periodic traffic from the microphone after pressing the “Mute” button can be considered a data leak.
Firstly, after pressing the “Mute” button in the background activity mode, most users engage in personal activities, which are accompanied by characteristic sounds. Most often, this is cooking/eating (71%), talking (42%), watching TV (38%), and playing games (22%). Since the sum of the answers is greater than 100%, two or more simultaneous activities are possible. Full survey results are here .
Secondly, the experimenters were able to recognize a person’s occupation based on fragments of data obtained from the VCA sound recording path after pressing the “Mute” button. Fig. 2 shows that different types of activity are clearly distinguished in 3D space, the axes of which show the indicators audioMaxGain, audioMeanGainand audioMinGain.
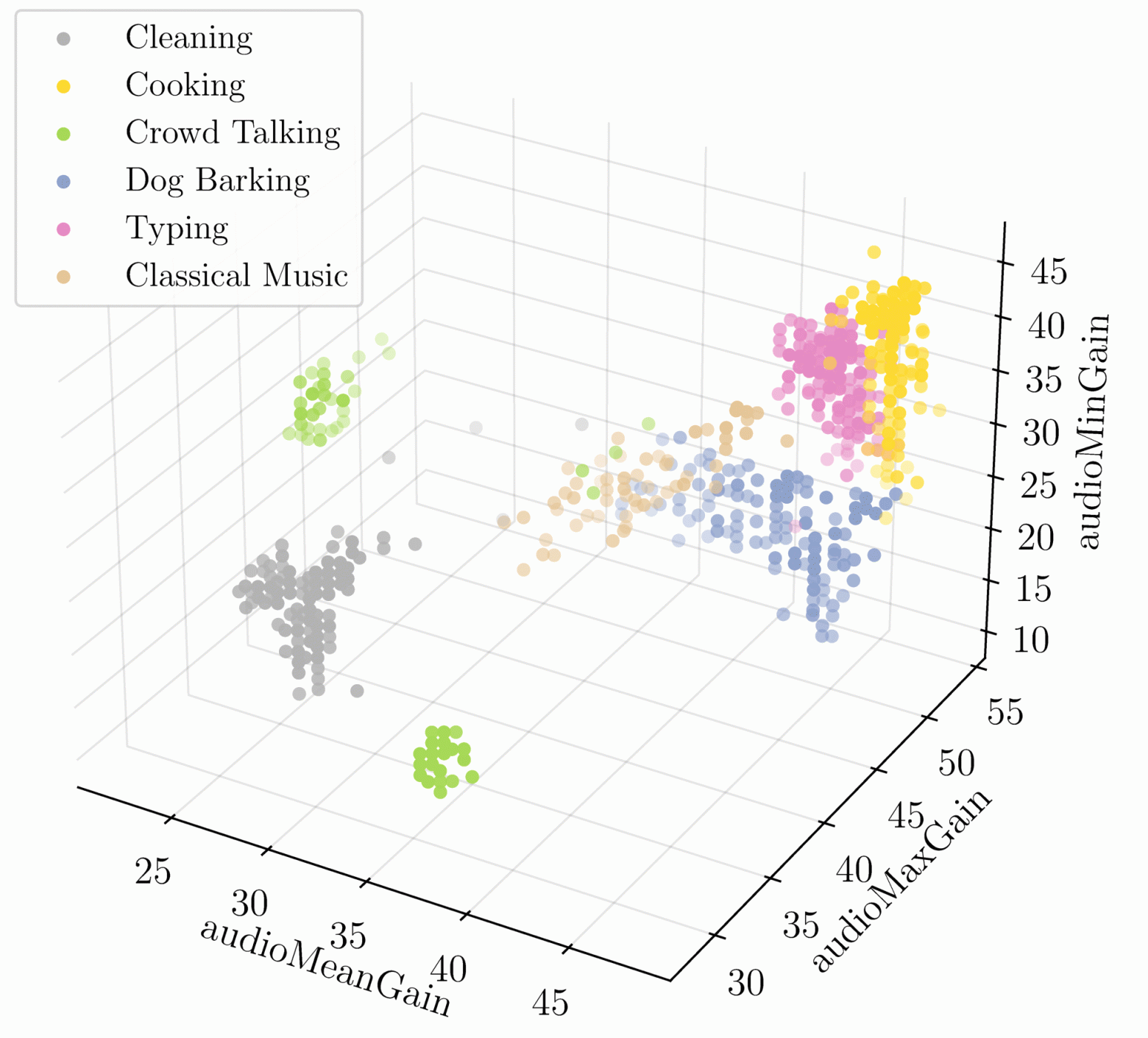
Fig. 2
In connection with this topic, we can recall the words of former NSA contractor Snowden: after buying a new smartphone, he always disassembles it and desolders the tiny microphones on the motherboard (on the KDPV, a photo taken by Edward).
Of course, not everyone needs such security measures. But all users should keep in mind that the microphone of a smartphone, laptop or webcam on a desktop cannot be disabled by software.
The authors believe that the simplest technical solution is a “software mute”, similar to that implemented in Chromium and WebRTC. For example, an indicator in the corner of the screen with a crossed-out microphone icon, meaning that traffic from the microphone driver to the VCA is blocked at the operating system level. In this case, unauthorized wiretapping is possible only after hacking the OS, and not by standard VCA tools, as is now the case.
Source
