Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,096
- Points
- 113
Your device can be hacked via SMS message.
A serious security threat to users of Apple devices has been discovered on one of the hacker forums. A hacker under the pseudonym KeeperZed has introduced a new 0-day exploit of the ZeroClick type, targeting iOS versions 17.xx and 18.xx. This exploit falls into the Remote Code Execution (RCE) category and is distributed via SMS, which makes it particularly dangerous as it does not require any user interaction to activate.
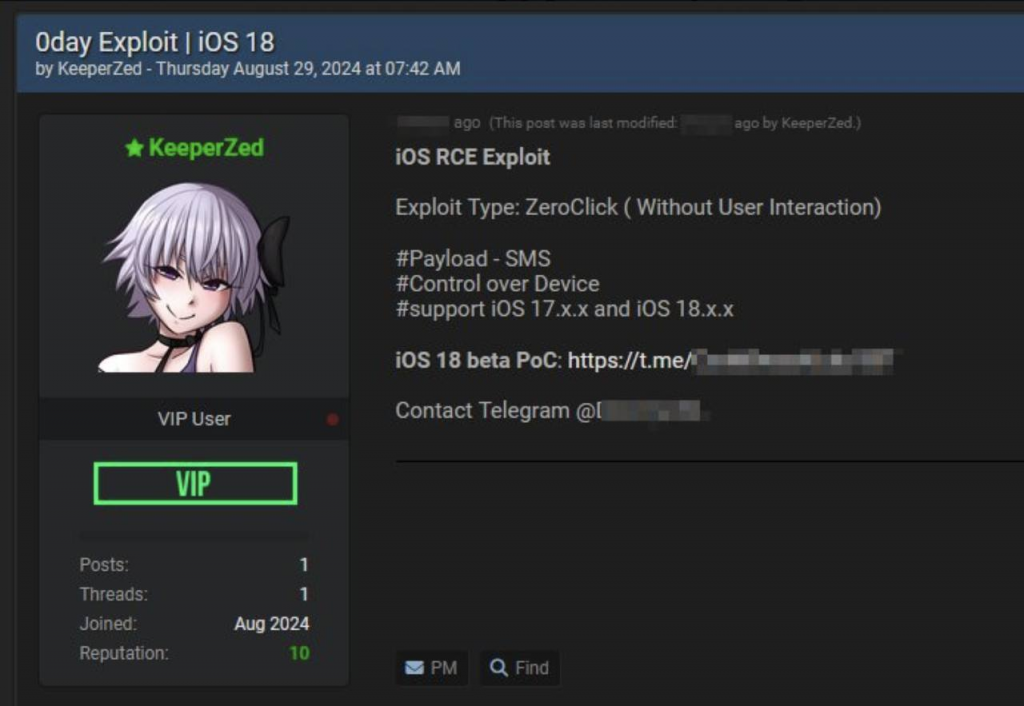
This exploit allows attackers to gain full control over the victim's device, which opens up wide opportunities for espionage, data theft, and the installation of additional malware. Of particular concern is the fact that the vulnerability works on the latest versions of iOS, bypassing existing protections. KeeperZed invites potential buyers to familiarize themselves with the Proof of Concept (PoC) via Telegram, which indicates a willingness to sell the exploit to interested parties.
It is worth noting that in the shadow market, such exploits can cost several million dollars, which reflects the high demand for these tools. Stakeholders can include both government agencies and private companies specializing in the development of targeted surveillance tools. A well-known example of the use of such vulnerabilities is the Pegasus software created by the NSO Group.
Such tools potentially allow unauthorized access to sensitive data on the device, including messages, photos, and location information, without the owner's knowledge. This poses a serious threat to the privacy and security of iOS users.
This situation once again highlights the constant challenges in the field of mobile cybersecurity. Despite the best efforts of manufacturers to protect their products, cybercriminals continue to find ways to bypass protection mechanisms. Users are therefore advised to regularly update their device software, use additional security tools, and be vigilant when receiving suspicious messages.
Mobile device manufacturers, in turn, continue to work on strengthening protective mechanisms, but the threat of new exploits remains relevant. This news serves as a reminder of the importance of continuous improvement of security measures on the part of both developers and users.
Source
A serious security threat to users of Apple devices has been discovered on one of the hacker forums. A hacker under the pseudonym KeeperZed has introduced a new 0-day exploit of the ZeroClick type, targeting iOS versions 17.xx and 18.xx. This exploit falls into the Remote Code Execution (RCE) category and is distributed via SMS, which makes it particularly dangerous as it does not require any user interaction to activate.

This exploit allows attackers to gain full control over the victim's device, which opens up wide opportunities for espionage, data theft, and the installation of additional malware. Of particular concern is the fact that the vulnerability works on the latest versions of iOS, bypassing existing protections. KeeperZed invites potential buyers to familiarize themselves with the Proof of Concept (PoC) via Telegram, which indicates a willingness to sell the exploit to interested parties.
It is worth noting that in the shadow market, such exploits can cost several million dollars, which reflects the high demand for these tools. Stakeholders can include both government agencies and private companies specializing in the development of targeted surveillance tools. A well-known example of the use of such vulnerabilities is the Pegasus software created by the NSO Group.
Such tools potentially allow unauthorized access to sensitive data on the device, including messages, photos, and location information, without the owner's knowledge. This poses a serious threat to the privacy and security of iOS users.
This situation once again highlights the constant challenges in the field of mobile cybersecurity. Despite the best efforts of manufacturers to protect their products, cybercriminals continue to find ways to bypass protection mechanisms. Users are therefore advised to regularly update their device software, use additional security tools, and be vigilant when receiving suspicious messages.
Mobile device manufacturers, in turn, continue to work on strengthening protective mechanisms, but the threat of new exploits remains relevant. This news serves as a reminder of the importance of continuous improvement of security measures on the part of both developers and users.
Source

