Man
Professional
- Messages
- 3,222
- Reaction score
- 1,216
- Points
- 113
Forensics leader GrayKey loses full access to iPhone.
The GrayKey phone unlocking and digital forensics tool is no longer capable of extracting full data from iPhones running on iOS 18 and iOS 18.0.1. This became known thanks to the leak of internal documents of Magnet Forensics, which owns GrayKey. Documents obtained by 404 Media detail GrayKey's capabilities and show that for modern devices, the tool provides only partial access to data.
According to the materials, GrayKey can extract data from the iPhone 12 to the latest iPhone 16 series on iOS 18.0 and iOS 18.0.1, but the data is limited to only partial access. Details about the types of information being exfiltrated are not disclosed, however, as previously reported, "partial access" can only include unencrypted files and metadata such as file sizes and folder structures.
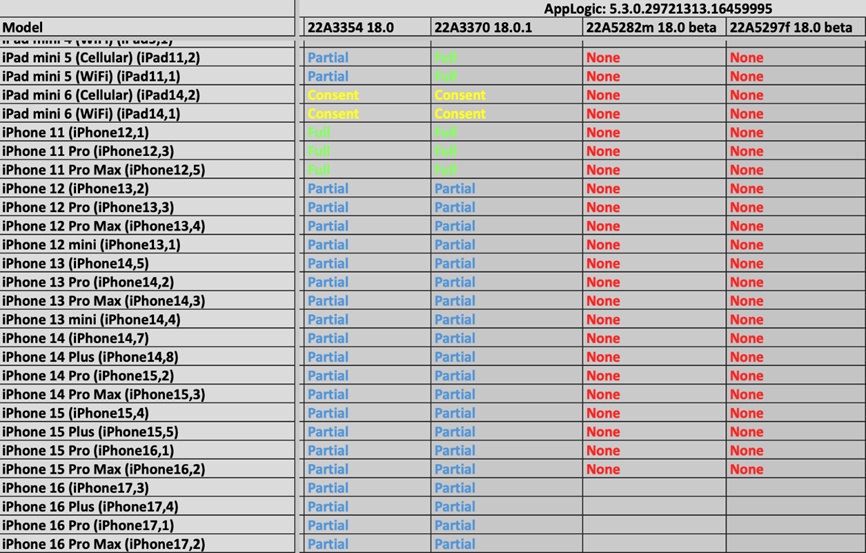
Screenshot of one of the documents demonstrating the capabilities of Graykey on iPhones running iOS 18.0 and 18.0.1
Against the backdrop of the leak, you can see the confrontation between the companies developing digital forensics tools and the manufacturers of mobile devices - Apple and Google. In particular, Apple has strengthened security measures with the release of iOS 18, which has made it difficult to access devices even for powerful tools like GrayKey.
The documents also show that GrayKey is virtually powerless against iPhones running iOS 18.1 betas. The reasons for this are unknown: perhaps the developers of Magnet simply did not have time to adapt their technologies or Apple has implemented serious improvements in the security system.
Android devices remain another area of work for the GrayKey, but the variety of versions leads to mixed results. For example, for the latest Google Pixel models, the tool only provides partial access, especially in the After First Unlock (AFU) state, when the device has already been unlocked at least once after turning it on.
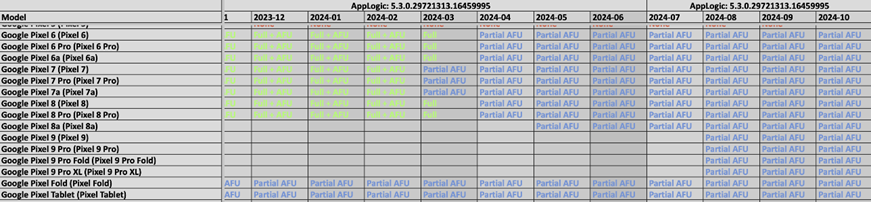
Screenshot of one of the documents demonstrating Graykey's capabilities compared to Google Pixel phones
The documents also mention the term "AppLogic", which is used by Magnet Forensics. The term describes the internal mechanisms of the company's tools, but details about it are available only through closed resources.
It is worth noting that similar leaks previously occurred at Magnet's competitor, Cellebrite. The documents pointed to Cellebrite's inability to extract data from many modern iPhones. However, over time, the company manages to find new vulnerabilities, which confirms the ongoing confrontation between the developers of forensic tools and smartphone manufacturers.
This situation underscores the current status quo in the issue of data security: companies are developing new hacking methods, Apple and Google are quickly closing the vulnerabilities they find, and the cycle continues. Apple, Google, and Magnet Forensics declined to comment on the leak. Meanwhile, experts point out that such tools continue to be used by law enforcement agencies to work with digital evidence, despite the growing difficulty of accessing data.
In June 2021, instructions were revealed revealing how law enforcement officials hack iPhones. The documents described unlocking turned off or discharged iPhones.
Source
The GrayKey phone unlocking and digital forensics tool is no longer capable of extracting full data from iPhones running on iOS 18 and iOS 18.0.1. This became known thanks to the leak of internal documents of Magnet Forensics, which owns GrayKey. Documents obtained by 404 Media detail GrayKey's capabilities and show that for modern devices, the tool provides only partial access to data.
According to the materials, GrayKey can extract data from the iPhone 12 to the latest iPhone 16 series on iOS 18.0 and iOS 18.0.1, but the data is limited to only partial access. Details about the types of information being exfiltrated are not disclosed, however, as previously reported, "partial access" can only include unencrypted files and metadata such as file sizes and folder structures.

Screenshot of one of the documents demonstrating the capabilities of Graykey on iPhones running iOS 18.0 and 18.0.1
Against the backdrop of the leak, you can see the confrontation between the companies developing digital forensics tools and the manufacturers of mobile devices - Apple and Google. In particular, Apple has strengthened security measures with the release of iOS 18, which has made it difficult to access devices even for powerful tools like GrayKey.
The documents also show that GrayKey is virtually powerless against iPhones running iOS 18.1 betas. The reasons for this are unknown: perhaps the developers of Magnet simply did not have time to adapt their technologies or Apple has implemented serious improvements in the security system.
Android devices remain another area of work for the GrayKey, but the variety of versions leads to mixed results. For example, for the latest Google Pixel models, the tool only provides partial access, especially in the After First Unlock (AFU) state, when the device has already been unlocked at least once after turning it on.

Screenshot of one of the documents demonstrating Graykey's capabilities compared to Google Pixel phones
The documents also mention the term "AppLogic", which is used by Magnet Forensics. The term describes the internal mechanisms of the company's tools, but details about it are available only through closed resources.
It is worth noting that similar leaks previously occurred at Magnet's competitor, Cellebrite. The documents pointed to Cellebrite's inability to extract data from many modern iPhones. However, over time, the company manages to find new vulnerabilities, which confirms the ongoing confrontation between the developers of forensic tools and smartphone manufacturers.
This situation underscores the current status quo in the issue of data security: companies are developing new hacking methods, Apple and Google are quickly closing the vulnerabilities they find, and the cycle continues. Apple, Google, and Magnet Forensics declined to comment on the leak. Meanwhile, experts point out that such tools continue to be used by law enforcement agencies to work with digital evidence, despite the growing difficulty of accessing data.
In June 2021, instructions were revealed revealing how law enforcement officials hack iPhones. The documents described unlocking turned off or discharged iPhones.
Source
