Man
Professional
- Messages
- 3,225
- Reaction score
- 1,014
- Points
- 113

LTE Base Station
There are many instructions on the Internet on how to equip your own LTE station. 4G networks are becoming a mass and accessible infrastructure for data transmission. And it is important to understand what security threats exist in this area, how to intercept and analyze traffic.
Until recently, devices for listening to LTE traffic had limited functionality and could not analyze all service data. However, last year, engineers from the Korea Advanced Institute of Science and Technology (KAIST) published the source code of the world's first open-source sniffer LTESniffer with a full set of functionality, including decoding PDCCH and PDSCH traffic.
History of LTE sniffers and how to use them
An LTE sniffer passively intercepts wireless traffic from 4G base station subscribers. Due to the nature of LTE traffic transmission, anyone with the appropriate equipment can intercept these signals. By simulating the behavior of user equipment (such as a smartphone) and a base station, the sniffer decodes the downlink and uplink trace. Unlike regular smartphones, which only decode their own trace, the sniffer decodes all available traces on the air, including plaintext and some service packets. Of course, it is not able to decrypt encrypted traffic from a client device, but it can still extract some information from there.
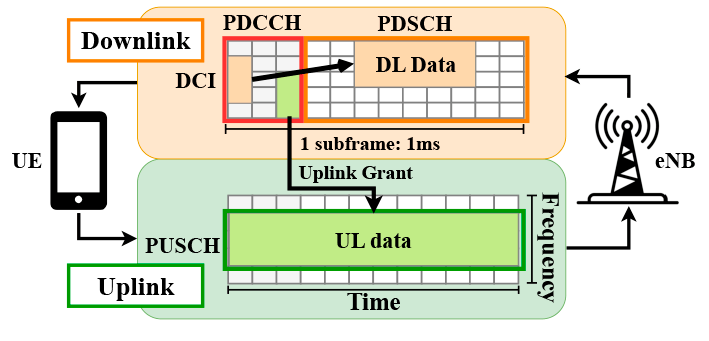
LTE Physical Layer
The scope of LTE sniffers use by attackers and security specialists is described in detail in the literature:
- tracking of mobile phone user IDs, i.e. monitoring specific users or devices;
- determining the presence or precise location of specific users;
- Identifying videos watched by LTE users and website addresses [1, 2]
- recording telephone conversations ;
- Monitor the number of users and network bandwidth (useful for debugging and optimizing networks).
The last task (network analytics) is the main reason why engineers develop and use sniffers.
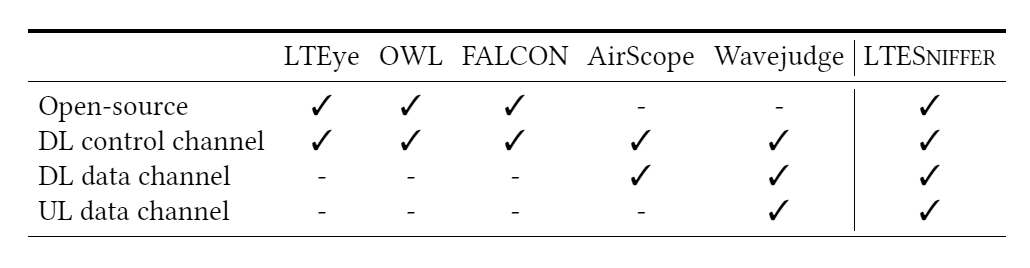
Several sniffers have been implemented in previous years, but almost all of them are limited to decoding the downlink control channel (PDCCH). They do not listen to IP packets or connection control protocol packets between the device and the cellular network (e.g. RRC and NAS). The first attempt at decoding the DL channel was LTEye, which had basic network monitoring functions. Later came OWL and FALCON. There are also three commercial sniffers, Wavejudge, ThinkRF, and AirScope, that can decode data channels. The first two decode both DL and UL, but they are difficult to use due to their high price (from $25,000 for Wavejudge). The most popular commercial sniffer in scientific circles is AirScope, but it does not decode UL traffic and its performance leaves much to be desired (see below). In addition, commercial programs are closed source, so they are not easy to modify and add new features.
The aforementioned LTESniffer from Korean specialists is the world's first open source LTE sniffer that passively decodes data in the uplink and downlink channels. Crucial to its operation is obtaining information about all subscriber devices in order to improve the accuracy of data decoding, especially in high-bandwidth scenarios. The main functions in the program are implemented using the open source srsRAN package. The paper "LTESniffer: An Open Source Eavesdropper for LTE Downlink/Uplink" was prepared for the 16th ACM WiSec 2023 Conference.
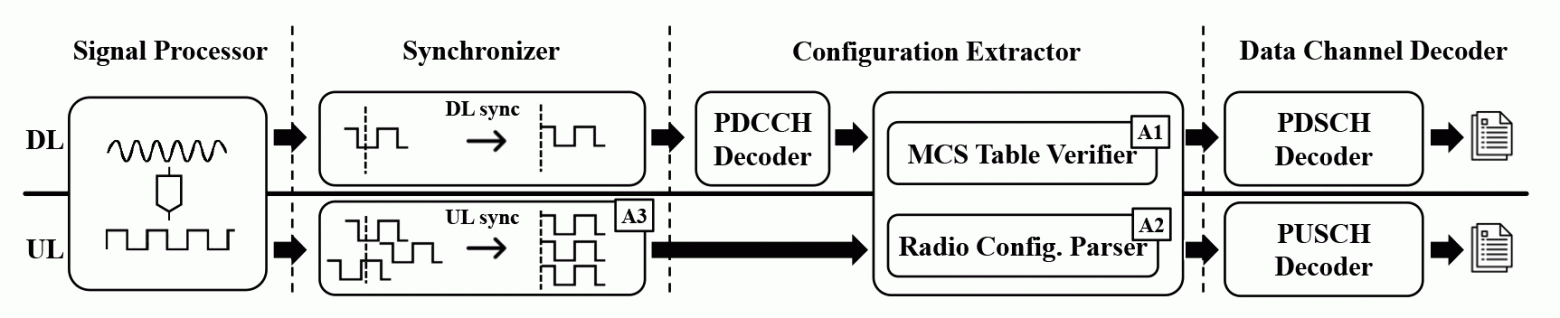
LTESniffer Architecture
The implementation of LTESniffer is not very trivial, since it is necessary to understand the detailed configurations and parameters to successfully decode each user's traffic. Using various methods, the authors found a way to improve the decoding performance. The following chart shows that LTESniffer dramatically outperforms AirScope in decoding speed:
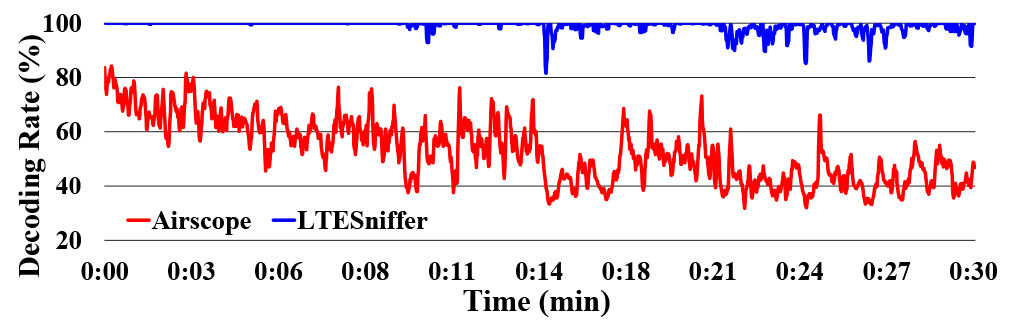
Subframe decoding speed during peak load, compared to AirScope
LTESniffer compares favorably with other LTE sniffers. As mentioned, it is essentially the only open source system that monitors both data channels (DL/UL) and controls transmission:
The program decodes the physical Downlink Control Channel (PDCCH) to obtain the Downlink Control Information (DCIs) and Radio Network Temporary Identifiers (RNTIs) of all active users. Using the decoded DCIs and RNTIs, LTESniffer then decodes the Physical Downlink Shared Channel (PDSCH) and Physical Uplink Shared Channel (PUSCH) to obtain the uplink and downlink data traffic.
LTESniffer supports an API with three functions: ID matching, IMSI collection, and profiling.
System requirements
LTESniffer currently works stably on Ubuntu 18.04/20.04/22.04.
Decoding real-time traffic requires a high-performance CPU with multiple cores, especially during peak loads when the base station has many active users.
LTESniffer successfully decoded real-time traffic from a base station with 150 active users on an Intel i7-9700K.
Recommended configuration:
- CPU Intel i7 with at least 8 physical cores
- At least 16 GB RAM
- SSD 256GB
- Software Defined Radio SDR
LTESniffer is compatible with different SDRs for uplink and downlink.
For single downlink traffic from the base station, most SDRs supported by the srsRAN library (e.g. USRP or BladeRF) can be used. The SDR must be connected to the PC via USB 3.0. Additionally, decoding downlink messages in TX Modes 3 and 4 requires a GPSDO and two RX antennas.
In UL+DL listening mode, two frequencies must be processed simultaneously, which can be achieved with the more professional USRP X310 (costs about $9100) or two USRP B-Series.
Thus, for effective monitoring of the cellular network, tracking users and analyzing network traffic, it is no longer necessary to buy an expensive license for commercial software. All this is available in an open source package.
Source
