Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
Soon the world will see new ransomware operations with many branches of software.
The full source code for the first version of the HelloKitty ransomware was recently posted on a cybercrime forum. The participant who posted the data announced the development of a new, more powerful cryptographer.
The source code was discovered by a cybersecurity researcher under the pseudonym "3xp0rt". He found out that the archive with the code of the sixth of October was posted by a hacker under the pseudonym "kapuchin0", which is also known online as"Gookee".
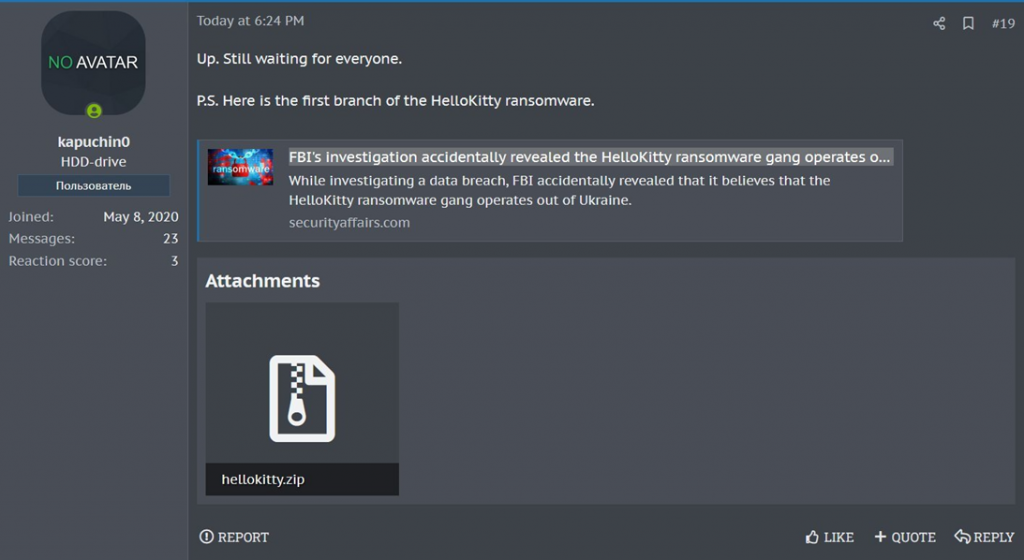
Posting "kapuchin0" on a cybercrime forum
Gookee has previously been linked to fraudulent activity. It offered access to Sony Network Japan in 2020, tried to sell malware source codes, and even provided its own RaaS service called " Gooke Ransomware."
Apparently, kapuchin0/Gookee is the direct developer of the HelloKitty cryptographer and is currently preparing a new product, which, according to him, will be much more interesting than the sensational Lockbit.
Published hellokitty archive.The zip contains a ready-made Microsoft Visual Studio solution that creates the HelloKitty cryptographer and decryptor, as well as the NTRUEncrypt library used by this version of malware to encrypt files.
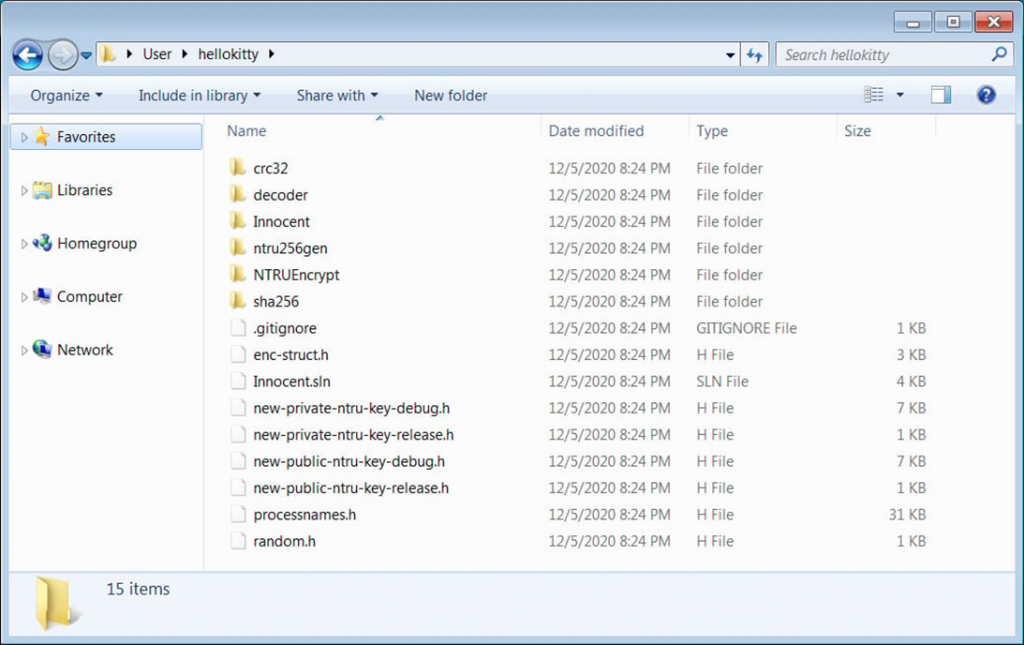
Contents of the published archive
Michael Gillespie, a ransomware expert, confirmed that this is the valid source code for HelloKitty, which was used when the operation was launched in 2020.
Although releasing the source code of a ransomware program to the public can potentially be useful for security research, this event still has more disadvantages than advantages. As a rule, cybercriminals quickly adapt open source code to their needs and create dozens of branches from a particular malware, launching their own malicious operations.
Operation HelloKitty has been active since November 2020 and is well known for its attacks on corporate networks, data theft, and system encryption. The most famous attack using this cryptographer was made on the Polish company CD Projekt Red in February 2021, when attackers publicly announced the theft of the source code of various games of the studio.
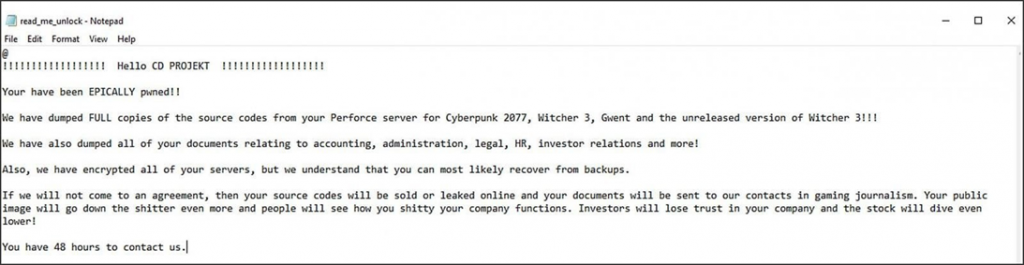
Personal note for CD Projekt Red from HelloKitty hackers
The HelloKitty ransomware and its variants have also been used under other names, including DeathRansom, Fivehands, and possibly Abyss Locker.
The Federal Bureau of Investigation (FBI) even distributed a detailed list of compromise indicators at the end of October 2021 to help cybersecurity specialists detect HelloKitty, but this data may have become outdated over time.
The full source code for the first version of the HelloKitty ransomware was recently posted on a cybercrime forum. The participant who posted the data announced the development of a new, more powerful cryptographer.
The source code was discovered by a cybersecurity researcher under the pseudonym "3xp0rt". He found out that the archive with the code of the sixth of October was posted by a hacker under the pseudonym "kapuchin0", which is also known online as"Gookee".

Posting "kapuchin0" on a cybercrime forum
Gookee has previously been linked to fraudulent activity. It offered access to Sony Network Japan in 2020, tried to sell malware source codes, and even provided its own RaaS service called " Gooke Ransomware."
Apparently, kapuchin0/Gookee is the direct developer of the HelloKitty cryptographer and is currently preparing a new product, which, according to him, will be much more interesting than the sensational Lockbit.
Published hellokitty archive.The zip contains a ready-made Microsoft Visual Studio solution that creates the HelloKitty cryptographer and decryptor, as well as the NTRUEncrypt library used by this version of malware to encrypt files.

Contents of the published archive
Michael Gillespie, a ransomware expert, confirmed that this is the valid source code for HelloKitty, which was used when the operation was launched in 2020.
Although releasing the source code of a ransomware program to the public can potentially be useful for security research, this event still has more disadvantages than advantages. As a rule, cybercriminals quickly adapt open source code to their needs and create dozens of branches from a particular malware, launching their own malicious operations.
Operation HelloKitty has been active since November 2020 and is well known for its attacks on corporate networks, data theft, and system encryption. The most famous attack using this cryptographer was made on the Polish company CD Projekt Red in February 2021, when attackers publicly announced the theft of the source code of various games of the studio.

Personal note for CD Projekt Red from HelloKitty hackers
The HelloKitty ransomware and its variants have also been used under other names, including DeathRansom, Fivehands, and possibly Abyss Locker.
The Federal Bureau of Investigation (FBI) even distributed a detailed list of compromise indicators at the end of October 2021 to help cybersecurity specialists detect HelloKitty, but this data may have become outdated over time.

