Lord777
Professional
- Messages
- 2,578
- Reaction score
- 1,532
- Points
- 113
An experiment by GoSecure showed how hackers work and the servers of which countries they use.
Remote Desktop Protocol (RDP) it attracts hackers so much that an open connection can receive an average of more than 37,000 hacking attempts per day from different IP addresses.
An experiment using decoys (honeypots) with an RDP connection accessible from the Internet shows how persistent the attackers are and that they work on a schedule very similar to a normal working day.
GoSecure said that the decoys are a research program aimed at understanding hackers strategies, which could be translated into recommendations for preventing threats.
Within three months, researchers from the information security company GoSecure recorded about 3.5 million attempts to log in to their honeypot with RDP.
The honeypot has been running intermittently for more than 3 years and has been stable for more than a year, but the data collected covers only 3 months - from July 1 to September 30, 2022. During this period, the decoy was attacked 3,427,611 times from more than 1,500 IP addresses. However, the number of attacks for the entire year reached 13 million login attempts.
To attract attackers, the researchers named the system so that it appeared to be part of the banking network.
As expected, the attackers used the brute force method, and the most common username was "Administrator" and its variations. In 60,000 hacks, attackers conducted reconnaissance before selecting a username.
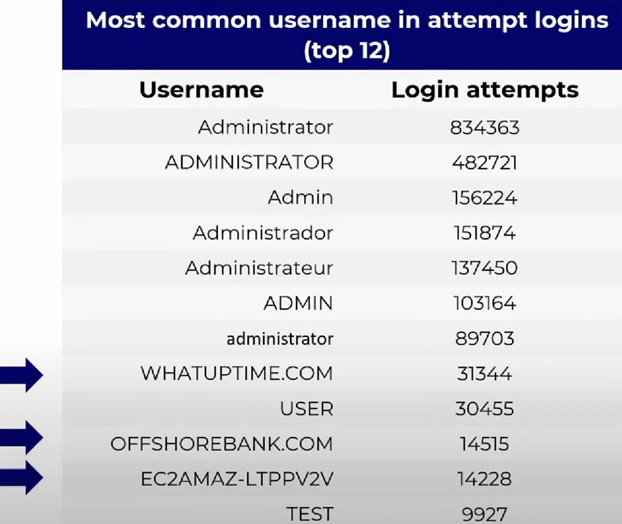
The most common user logins in malicious searches
The honeypot system collected password hashes, and researchers were able to recover the weaker ones. The most common passwords are different versions of the word "password" and a simple string of ten digits.
Notably, login attempts came from IP addresses in China (98%) and Russia (2%). However, this does not mean that the attackers are located in these countries. Hackers are probably using the infrastructure in these countries. In addition, 15% of attackers combined thousands of passwords with only 5 usernames.
Human involvement in the attack became more apparent after the initial stage of brute-forcing passwords, when hackers began searching the system for valuable data.
Despite the fact that the researchers lowered the difficulty of logging into the honeypot with a pair of "admin/admin" credentials, only 25% of hackers began to explore the machine in search of important files. However, the bait originally didn't contain any data. In the future, experts plan to fill in the honeypot with fake corporate files and implement a system for tracking the actions of attackers.
Remote Desktop Protocol (RDP) it attracts hackers so much that an open connection can receive an average of more than 37,000 hacking attempts per day from different IP addresses.
An experiment using decoys (honeypots) with an RDP connection accessible from the Internet shows how persistent the attackers are and that they work on a schedule very similar to a normal working day.
GoSecure said that the decoys are a research program aimed at understanding hackers strategies, which could be translated into recommendations for preventing threats.
Within three months, researchers from the information security company GoSecure recorded about 3.5 million attempts to log in to their honeypot with RDP.
The honeypot has been running intermittently for more than 3 years and has been stable for more than a year, but the data collected covers only 3 months - from July 1 to September 30, 2022. During this period, the decoy was attacked 3,427,611 times from more than 1,500 IP addresses. However, the number of attacks for the entire year reached 13 million login attempts.
To attract attackers, the researchers named the system so that it appeared to be part of the banking network.
As expected, the attackers used the brute force method, and the most common username was "Administrator" and its variations. In 60,000 hacks, attackers conducted reconnaissance before selecting a username.

The most common user logins in malicious searches
The honeypot system collected password hashes, and researchers were able to recover the weaker ones. The most common passwords are different versions of the word "password" and a simple string of ten digits.
Notably, login attempts came from IP addresses in China (98%) and Russia (2%). However, this does not mean that the attackers are located in these countries. Hackers are probably using the infrastructure in these countries. In addition, 15% of attackers combined thousands of passwords with only 5 usernames.
Human involvement in the attack became more apparent after the initial stage of brute-forcing passwords, when hackers began searching the system for valuable data.
Despite the fact that the researchers lowered the difficulty of logging into the honeypot with a pair of "admin/admin" credentials, only 25% of hackers began to explore the machine in search of important files. However, the bait originally didn't contain any data. In the future, experts plan to fill in the honeypot with fake corporate files and implement a system for tracking the actions of attackers.
