Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Even hackers themselves are not protected from virus infection.
Cybersecurity specialists are increasingly obtaining information about suspected criminals from unexpected sources – a huge amount of compromised credentials, browser profiles, and other system information available on Telegram. Attackers themselves are trapped by infecting their devices with malware, which in turn reveals their identities to researchers and law enforcement.
So, last week, Hudson Rock announced that it had found data on two alleged fraudsters - Mujtab Raz and Mohsin Raz, who are listed on the FBI's most wanted list. In April 2021, US authorities charged the men with conspiracy to produce and transmit forged documents, as well as fraud using fake IDs.
According to investigators, the men operated an illegal online business called SecondEye Solution, which was based in Karachi, Pakistan. The company sold digital copies of fake passports, driver's licenses, and national licenses to more than 200 countries. The criminals advertised their activities on hacker forums.
After the charges were brought, Mujtaba and Mohsin went into hiding and have been wanted ever since. However, Hudson Rock was able to obtain information about them using data collected through infostealers. Such programs infect computers by collecting credentials and other information, which then often ends up in the public domain on Telegram. Among the common infostealers mentioned are RedLine, Raccoon, and Erbium, which are often distributed through fake programs, cryptocurrency wallets, or pirated software.
Among the information found were accounts associated with SecondEye, as well as cloud storage linked to the same accounts. Of particular interest were the browser logs from the infected device, which contained information about the history of visiting sites, autofill with addresses and passport numbers, as well as IP addresses and computer names. One of the screenshots taken by the malware captured the moment of using a Skype account branded by Forwarderz, another company associated with the suspects.
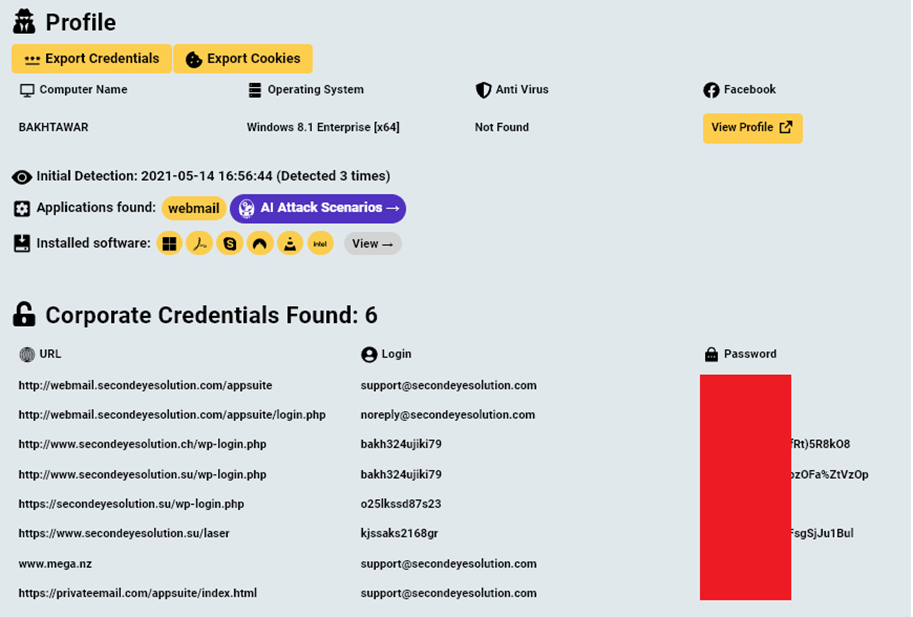
Example of collected data
Hudson Rock believes that the computers do not belong to Mujtaba and Mohsin themselves, but to their alleged accomplices, Muhammad Kamber and Bakhtawar Abbas. However, it was not possible to get comments from accomplices.
The collected data was also implicated in recent leaks that allowed hackers to access information from major companies such as AT&T and Ticketmaster. The results of the investigation were transferred to the FBI and met all the necessary requirements for public disclosure. Neither the FBI nor Hudson Rock itself provided further comment.
Cases of using infostealers to identify criminals are becoming more and more frequent. In July, Recorded Future discovered more than 3,300 unique credentials associated with accessing websites that distribute CSAM material.
Source
Cybersecurity specialists are increasingly obtaining information about suspected criminals from unexpected sources – a huge amount of compromised credentials, browser profiles, and other system information available on Telegram. Attackers themselves are trapped by infecting their devices with malware, which in turn reveals their identities to researchers and law enforcement.
So, last week, Hudson Rock announced that it had found data on two alleged fraudsters - Mujtab Raz and Mohsin Raz, who are listed on the FBI's most wanted list. In April 2021, US authorities charged the men with conspiracy to produce and transmit forged documents, as well as fraud using fake IDs.
According to investigators, the men operated an illegal online business called SecondEye Solution, which was based in Karachi, Pakistan. The company sold digital copies of fake passports, driver's licenses, and national licenses to more than 200 countries. The criminals advertised their activities on hacker forums.
After the charges were brought, Mujtaba and Mohsin went into hiding and have been wanted ever since. However, Hudson Rock was able to obtain information about them using data collected through infostealers. Such programs infect computers by collecting credentials and other information, which then often ends up in the public domain on Telegram. Among the common infostealers mentioned are RedLine, Raccoon, and Erbium, which are often distributed through fake programs, cryptocurrency wallets, or pirated software.
Among the information found were accounts associated with SecondEye, as well as cloud storage linked to the same accounts. Of particular interest were the browser logs from the infected device, which contained information about the history of visiting sites, autofill with addresses and passport numbers, as well as IP addresses and computer names. One of the screenshots taken by the malware captured the moment of using a Skype account branded by Forwarderz, another company associated with the suspects.

Example of collected data
Hudson Rock believes that the computers do not belong to Mujtaba and Mohsin themselves, but to their alleged accomplices, Muhammad Kamber and Bakhtawar Abbas. However, it was not possible to get comments from accomplices.
The collected data was also implicated in recent leaks that allowed hackers to access information from major companies such as AT&T and Ticketmaster. The results of the investigation were transferred to the FBI and met all the necessary requirements for public disclosure. Neither the FBI nor Hudson Rock itself provided further comment.
Cases of using infostealers to identify criminals are becoming more and more frequent. In July, Recorded Future discovered more than 3,300 unique credentials associated with accessing websites that distribute CSAM material.
Source

