Father
Professional
- Messages
- 2,602
- Reaction score
- 786
- Points
- 113
The developers explained what was going on – everything turned out to be much easier.
Telegram has fixed a zero-day vulnerability in its Windows app that allowed it to bypass security warnings and automatically run Python scripts. This was announced by the developers after the spread of rumors and videos demonstrating the vulnerability on various platforms and forums.
According to the original post, a bug in the source code allowed sending ".pyzw " files, which when clicked on would start automatically. Telegram noted that although it was initially reported that there was a vulnerability that allows executing code without clicking on the file, the reality turned out to be different. To exploit the flaw, it was necessary to have the Python interpreter installed and click on the masked file. It is noted that the error could affect only a small proportion of users — less than 0.01%.
The company has applied a server-side fix that allows ".pyzw" files to now receive the ".untrusted " extension, which causes Windows to ask which program to open the file in instead of running it automatically.
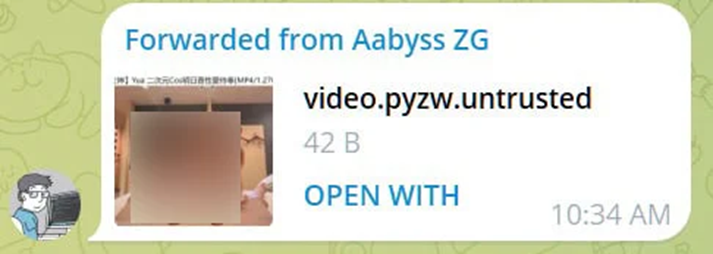
Telegram Server Fix
Using the vulnerability, security researchers disguised the file as an MP4 video using a Telegram bot, which misled users and forced them to run the script. Such actions allowed attackers to execute code remotely on Windows devices.
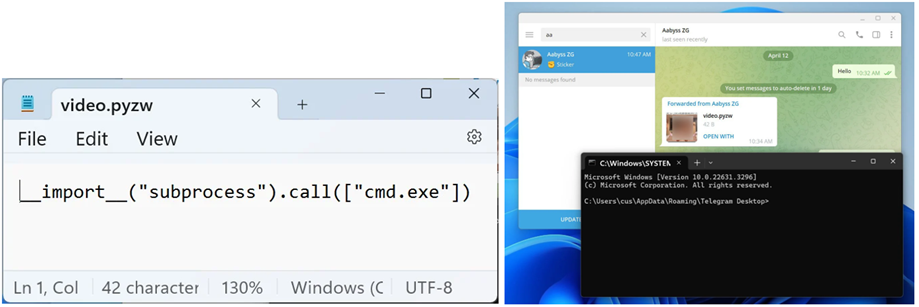
Demonstration of the error when opening the command line
After reporting the flaw on April 10, Telegram developers quickly made changes to the source code, correcting the spelling of the extension in the code file "data_document_resolver.cpp". However, this fix doesn't apply yet, because warnings don't appear when you click a file to run it.
The ".pyzw " extension is intended for Python ZIP applications, which are standalone Python programs contained in ZIP archives. Telegram developers realized that these types of executable files should be considered risky, and added them to the list of executable file extensions. However, when adding the extension, the developers made a typo by entering the extension as "pywz" instead of the correct spelling "pyzw".
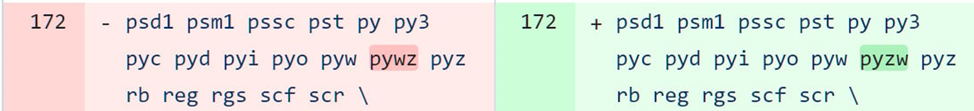
Fix for writing the Python extension ".pyzw"
So when a file was sent via Telegram and the user clicked on it, the Python script automatically ran if it was installed on Windows.
Representatives of Telegram also said that in future versions of the application, it is planned to return security warnings, which will strengthen the protection of users from such attacks.
Telegram has fixed a zero-day vulnerability in its Windows app that allowed it to bypass security warnings and automatically run Python scripts. This was announced by the developers after the spread of rumors and videos demonstrating the vulnerability on various platforms and forums.
According to the original post, a bug in the source code allowed sending ".pyzw " files, which when clicked on would start automatically. Telegram noted that although it was initially reported that there was a vulnerability that allows executing code without clicking on the file, the reality turned out to be different. To exploit the flaw, it was necessary to have the Python interpreter installed and click on the masked file. It is noted that the error could affect only a small proportion of users — less than 0.01%.
The company has applied a server-side fix that allows ".pyzw" files to now receive the ".untrusted " extension, which causes Windows to ask which program to open the file in instead of running it automatically.

Telegram Server Fix
Using the vulnerability, security researchers disguised the file as an MP4 video using a Telegram bot, which misled users and forced them to run the script. Such actions allowed attackers to execute code remotely on Windows devices.

Demonstration of the error when opening the command line
After reporting the flaw on April 10, Telegram developers quickly made changes to the source code, correcting the spelling of the extension in the code file "data_document_resolver.cpp". However, this fix doesn't apply yet, because warnings don't appear when you click a file to run it.
The ".pyzw " extension is intended for Python ZIP applications, which are standalone Python programs contained in ZIP archives. Telegram developers realized that these types of executable files should be considered risky, and added them to the list of executable file extensions. However, when adding the extension, the developers made a typo by entering the extension as "pywz" instead of the correct spelling "pyzw".

Fix for writing the Python extension ".pyzw"
So when a file was sent via Telegram and the user clicked on it, the Python script automatically ran if it was installed on Windows.
Representatives of Telegram also said that in future versions of the application, it is planned to return security warnings, which will strengthen the protection of users from such attacks.
