Brother
Professional
- Messages
- 2,590
- Reaction score
- 526
- Points
- 113
The Terrapin technique allows you to manipulate authentication algorithms.
A group of researchers from the Ruhr University in Bochum has developed a new attack vector called "Terrapin", which is based on manipulating the sequence of numbers during the connection establishment process (handshake).
The Terrapin attack can break the integrity of SSH channels when using popular encryption modes. Using this method, hackers can delete or modify messages in the channel, which leads to a decrease in the security level of the public key algorithms involved in user authentication, as well as disabling protection against attacks based on key press time analysis, which is dangerous for OpenSSH 9.5.
University experts noted that the Terrapin attack exploits vulnerabilities in the SSH protocol along with cryptographic algorithms and encryption modes introduced in OpenSSH more than a decade ago.
The mentioned vulnerabilities related to the new attack vector were identified as CVE-2023-48795, CVE-2023-46445 and CVE-2023-46446.
To perform a Terrapin attack, the attackers must be in a man-in-the-middle (MiTM) position, and the connection must be protected by either ChaCha20-Poly1305 or CBC with Encrypt-then-MAC.
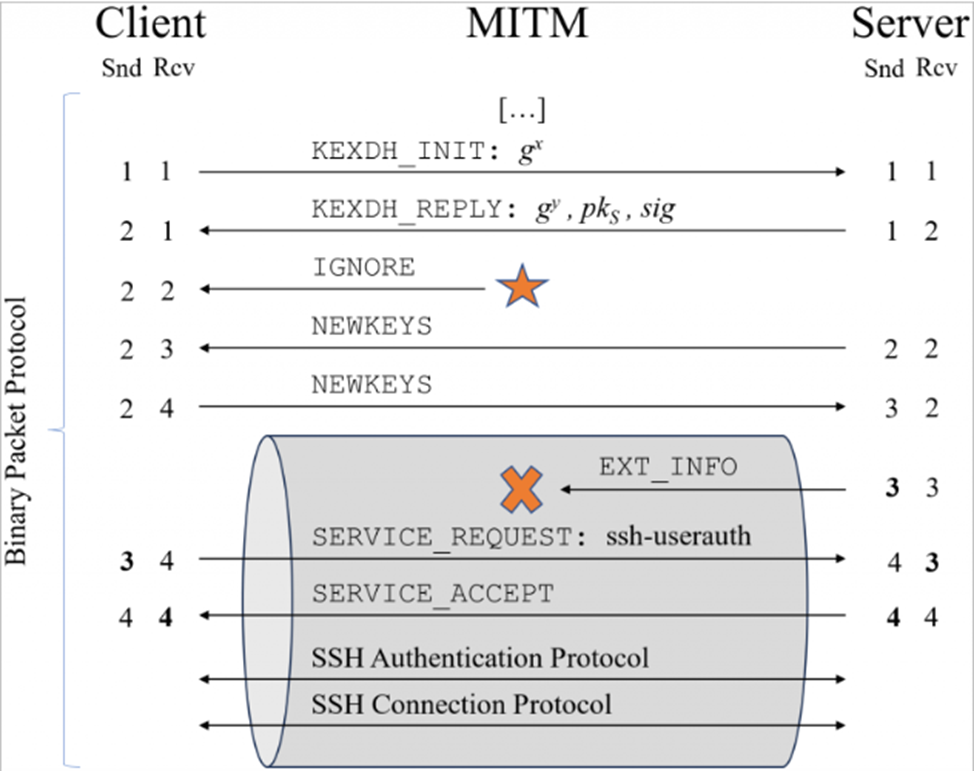
Many manufacturers are already taking steps to mitigate the risks associated with Terrapin operation. The use of strict key exchange, which prevents packets from being introduced during the connection establishment process, is one of the ways to combat this threat. Experts emphasize that to achieve maximum protection, measures must be implemented both on the client and server sides, which will require additional time.
Researchers have developed a specialized Terrapin vulnerability scanner, available on GitHub, which helps determine whether an SSH client or server is susceptible to this vulnerability. A detailed description of the attack and recommendations on how to protect against it are presented in the technical report prepared by experts from the Ruhr University.
A group of researchers from the Ruhr University in Bochum has developed a new attack vector called "Terrapin", which is based on manipulating the sequence of numbers during the connection establishment process (handshake).
The Terrapin attack can break the integrity of SSH channels when using popular encryption modes. Using this method, hackers can delete or modify messages in the channel, which leads to a decrease in the security level of the public key algorithms involved in user authentication, as well as disabling protection against attacks based on key press time analysis, which is dangerous for OpenSSH 9.5.
University experts noted that the Terrapin attack exploits vulnerabilities in the SSH protocol along with cryptographic algorithms and encryption modes introduced in OpenSSH more than a decade ago.
The mentioned vulnerabilities related to the new attack vector were identified as CVE-2023-48795, CVE-2023-46445 and CVE-2023-46446.
To perform a Terrapin attack, the attackers must be in a man-in-the-middle (MiTM) position, and the connection must be protected by either ChaCha20-Poly1305 or CBC with Encrypt-then-MAC.

Many manufacturers are already taking steps to mitigate the risks associated with Terrapin operation. The use of strict key exchange, which prevents packets from being introduced during the connection establishment process, is one of the ways to combat this threat. Experts emphasize that to achieve maximum protection, measures must be implemented both on the client and server sides, which will require additional time.
Researchers have developed a specialized Terrapin vulnerability scanner, available on GitHub, which helps determine whether an SSH client or server is susceptible to this vulnerability. A detailed description of the attack and recommendations on how to protect against it are presented in the technical report prepared by experts from the Ruhr University.
