Man
Professional
- Messages
- 3,223
- Reaction score
- 1,150
- Points
- 113

SSH has become almost a de facto standard for connecting to a server or remote desktop. Therefore, vulnerabilities cause some concern. Especially in the current conditions, when all traffic on the Internet is recorded and stored in the storage of providers and hosters. That is, in the future it can be decrypted if a vulnerability is found that undermines the basic cryptography.
A dangerous vulnerability was found by researchers from the Ruhr University in Bochum. The attack was named Terrapin (CVE-2023-48795). However, it is unlikely to be used on saved traffic, because the MiTM scheme involves selecting values during the handshake between the server and the client. The attacker must have access to the channel and the ability to replace packets.
The practical application of Terrapin is shown in the illustration on the KDPW. We will duplicate here two diagrams from the scientific paper. Below is a normal SSH handshake using the binary packet protocol BPP (SSH2 Binary Packet Protocol) and Diffie-Hellman key exchange with a finite field. Sequence numbers are supported by BPP: Sndis the counter of sent packets, and is the counter Rcvof received packets. Sequence numbers checked by authentication and encryption are highlighted in bold:

And here is how the prefix truncation occurs during an attack on BPP. The server sends SC1 and SC2 packets, and the client receives only SC2:

The KDPW shows that by removing/adding packets, an attacker can remove the message EXT_INFO, which is used to negotiate several protocol extensions, unnoticed by the client and the server. Packet injection at the handshake stage allows for an extension downgrade attack and a lower level of SSH protection. The exact consequences depend on the versions of the software used on the server and client, as well as the extensions used.
The method only works if the ChaCha20-Poly1305 cipher or another cipher in block chaining (CBC) mode in Encrypt-then-MAC encryption mode is used for SSH.
You can use this scanner to check your server and clients for vulnerabilities .
TunnelCrack: Hacking VPN Tunnels
It's not just the SSH protocol that has been under attack lately.
Recall that in August 2023, a dangerous TunnelCrack attack was published that exploits two widespread VPN vulnerabilities (LocalNet and ServerIP). An attacker can use them to extract traffic outside the encrypted VPN tunnel.
Tests showed that all tested VPN services are vulnerable to the vulnerabilities on at least one device, disabling iPhone, iPad, MacBook, as well as most VPNs on Windows and Linux. Android clients turned out to be the most secure - only a quarter of VPN applications are vulnerable. The vulnerabilities discovered can be exploited regardless of the VPN protocol.
Both attacks are used when the user connects to an untrusted Wi-Fi. In addition, the ServerIP attack can be used from the ISP side. During the attack, the malware modifies the routing tables to redirect traffic outside the secure VPN tunnel.
The LocalNet attack works if the victim connects to someone else's hotspot, for example, in a cafe or hotel. There, they are assigned a new IP address. Since most VPN services allow access to the local network while the tunnel is running, traffic can be freely redirected to the local LAN, that is, to the attacker. Testing has shown that all iOS applications are vulnerable.
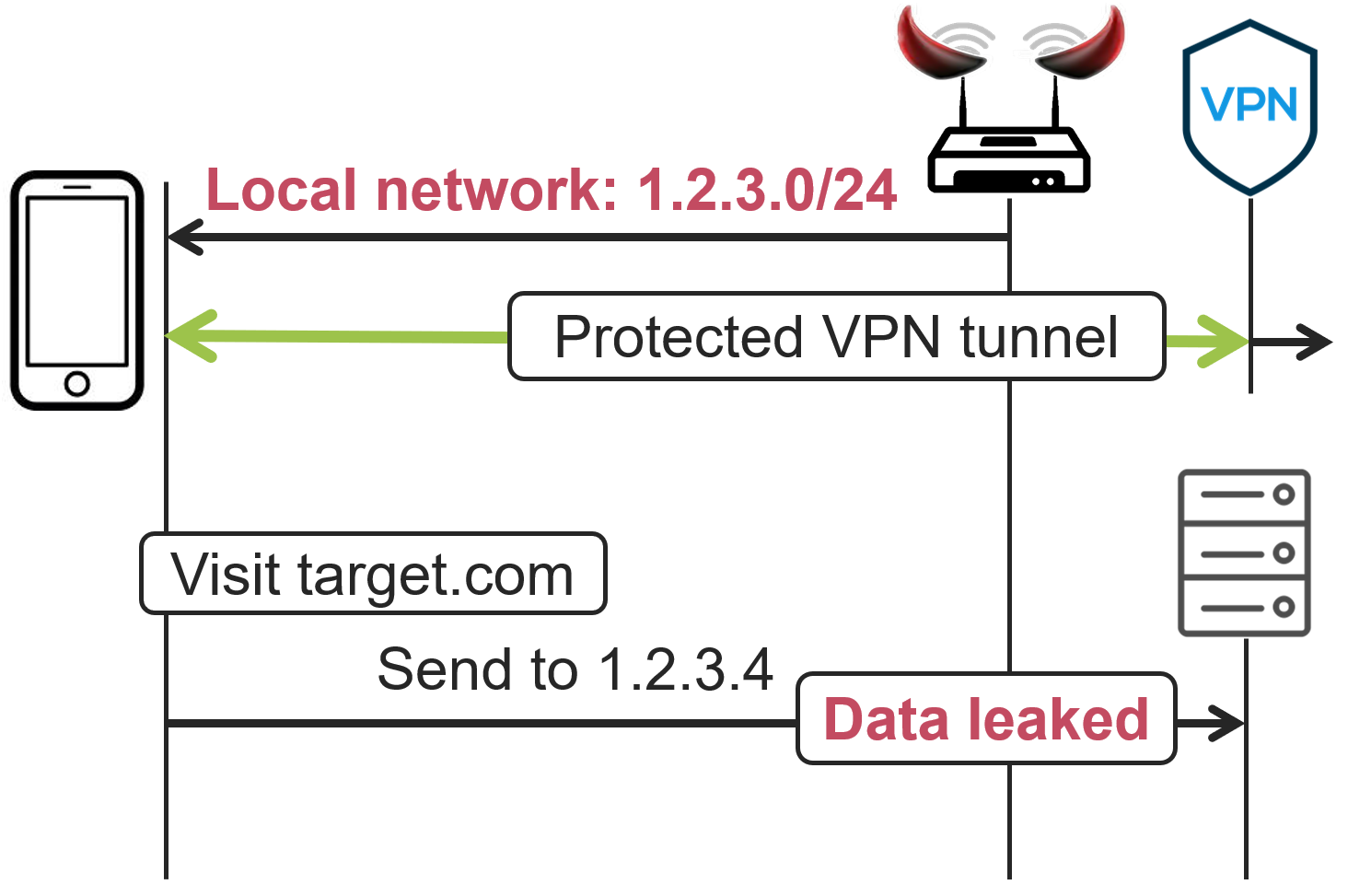
The ServerIP attack exploits the fact that many VPNs do not encrypt traffic from the client to the VPN server IP address:

For technical details of the TunnelCrack attack, see the research paper "Tunnel Traversal: Leaking VPN Client Traffic by Abusing Routing Tables", which the authors presented at the USENIX Security 2023 security conference.
SSH3
To protect against existing and future attacks, as well as to improve the efficiency of data transfer, the third version of the SSH3 protocol has already been developed . In short, SSH3 is SSH2, which operates on the HTTP/3 protocol and QUIC + TLS 1.3, with the HTTP Authorization user authorization mechanism.

Among other things, SSH3 implements the following improvements:
- Significantly faster session establishment
- New HTTP authentication methods such as OAuth 2.0 and OpenID Connect, in addition to classic SSH authentication
- Support for X.509 certificates
- Port Scan Protection: SSH3 Server Can Be Made Invisible on the Internet
- UDP port forwarding in addition to classic TCP forwarding
- All QUIC features, including connection migration (coming soon) and multipath connections
If you look closely, SSH3 implements many of the features of OpenSSH.
You can already download the latest version of the SSH3 server (Windows, Linux, ARM binaries), install it, and play with this experimental development on a secret address, so that no one will notice.
The secret link is implemented as follows:
Code:
ssh3-server -bind 192.0.2.0:443 -url-path <long_secret>If you replace <long_secret> with some random value like M3MzkxYWMxMjYxMjc5YzJkODZiMTAyMjU, the SSH3 server will only be accessible at https://192.0.2.0:443/M3MzkxYWMxMjYxMjc5YzJkODZiMTAyMjU, returning 404 for all other requests.
Source
