Attack on SS7 protocol: how to intercept other people's calls and SMS
How do we protect ourselves today from various attacks aimed at obtaining your password? Someone makes the most complex passwords, someone installs brute force protection systems, etc. But the most confident in their security are those who use the popular service today - two-factor authorization via SMS. Such services are provided by banks, well-known messengers (viber, telegram, etc.), social networks (Facebook, etc.), mail systems (Gmail, etc.) and a large number of other Internet resources, requiring registration. It's not just that this method is considered the safest. After all, a priori, your mobile phone is always with you, like a wallet and other personal items that you closely follow. In addition, it is the second authentication factor (used only after entering the main password).
And now, unexpectedly, hectic days have come for SMS verification users. Already now there is an opportunity for a small amount of money with an average level of skill to receive all your SMS so that you will never know about it!
The list of resources that an attacker can get access to is even difficult to imagine (social networks, instant messengers, confirmation of banking transactions, etc.). After all, our "whole life" is tied to our phone number. It was not for nothing that an amendment was introduced that allows the transfer of a phone number when changing an operator. Changing a number now is like starting a new life from scratch.
This pattern break happened due to the vulnerability of the SS7 protocol in the networks of cellular operators.
What is SS7?
SS7, also known as Signaling System # 7, refers to a data network and a set of technical protocols or rules that govern the exchange of data over it. It was developed in the 1970s to track and connect calls across different carrier networks, but is now commonly used to calculate cellular billing and send text messages in addition to routing mobile and landline calls between carriers and regional switching centers.
Vulnerability history
It is not surprising, but it became known about the presence of this vulnerability in ancient times. The well-known Steve Jobs carried out the first attacks in his garage, making a so-called free cellular connection using vulnerabilities. Since that time, some of the shortcomings have been closed, but SS7 is still subject to successful attacks.
In February 2014, the US ambassador to Ukraine suffered a nasty leak. A secret conversation between him and US Assistant Secretary of State Victoria Nuland was posted on YouTube, in which Nuland spoke disparagingly about the European Union.
The conversation took place over unencrypted phones, and US officials told reporters that they suspected the call was intercepted in Ukraine, but did not say how it was done. Some experts believe that this happened by exploiting vulnerabilities in the mobile data network known as SS7, which is part of the underlying infrastructure.
It wasn't until December 2014 that telecommunications companies began to consider tools to stop SS7 attacks. It was then that Karsten Nohl of the Berlin Security Research Laboratories and an independent researcher named Tobias Engel made reports on SS7 at the Chaos Communications Congress in Germany, months after the Ukrainian incident was discovered. Engel demonstrated the SS7 method for tracking phones in 2008, but the method was not as flashy as the ones he and Nol described in 2014. The latter prompted regulators in Northern Europe to require operators to start implementing measures to prevent SS7 attacks by the end of 2015.
How to attack SS7?
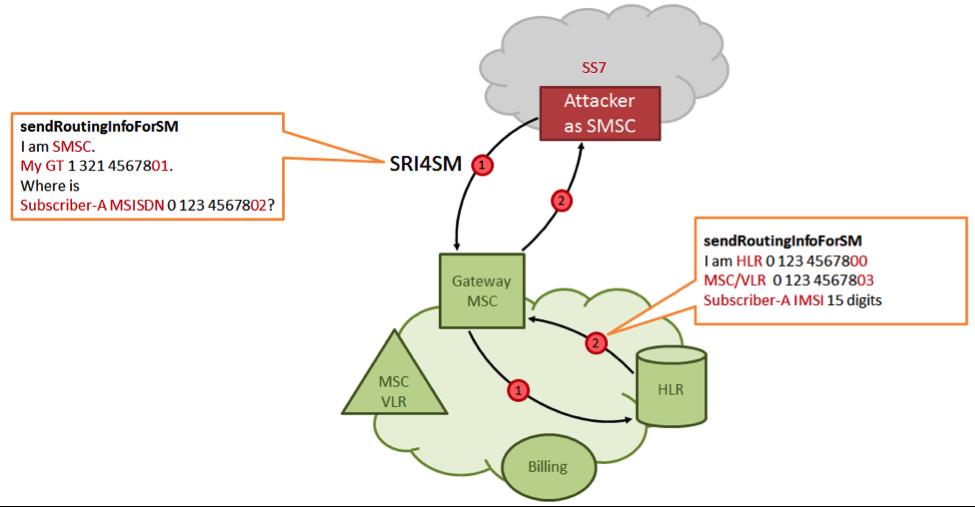
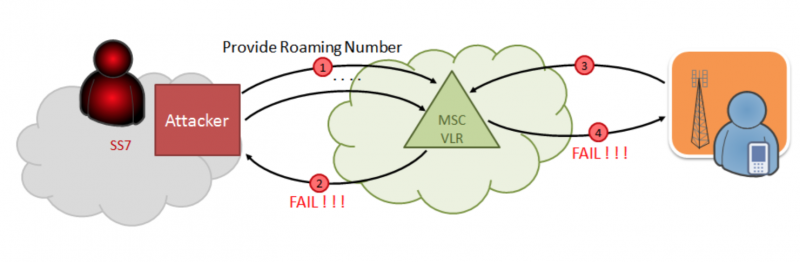
The attacker connects to the SS7 signaling network and sends the Send Routing Info service command for SM (SRI4SM) to the network channel, specifying the phone number of the attacked subscriber as a parameter. The home subscriber network responds with the following technical information: IMSI (International Mobile Subscriber Identity) and the MSC address at which it is currently providing services to the subscriber.
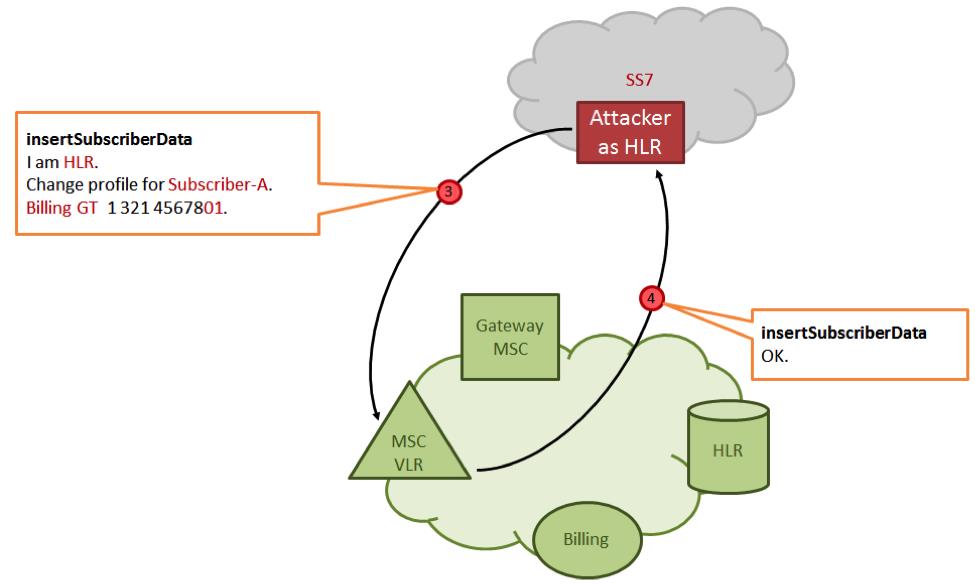
After that, the attacker changes the address of the billing system in the subscriber's profile to the address of his own pseudo-billing system (for example, he informs that the subscriber flew to rest and registered in the new billing system in roaming). As you know, this procedure does not pass any verification. The attacker then enters the updated profile into the VLR database via an Insert Subscriber Data (ISD) message.
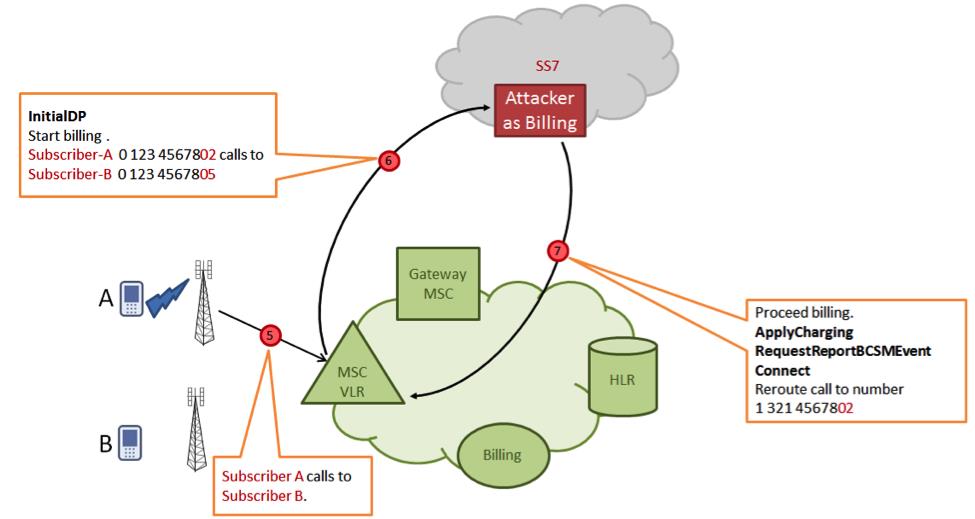
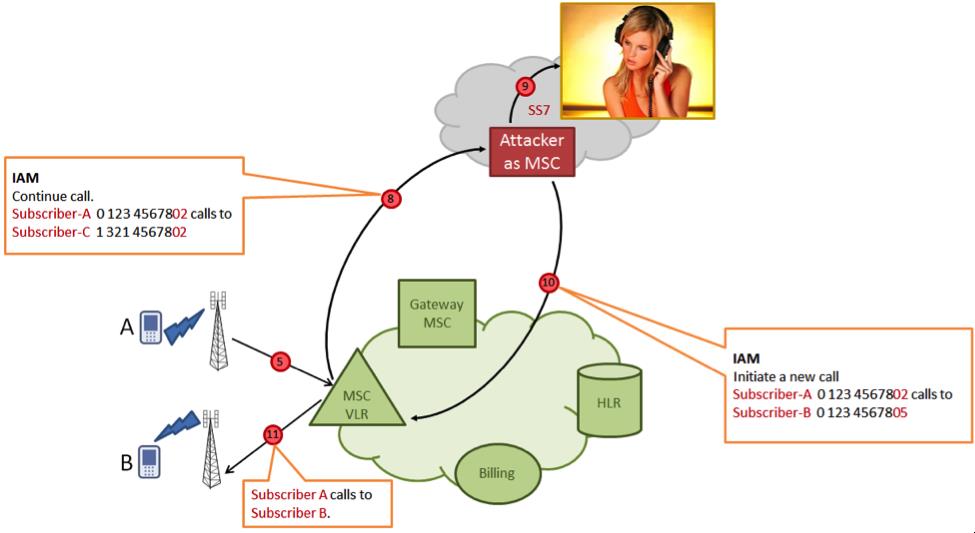
When the attacked subscriber makes an outgoing call, his switch accesses the attacker's system instead of the actual billing system. The attacker system sends a command to the switch to redirect the call to a third party controlled by the attacker.
In a third-party location, a conference call is established with three subscribers, two of them are real (caller A and callee B), and the third is entered illegally by an attacker and is able to listen and record the conversation.
Correspondingly, we receive the attacked SMS. Having access to the pseudo-billing system, to which our subscriber has already registered, you can get any information that comes or goes from his phone.
How to get illegal access to SS7 network?
As we saw, having access to the SS7 network, it is not difficult to launch an attack. How do you get illegal access to the network?
Access is sold on the darknet, and if you wish, you can find it for free. This availability is due to the fact that in less developed countries it is very easy to obtain operator status, and accordingly, to get access to SS7 hubs. There are also unscrupulous workers at the operators.
What are providers and Internet resources doing with SMS verification?
At the moment, operators are slowly closing numerous holes in SS7, despite the fact that some do not even acknowledge their existence. Someone accuses of stirring up panic around this problem, someone refrains from commenting, someone says streamlined phrases such as: "The safety of our customers is our priority." However, to date, this issue has not received due attention from operators, and the availability of exploitation of this vulnerability is greater than ever.
Hacking cellular networks: not easy, but very simple
Is it possible to find out where the person is by the phone number? Can! And at the same time you can rob him and eavesdrop on his conversations. And if you believe Positive Technologies specialists, it's not that difficult at all.
Some time ago, the Internet was popular "wiring" in the form of a "program for punching a mobile number". Somewhere it was offered to download for free, somewhere it was sold for money, somewhere it was “implemented” as an online service - the result was the same anyway: a computer infected with a Trojan or a leak of funds from a mobile account through a paid subscription or others. similar relatively honest ways. Taught by bitter experience and the comments of mobile operators, users practically believed that the creation of such a program is physically impossible.
Nevertheless, hacking a cellular network and determining the location of a subscriber, reading his SMS, eavesdropping on conversations and even stealing money from an account using a USSD request is not easy, but very simple. The company Positive Technologies has released a report on the safety of cellular networks; her research clearly demonstrates that such "tricks" are available even to a novice hacker.
No "spy tricks" (although, according to Snowden, these are the methods used by the NSA to spy on people around the world) for this will not be required. Moreover, the special services themselves do not need them: all networks are already connected to SORM, so all your conversations and correspondence, and when conducting search activities, the location is quite accessible to the relevant authorities and without hacking. But the fact that virtually any student can get access to your personal information is not good news.
There is a demand for services, the price is affordable for almost everyone
The main vulnerability is in the SS7 signaling protocols (called SS7 in Western literature), developed in the late 1970s and adopted in 1981. Then it was a breakthrough in terms of security, because a separate channel, physically inaccessible to the subscriber, began to be used for signaling (that is, for transmitting service commands during the establishment of a telephone connection). Prior to that, all commands in the form of tones were transmitted directly to the line and, for example, based on the undocumented functions of old protocols, it was possible to implement caller ID on analog PBXs: the telephone set sent a request for a number and received a response from the station. Initially, this was invented for long-distance PBXs, so that after dialing eight on the city PBX, it would be possible to understand who to bill for the call. However, using the same channel for signaling,
"But the signal channel is not available to the subscriber!" - you say. However, the fact is that in the early 2000s, the SIGTRAN specification was developed, which allows the transmission of SS-7 commands over IP networks. And it so happened that unprotected protocols (after all, their developers assumed that no one would physically get to the signal channel, so they considered it inexpedient to complicate everything) ended up in public IP networks, and now all that is needed is a computer with an Internet connection and simple software: the authors of the report used a Linux system with the SDK installed to generate SS7 packages. The whole idea of hacking is based on the fact that the system does not check the source of the package (again: according to the logic of the developers, it physically cannot appear from the outside), therefore, it processes the commands of the attacker in the same way as legitimate ones. allowing you to fully "wedge in" and implement a man-in-the-middle attack. It is impossible to filter these packets because their legitimacy cannot be reliably established.
[/URL]
Connection diagram for attack through OKS-7
However, let's
upset the hackers a
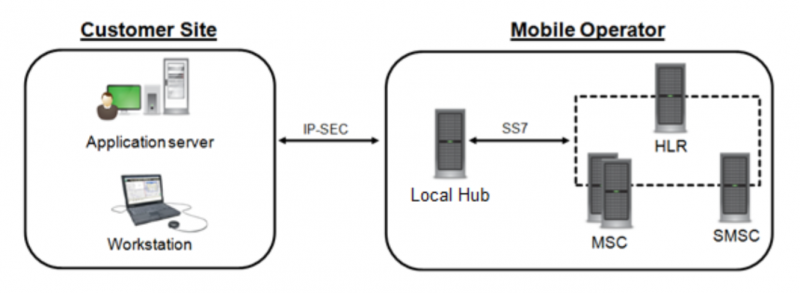
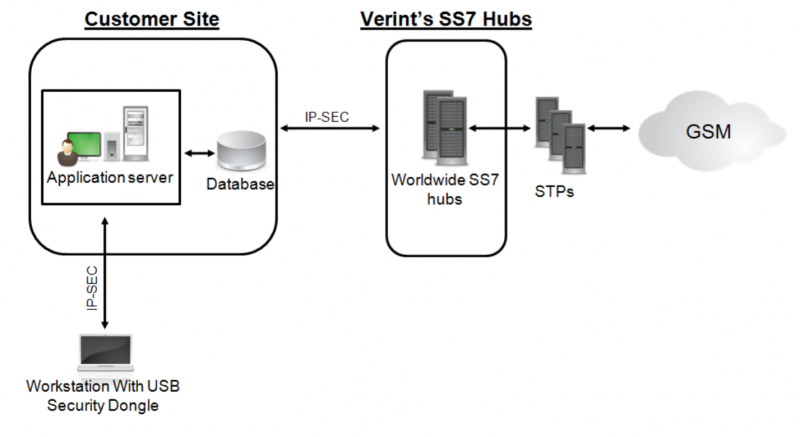
little.who have already gathered to misbehave without getting up from the couch: to carry out attacks, it is not enough to install the necessary software that emulates the operator's equipment. You also need a connection as an operator, which, however, is easy to buy on the black market: in a number of countries where an operator license is issued to just about anyone, such a "business" is thriving, and for a successful attack it does not matter which country your "operator" is from: paid for access to the gateway - and attack the subscriber anywhere in the world. Blocking OKS-7 packages from abroad in this case will not help, because it will lead to the impossibility of roaming and international communication. In addition, it is possible to gain access to the operator's network, for example, by hacking a femtocell. And finally, you can generally be a humanist and just order a service. For example, it is offered under the SkyLock brand by Verint.
[/URL]
As part of the SkyLock service, you can buy a connection directly to the operator through IP-SEC
Before proceeding to a description of the attacks themselves, let us recall how mobile networks are arranged. You have a number. For example, +79992128506. This is MSISDN (Mobile Subscriber Integrated Services Digital Number). It is not stored in the SIM card, as many people think. Another identifier is stored in the SIM card - IMSI (International Mobile Subscriber Identity), which is transmitted to the network only during subscriber registration. This is a 15-digit number of the form 250115556667778, in which 250 is the country code, 11 is the operator's code, and the remaining 10 digits are the internal unique number of this SIM card (MSIN, Mobile Subscriber Identification Number). It is IMSI that is used to identify the subscriber within the cellular network, that is, to perform any operations with the number.
Information on compliance with IMSI and MSISDN (that is, which subscriber has which SIM card) is stored in a database called HLR (Home Location Register), and there may be several such databases - which is why, for example, when trying to change a SIM card for a new one the operator's salon may not have SIM cards for your number, since the IMSI of the existing SIM cards may already be entered into another HLR. At the same time, for each of the network segments (switches), a similar VLR (Visitor Location Register) database is used - its difference lies in the fact that data is stored in it temporarily, copied from HLR when a subscriber appears in this part of the network. The VLR also stores data about the current location of the subscriber (in order to know through which base station to route the incoming call and message), forwarding settings, and the like.
]
[/URL]
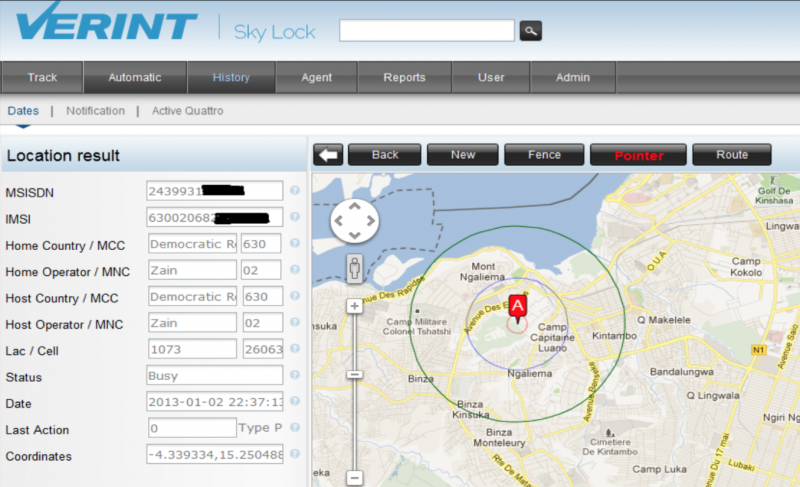
In the SkyLock service, the location of any subscriber is indicated on the map: the interface is understandable to anyone, the entire hacking is performed by the program
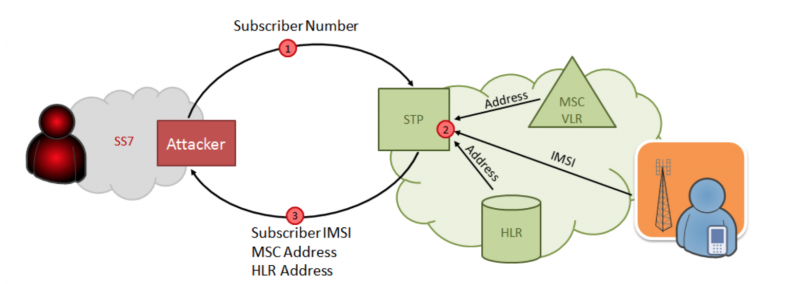
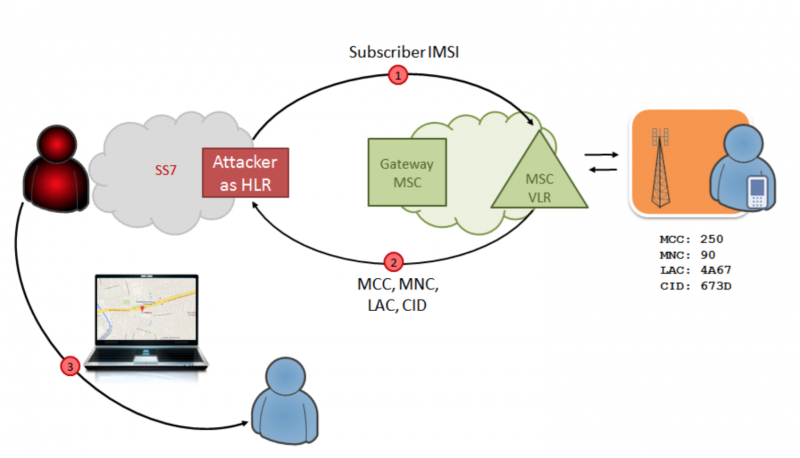
So how does the hack happen? Initially, the attacker only has a phone number (MSISDN). To do something with it, you need to get the IMSI. This can be done by generating a request to deliver an SMS message from our external "network" emulated on a computer. In this case, the home network responds to the request with the address of the MSC / VLR that is currently serving the subscriber: these data are necessary in order to find out if the subscriber is at home or in roaming, and if in roaming, then in which network, so that in this In this case, send SMS directly there (with a voice call, this will not work, because it always passes through the MSC of the home network - and that already determines how to route the call further). In this case, the transfer of IMSI occurs, since it is also necessary for routing.
Attack scheme for obtaining IMSI
Now you can get a request for the exact location of the subscriber: the attacker, knowing the current MSC / VLR, sends there a request about which base station serves the subscriber with such and such an IMSI. In response, a unique BS identifier is received, by which, through open databases, you can find out where it is located, and find the subscriber with an accuracy of a couple of hundred meters - just like smartphones with GPS turned off determine the location.
[/URL]
Attack pattern for locating a subscriber
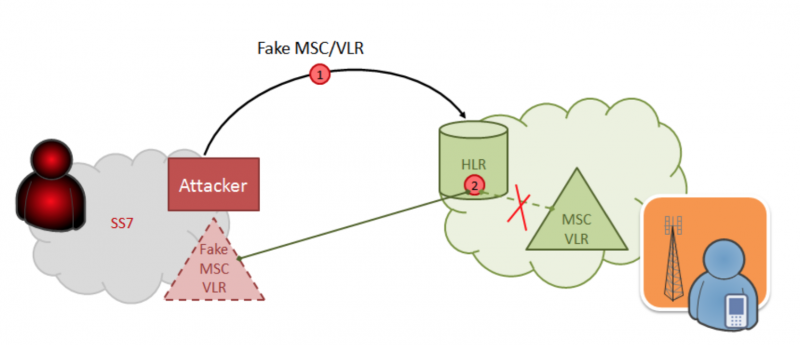
Why not play a hooligan now? Let's inform HLR that the subscriber has registered in the roaming network: we will transmit the IMSI and the address of the new MSC / VLR. Now no one will be able to call or send an SMS to the victim: the home network forwards requests to nowhere, while the subscriber will still be registered in the network and will not suspect anything.
[/URL]
Attack pattern for blocking victim's accessibility
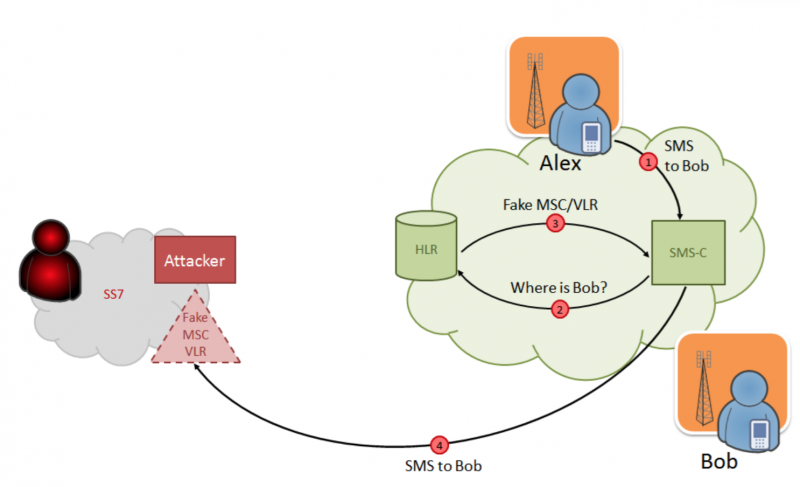
By the way, why send calls and SMS to nowhere? Goodness should not be lost! Let's enter your MSC / VLR - and all traffic will be directed to us! For example, in this way you can collect one-time SMS passwords for two-factor authentication in various services, and this creates almost unlimited opportunities for stealing money and accounts. Or you can just read the entire SMS-correspondence, and the victim will not even suspect that she is being followed. The fact is that SMS requires MSC / VLR to confirm its delivery, and if it is not sent (we have not a real network, but emulation, you can receive a message, but say that you have not received it), and instead re-register the subscriber to " real »MSC, then in a few minutes another attempt will be made to deliver the message and it will arrive at the addressee. That is, the same SMS will be sent two times:
Attack scheme for intercepting SMS messages addressed to the victim
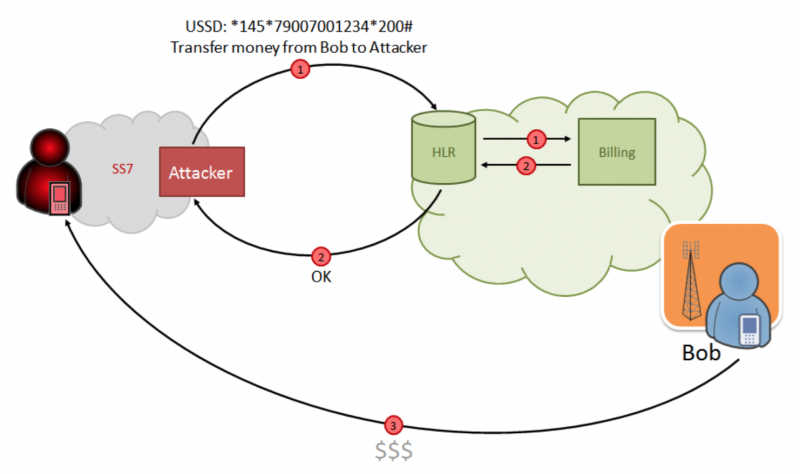
As you know, USSD requests always work in roaming, allowing you to check the balance, activate different services and tariff options. By simulating a USSD request from VLR to HLR (here you need the MSISDN, the HLR address and the actual request itself in the form of a combination of numbers, asterisks and hashs), you can, for example, initiate a transfer of funds from one account to another. Some operators use SMS authorization to confirm this operation, but we just learned how to intercept SMS.
Scheme of an attack with sending USSD requests on behalf of the victim
By changing the parameters of the subscriber's account in the VLR, in particular the address of the billing system, an attacker can intercept the request for tariffication of an outgoing call - the number of the subscriber to whom the victim is trying to call will be visible in it. Now this subscriber can also be made victim: the same method as for intercepting SMS, will allow you to forward the call to the attacker's number, and he already initiates a conference call with the real subscriber, quietly eavesdropping on the conversation. Accordingly, incoming calls can be listened to in the same way, but without the need to emulate the billing system. All these procedures take place in a few seconds, and none of the interlocutors will suspect that there is someone third between them. In addition, you can redirect traffic not for listening, but in some expensive service like "phone sex" and the like: this can be well monetized, since the connection fee will be debited from the callers.
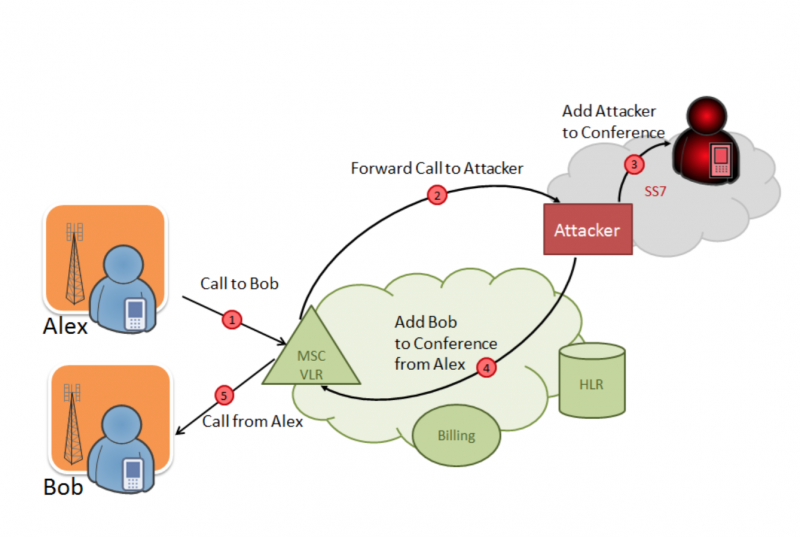
Attack scheme with wiretapping of the subscriber's conversations
Finally, with the help of SS-7, you can arrange a real DoS attack on the switch, which will lead to the inability to receive incoming calls from all subscribers in its service area. To do this, you need to know that when registering with the VLR, a temporary roaming number is allocated, which is needed so that the MSC knows exactly where to route the call. To the generally used concept of roaming (international or intranet), the roaming number has a very distant relationship. It also stands out in the home network: despite the fact that MSC and VLR, as a rule, are combined, according to the GSM standard they are two independent logical network elements, and signaling messages are still exchanged between them. So, if you massively send requests for the allocation of roaming numbers, then their pool will end,
DoS attack scheme on the switch
What to do? For now, we can only talk about “how scary it is to live”: protection solutions mainly boil down to monitoring attacks to detect suspicious activity according to the scenarios described above - this allows you to selectively block certain requests. Meanwhile, operators try not to advertise the presence of vulnerabilities: hacking opportunities practically do not affect their business, and subscribers can still be advised not to conduct confidential conversations over the phone and not rely on SMS for authorization. In addition, for such purposes, it is better to purchase a separate SIM card, the number of which will not be known to anyone from your social circle.
Additional information
Discover the best practices for information security and cyber threat detection. Learn how to effectively respond to threats and protect your data.

logrhythm.com
You can find SMS hacking specialist on the forums raidforums.com, exploit.in and hackerplace.org
Current hacking method: