Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,212
- Points
- 113
The hacking of a spyware manufacturer has exposed a large-scale spy campaign around the world.
Spytech, a Minnesota-based spyware manufacturer, has been hacked, revealing that tens of thousands of devices around the world are under the company's covert remote surveillance.
Information about the hack came from a person who has access to the company's database. The source provided TechCrunch with a cache of files from servers containing detailed logs of the activity of devices, phones, tablets and computers that are tracked by Spytech, and some of the files date back to the beginning of June. TechCrunch confirmed the authenticity of the data by partially analyzing device activity logs associated with the company's chief executive officer, Nathan Polenchek, who installed spyware on one of his devices.
Spytech's spy programs – Realtime-Spy and SpyAgent-have been used to compromise more than 10,000 devices since 2013, including Android devices, Chromebooks, Macs, and Windows PCs around the world, according to the report. Polenchek first learned about the hack from a TechCrunch email and has not yet discovered the data leak, but has launched an investigation and promised to take appropriate action.
Spytech makes remote access applications (stalkerware), which are sold under the guise of parental control programs, but are also advertised as a tool for tracking the devices of spouses and partners. The company's website openly offers similar surveillance products.
Stalkerware is usually installed by a person with physical access and knowledge of the victim's device password. Stalkerware works covertly, so it is difficult to detect and remove such software. Once installed, the spyware collects information about keystrokes, screen taps, web search history, device activity, and, in the case of Android devices, location data.
The leaked data contains logs of all monitored devices, including unencrypted activity logs. Analysis of the victims ' location data showed that most of the devices are located in Europe, the United States, Africa, Asia, Australia, and the Middle East. One of the records linked to Polencek's administrator account contains the exact geolocation of his home in Minnesota.
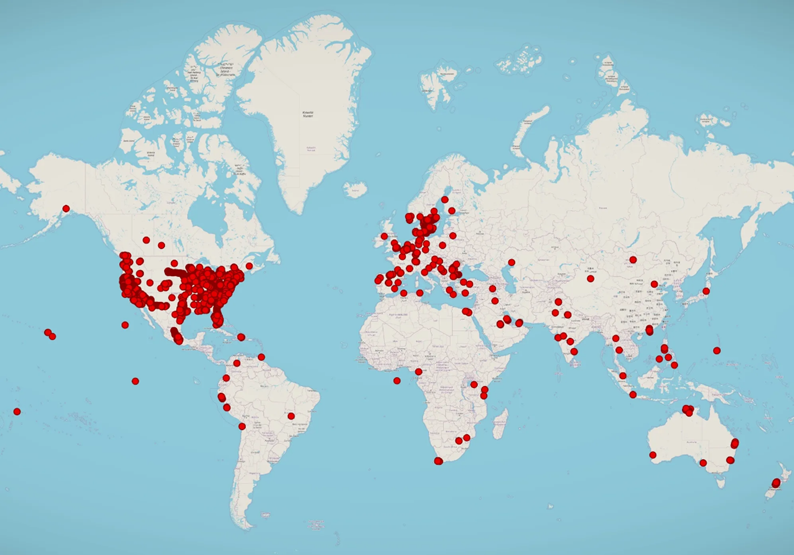
Geolocation of spyware victims
Although the leak includes a lot of sensitive and personal information obtained from people's devices (some of them may not know about monitoring), the data does not contain enough identifying information for TechCrunch to notify victims of the leak.
When asked by TechCrunch if the company plans to notify its customers or the relevant authorities (as required by data breach laws), Polenchek did not respond. The agency tried to contact the Attorney General of Minnesota, but there was no response.
Spytech has been around since at least 1998. Until 2009, the company's activities went unnoticed, until an Ohio man was convicted of using Spytech spyware to infect the computer systems of a children's hospital in order to track the email of his ex-girlfriend working there. The spyware got into the hospital's systems as soon as the girl opened the infected attachment. In addition to the girl's personal email, the program collected confidential information about patients health.
Spytech is the second U.S. spyware manufacturer to suffer a data breach in recent months. In May, a hacker hacked the site of the pcTattletale spy app, which turned out to be installed in the check-in systems of several Wyndham hotels in the United States. The attacker posted offensive content on the official page and leaked more than a dozen archives containing databases and the source code of the program to the public.
Source
Spytech, a Minnesota-based spyware manufacturer, has been hacked, revealing that tens of thousands of devices around the world are under the company's covert remote surveillance.
Information about the hack came from a person who has access to the company's database. The source provided TechCrunch with a cache of files from servers containing detailed logs of the activity of devices, phones, tablets and computers that are tracked by Spytech, and some of the files date back to the beginning of June. TechCrunch confirmed the authenticity of the data by partially analyzing device activity logs associated with the company's chief executive officer, Nathan Polenchek, who installed spyware on one of his devices.
Spytech's spy programs – Realtime-Spy and SpyAgent-have been used to compromise more than 10,000 devices since 2013, including Android devices, Chromebooks, Macs, and Windows PCs around the world, according to the report. Polenchek first learned about the hack from a TechCrunch email and has not yet discovered the data leak, but has launched an investigation and promised to take appropriate action.
Spytech makes remote access applications (stalkerware), which are sold under the guise of parental control programs, but are also advertised as a tool for tracking the devices of spouses and partners. The company's website openly offers similar surveillance products.
Stalkerware is usually installed by a person with physical access and knowledge of the victim's device password. Stalkerware works covertly, so it is difficult to detect and remove such software. Once installed, the spyware collects information about keystrokes, screen taps, web search history, device activity, and, in the case of Android devices, location data.
The leaked data contains logs of all monitored devices, including unencrypted activity logs. Analysis of the victims ' location data showed that most of the devices are located in Europe, the United States, Africa, Asia, Australia, and the Middle East. One of the records linked to Polencek's administrator account contains the exact geolocation of his home in Minnesota.

Geolocation of spyware victims
Although the leak includes a lot of sensitive and personal information obtained from people's devices (some of them may not know about monitoring), the data does not contain enough identifying information for TechCrunch to notify victims of the leak.
When asked by TechCrunch if the company plans to notify its customers or the relevant authorities (as required by data breach laws), Polenchek did not respond. The agency tried to contact the Attorney General of Minnesota, but there was no response.
Spytech has been around since at least 1998. Until 2009, the company's activities went unnoticed, until an Ohio man was convicted of using Spytech spyware to infect the computer systems of a children's hospital in order to track the email of his ex-girlfriend working there. The spyware got into the hospital's systems as soon as the girl opened the infected attachment. In addition to the girl's personal email, the program collected confidential information about patients health.
Spytech is the second U.S. spyware manufacturer to suffer a data breach in recent months. In May, a hacker hacked the site of the pcTattletale spy app, which turned out to be installed in the check-in systems of several Wyndham hotels in the United States. The attacker posted offensive content on the official page and leaked more than a dozen archives containing databases and the source code of the program to the public.
Source
