Professor
Professional
- Messages
- 1,384
- Reaction score
- 1,297
- Points
- 113
Hi, friend
WebRTC - Spoofing or hide for carding?
Reading Darknet forums I see stupid templates. Authors retell information from the time of dinosaurs without understanding the essence of the card. Beginners blindly follow the advice of "authorities".
To understand, I will answer 3 questions:
Knowing the answers to the questions above, we begin to think logically. Why ask the question: "Is it possible to change the IP?" Think about it, does KH change the IP? He changes, he is an average person. He sits at home with a computer, then goes to eat burgers, and there from another IP he buys himself sneakers.
Logic is a cool thing. For example, in pursuit of anonymity, newbies are eager to turn off WebRTC. Okay, young hacker reading the text, go to your mom and ask: "Mom, are you turning off WebRTC?" The same goes for KH, he doesn't give a damn about bringing anonymity to 100%.
But let's not forget that each shop has its own anti-fraud system. And it's quite possible that with WebRTC disabled, fat packs will fly in. It's necessary to test different systems and approaches to the shop in order to know for sure.
WebRTC Spoofing
The software works with: Soks5, SSH, Tor. Automatically replaces WebRTC and you can configure DNS. The program is free. It receives profit from advertising SSH sellers and donations.
Official website: http://ssh-tunnel.in/viewtopic.php?f=5&t=32816
The software is detected on virustotal.com. The problem was discussed on exploit.in and as it turned out, everything was clean. According to the author, the reason is in the packaging of the software through the Winlicense protector. I recommend running it on a virtual machine.
This manual allows you to replace WebRTC with the IP of the tunnel or socks that you use. As an alternative to disabling WebRTC in the browser.
The setup is divided into several parts.
1. Install and configure the firewall
We stomp to the control panel.
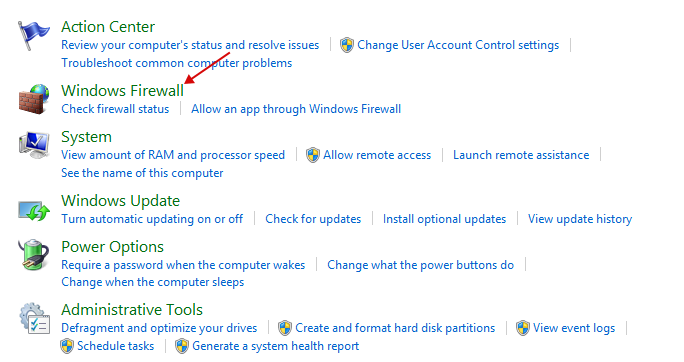
Click on "Advanced settings".
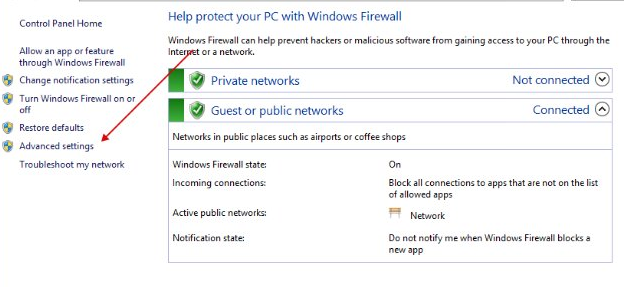
Next, click on "Windows Firewall Properties".
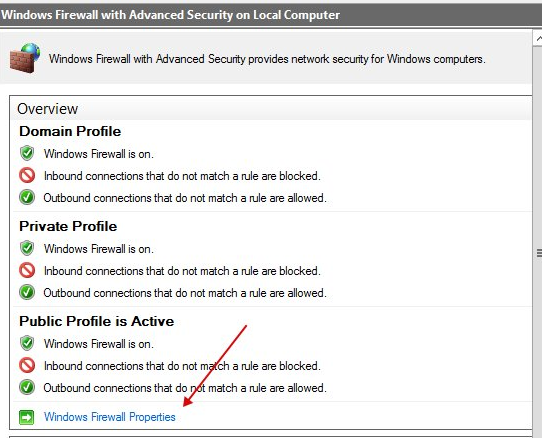
Next, in all three tabs, specify "Outbound connections: Block".
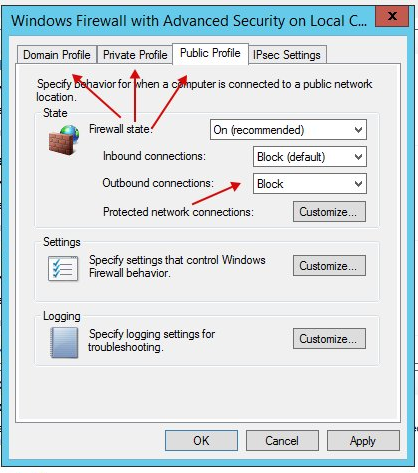
Next, go to Outbound Rules and click on New Rule.
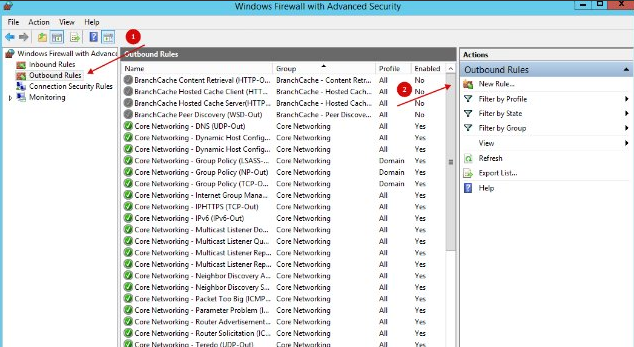
Select "Program".
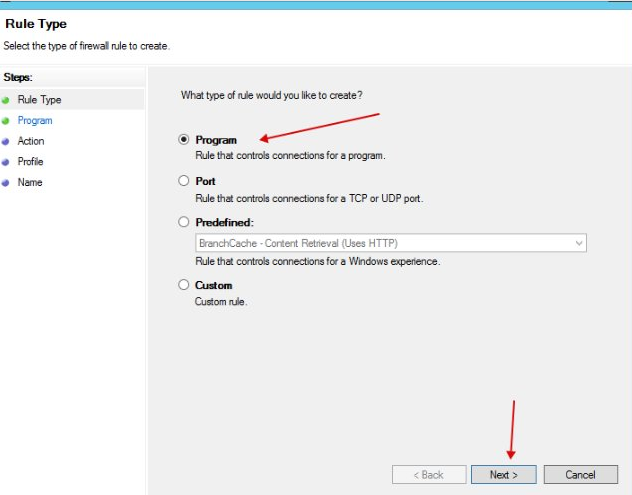
We indicate the application that should go online (Bitvise, proxyfier).
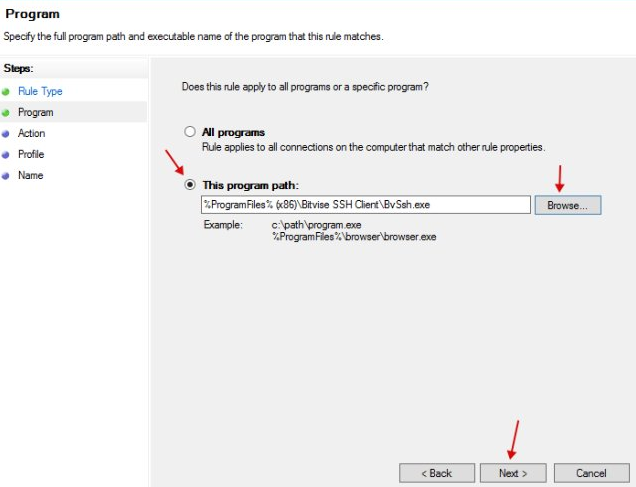
We specify "Allow the connection".
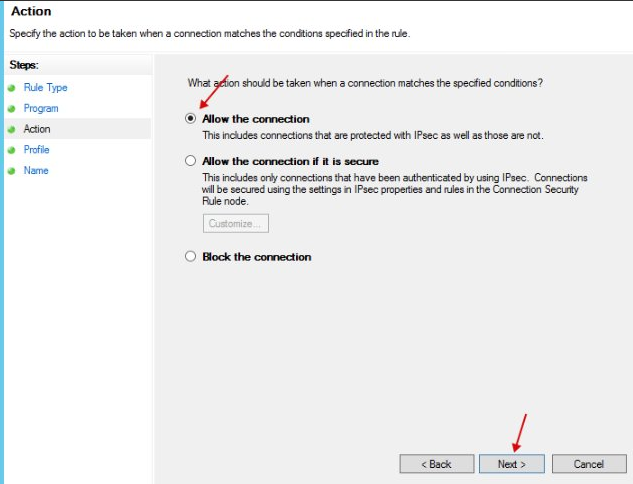
Next, we set the network name and close the settings.
We are trying to connect to the Internet in our case using "Bitvise" and tunnels.
If everything is done correctly, WebRTC will show us only the internal network IP without the external one.
It should look something like this:
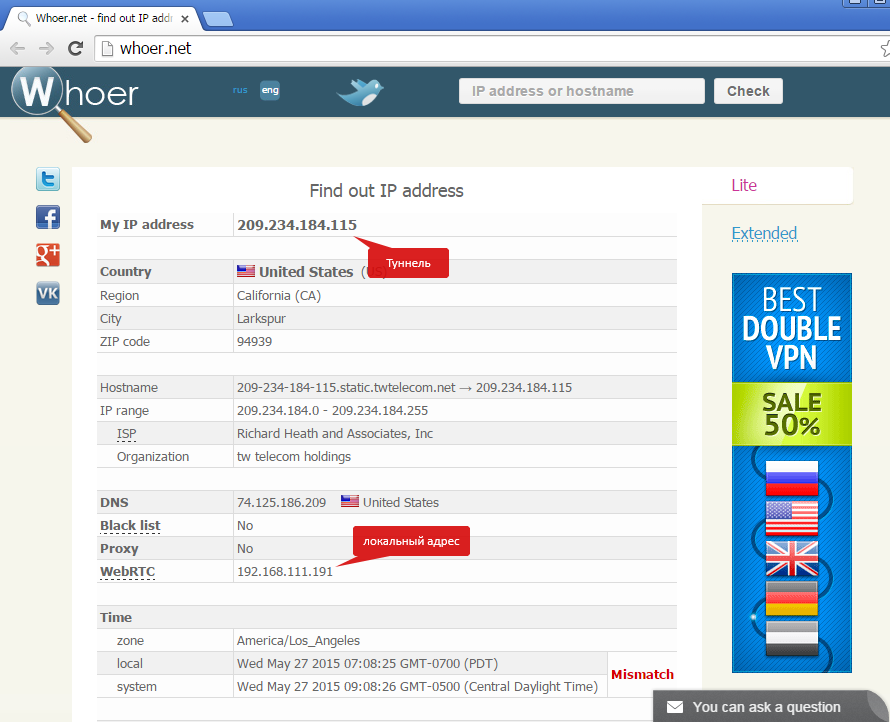
If so, then everything is fine. Now we need WebRTC to show the IP we need.
Part 2. CONFIGURING THE SELF-LOOPING ADAPTER.
Now we need to create a loopback adapter to fool WebRTC.
To do this, go to the hardware manager and select "Add legacy hardware" in the "Action" menu, after clicking on the "Network adapters" section.
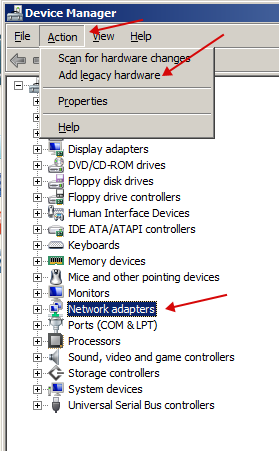
We select manual installation.
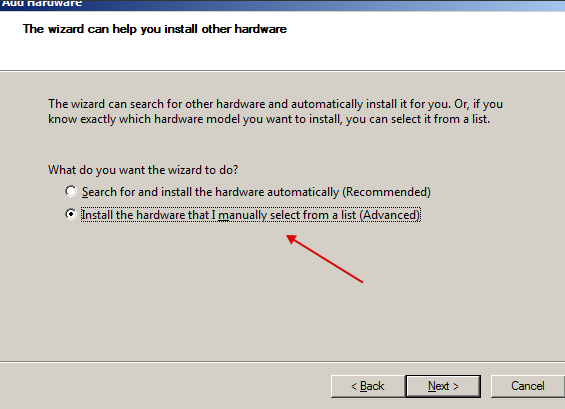
Select "Network adapters".
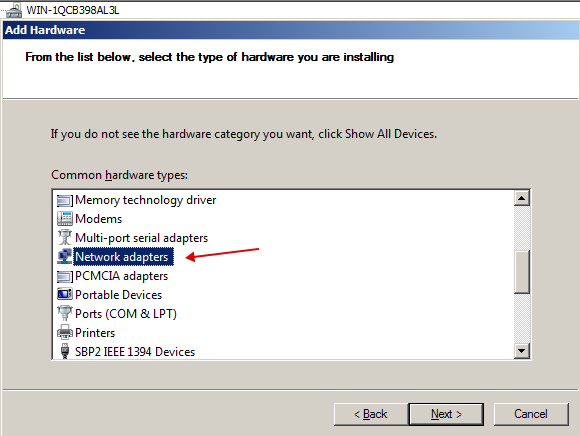
Select "Microsoft" and select "Microsoft Loopback Adapter".
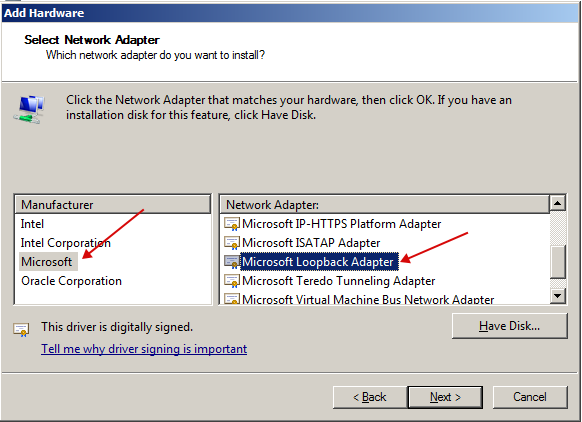
After installation, we go to the settings of this adapter. And in its properties we specify the IP that Whoer showed us.
In my case it is 64.53.67.252:
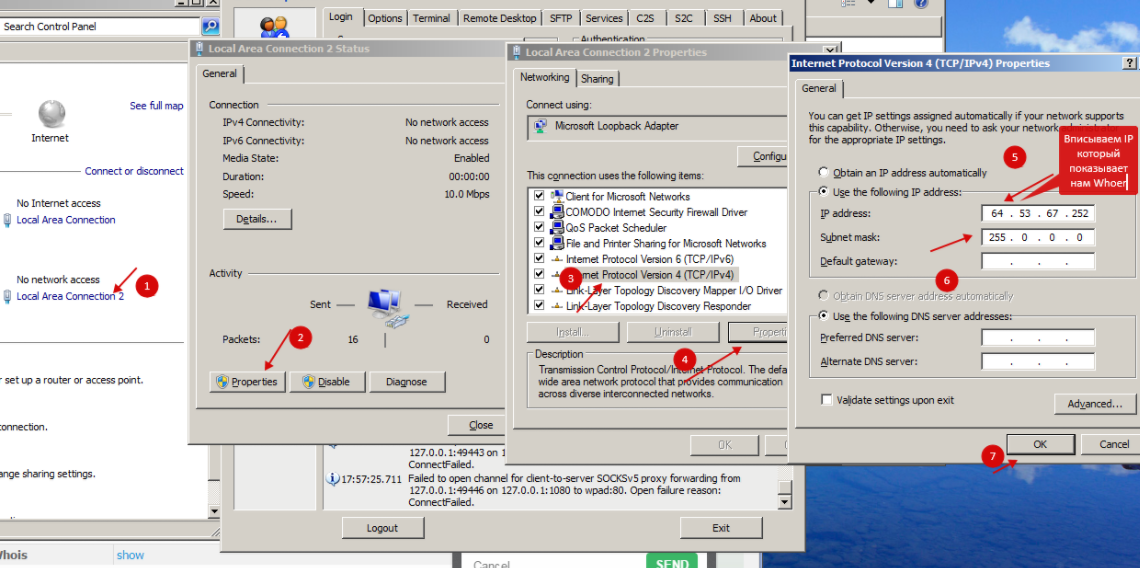
Afterwards, save and run the command line. In the command line, enter the following:
To find out the Default gateway, enter "ipconfig" in the command line. If the line is empty, look for the gateway address in the virtual machine network settings. In my case, I enter in the command line:
If everything is OK, the command line will respond as follows.
If you receive an error with the text "The requested operation requires elevation" then run the command line as administrator.
Delete the old rule with the command:
Set a new rule with the command:
P.s. after reboot all the rules you specified are deleted. That is, after reboot there is no need to delete old rules.
Now let's head to Whoer.net.
We refresh the page a couple of times and if everything is ok, the following will happen:
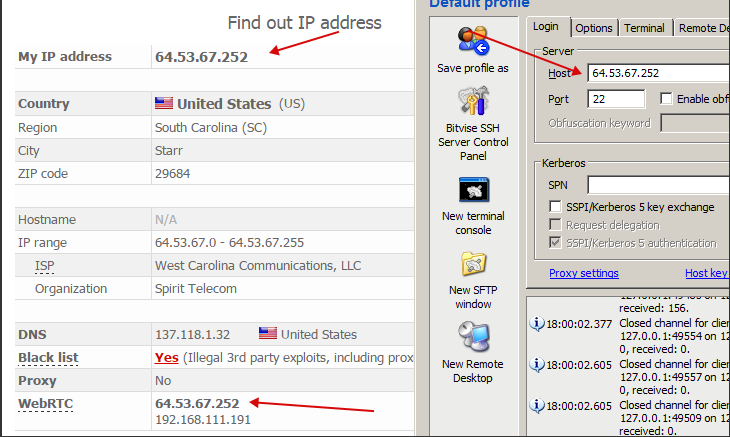
We can't believe our eyes and go check somewhere else.
The result is the same:
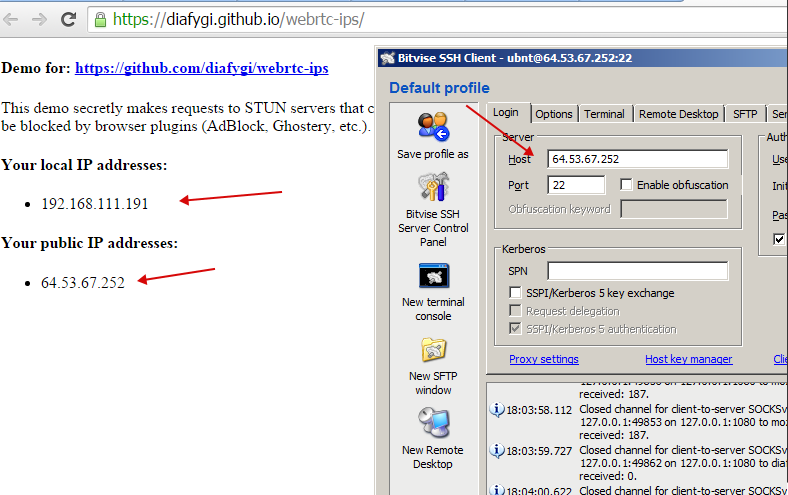
Thank you for staying with us! Have a good carding!
WebRTC - Spoofing or hide for carding?
Reading Darknet forums I see stupid templates. Authors retell information from the time of dinosaurs without understanding the essence of the card. Beginners blindly follow the advice of "authorities".
To understand, I will answer 3 questions:
- What is carding? Fraud with other people's payment data.
- Antifraud system? Checks transactions for fraud.
- How to bypass antifraud? It is necessary to differ minimally from CH.
WebRTC reveals real IP. We check on whoer.net
CH (card holder) - the owner of the card.
Knowing the answers to the questions above, we begin to think logically. Why ask the question: "Is it possible to change the IP?" Think about it, does KH change the IP? He changes, he is an average person. He sits at home with a computer, then goes to eat burgers, and there from another IP he buys himself sneakers.
Logic is a cool thing. For example, in pursuit of anonymity, newbies are eager to turn off WebRTC. Okay, young hacker reading the text, go to your mom and ask: "Mom, are you turning off WebRTC?" The same goes for KH, he doesn't give a damn about bringing anonymity to 100%.
But let's not forget that each shop has its own anti-fraud system. And it's quite possible that with WebRTC disabled, fat packs will fly in. It's necessary to test different systems and approaches to the shop in order to know for sure.
WebRTC Spoofing
- Antidetect browser . You can buy software and in a few clicks you will configure WebRTC and a number of other parameters.
- Replacement at the hardware level. You'll have to bother with the settings.
- Double SSH Tunnel Manager.
The software works with: Soks5, SSH, Tor. Automatically replaces WebRTC and you can configure DNS. The program is free. It receives profit from advertising SSH sellers and donations.
Official website: http://ssh-tunnel.in/viewtopic.php?f=5&t=32816
The software is detected on virustotal.com. The problem was discussed on exploit.in and as it turned out, everything was clean. According to the author, the reason is in the packaging of the software through the Winlicense protector. I recommend running it on a virtual machine.
This manual allows you to replace WebRTC with the IP of the tunnel or socks that you use. As an alternative to disabling WebRTC in the browser.
The setup is divided into several parts.
1. Install and configure the firewall
We stomp to the control panel.

Click on "Advanced settings".

Next, click on "Windows Firewall Properties".

Next, in all three tabs, specify "Outbound connections: Block".

Next, go to Outbound Rules and click on New Rule.

Select "Program".

We indicate the application that should go online (Bitvise, proxyfier).
However, do not forget that the main application can use auxiliary ones to connect to tunnels or socks (usually putty or plink in the folder with the main application), they will also need to be added to the exceptions.

We specify "Allow the connection".

Next, we set the network name and close the settings.
We are trying to connect to the Internet in our case using "Bitvise" and tunnels.
If everything is done correctly, WebRTC will show us only the internal network IP without the external one.
It should look something like this:

If so, then everything is fine. Now we need WebRTC to show the IP we need.
Part 2. CONFIGURING THE SELF-LOOPING ADAPTER.
Now we need to create a loopback adapter to fool WebRTC.
To do this, go to the hardware manager and select "Add legacy hardware" in the "Action" menu, after clicking on the "Network adapters" section.

We select manual installation.

Select "Network adapters".

Select "Microsoft" and select "Microsoft Loopback Adapter".

After installation, we go to the settings of this adapter. And in its properties we specify the IP that Whoer showed us.
In my case it is 64.53.67.252:

Afterwards, save and run the command line. In the command line, enter the following:
Code:
route add (tunnel/sock address) mask 255.255.255.255 (default gateway) metric 1To find out the Default gateway, enter "ipconfig" in the command line. If the line is empty, look for the gateway address in the virtual machine network settings. In my case, I enter in the command line:
Code:
route add 64.53.67.252 mask 255.255.255.255 192.168.111.2 metric 1If everything is OK, the command line will respond as follows.
If you receive an error with the text "The requested operation requires elevation" then run the command line as administrator.
Delete the old rule with the command:
Code:
route delete (tunnel/sock address) mask 255.255.255.255 (default gateway) metric 1Set a new rule with the command:
Code:
route add (tunnel/sock address) mask 255.255.255.255 (default gateway) metric 1P.s. after reboot all the rules you specified are deleted. That is, after reboot there is no need to delete old rules.
Now let's head to Whoer.net.
We refresh the page a couple of times and if everything is ok, the following will happen:

We can't believe our eyes and go check somewhere else.
The result is the same:

Thank you for staying with us! Have a good carding!

