Carding
Professional
- Messages
- 2,871
- Reaction score
- 2,391
- Points
- 113
Social engineering is a method of manipulating the thoughts and actions of people. It is based on the psychological characteristics of the individual and the laws of human thinking.
Sometimes you can find the interpretation of social engineering as a method of unauthorized gaining access to classified data, which is not entirely true: a number of techniques of psychological influence can be used legally. However, these days, obtaining sensitive information that has value is still one of the main areas of application of social engineering.
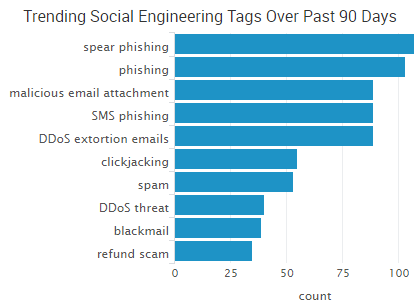
In social engineering, there are several techniques used to accomplish a given task. All of them are based on mistakes made by a person in behavior. For example, phishing is used to collect usernames and passwords by sending emails and messages encouraging the victim to provide information of interest to the attacker. Pretext is about impersonating another person in order to obtain the desired data. Such an attack is carried out by telephone or mail. It is preliminarily prepared to inspire the user's confidence.
You can get information about a person through open source sources, mainly from social networks. One social engineering technique is "shoulder surfing", which is used in transportation, cafes and other public places to observe computer devices and telephones over the victim's shoulder. There are situations in which the user himself offers the fraudster the necessary information, being confident in the decency of the person. In this case, they talk about reverse social engineering.
Social engineering threat classification
All threats directed at the user through social engineering can be divided into several groups.
Object of influence
Social engineering is directed not at computer hardware, but at its user. Of interest are all solvent persons, as well as users with valuable information, employees of enterprises and government agencies.
The method is used to carry out financial transactions, hacking, stealing information (for example, customer databases, personal data) and other unauthorized access to information. Social engineering helps competitors conduct intelligence, identify organizational weaknesses, and entice employees.
Source of threat
Attackers use social engineering to gain material gain or to extract data for resale. Social engineering can be used as one of the tools for complex targeted cyberattacks.
The source of the threat can be emails, text messages in any instant messenger, SMS messages and phone calls. Fraudsters can impersonate employees of banks and other financial organizations, government officials, employees of law enforcement agencies, Internet providers, representatives of postal services and large web resources, etc.
Risk analysis
To protect the company from fraud, it is necessary to train staff to recognize and respond to social engineering, prohibit employees from sharing passwords or have one common password, ensure the protection of customer bases and other confidential information, and apply a special confirmation procedure for persons requesting access to any data.
An anti-phishing option has appeared in browsers, warning site visitors about the unreliability or danger of the resource. Spam filters can help protect against threats sent in emails. There is a monitoring service demanded by companies that are most frequently attacked by intruders. More complex authorization methods will also reduce risks.
Sometimes you can find the interpretation of social engineering as a method of unauthorized gaining access to classified data, which is not entirely true: a number of techniques of psychological influence can be used legally. However, these days, obtaining sensitive information that has value is still one of the main areas of application of social engineering.

In social engineering, there are several techniques used to accomplish a given task. All of them are based on mistakes made by a person in behavior. For example, phishing is used to collect usernames and passwords by sending emails and messages encouraging the victim to provide information of interest to the attacker. Pretext is about impersonating another person in order to obtain the desired data. Such an attack is carried out by telephone or mail. It is preliminarily prepared to inspire the user's confidence.
You can get information about a person through open source sources, mainly from social networks. One social engineering technique is "shoulder surfing", which is used in transportation, cafes and other public places to observe computer devices and telephones over the victim's shoulder. There are situations in which the user himself offers the fraudster the necessary information, being confident in the decency of the person. In this case, they talk about reverse social engineering.
Social engineering threat classification
All threats directed at the user through social engineering can be divided into several groups.
- Threats from using the phone. The telephone is the most popular means of communication, therefore it serves as an excellent tool for influencing a person. It is easy to impersonate someone else on the phone, therefore, using acting, the attacker easily convinces the victim to transfer a certain amount to a bank account or provide personal information. There are widespread methods of fetching money through messages ("smishing") and phone calls about winning competitions or lotteries, requests for money transfers for urgent needs. For safety, it is recommended to be skeptical about dubious SMS-messages, ignore the links coming in them. It is necessary to verify the identity of the subscriber, use the number identification service.
- Threats from emails (phishing). By e-mail, letters may come containing false information on behalf of banks and other institutions, forcing you to follow the link and enter your personal data. By mail, as well as by phone, you may receive false requests for help to loved ones, messages about gifts, winnings and other free bonuses, for which you need to transfer money. You can protect yourself from intruders by ignoring letters from unknown addressees.
- Threats when using the instant messaging service. Users quickly appreciated the convenience of instant messengers. The availability and speed of this method of communication makes it open to all kinds of attacks. For safety, you should ignore messages from unknown users, do not provide them with personal information, do not follow the links sent.
Object of influence
Social engineering is directed not at computer hardware, but at its user. Of interest are all solvent persons, as well as users with valuable information, employees of enterprises and government agencies.
The method is used to carry out financial transactions, hacking, stealing information (for example, customer databases, personal data) and other unauthorized access to information. Social engineering helps competitors conduct intelligence, identify organizational weaknesses, and entice employees.
Source of threat
Attackers use social engineering to gain material gain or to extract data for resale. Social engineering can be used as one of the tools for complex targeted cyberattacks.
The source of the threat can be emails, text messages in any instant messenger, SMS messages and phone calls. Fraudsters can impersonate employees of banks and other financial organizations, government officials, employees of law enforcement agencies, Internet providers, representatives of postal services and large web resources, etc.
Risk analysis
To protect the company from fraud, it is necessary to train staff to recognize and respond to social engineering, prohibit employees from sharing passwords or have one common password, ensure the protection of customer bases and other confidential information, and apply a special confirmation procedure for persons requesting access to any data.
An anti-phishing option has appeared in browsers, warning site visitors about the unreliability or danger of the resource. Spam filters can help protect against threats sent in emails. There is a monitoring service demanded by companies that are most frequently attacked by intruders. More complex authorization methods will also reduce risks.
