Man
Professional
- Messages
- 3,221
- Reaction score
- 1,189
- Points
- 113
Hello everyone! In today's article, we will consider the smartphone as a useful tool for an information security specialist and security service worker. From obvious functions like remote photography and listening to surveillance detection and hidden camera search. As usual, with examples, useful applications and other details. For details, welcome under the cut!

Of course, this is an important task for security services. Security officers can use various equipment to detect hidden devices. This may include radio frequency signal detectors, optical scanners, thermal imagers, and other devices that can detect electromagnetic radiation or other signs of hidden devices. Smartphones usually do not have built-in functions for detecting bugs and hidden cameras. However, you can still use your smartphone as an auxiliary tool when searching for such devices.
In smartphone app stores, you can find software that detects hidden cameras. The effectiveness of such apps may be limited, as they rely on certain algorithms and sensors in the smartphone. For example, some smartphones have a built-in infrared receiver that can be used to detect infrared signals from hidden cameras or bugs (for example, Hidden Camera Detector or Glint Finder - Camera Detector).
In addition, even the built-in flashlight on your smartphone can help detect such cameras. Turn it on and illuminate the suspected area of the camera. If the camera has infrared LEDs, they may glow red or purple, which is not visible to the naked eye.

Also, some hidden cameras or microphones can be installed using magnets or hidden wiring. To detect them, you should use a smartphone with a built-in metal sensor and a corresponding pre-installed application (for example, Metal Sniffer: Metal Detector ). Cameras and microphones operating within the network space (WiFi) are also detected by a smartphone using special programs (for example, Fing - Network Tools or its analogues).

We can implement this function using various methods of responding to movement in the frame, device movement, turning on light or sound. And this, in turn, will allow us to notice suspicious activity and warn the user about a potential threat. An example of such use of a smartphone is the Haven application.
This app can use your smartphone’s microphone to detect various sounds, whether it’s just loud noises, knocks, or voices. It uses your smartphone’s built-in accelerometer and gyroscope to detect movement or vibration. If you have a front-facing camera, Haven can be used to detect changes in lighting. And if incidents are detected, Haven can send real-time notifications to your backup smartphone or email address.

To detect anything related to outdoor surveillance, you can use BT/WiFi devices such as smartphones, trackers, headsets, and smart watches. Checking for connected devices and their activity can help you spot potential problems. My favorite app in this area is WiGLE (from Wireless Geographic Logging Engine).
WiGLE is an open-source project that collects and analyzes wireless network data. The app can passively collect information about cellular stations, WiFi routers, and Bluetooth devices with geolocation. This allows us to identify devices that are “moving” with us, i.e., can spy on us. WiGLE provides the approximate proximity of such devices, their names, and MAC addresses.
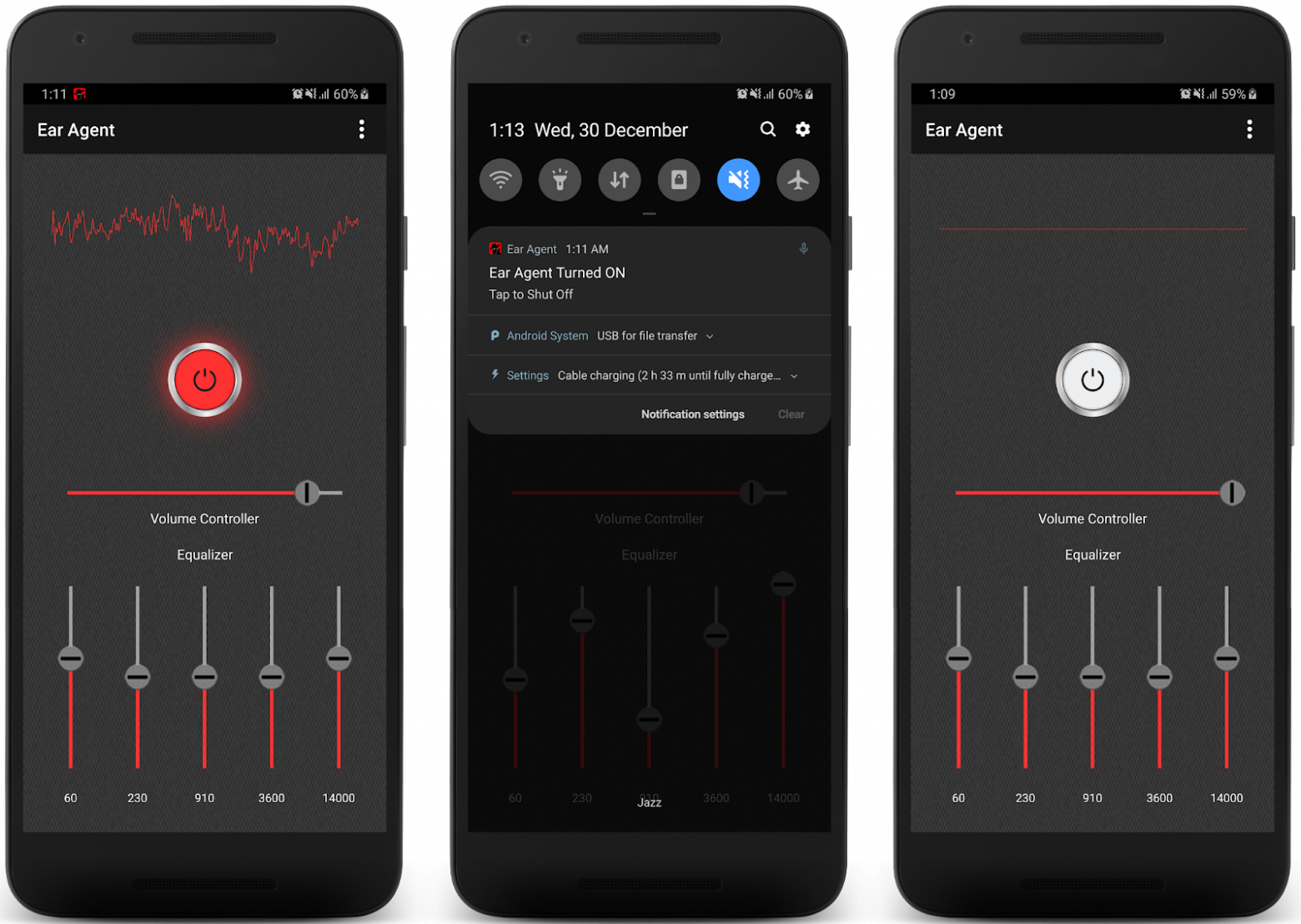
Using wireless headphones, recording sounds around the smartphone also becomes a possible function, but it should be remembered that using such methods may be illegal and violate private and legal rights. However, using a smartphone as a listening device can be useful to you in a variety of life situations.
The easiest way to carry out wiretapping is to install special software on the phone. There are several applications of this kind for Android smartphones, and one of the most popular is the free Ear Agent application, but it also has analogues. In essence, such applications are a regular sound amplifier for the hearing-impaired. True, exactly until the moment when you “forgot” your smartphone in the office of a competitor.

Everything is elementary here. We can add a bit of spy entourage using smart watches, if the devices have the functionality we need and support the appropriate communication protocols. This functionality has long been the norm for most smart watches and does not require the installation of additional applications. Use it, but do not forget about the legislation.
If the functionality of a smart watch for remote photography is not enough, it can be expanded using third-party applications. For example, DroidCam allows you to use your phone as a webcam for a PC. Similar applications allow you to control your phone's camera via a tablet. Here, everything is limited only by your requests and imagination in using your smartphone as a tool for remote photo and video shooting.
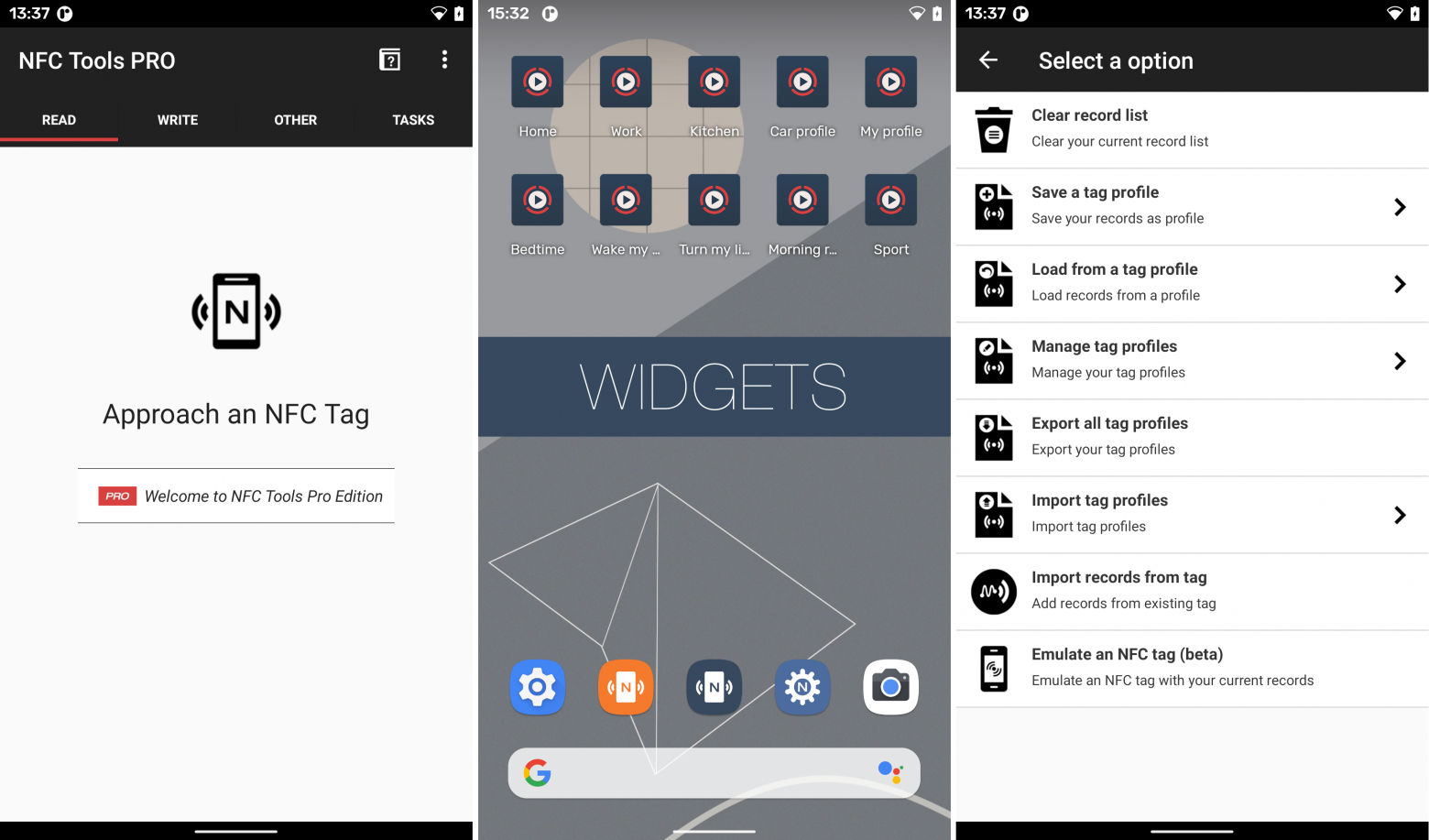
And this, in turn, becomes possible with specialized equipment and software that supports such a function. However, again, its use must be consistent with legal and ethical standards. The absolute favorite in this matter is the NFC Tools application, which allows you to read and create your own NFC tags.
In particular, NFC Tools allows you to copy information from one NFC card to another or create a clone of the card for use on different devices. Also, using the NFC Tools application, you can read data from NFC tags or labels and write new information to them. This will allow you, for example, to create a physical route for guards to patrol the territory, as well as control the regularity of such patrols.

It is important to remember that access to the office workstation and specialized software products must be carried out in accordance with security policies and have the appropriate permissions. But, in turn, this can become a useful function for remote monitoring and management of systems or applications. Trivial, but necessary.
For example, your databases or other services work only under Windows. Sometimes it is simply too lazy to carry a heavy work laptop with all its cables and chargers. An accessible method of using them is to use a remote desktop. You can do it, for example, using Chrome Remote Desktop applications. However, if you are a principled opponent of Google, you can also use the TeamViewer program. In the context of domestic software, it is worth taking a closer look at "RMS Remote Access". Here you have working IBM i2 with Maltego on a smartphone. Here you have work with a DBMS for a couple of terabytes.
Source
Smartphone at the service of a security guard
Modern smartphones provide security personnel with many opportunities to effectively perform their professional duties. I would like to point out right away that the quality of the mobile applications we will discuss directly depends on the components of your smartphone. For example, it is impossible to detect hidden wiring if your device does not have a metal detector. So, let's figure out which smartphone functions can be a useful aid in the work of an IBS/SB specialist.1. Detection of hidden cameras and bugs

Of course, this is an important task for security services. Security officers can use various equipment to detect hidden devices. This may include radio frequency signal detectors, optical scanners, thermal imagers, and other devices that can detect electromagnetic radiation or other signs of hidden devices. Smartphones usually do not have built-in functions for detecting bugs and hidden cameras. However, you can still use your smartphone as an auxiliary tool when searching for such devices.
In smartphone app stores, you can find software that detects hidden cameras. The effectiveness of such apps may be limited, as they rely on certain algorithms and sensors in the smartphone. For example, some smartphones have a built-in infrared receiver that can be used to detect infrared signals from hidden cameras or bugs (for example, Hidden Camera Detector or Glint Finder - Camera Detector).
In addition, even the built-in flashlight on your smartphone can help detect such cameras. Turn it on and illuminate the suspected area of the camera. If the camera has infrared LEDs, they may glow red or purple, which is not visible to the naked eye.

Also, some hidden cameras or microphones can be installed using magnets or hidden wiring. To detect them, you should use a smartphone with a built-in metal sensor and a corresponding pre-installed application (for example, Metal Sniffer: Metal Detector ). Cameras and microphones operating within the network space (WiFi) are also detected by a smartphone using special programs (for example, Fing - Network Tools or its analogues).
2. Alarm function

We can implement this function using various methods of responding to movement in the frame, device movement, turning on light or sound. And this, in turn, will allow us to notice suspicious activity and warn the user about a potential threat. An example of such use of a smartphone is the Haven application.
This app can use your smartphone’s microphone to detect various sounds, whether it’s just loud noises, knocks, or voices. It uses your smartphone’s built-in accelerometer and gyroscope to detect movement or vibration. If you have a front-facing camera, Haven can be used to detect changes in lighting. And if incidents are detected, Haven can send real-time notifications to your backup smartphone or email address.
3. Detecting technical surveillance

To detect anything related to outdoor surveillance, you can use BT/WiFi devices such as smartphones, trackers, headsets, and smart watches. Checking for connected devices and their activity can help you spot potential problems. My favorite app in this area is WiGLE (from Wireless Geographic Logging Engine).
WiGLE is an open-source project that collects and analyzes wireless network data. The app can passively collect information about cellular stations, WiFi routers, and Bluetooth devices with geolocation. This allows us to identify devices that are “moving” with us, i.e., can spy on us. WiGLE provides the approximate proximity of such devices, their names, and MAC addresses.
4. Remote listening and recording of background sounds

Using wireless headphones, recording sounds around the smartphone also becomes a possible function, but it should be remembered that using such methods may be illegal and violate private and legal rights. However, using a smartphone as a listening device can be useful to you in a variety of life situations.
The easiest way to carry out wiretapping is to install special software on the phone. There are several applications of this kind for Android smartphones, and one of the most popular is the free Ear Agent application, but it also has analogues. In essence, such applications are a regular sound amplifier for the hearing-impaired. True, exactly until the moment when you “forgot” your smartphone in the office of a competitor.
5. Remote photography and video recording

Everything is elementary here. We can add a bit of spy entourage using smart watches, if the devices have the functionality we need and support the appropriate communication protocols. This functionality has long been the norm for most smart watches and does not require the installation of additional applications. Use it, but do not forget about the legislation.
If the functionality of a smart watch for remote photography is not enough, it can be expanded using third-party applications. For example, DroidCam allows you to use your phone as a webcam for a PC. Similar applications allow you to control your phone's camera via a tablet. Here, everything is limited only by your requests and imagination in using your smartphone as a tool for remote photo and video shooting.
6. Reading, copying and writing NFC cards

And this, in turn, becomes possible with specialized equipment and software that supports such a function. However, again, its use must be consistent with legal and ethical standards. The absolute favorite in this matter is the NFC Tools application, which allows you to read and create your own NFC tags.
In particular, NFC Tools allows you to copy information from one NFC card to another or create a clone of the card for use on different devices. Also, using the NFC Tools application, you can read data from NFC tags or labels and write new information to them. This will allow you, for example, to create a physical route for guards to patrol the territory, as well as control the regularity of such patrols.
7. Remote access to video surveillance systems

It is important to remember that access to the office workstation and specialized software products must be carried out in accordance with security policies and have the appropriate permissions. But, in turn, this can become a useful function for remote monitoring and management of systems or applications. Trivial, but necessary.
For example, your databases or other services work only under Windows. Sometimes it is simply too lazy to carry a heavy work laptop with all its cables and chargers. An accessible method of using them is to use a remote desktop. You can do it, for example, using Chrome Remote Desktop applications. However, if you are a principled opponent of Google, you can also use the TeamViewer program. In the context of domestic software, it is worth taking a closer look at "RMS Remote Access". Here you have working IBM i2 with Maltego on a smartphone. Here you have work with a DBMS for a couple of terabytes.
And finally
A little about how to ensure the privacy of meetings without putting your smartphones in a safe. Any modern Android can enable the "Sensors off" button in the engineering menu - a function that activates a special icon in the curtain, using which you can quickly turn off the camera and microphone. It is enabled depending on the OS version and device in different ways. So, google it yourself in relation to your smartphone model. Enabling "Sensors off" completely blocks access of any applications to the device's camera and microphone.Source

