Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
The first reports of problems among users of Electrum cryptocurrency wallets began to appear back in December 2018, when criminals attacked the project's infrastructure and stole about a million dollars in cryptocurrency.
Then the Electrum developers called what was happening a phishing attack and, in essence, they were right, it really was phishing, although in an unusual format. Let me remind you that the attack was extremely simple: scammers found a way to show users of legitimate wallets officially looking messages, according to which the victim needs to immediately download and install the Electrum update from the GitHub repository. The repository indicated in the messages, of course, belonged to the attackers themselves and distributed malware that steals cryptocurrency.
The fact is that in order to process transactions, Electrum wallets connect to the Bitcoin blockchain through the Electrum server network known as ElectrumX. As a rule, wallet applications control who can manage such servers, but the Electrum ecosystem works differently: here anyone can raise an ElectrumX gateway server.
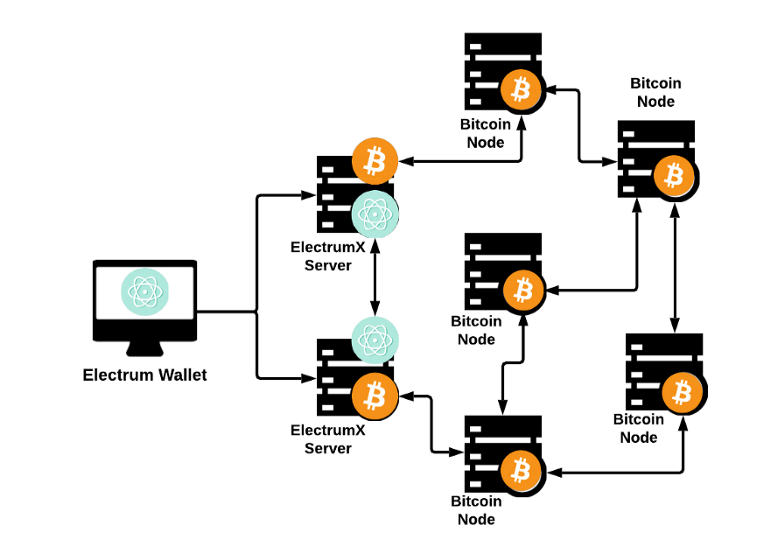
How Electrum works
It is this feature of the project that is abused by cybercriminals who deploy malicious nodes and send users fake messages about the need to urgently update the wallet. Usually, the download link for such an "update" does not lead to the official Electrum website (electrum.org), but to a similar domain or directly to the GitHub repository.
If the victim does not pay attention to the URL, they install the malicious version of Electrum on their machine, and the next time the user tries to use the wallet, the malware will ask him for a one-time password. Such passwords are requested only to confirm the transfer of funds, and not when launching the wallet, however, users regularly fall for the bait of scammers and enter the requested code, thereby giving the malware official permission to transfer all their funds to the attacker's account ...
Unfortunately, by mid-2019 the situation had changed only for the worse, although the developers were releasing patches and trying to combat such attacks by exploiting a DoS vulnerability unknown to the public in old Electrum clients, forcing them to stop connecting to the attackers' nodes and update. The developers also implemented a server blacklisting system on ElectrumX servers and prevented servers from showing HTML pop-ups to end users. Alas, all this did not help much, and as of April 2019, scammers managed to steal about $ 4.6 million, and the Electrum infrastructure was attacked by a botnet whose maximum size exceeded 152,000 hosts.
Now, ZDNet reports that hackers have continued to use this attack pattern over the years, with some incidents occurring quite recently, in September 2020. Electrum users continue to receive fake pop-ups informing them of the need to update, and after the update, their funds are immediately gone to attackers.
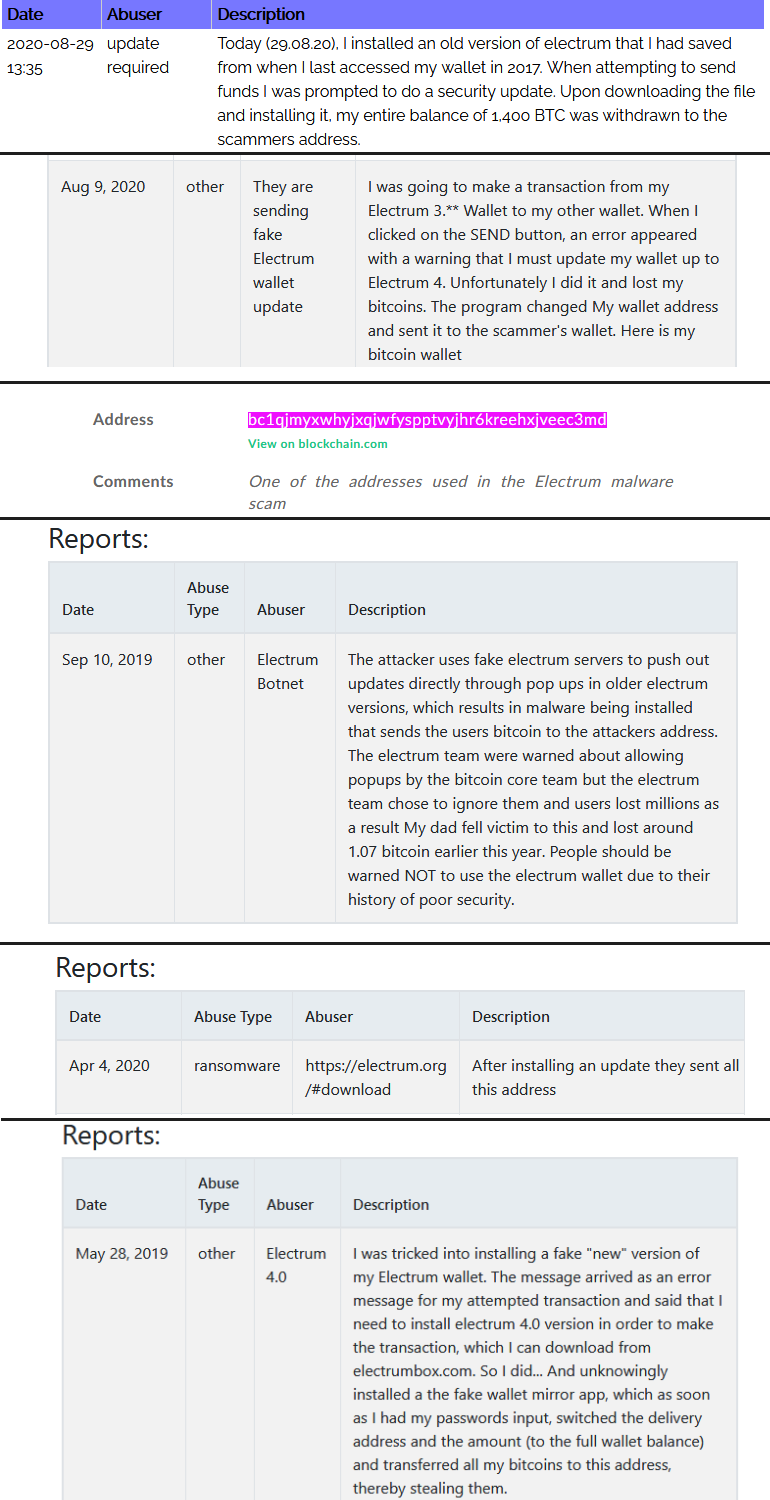
Complaints from affected users
According to journalists, currently in the wallets of the scammers who trade such attacks, there are about 1980 BTC, that is, approximately 22 million US dollars. If you add here 202 BTC stolen back in December 2018, the total amount of stolen funds is already more than $ 24.6 million.
Notably, most of these funds appear to have been stolen in one single incident: in August 2020, a user reported theft of 1,400 bitcoins (about $ 15,800,000) following an Electrum wallet update.
Then the Electrum developers called what was happening a phishing attack and, in essence, they were right, it really was phishing, although in an unusual format. Let me remind you that the attack was extremely simple: scammers found a way to show users of legitimate wallets officially looking messages, according to which the victim needs to immediately download and install the Electrum update from the GitHub repository. The repository indicated in the messages, of course, belonged to the attackers themselves and distributed malware that steals cryptocurrency.
The fact is that in order to process transactions, Electrum wallets connect to the Bitcoin blockchain through the Electrum server network known as ElectrumX. As a rule, wallet applications control who can manage such servers, but the Electrum ecosystem works differently: here anyone can raise an ElectrumX gateway server.

How Electrum works
It is this feature of the project that is abused by cybercriminals who deploy malicious nodes and send users fake messages about the need to urgently update the wallet. Usually, the download link for such an "update" does not lead to the official Electrum website (electrum.org), but to a similar domain or directly to the GitHub repository.
If the victim does not pay attention to the URL, they install the malicious version of Electrum on their machine, and the next time the user tries to use the wallet, the malware will ask him for a one-time password. Such passwords are requested only to confirm the transfer of funds, and not when launching the wallet, however, users regularly fall for the bait of scammers and enter the requested code, thereby giving the malware official permission to transfer all their funds to the attacker's account ...
Unfortunately, by mid-2019 the situation had changed only for the worse, although the developers were releasing patches and trying to combat such attacks by exploiting a DoS vulnerability unknown to the public in old Electrum clients, forcing them to stop connecting to the attackers' nodes and update. The developers also implemented a server blacklisting system on ElectrumX servers and prevented servers from showing HTML pop-ups to end users. Alas, all this did not help much, and as of April 2019, scammers managed to steal about $ 4.6 million, and the Electrum infrastructure was attacked by a botnet whose maximum size exceeded 152,000 hosts.
Now, ZDNet reports that hackers have continued to use this attack pattern over the years, with some incidents occurring quite recently, in September 2020. Electrum users continue to receive fake pop-ups informing them of the need to update, and after the update, their funds are immediately gone to attackers.

Complaints from affected users
According to journalists, currently in the wallets of the scammers who trade such attacks, there are about 1980 BTC, that is, approximately 22 million US dollars. If you add here 202 BTC stolen back in December 2018, the total amount of stolen funds is already more than $ 24.6 million.
Notably, most of these funds appear to have been stolen in one single incident: in August 2020, a user reported theft of 1,400 bitcoins (about $ 15,800,000) following an Electrum wallet update.

