Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
A security breach in the messenger allows you to find out the OS and devices of the interlocutor.
WhatsApp messenger has faced serious privacy problems. The application, known for its end-to-end encryption (E2EE) system, turned out to be vulnerable due to the peculiarities of working in Multi Device mode. According to a new study by Zengo, attackers can gain access to information about the devices they are using and even identify their operating system, making it much easier to prepare for attacks.
In Multi Device mode, each user's device must establish a separate encryption session with the interlocutor's devices. For example, sending a message from Alice to Bob with five connected devices requires the creation of five separate encrypted sessions. This leads to information leakage because senders can learn the details of recipients' devices, and the devices themselves store cryptographic keys, allowing active devices to be tracked over time.
Attackers gain access to the following data:
To clarify the data, the researchers studied the process of generating Message IDs on different platforms. It was revealed that the structure of ID varies depending on the operating system. For example, messages sent from a web client start with "3EB0," which allows the device to be identified as a web version.
A table showing the differences in Message ID length and prefix across WhatsApp platforms: Web, Android, iPhone, Mac, and Windows Desktop. The table includes information about the ID length, presence of prefixes, and additional notes for each platform to help with device analysis and tracking.
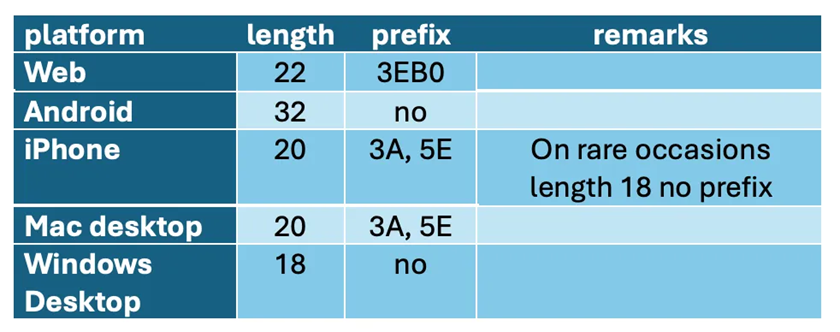
OS-specific prefixes
Not only can you differentiate between iPhone and Mac, but you can also check the device type (mobile or desktop) and its OS, which opens up the possibility of more accurate tracking of user activity.
The information obtained gives hackers a number of opportunities:
Even less experienced cybercriminals can use such a leak for surveillance. For example, finding a new device or using WhatsApp on a computer can be a cause for suspicion.
The researchers notified Meta of the problem on September 17 and received an initial response on the same day. However, the company did not take any follow-up action, and did not respond to additional requests. Experts decided to make their findings public, as similar vulnerabilities are already used in popular open-source projects such as whatsapp-web.js.
The authors of the report conclude that WhatsApp has always emphasized the importance of privacy through end-to-end encryption. However, the current situation demonstrates that the company's response to the detected security problems is not prompt enough. Simply changing the logic of generating a Message ID could eliminate the possibility of device identification, but so far no steps have been taken in this direction. At the moment, WhatsApp has not commented.
Source
WhatsApp messenger has faced serious privacy problems. The application, known for its end-to-end encryption (E2EE) system, turned out to be vulnerable due to the peculiarities of working in Multi Device mode. According to a new study by Zengo, attackers can gain access to information about the devices they are using and even identify their operating system, making it much easier to prepare for attacks.
In Multi Device mode, each user's device must establish a separate encryption session with the interlocutor's devices. For example, sending a message from Alice to Bob with five connected devices requires the creation of five separate encrypted sessions. This leads to information leakage because senders can learn the details of recipients' devices, and the devices themselves store cryptographic keys, allowing active devices to be tracked over time.
Attackers gain access to the following data:
- Number of devices: WhatsApp supports one primary mobile device and up to four secondary devices (desktop apps or the web);
- Long-term device identifiers: Each device receives a unique identifier that allows you to track its activity;
- Device type: You can determine whether the device is a primary mobile device or a secondary desktop device.
To clarify the data, the researchers studied the process of generating Message IDs on different platforms. It was revealed that the structure of ID varies depending on the operating system. For example, messages sent from a web client start with "3EB0," which allows the device to be identified as a web version.
A table showing the differences in Message ID length and prefix across WhatsApp platforms: Web, Android, iPhone, Mac, and Windows Desktop. The table includes information about the ID length, presence of prefixes, and additional notes for each platform to help with device analysis and tracking.

OS-specific prefixes
Not only can you differentiate between iPhone and Mac, but you can also check the device type (mobile or desktop) and its OS, which opens up the possibility of more accurate tracking of user activity.
The information obtained gives hackers a number of opportunities:
- Device operating system detection: Vulnerabilities are often OS-specific, allowing for targeted exploits;
- Choosing the least secure device: Desktop devices are usually less secure than mobile devices, making them a priority target;
- Active device detection: Attackers can wait until the desired device is not used to carry out an attack.
Even less experienced cybercriminals can use such a leak for surveillance. For example, finding a new device or using WhatsApp on a computer can be a cause for suspicion.
The researchers notified Meta of the problem on September 17 and received an initial response on the same day. However, the company did not take any follow-up action, and did not respond to additional requests. Experts decided to make their findings public, as similar vulnerabilities are already used in popular open-source projects such as whatsapp-web.js.
The authors of the report conclude that WhatsApp has always emphasized the importance of privacy through end-to-end encryption. However, the current situation demonstrates that the company's response to the detected security problems is not prompt enough. Simply changing the logic of generating a Message ID could eliminate the possibility of device identification, but so far no steps have been taken in this direction. At the moment, WhatsApp has not commented.
Source

