Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
A bundle of 14 critical 5Ghoul vulnerabilities leaves users no chance for security.
Recently, information about serious vulnerabilities in the firmware of 5G modems was published in the public domain, which affect the products of leading chipset manufacturers such as MediaTek and Qualcomm. These flaws pose a threat not only to USB and IoT modems, but also to hundreds of models of smartphones based on Android and iOS.
The researchers identified 14 vulnerabilities, collectively called " 5Ghoul "(from the English words 5G and Ghoul — "ghoul"). Of these, 10 concern 5G modems from MediaTek and Qualcomm, three of which are classified as high-severity vulnerabilities.
Especially worryingly, "5Ghoul vulnerabilities can be used to conduct attacks to break the connection, freeze the connection that requires a manual reboot, or downgrade the 5G connection to 4G," the study says.
Under threat were 714 smartphone models from 24 brands, including Vivo, Xiaomi, OPPO, Samsung, Honor, Motorola, realme, OnePlus, Huawei, ZTE, Asus, Sony, Meizu, Nokia, Apple and Google.
All of these security flaws were discovered by the ASSET Research Group at the Singapore University of Technology and Design. They previously disclosed the vulnerabilities of BrakTooth in September 2021 and SweynTooth in February 2020.
Attacks, in general, consist in "deception" of a smartphone or device with 5G, when attackers force them to connect to a malicious base station. "To do this, an attacker does not need to know secret information about the target hardware, such as SIM card details. It is enough just to simulate the operation of a legitimate base station, " the researchers explain.
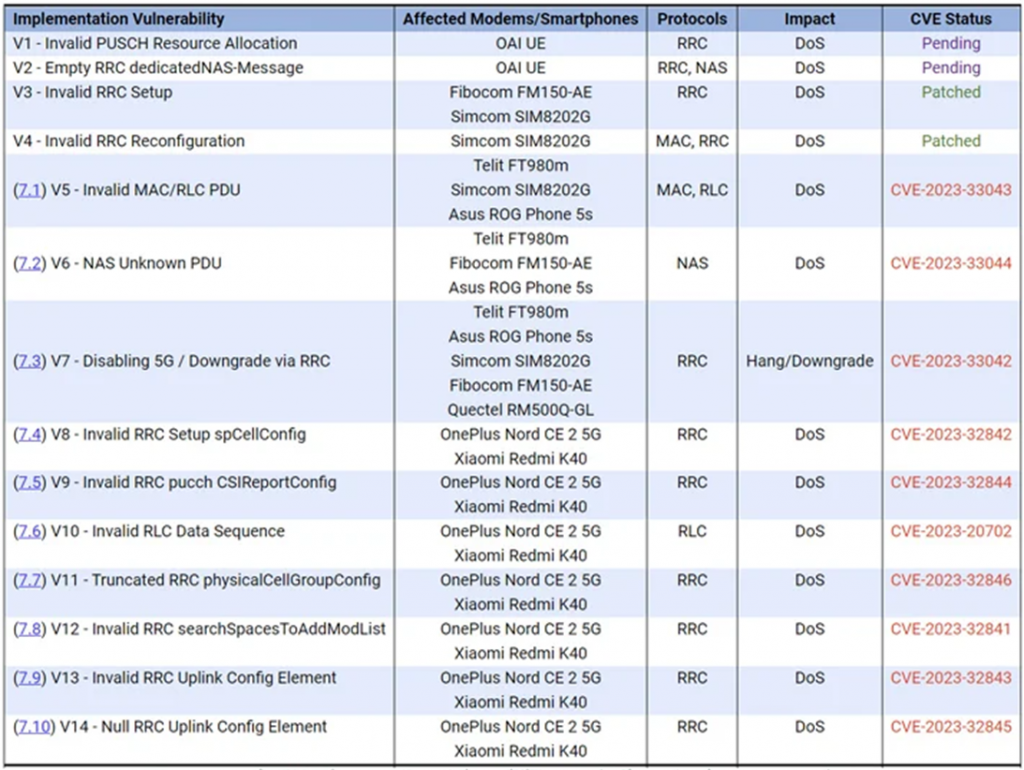
List of 5Ghoul vulnerabilities
One of the key vulnerabilities, CVE-2023-33042, allows an attacker in range to cause a downgrade of 5G communication quality or denial of service in the Qualcomm X55/X60 modem firmware by sending an incorrectly formed radio resource management frame to the target 5G device.
To successfully exploit other DoS vulnerabilities, you may need to manually reboot your device to restore 5G connectivity.
Patches from MediaTek and Qualcomm have already been released for 12 of the 14 identified vulnerabilities. Information about two uncorrected vulnerabilities is currently not disclosed for security reasons.
The researchers emphasize that detecting problems in the implementation of 5G modem firmware seriously affects suppliers of products going lower in the supply chain. It often happens that it may take six months or more for end users of such devices to receive a security update. This is due to the dependence of hardware manufacturers on modem and chipset suppliers, which introduces difficulties and delays in the patch release and distribution process.
Recently, information about serious vulnerabilities in the firmware of 5G modems was published in the public domain, which affect the products of leading chipset manufacturers such as MediaTek and Qualcomm. These flaws pose a threat not only to USB and IoT modems, but also to hundreds of models of smartphones based on Android and iOS.
The researchers identified 14 vulnerabilities, collectively called " 5Ghoul "(from the English words 5G and Ghoul — "ghoul"). Of these, 10 concern 5G modems from MediaTek and Qualcomm, three of which are classified as high-severity vulnerabilities.
Especially worryingly, "5Ghoul vulnerabilities can be used to conduct attacks to break the connection, freeze the connection that requires a manual reboot, or downgrade the 5G connection to 4G," the study says.
Under threat were 714 smartphone models from 24 brands, including Vivo, Xiaomi, OPPO, Samsung, Honor, Motorola, realme, OnePlus, Huawei, ZTE, Asus, Sony, Meizu, Nokia, Apple and Google.
All of these security flaws were discovered by the ASSET Research Group at the Singapore University of Technology and Design. They previously disclosed the vulnerabilities of BrakTooth in September 2021 and SweynTooth in February 2020.
Attacks, in general, consist in "deception" of a smartphone or device with 5G, when attackers force them to connect to a malicious base station. "To do this, an attacker does not need to know secret information about the target hardware, such as SIM card details. It is enough just to simulate the operation of a legitimate base station, " the researchers explain.

List of 5Ghoul vulnerabilities
One of the key vulnerabilities, CVE-2023-33042, allows an attacker in range to cause a downgrade of 5G communication quality or denial of service in the Qualcomm X55/X60 modem firmware by sending an incorrectly formed radio resource management frame to the target 5G device.
To successfully exploit other DoS vulnerabilities, you may need to manually reboot your device to restore 5G connectivity.
Patches from MediaTek and Qualcomm have already been released for 12 of the 14 identified vulnerabilities. Information about two uncorrected vulnerabilities is currently not disclosed for security reasons.
The researchers emphasize that detecting problems in the implementation of 5G modem firmware seriously affects suppliers of products going lower in the supply chain. It often happens that it may take six months or more for end users of such devices to receive a security update. This is due to the dependence of hardware manufacturers on modem and chipset suppliers, which introduces difficulties and delays in the patch release and distribution process.

