BadB
Professional
- Messages
- 1,866
- Reaction score
- 1,903
- Points
- 113

Hello. But let's immediately agree that I am not a provocateur. I only provide information for thought, and at the same time I point out security problems that can very well become federal problems if you do not distract from the budget cut in time and focus on the really important aspects.
This summer, a complete replacement of electricity meters began in the Moscow region. This know-how also affected our "collective farm". Instead of the good old home meters, small white boxes began to appear on the power poles, connected between the highway and the consumer.
Since my 2.5 miners had to be stopped, I was outraged and decided to figure out what kind of “new technologies” it was.
Until we suspected nothing in the bowels of Rostec, several projects were ripening at once within the framework of the Digital Transformation program. And since July 1, 2020, smart meters must be installed by all network and resource supply organizations.
Let's figure it out.
The “Smart Meter” was produced under the “ Strizh ” trademark by Igor Rotenberg's “Modern Radio Technologies” company. The device works on LPWAN technology and uses the proprietary XNB protocol. XNB is a closed protocol and its specifications could not be found in the public domain. However, not everything is so complicated. The XNB technology is based on the SigFox protocol, but there is much more information about it.

Smart counters "Strizh".
Astronomical budgets for the development of “digital technologies” are so large that not all companies can withstand their “cutting”. Feeling the federal scale, some employees of "Modern Radio Technologies" left the company, taking XNB with them and founded a new company WavIoT , which slightly modified the stolen XNB (or rather, SigFox) and issued the NB-Fi protocol.... WavIoT could not compete with Rotenberg's brainchild SRT, and in November 2017, its director, Evgeny Akhmadishin, was arrested by order of the Basmanny Court of Moscow on suspicion of fraud under Part 4 of Article 159 of the Criminal Code of the Russian Federation. According to the Unified State Register of Legal Entities, in April 2018, Vaviot LLC ceased its activities. But the products under this brand continue to develop through the Telematic Solutions company, where Evgeny Akhmadishin was also the CEO.
Be that as it may, at the heart of all Russian smart metering technologies, proprietary and not very much, is the SigFox protocol, which is not in demand in the West due to a large number of problems and a limited scope of application. In the Russian Federation, modifications of SigFox with minor changes are proposed to be used as a universal solution for “the entire Internet of things”. Those. technology with a huge number of fundamental flaws to make one single. Hurrah!
“Strizh” “smart meters” operating on the XNB protocol and using ON Semiconductor AX8052F143 chips are connected to base stations (BS) at a frequency of 868.8 MHz and transmit 8-byte data packets (in the case of “Strizh”). BSs can be located at a distance of up to 10 km, but in reality they are at a distance of up to 500 meters on the territories already covered by the system and transmit data to the Internet. The data transfer rate can be up to 50 bps, but in practice this value is somewhat lower. Consumption statistics are transmitted once an hour. The base LPWAN station is a Raspberry PI running Linux Debian Jessie in a sealed shockproof case with an SDR receiver and transmitter and a large antenna.

Base station of the Strizh system.
On servers, data is processed and provided in a convenient form in a specially designed web interface. The reverse communication channel operates at a frequency of 446.0 MHz and allows you to control individual devices and devices remotely, which allows, for example, disconnecting points for non-payment.
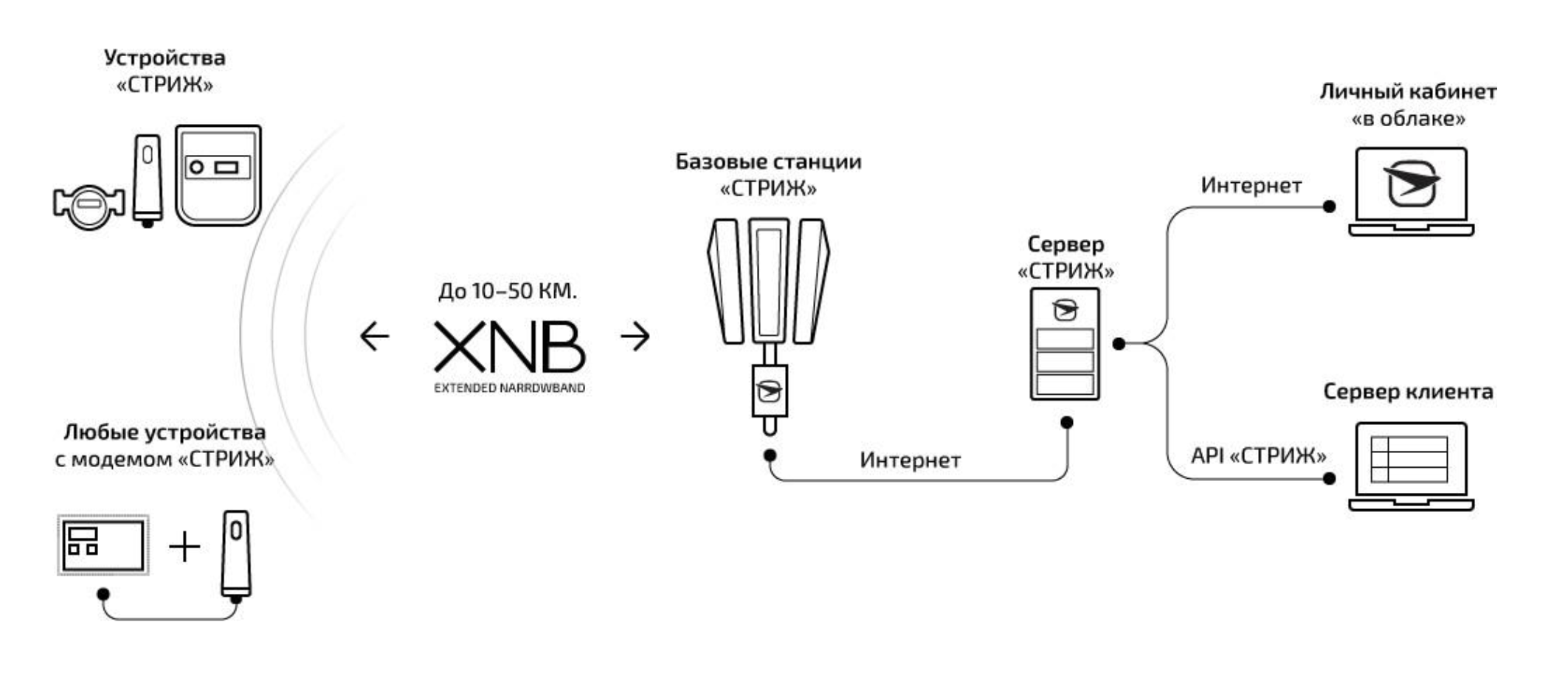
The architecture of the "Strizh" system.
The technical specification from the manufacturer is as follows:
| XNB radio protocol characteristics | Value |
| Signal modulation | DBPSK |
| Uplink transmission frequency | 868.8 MHz |
| Downlink transmission frequency | 446.0 MHz |
| Alternative operating frequencies | Up to 1GHz on request |
| Transmission speed | 50/100/1000 bit / s |
| Transmitter channel bandwidth | 100 Hz |
| Available number of channels in the ISM-band 868.8 MHz | 5000 channels |
| Efficiency of use of the ISM spectrum 868.8 MHz | High |
| Transmission power | 25 mW |
| Encryption | AES-128, XTEA-256, GOST R34.12-2015 |
| Anti-interference | FEC, CRC32, pseudo-random frequency hopping |
| Multiple access | Intelligent channel allocation |
| Remote firmware update of devices | Yes |
| Two-way communication channel | Yes |
| Signal transmission range | Up to 10 km in urban conditions Up to 50 km in the line of sight |
| Consumption for sending data packet | 35-40 mA for 10 seconds |
In practice, everything is much more prosaic from the vulnerable SigFox "Strizh" mainly by the presence of domestic encryption standards.
As we see in practice, in Russia, preference was given to wireless technologies, and this in itself is an epic fail. It’s half the trouble if the devices were used only for the transmission of telemetry from electricity meters, but the “Strizh” devices are also used at critical infrastructure facilities.
Radio - there is radio. Even the use of a simple jammer did not allow reading the data from the meter using the supplied control panel. The prolonged power on made technicians fuss and check devices all over the street. The device is not resistant to ddos attacks, and even through simple manipulations with bladeRF, there were serious jambs with reading the meter readings.
All data is transmitted on open frequencies 868.8 and 446.0 MHz. Even with a cursory study and despite encryption, the message header, sequence number, device number, encrypted load (which, despite sufficiently strong encryption, can also potentially be decrypted, since the encryption key is not generated dynamically), checksum and message authentication code (MAC).
In case of remote firmware update initiated from the base station, the encryption key is transmitted in clear text!
Needless to say ... If the use of jammers and ddos attacks on electricity meters can only entail incorrect metering of consumed electricity (and criminal liability, since such actions are illegal), then in the case of critical infrastructure, the consequences can be dire. Imagine an incorrectly calculated volume of pumped gas or a radio-controlled steam valve not closed in time! The consequences can be dire.
But nobody thinks about it. Everyone is just sawing the budget.
Saw, Arkady Romanovich, saw, they are digital.
P.S. IoT infrastructure security problems are present not only in Russia. Nevertheless, instead of copying unsafe “foreign” technologies and calling them “domestic developments, we are stepping on the same rake. Alas, for financial reasons. Sooner or later, this will lead first to collapse, and then to re-realization. But won't it be too late?
