Man
Professional
- Messages
- 3,222
- Reaction score
- 988
- Points
- 113

Transferring information from an air-gapped computer is a non-trivial task, since it is disconnected from the network and is usually located in a separate room. But it is possible through third-party channels. For example, removing electromagnetic radiation from a video card or other components on the motherboard, recognizing keystrokes by sound, etc.
There is another area of research in which various PC components are used as "beacons" to send a signal to a remote observer. This can be done by transmitting one or more words or numbers. For example, a secret password or hardware configuration from a secret computer.
In particular, the signal can be sent by blinking the HDD LED, router or keyboard, electromagnetic radiation from the USB bus, sounds from the GPU cooler and HDD magnetic head, through thermal radiation and audio speakers (ultrasound), changes in PC power consumption and display brightness, fan vibrations, etc.
Recently, a new method has been added to this list: radio transmission using a SATA cable (standard red cable for connecting SSD, HDD and CD / DVD).
The SATA connector has seven contacts, including three grounds (1, 4, 7), two for transmission (2, 3) and two for reception (5, 6):

The SATA interface constantly transmits electromagnetic radiation in the background in the ranges of 1 GHz, 2.5 GHz, 3.9 GHz and about 6 GHz. The signal characteristics can be used to distinguish between read and write operations:

For the radio beacon to work, you need to mix a useful signal into this broadcast - and then catch it on the receiver side. In this case, files transmitted via SATA 3.0 were used as distinguishable radio pulses. Each such transmission is distinguishable on the spectrogram. Accordingly, they can be used for the beacon and to encode useful information.
The algorithm for generating a SATA 3.0 signal for a given byte sequence:

On the receiver side, a software radio (Software Defined Radio) is used, which records the signal in the range from 5.9 to 6 GHz. After the Fourier transform, the headers of the beginning of the packets are recognized and the payload is extracted.
The signal decoding algorithm is:

The nice thing about this malware is that it can be inserted into the working memory directly from the browser as a separate process, and this will not arouse suspicion in the antivirus. After all, the malicious code simply writes and reads files in temporary folders, which is completely normal. The process does not transmit any information over the network and does not contact the remote server, that is, it does not do anything suspicious.

A radio broadcast recording receiver should be placed near the infected computer.
SATAn attack
The experimental radio transmission was conducted from three desktops equipped with a Transcend 256GB MLC SATA III 6Gb/s 2.5” Solid State Drive 370 drive running Linux Ubuntu 20.04.1 64-bit.
The ADALM PLUTO Software-defined Radio (SDR) AD9364 RF device connected via USB to a computer running Windows 10 was used as a receiver, and demodulation was performed by a script in the MathWorks MATLAB program.
The word SECRET in the radio channel:

Transmission spectrogram with different timings:
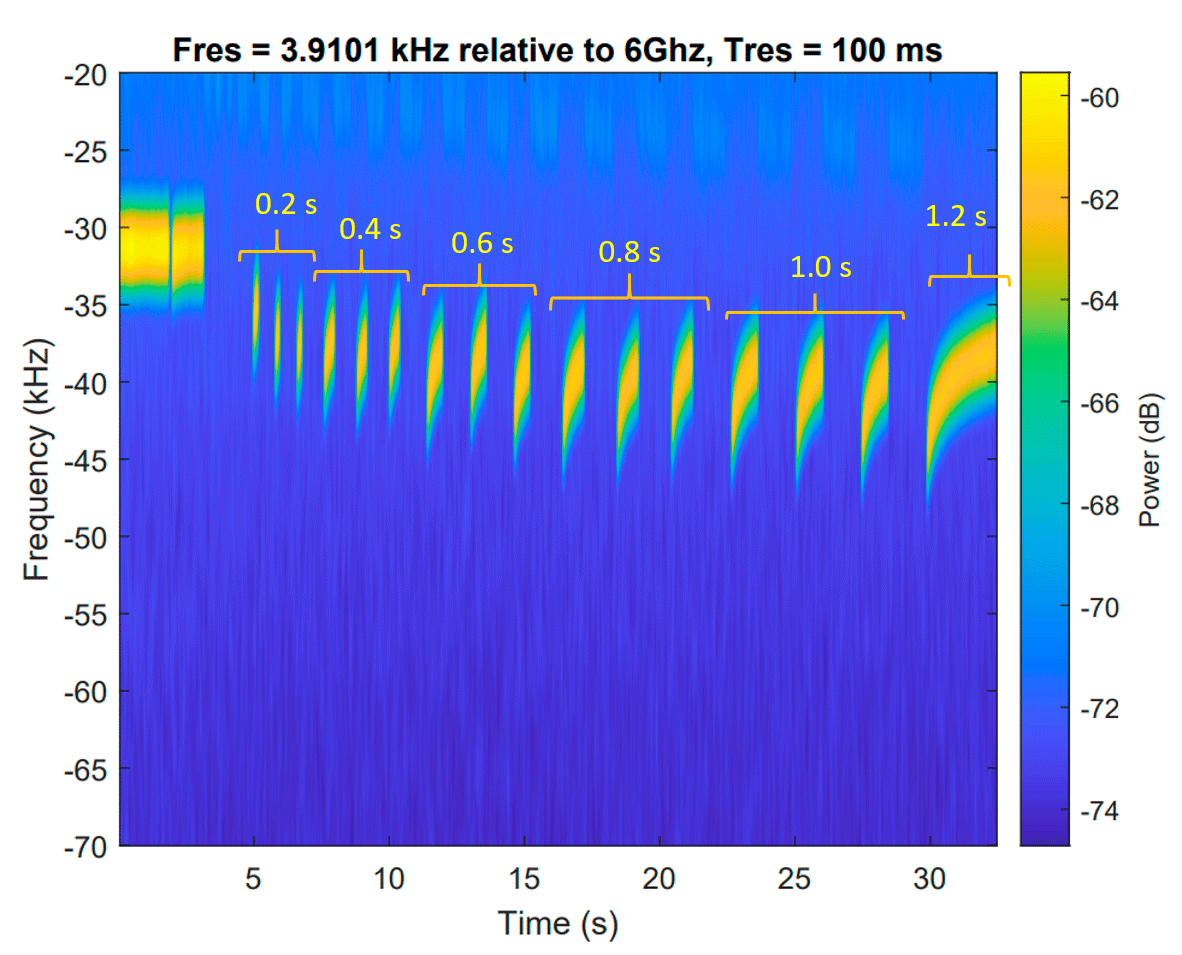
The experiment showed the possibility of successful reception of information at a distance of up to 90 cm from the transmitter, while at a distance the error rate increases to 15%. SATA activity during reading and writing stands out strongly from the general signal. A research article by Mordechai Guri from Ben-Gurion University of the Negev (Israel) was published on July 15, 2022, on the preprint website arXiv.org (doi: 10.48550/arXiv.1803.03422).
As a protective measure, experts recommend shielding the case and prohibiting the use of radio receiving devices near computers.
Source
