Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
The updated solution for combating fraud ("fraud") WEB ANTIFRAUD v2 has expanded its functionality and now additionally allows you to timely determine the use of software for remote access to a protected resource. In addition, the new version of the system controls and protects all pages of the user's personal account, and not just the authorization form. In the review, we will look at what the updated WEB ANTIFRAUD v2 fraud monitoring system is, and also test its new capabilities.
AM Test Lab Certificate
Certificate Number: 304
Date of issue: 18.09.
Validity: 09/18/2025
Content
1. Introduction
2. Major changes in WEB ANTIFRAUD v2
3. Problems of remote access to a device (resources)
4. Why port scanning is ineffective
5. Definition of remote access in WEB ANTIFRAUD v2
5.1 Remote Access Software Discovery: LogMeIn
5.2 Remote Access Software Discovery: NetSupport
5.3. Remote Access Software Detection: AnyDesk
5.4. Remote Access Software Detection: UltraVNC
5.5. Remote Access Client Discovery: RDP
5.6. Remote Access Software Discovery: TeamViewer
6. Analytics of the WEB ANTIFRAUD v2 system
7. Conclusions
To further exacerbate the problem of information security of remote work, company employees use home desktops, as well as personal laptops and smartphones, which can be easily accessed (due to lack of proper attention and control on the part of the user) intruders.
Therefore, for a high-quality and safe organization of remote work, an integrated approach is needed, where, among other things, it is necessary to have a system for combating cyber fraud, which will conduct timely monitoring and analysis of all user actions and guaranteed to identify malicious activity among them.
We have already reviewed the WEB ANTIFRAUD antifraud system earlier. This article will focus on its updated version - WEB ANTIFRAUD v2.
Also, the updated version of WEB ANTIFRAUD determines whether user information has been intercepted using phishing, by checking the current IP address for the use of proxy servers or other means of anonymization. The updates directly affected the user's personal account: now WEB ANTIFRAUD can track fraudulent activity on any of its pages.
The new version of the product makes it possible to more effectively link fraudulent accounts and their actions with each other; the mechanism for determining the behavioral and technical "fingerprint" of the user has been improved, as well as the line of support for mobile devices has been expanded.
It is also important that the updated version uses a redesigned client API, which has a positive effect on the integration capabilities and the flexibility of the system as a whole.
The following can be singled out as the main security problems in the implementation of remote access of company employees to its information resources:
The creators of WEB ANTIFRAUD came to the conclusion that it is ineffective and undesirable to use scanning of open network ports of a user device to detect unwanted software, with the help of which it is possible to gain remote access to an object. There are the following reasons for this:
It is also not entirely correct to use a reverse ping of a user's IP address for the following reasons:
Thus, the effectiveness of the above technologies for detecting unwanted software in the existing realities is much lower than necessary, and false alarms of user security systems due to scanning network ports can even lead to undeserved reputational losses not only in organizations where such an antifraud system was used. but also in companies that were involved in its development, configuration and installation.
Figure 1. Test bench for testing the new WEB ANTIFRAUD v2 function for determining remote access
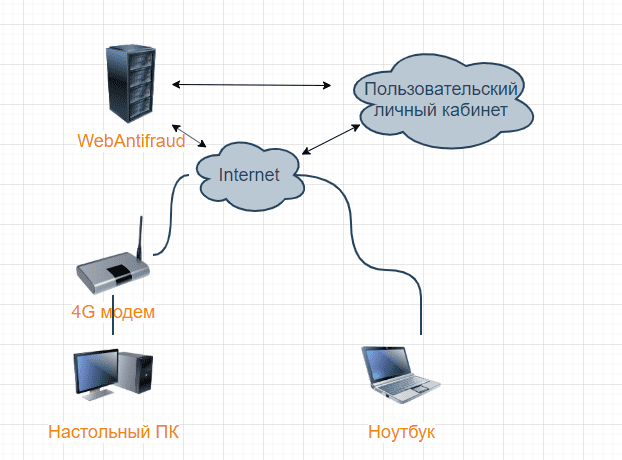
From Figure 1, you can see that the test bench used two workstations that simulate an attacker (desktop) and a potential victim (laptop). Internet access on a desktop PC was carried out using a 4G modem, and a physical cable leased line was used in the laptop. Both systems came with fresh Windows 10 preinstalled; access to the user account protected by the WEB ANTIFRAUD v2 anti-fraud system was carried out through the Google Chrome browser.
To conduct the most ambitious and objective testing, we have chosen the most popular software today in the area of interest to us, namely LogMeIn, NetSupport, AnyDesk, UltraVNC, TeamViewer and the Windows Remote Desktop client. For the purity of the experiment, all programs were downloaded from the official information resources of the developer companies. Products for remote access were installed and tested strictly one by one to exclude their influence on each other and the occurrence of abnormal situations that could lead to false positives of the tested anti-fraud system.
After installing and configuring the program, we carry out the procedure of remote connection to the workstation of the "victim". Next, we try to get into the user's personal account (Fig. 2).
Figure 2. The page for remote authorization in your personal account using LogMeIn
After successfully gaining remote access to the user's personal account, the WEB ANTIFRAUD system did not disregard this event, which is noted in the log of detected incidents (see Fig. 3).
Figure 3. Incident detection record - remote access using LogMeIn
Figure 4. Incident Record - Remote Access Using NetSupport

After successful authorization and imitation of the attacker's actions in the personal account, the system successfully determined the use of software for remote access (Fig. 5).
Figure 5. Incident detection record - remote access using AnyDesk
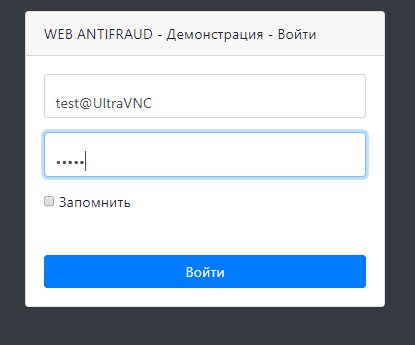
Figure 6. The page for remote authorization in your personal account using UltraVNC
We see that the anti-fraud system quickly detected this incident as well, which is noted in the log (Fig. 7).
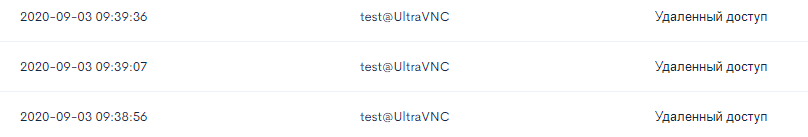
Figure 7. Incident Record - Remote Access with UltraVNC
 [/URL]
[/URL]
After a short setup of the client, we get remote access to the laptop, which imitates the victim of an intruder. As in the previous tests, we try to log in to the user's personal account.
The authorization is successful. As you can see from Figure 8, the system detected the incident and recorded information about it in the log.
Figure 8. Incident Record - Remote Access Using RDP Client
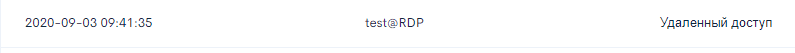
Download TeamViewer version 15.9.4 from the official source. Next, we configure the product and get the remote access we need. We log in to the user's personal account.
Figure 9 shows an entry from the log of the WEB ANTIFRAUD analytics system, in which the detection of software for remote access is noted.
Figure 9. Incident detection record - Remote access via TeamViewer
Next, we define which open local port is currently being used for remote access by the TeamViewer software.
Figure 10. Determining the used local port
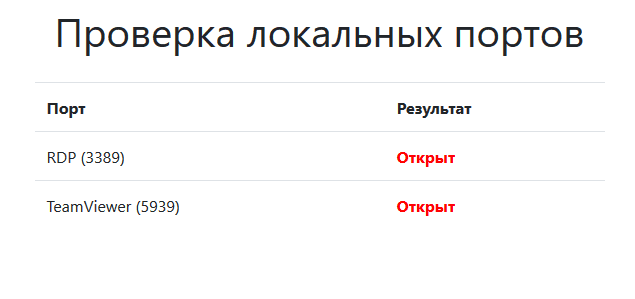
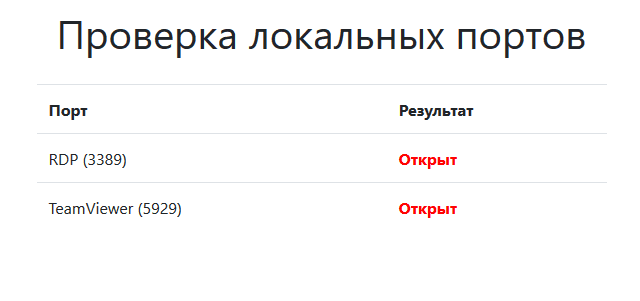
As follows from Figure 10, TeamViewer uses the local port 5939 for remote access. To test the declared feature of WEB ANTIFRAUD, namely, the lack of scanning local ports to determine the software used, we will try to change the TeamViewer port to an arbitrary one, for example, 5929. In the figure 11 you can see that the used local port in TeamViewer has changed to the required one.
Figure 11. Determining the changed local port
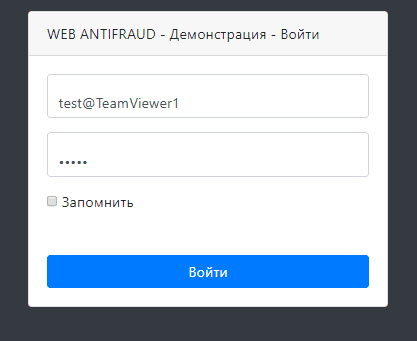
Now we get remote access again and try to log in to the user's personal account. The authorization process is shown in Figure 12.
Figure 12. Login page in your personal account using TeamViewer on the 5929 local port
After successful authorization, we check the WEB ANTIFRAUD incident log and make sure that the anti-fraud system successfully detects such incidents and enters all the information about them necessary for further investigation into the protocol (Fig. 13).
Figure 1 3. Incident detection record - remote access with TeamViewer using a non-standard network port
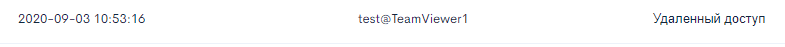
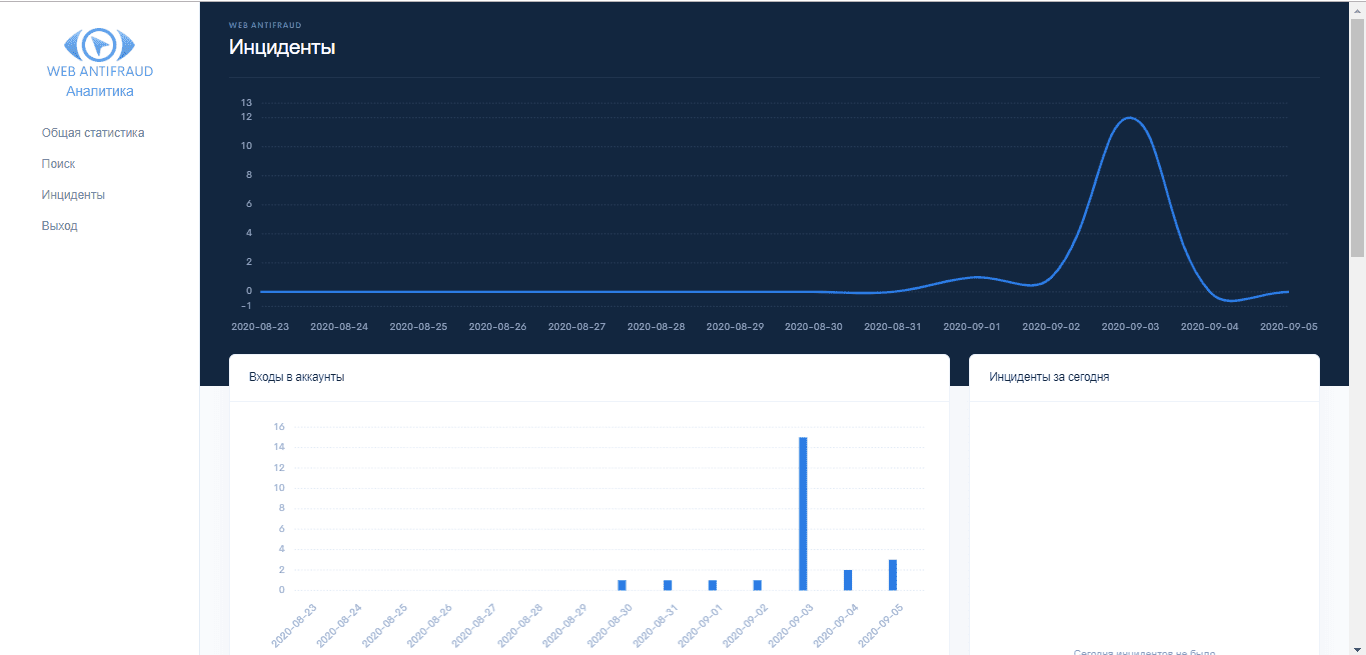
Figure 14. Graphical presentation of detected incidents on the main page in the WEB ANTIFRAUD system
All identified incidents are recorded in the corresponding log (Fig. 15).
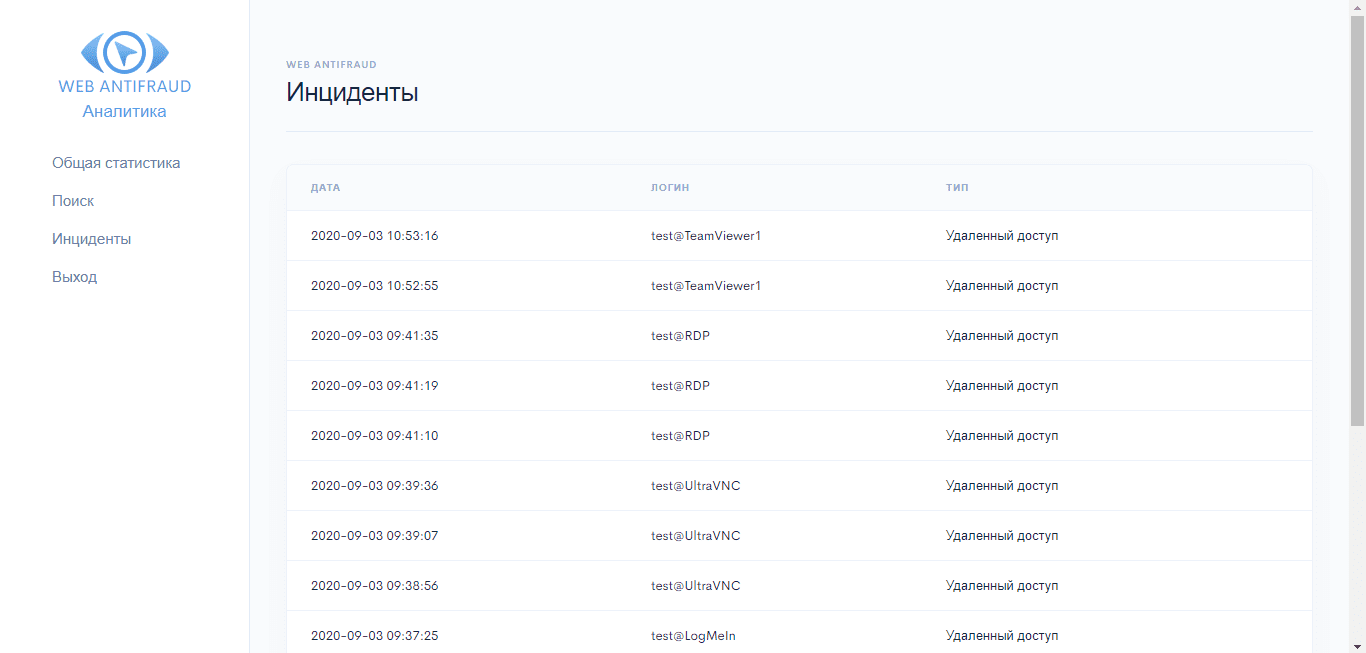
Figure 15. List of detected incidents on the general statistics page in the WEB ANTIFRAUD system
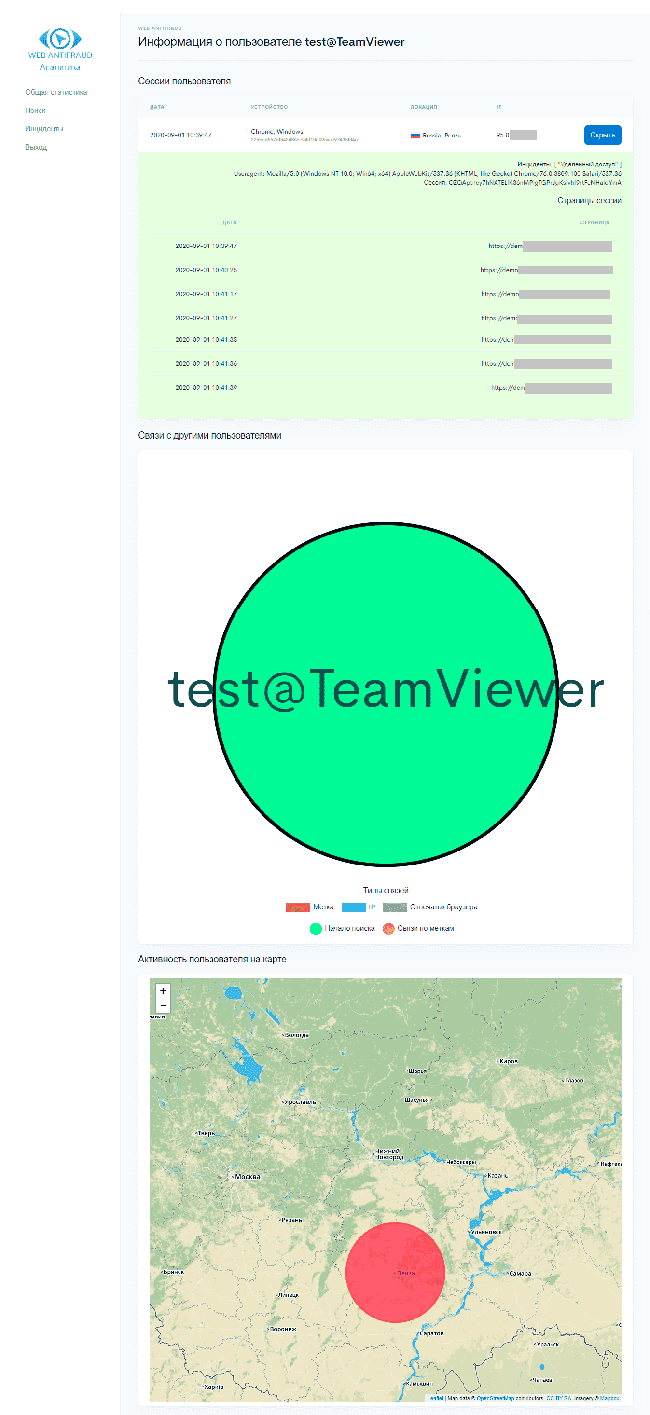
For each user and for each detected incident, the WEB ANTIFRAUD analytics system allows you to obtain (through the "Search" menu item) detailed information for conducting an objective investigation, as well as, if necessary, for choosing an adequate response. Figure 16 shows all the collected information on a remote access incident using TeamViewer software.
Figure 16. Incident information: Remote access using TeamViewer software
During testing, it was found that a new function of the system - determining the use of software for remote access when accessing a protected resource - works correctly and quite efficiently. We also found that the WEB ANTIFRAUD v2 system successfully detects such software even when changing standard network ports; this proves that the system does not scan them according to a fixed list, thereby preventing false alarms of antivirus protection and firewalls on the user's side.
Advantages:
Disadvantages:
The system developer can be contacted via the official website or via a twitter account (@AntiFraud2ru).
AM Test Lab Certificate
Certificate Number: 304
Date of issue: 18.09.
Validity: 09/18/2025
Content
1. Introduction
2. Major changes in WEB ANTIFRAUD v2
3. Problems of remote access to a device (resources)
4. Why port scanning is ineffective
5. Definition of remote access in WEB ANTIFRAUD v2
5.1 Remote Access Software Discovery: LogMeIn
5.2 Remote Access Software Discovery: NetSupport
5.3. Remote Access Software Detection: AnyDesk
5.4. Remote Access Software Detection: UltraVNC
5.5. Remote Access Client Discovery: RDP
5.6. Remote Access Software Discovery: TeamViewer
6. Analytics of the WEB ANTIFRAUD v2 system
7. Conclusions
Introduction
Due to today's realities, namely, the unfavorable epidemiological situation that is developing around the world, many companies were forced to transfer most of their staff to remote work. On the one hand, these measures allow not to stop business processes and make it possible to protect staff and customers from mass infection, as well as save a considerable part of the financial resources that would be used to support office activity. On the other hand, all these measures inevitably entail the emergence of serious cyber threats that are directly aimed at the information assets of companies.To further exacerbate the problem of information security of remote work, company employees use home desktops, as well as personal laptops and smartphones, which can be easily accessed (due to lack of proper attention and control on the part of the user) intruders.
Therefore, for a high-quality and safe organization of remote work, an integrated approach is needed, where, among other things, it is necessary to have a system for combating cyber fraud, which will conduct timely monitoring and analysis of all user actions and guaranteed to identify malicious activity among them.
We have already reviewed the WEB ANTIFRAUD antifraud system earlier. This article will focus on its updated version - WEB ANTIFRAUD v2.
Major changes in WEB ANTIFRAUD v2
The main difference from the previous release is the function that detects the use of software and various clients to obtain remote access to the protected resource (device), and without scanning open ports in the system and pinging back users.Also, the updated version of WEB ANTIFRAUD determines whether user information has been intercepted using phishing, by checking the current IP address for the use of proxy servers or other means of anonymization. The updates directly affected the user's personal account: now WEB ANTIFRAUD can track fraudulent activity on any of its pages.
The new version of the product makes it possible to more effectively link fraudulent accounts and their actions with each other; the mechanism for determining the behavioral and technical "fingerprint" of the user has been improved, as well as the line of support for mobile devices has been expanded.
It is also important that the updated version uses a redesigned client API, which has a positive effect on the integration capabilities and the flexibility of the system as a whole.
Problems of remote access to a device (resources)
Providing employees with remote access to internal information resources of a company is for many organizations the only opportunity at the moment to stay “afloat” and not stop business processes. Not everyone succeeds in fully taking into account the threats and risks of such work, although there are a lot of them and the probability of their occurrence is high.The following can be singled out as the main security problems in the implementation of remote access of company employees to its information resources:
- The problem of correct operation, configuration, as well as timely updating by the user on home information systems from which remote access is carried out, of personal protection means (antivirus software, firewall). Personal computers, laptops, smartphones and tablets, as well as home local networks in the absence or improper configuration / operation of security programs are at risk. Threat sources include, for example, the ability to steal passwords and confidential information from user traffic. The importance of the issue of social engineering is also keenly felt. The user may not recognize the phishing link, and then attackers, for example, will receive authentication information from the employee's personal account.
- The problem of using unlicensed software. In this case, we are talking about pirated versions of operating systems and publicly available protection tools. Even if such an antivirus or firewall is configured correctly and is updated in a timely manner, it is possible that the internal product code changes in order to hide the use of an unlicensed version; then it will be difficult to guarantee the required level of protection. The same can be said for operating systems. As a rule, pirates disable update mechanisms in them, and it may not be possible to install security patches from an official source. Thus, the usefulness of any, even the most modern and well-configured, means of protection is reduced to zero, since there is a high probability of the existence of software bookmarks at the OS level.
- The problem of changing the protective perimeter. Companies, as a rule, have been building an optimal system for ensuring internal information security for years and constantly monitoring the strategies used to combat threats in order to determine the effectiveness of countering intruders. Relocating employees to remote work expands and erodes this perimeter, and also often nullifies the effectiveness of the aforementioned strategies, since workplaces fall out of the sight of information security administrators (officers) and IT professionals.
Why port scanning is ineffective
A tool for better detection of fraudulent activity is intended to be the functionality that makes it possible to determine the presence of programs (including Trojans) for remote access to a protected object. Most often, developers of anti-fraud systems solve this problem by scanning network ports open on a user device that can potentially be used by such software, as well as by measuring the ping time.The creators of WEB ANTIFRAUD came to the conclusion that it is ineffective and undesirable to use scanning of open network ports of a user device to detect unwanted software, with the help of which it is possible to gain remote access to an object. There are the following reasons for this:
- Having an open port does not mean that the device is guaranteed to be used by an attacker.
- Both false positive and false negative results are possible during port scans.
- An open port can be used by a legitimate user program.
- Remote port scanning mostly triggers the triggering of protective systems (antivirus software and firewalls), blocking "malicious" activity and notifying the user about the detected attack.
- Port scanning increases network latency.
It is also not entirely correct to use a reverse ping of a user's IP address for the following reasons:
- Many companies route all user traffic through various proxy servers or use a corporate VPN.
- The security system can be configured in such a way that there is no reaction to external pings.
- Different topology and non-obviousness of the network can give false scan results.
Thus, the effectiveness of the above technologies for detecting unwanted software in the existing realities is much lower than necessary, and false alarms of user security systems due to scanning network ports can even lead to undeserved reputational losses not only in organizations where such an antifraud system was used. but also in companies that were involved in its development, configuration and installation.
Definition of remote access in WEB ANTIFRAUD v2
In order to test the function of searching for software for remote access, a test bench was assembled, which is schematically shown in Figure 1.Figure 1. Test bench for testing the new WEB ANTIFRAUD v2 function for determining remote access

From Figure 1, you can see that the test bench used two workstations that simulate an attacker (desktop) and a potential victim (laptop). Internet access on a desktop PC was carried out using a 4G modem, and a physical cable leased line was used in the laptop. Both systems came with fresh Windows 10 preinstalled; access to the user account protected by the WEB ANTIFRAUD v2 anti-fraud system was carried out through the Google Chrome browser.
To conduct the most ambitious and objective testing, we have chosen the most popular software today in the area of interest to us, namely LogMeIn, NetSupport, AnyDesk, UltraVNC, TeamViewer and the Windows Remote Desktop client. For the purity of the experiment, all programs were downloaded from the official information resources of the developer companies. Products for remote access were installed and tested strictly one by one to exclude their influence on each other and the occurrence of abnormal situations that could lead to false positives of the tested anti-fraud system.
Remote Access Software Discovery: LogMeIn
First on the list was LogMeIn, version 4.1.0.13744. To correctly configure the software, official information was used, which can be found on the website of the developer company.After installing and configuring the program, we carry out the procedure of remote connection to the workstation of the "victim". Next, we try to get into the user's personal account (Fig. 2).
Figure 2. The page for remote authorization in your personal account using LogMeIn

After successfully gaining remote access to the user's personal account, the WEB ANTIFRAUD system did not disregard this event, which is noted in the log of detected incidents (see Fig. 3).
Figure 3. Incident detection record - remote access using LogMeIn

Remote Access Software Discovery: NetSupport
Next, we tested the use of NetSupport software (version 12.80.5). Just as in the previous case, after installation and configuration, we perform the remote connection procedure and try to get into the user's personal account. As a result, we see that the analytics of WEB ANTIFRAUD recorded this attempt as well (Fig. 4).Figure 4. Incident Record - Remote Access Using NetSupport

Remote Access Software Detection: AnyDesk
Next, let's check the reaction of the WEB ANTIFRAUD system to the use of the AnyDesk program by an attacker (version 6.0.7). Similar to the previous tests, we install and configure the software, after which we get remote access to the workplace of the "victim" and try to log in on her behalf.After successful authorization and imitation of the attacker's actions in the personal account, the system successfully determined the use of software for remote access (Fig. 5).
Figure 5. Incident detection record - remote access using AnyDesk

Remote Access Software Detection: UltraVNC
The next product tested was UltraVNC, version 1.2.4.0. Install and configure it using the official source. Next, we successfully get remote access and try to log in to the protected personal account.Figure 6. The page for remote authorization in your personal account using UltraVNC

We see that the anti-fraud system quickly detected this incident as well, which is noted in the log (Fig. 7).
Figure 7. Incident Record - Remote Access with UltraVNC

Remote Access Client Discovery: RDP
Now we will test the reaction of the system to the use of the most common external control tool - the built-in Windows Remote Desktop (RDP) client. Since it is available in most versions of this family of operating systems, we could not ignore it.After a short setup of the client, we get remote access to the laptop, which imitates the victim of an intruder. As in the previous tests, we try to log in to the user's personal account.
The authorization is successful. As you can see from Figure 8, the system detected the incident and recorded information about it in the log.
Figure 8. Incident Record - Remote Access Using RDP Client
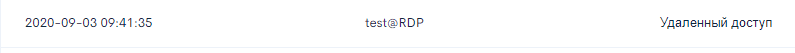
Remote Access Software Discovery: TeamViewer
To conclude the testing of the remote access software search function, we will find out how the ANTIFRAUD WEB system will react to the use of the TeamViewer software. We will also try to change the network ports used by this popular product and see the result.Download TeamViewer version 15.9.4 from the official source. Next, we configure the product and get the remote access we need. We log in to the user's personal account.
Figure 9 shows an entry from the log of the WEB ANTIFRAUD analytics system, in which the detection of software for remote access is noted.
Figure 9. Incident detection record - Remote access via TeamViewer

Next, we define which open local port is currently being used for remote access by the TeamViewer software.
Figure 10. Determining the used local port

As follows from Figure 10, TeamViewer uses the local port 5939 for remote access. To test the declared feature of WEB ANTIFRAUD, namely, the lack of scanning local ports to determine the software used, we will try to change the TeamViewer port to an arbitrary one, for example, 5929. In the figure 11 you can see that the used local port in TeamViewer has changed to the required one.
Figure 11. Determining the changed local port

Now we get remote access again and try to log in to the user's personal account. The authorization process is shown in Figure 12.
Figure 12. Login page in your personal account using TeamViewer on the 5929 local port

After successful authorization, we check the WEB ANTIFRAUD incident log and make sure that the anti-fraud system successfully detects such incidents and enters all the information about them necessary for further investigation into the protocol (Fig. 13).
Figure 1 3. Incident detection record - remote access with TeamViewer using a non-standard network port

Analytics of the WEB ANTIFRAUD v2 system
System analytics have largely remained unchanged from the previous version. On the main screen, you can see a graphical representation of the identified incidents (Fig. 14); in our case, all incidents relate to the detection of software for remote access.Figure 14. Graphical presentation of detected incidents on the main page in the WEB ANTIFRAUD system

All identified incidents are recorded in the corresponding log (Fig. 15).
Figure 15. List of detected incidents on the general statistics page in the WEB ANTIFRAUD system

For each user and for each detected incident, the WEB ANTIFRAUD analytics system allows you to obtain (through the "Search" menu item) detailed information for conducting an objective investigation, as well as, if necessary, for choosing an adequate response. Figure 16 shows all the collected information on a remote access incident using TeamViewer software.
Figure 16. Incident information: Remote access using TeamViewer software

Conclusions
The updated WEB ANTIFRAUD v2 fraud monitoring system is an effective tool for detecting the fact of a user device being compromised and timely detecting fraudulent activity, which allows you to quickly respond to detected incidents and thereby minimize damage. Changes in the existing functions of the system and the addition of new capabilities ultimately significantly increase the efficiency of the solution as a whole.During testing, it was found that a new function of the system - determining the use of software for remote access when accessing a protected resource - works correctly and quite efficiently. We also found that the WEB ANTIFRAUD v2 system successfully detects such software even when changing standard network ports; this proves that the system does not scan them according to a fixed list, thereby preventing false alarms of antivirus protection and firewalls on the user's side.
Advantages:
- Determination of a wide range of fraudulent activities.
- Revealing the facts of using software for remote access without scanning the user's network ports.
- Tracking fraudulent activity on all pages and tabs in the user's personal account.
- Determination of interception of user information due to a phishing attack.
- Automatic processing of information in real time.
- The solution does not require access to the company's internal infrastructure and database.
- 24/7 and personalized product support.
Disadvantages:
- For the product to be fully functional, a backend API is required to integrate the solution with the client's site.
- There is no manual configuration of individual modules and system parameters.
The system developer can be contacted via the official website or via a twitter account (@AntiFraud2ru).

