Remember those epic heist movies? Where cool guys come up with a brilliant plan, change their appearance more often than models at shows, use incredible (unrealizable) psychological tricks and risk their skin in pursuit of profit. I think you remember. It's hard to imagine such robbers these days. Major economic crimes occur in the digital field. Today, the robber is not a psychological genius or a builder who knows where to start digging. Today, a robber is a hacker who knows all the subtleties of the banking sector.
Bank card history
Originally, in "prehistoric" times, there was nothing on the maps but an embossed number on the surface. The seller saved the number on a piece of paper. At the end of a business day or week, the data was sent to the acquiring bank, which sent a request to the issuing bank for debiting money from the cardholder. Then there were cards with a magnetic stripe that stored the necessary information: card number, expiration date, owner's name; service code (so that the ATM / terminal understands what functions the card has) and verification code (similar to what is written on the back of the card). Such cards had a significant drawback: the magnetic stripe is easy to copy using a reader/encoder. ATM skimming is a consequence of this vulnerability. Magnetic stripe cards were replaced in the 90s by smart cards (cards with chips) promoted by the EMV consortium (Europay, MasterCard, Visa). Smart card transactions provide three levels of protection: card authentication, payer verification, and transaction authorization. Finally, since the mid-2010s, contactless payments have become popular.
There are many different types of attacks that payment systems and banks have to deal with on a daily basis:

The image shows that there are not one, but two magnetic stripes of different densities (Track1 and Track2) on the map.
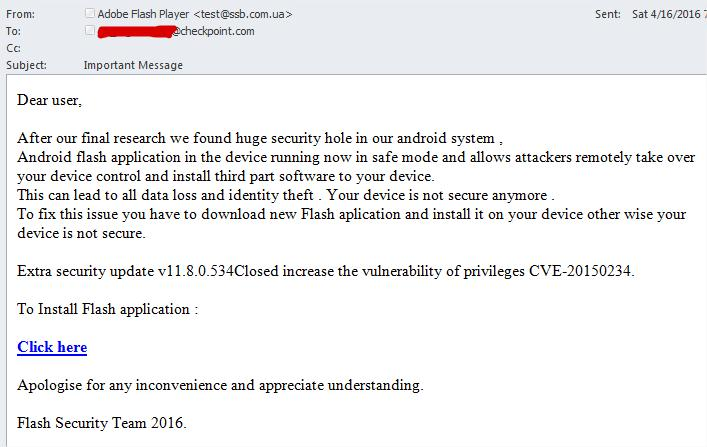
Example of a phishing email sent to one of the Check Point employees
An unsuspecting user downloaded a Trojan program disguised as Adobe Flash Player. During installation, the program requested administrator rights. When the user launched the banking application, the Trojan replaced the original window with a phishing window, where the necessary data was entered, which was then sent to the attackers ' server. With a username, password, and access to all SMS messages, including those with bank codes, fraudsters could successfully make bank transfers. The program was distributed via SMS distribution with a malicious link.
Example installing malware
As the authors of the study found out, remote access and management interfaces (such as SSH, Telnet, and file server access protocols), which are often accessible to any user, pose a great danger to banks. The study also showed that the weak link is also the bank's employees, as well as internal intruders. In some cases, the privileges of an employee who has access only to network sockets (security guards, cleaners) are sufficient for a successful attack. After gaining access to the internal network, attackers need to gain local administrator privileges on the employee's computer or servers. Attacks, according to analytics, rely mainly on a weak password policy (light passwords, standard accounts, bad group policy) and insufficient protection against password recovery from OS memory. Moving through the internal network using vulnerabilities and local software that does not cause suspicion, attackers can gain full control over the bank's infrastructure.
In general, an attack on the banking system can be described in the following steps::

Oh, what sins are not blamed on North Korea. Violation of citizens ' freedoms, totalitarianism, drug trafficking, aggressive foreign policy. But in terms of cyber attacks, North Korea has probably surpassed all other countries. State-sponsored hacker attacks bring huge amounts of money to the country.

The likely location of the hackers is the Ryuger Hotel in Pyongyang.
According to UN estimates, North Korea earned about $ 2 billion in total from hacking campaigns, and this is with $ 28 billion of GDP (for 2016)! 7% percent is not a bad thing. It's also not as bad as sponsoring a hacker program. According to unofficial data (and why would they be official in relation to the DPRK?) up to 20% of the annual military budget is spent on hacking programs. Periodically, North Korean schools conduct special tests of schoolchildren, according to the results of which high school students are sent to study computer science in depth. Here it is, the beginning of the formation of Kim Jong-un's cyber soldier. Often, the actions of hackers from the DPRK are associated with the hacker organization Lazarus. Some of the biggest attacks carried out by this group are the attack on Sony in 2014(presumably for the 2014 film "The Interview"), the attack on the Central Bank of Bangladesh in 2016 and the launch of the WannaCry ransomware virus in 2017(which affected more than 200,000 computers around the world). It is believed that Lazarus Group was established in 2007 under the control of the General Staff of the DPRK.

The FBI is looking for a Lazarus Group member. Maybe you've seen it somewhere?
There are some people who don't believe in gremlins.
But everyone gets hit on the head with a wrench that's not properly placed on the ladder."
OldGremlin is a Russian-speaking hacker group that announced itself in 2020. The first attack dates back to March-April 2020. In the wake of the coronavirus, OldGremlin, on behalf of the MiR Union of Microfinance Organizations, sent out security recommendations to financial organizations during the pandemic. In general, the tactics of this group can be described as opportunistic. During 2020, they sent out emails with a malicious link in connection with various public events: covid, political unrest in the CIS.
Timeline of Silence attacks in the 2018 report from Group-IB:
Mt. Gox.
Mt. Gox. — this is a bitcoin exchange. It was founded in 2010 in Tokyo. As of 2013, about 70% of all transactions involving the purchase and sale of bitcoin were made through it. In 2014, it declared bankruptcy due to theft.

Bitcoins from customer accounts began to leak since 2011: then the cryptocurrency was experiencing the first boom in its history, in June 2011, the price of it grew exponentially, which aroused the interest of hackers. Scammers created fake orders and withdrew several tens of thousands of bitcoins.
At some point, Mt. Gox began to experience problems, which led to an outflow of customers. But they began to discover that funds can be withdrawn from their accounts for several weeks, or even months. As a result, the exchange was closed, someone managed to withdraw, and someone did not have time, as they say "who managed, he ate". It is interesting that after some time, the exchange owner suddenly found 200 thousand bitcoins on one of the accounts. The theft case is still ongoing.

This was no ordinary glitch. This glitch was the culmination of the Lazarus hacker attack. Lazarus hacked a computer at the Central Bank and gained access to the bank's SWIFT account, which had huge capabilities. It also allowed you to make transactions. Here it is worth making a digression and saying that the Central Bank of Bangladesh keeps part of the money in the Federal Reserve Bank of New York. On February 4, the Central Bank of Bangladesh unwittingly initiated several dozen payments totaling $ 951 million. Thus, the hackers sent a request to New York, which no one in Bangladesh suspected. When the bank's employees found out about the severity of the situation, it was too late. The working day in New York has already ended, and all employees have left for the weekend.
Monday brought some news: both good and bad. The reason for the good news was the vigilance of colleagues from New York: transactions worth $ 870 million were canceled. Because of the English language. One of the transactions was sent to a strange recipient-Shalika Fandation in Sri Lanka. Apparently, hackers from Lazarus wanted to send money to the account of the non-existent organization Shalika Foundation, but their literacy failed them. The bad news was that $ 81 million worth of transactions were approved and the money went to fake accounts in the Philippines and Sri Lanka. Out of a possible 951 million, hackers received only 81 million-8.5 percent.
On April 12, 2021, the Central Bank of Russia reported an increase in Russian losses from cyber fraud by 52% in 2020, to 9.77 billion rubles. Responsibility for crimes in the field of computer information is described in Chapter 28 of the Criminal Code of the Russian Federation. Currently, there is no single approach to understanding cybercrime and the information space, which in turn leads to different understanding of homogeneous crimes in the legislation of different countries. If we talk about Russia, then its legislation in terms of cybercrime does not stand out in any special way.
Carding 2024
One of the most common types of "technological" fraud is fraud with bank cards. It is not surprising, because today almost everyone everywhere pays with cards. But are such payments safe?Bank card history
Originally, in "prehistoric" times, there was nothing on the maps but an embossed number on the surface. The seller saved the number on a piece of paper. At the end of a business day or week, the data was sent to the acquiring bank, which sent a request to the issuing bank for debiting money from the cardholder. Then there were cards with a magnetic stripe that stored the necessary information: card number, expiration date, owner's name; service code (so that the ATM / terminal understands what functions the card has) and verification code (similar to what is written on the back of the card). Such cards had a significant drawback: the magnetic stripe is easy to copy using a reader/encoder. ATM skimming is a consequence of this vulnerability. Magnetic stripe cards were replaced in the 90s by smart cards (cards with chips) promoted by the EMV consortium (Europay, MasterCard, Visa). Smart card transactions provide three levels of protection: card authentication, payer verification, and transaction authorization. Finally, since the mid-2010s, contactless payments have become popular.
There are many different types of attacks that payment systems and banks have to deal with on a daily basis:
Payments without 3-D Secure
Most cases of fraud occur in online payments that follow the card-not-present scheme (transactions only require data written on the card and easily extracted from shadow markets). To combat such schemes, they invented 3-D Secure, an additional authorization scheme that uses three domain entities: the domain of the online store, the domain of the payment system, and the domain of the acquiring bank. However, some large stores, such as Amazon, are not ready to work with 3-D Secure, which is good news for scammers.Cloning a magnetic stripe
Despite the fact that modern cards are equipped with a chip, magnetic stripe cloning is the second most popular type of fraud. The fact is that in many US stores, when paying with a smart card, you can make a transaction using a magnetic stripe. And if the terminal refuses to accept the magnetic stripe, there is a technical fallback scheme that works in America (both North and South) and Europe. Just insert a card with a non-existent chip into the terminal / ATM, and after three unsuccessful attempts, the terminal will offer to perform a transaction using a magnetic stripe. In Russia, payment terminals should not accept a magnetic stripe if the card is equipped with a chip. However, in some stores you can find terminals that accept technical fallback operations. And besides, no one forbids attackers to transfer data to Europe/America for further monetization.
The image shows that there are not one, but two magnetic stripes of different densities (Track1 and Track2) on the map.
Offline authentication
According to the current rules of payment systems, 99.9% of transactions must be made online (the cryptogram is confirmed on the issuing bank's side), with the exception of payments in the subway, on planes and cruise liners. In such places, the Internet does not always work stably. In addition, many payment systems used to work under Floor limit — transactions above a certain limit were confirmed online, and below-by the terminal itself. A few years ago, the number of such terminals (especially in America and Europe) was large enough to attack the shortcomings of offline card authentication.The human factor
A person is the weakest link in any system, no matter how reliable it is. Attackers easily bypass network perimeter protection by using banal phishing, which delivers malware to the corporate network. A bank employee can easily click on a suspicious link in an email or download an unidentified file. What can we say about ordinary users? The situation is aggravated by the fact that almost everyone has a remote banking service on their smartphone (for example, mobile banking). Consider a typical scheme using the example of the "5th Reich" virus from Chelyabinsk "cyber-fascists" (the control system had Nazi symbols).
Example of a phishing email sent to one of the Check Point employees
An unsuspecting user downloaded a Trojan program disguised as Adobe Flash Player. During installation, the program requested administrator rights. When the user launched the banking application, the Trojan replaced the original window with a phishing window, where the necessary data was entered, which was then sent to the attackers ' server. With a username, password, and access to all SMS messages, including those with bank codes, fraudsters could successfully make bank transfers. The program was distributed via SMS distribution with a malicious link.

Example installing malware
Corporate network penetration
According to a study by Positive Technologies, the company's specialists managed to gain access to financial applications in 58% of cases. In 25% of banks, the nodes used to manage ATMs were compromised. In 17% of banks, card processing systems are insufficiently protected, which allows manipulating the balance on card accounts, the report says. The level of protection of the network perimeter of banks is usually higher than that of other companies, but it is still far from ideal.As the authors of the study found out, remote access and management interfaces (such as SSH, Telnet, and file server access protocols), which are often accessible to any user, pose a great danger to banks. The study also showed that the weak link is also the bank's employees, as well as internal intruders. In some cases, the privileges of an employee who has access only to network sockets (security guards, cleaners) are sufficient for a successful attack. After gaining access to the internal network, attackers need to gain local administrator privileges on the employee's computer or servers. Attacks, according to analytics, rely mainly on a weak password policy (light passwords, standard accounts, bad group policy) and insufficient protection against password recovery from OS memory. Moving through the internal network using vulnerabilities and local software that does not cause suspicion, attackers can gain full control over the bank's infrastructure.
In general, an attack on the banking system can be described in the following steps::
- Penetration
- Remote access
- Getting privileges
- Finding goals
- Working with target systems
- Cashing out
Hacker organizations
NORTH Korea

Oh, what sins are not blamed on North Korea. Violation of citizens ' freedoms, totalitarianism, drug trafficking, aggressive foreign policy. But in terms of cyber attacks, North Korea has probably surpassed all other countries. State-sponsored hacker attacks bring huge amounts of money to the country.

The likely location of the hackers is the Ryuger Hotel in Pyongyang.
According to UN estimates, North Korea earned about $ 2 billion in total from hacking campaigns, and this is with $ 28 billion of GDP (for 2016)! 7% percent is not a bad thing. It's also not as bad as sponsoring a hacker program. According to unofficial data (and why would they be official in relation to the DPRK?) up to 20% of the annual military budget is spent on hacking programs. Periodically, North Korean schools conduct special tests of schoolchildren, according to the results of which high school students are sent to study computer science in depth. Here it is, the beginning of the formation of Kim Jong-un's cyber soldier. Often, the actions of hackers from the DPRK are associated with the hacker organization Lazarus. Some of the biggest attacks carried out by this group are the attack on Sony in 2014(presumably for the 2014 film "The Interview"), the attack on the Central Bank of Bangladesh in 2016 and the launch of the WannaCry ransomware virus in 2017(which affected more than 200,000 computers around the world). It is believed that Lazarus Group was established in 2007 under the control of the General Staff of the DPRK.

The FBI is looking for a Lazarus Group member. Maybe you've seen it somewhere?
OldGremlin
"There are people who believe in gremlins.There are some people who don't believe in gremlins.
But everyone gets hit on the head with a wrench that's not properly placed on the ladder."
OldGremlin is a Russian-speaking hacker group that announced itself in 2020. The first attack dates back to March-April 2020. In the wake of the coronavirus, OldGremlin, on behalf of the MiR Union of Microfinance Organizations, sent out security recommendations to financial organizations during the pandemic. In general, the tactics of this group can be described as opportunistic. During 2020, they sent out emails with a malicious link in connection with various public events: covid, political unrest in the CIS.
Silence
This grouping differs in that there are 2 main roles: operator and developer. Perhaps it only includes two people! Of course, this doesn't lessen the damage it does. The confirmed damage from this organization is estimated at 52 million rubles (according to other information, 272 million). The description of Silence roles from Group-IB can be found below:Timeline of Silence attacks in the 2018 report from Group-IB:
| Date | Attack characteristics |
| 2016, July | Failed attempt to withdraw funds via the Russian interbank transfer system. |
| 2016, August | Attempted hacking of the same bank. The attack was prevented. |
| 2017, October | Attack on the ATM network. In one night Silence stole about 7 million rubles. |
| 2018 year february | Attack via card processing. Through ATMs, the attackers withdrew about 35 million rubles. |
| 2018, April | Previous diagram. During the night Silence stole 10 million rubles. |
Major attacks
Billion. And this is not a Russian movie
You walk down the street and see that the ATM starts issuing money. Just like that. What's going on here anyway? Probably, this question arose among people in December 2013, when they saw a similar picture. The damage caused by an international group of hackers from Russia, China and Europe is estimated at approximately one billion dollars. The Carbanak virus was spread by hackers using email distribution, affecting about 100 financial organizations around the world. From the moment of infection to theft, it took about 2-4 months. ATMs were one of the ways to steal money. At some point, hackers gave a command to the ATM to issue cash. The kidnappers just had to come and collect the money.Mt. Gox.
Oh, it was necessary to buy bitcoin in 2010 and live happily ever after. I wonder what hackers did with the stolen 850 thousand bitcoins in 2013? Well, we'll never know. At the time of the theft, this amount of bitcoins was approximately $ 480 million. At the time of writing, so many bitcoins are already worth 51 billion. Almost like Mark Zuckerberg's floor!Mt. Gox.
Mt. Gox. — this is a bitcoin exchange. It was founded in 2010 in Tokyo. As of 2013, about 70% of all transactions involving the purchase and sale of bitcoin were made through it. In 2014, it declared bankruptcy due to theft.

Bitcoins from customer accounts began to leak since 2011: then the cryptocurrency was experiencing the first boom in its history, in June 2011, the price of it grew exponentially, which aroused the interest of hackers. Scammers created fake orders and withdrew several tens of thousands of bitcoins.
At some point, Mt. Gox began to experience problems, which led to an outflow of customers. But they began to discover that funds can be withdrawn from their accounts for several weeks, or even months. As a result, the exchange was closed, someone managed to withdraw, and someone did not have time, as they say "who managed, he ate". It is interesting that after some time, the exchange owner suddenly found 200 thousand bitcoins on one of the accounts. The theft case is still ongoing.
8,5%
HP LaserJet 400 is a laser printer. It costs about 20 thousand rubles. In one beautiful way (as it turns out later-no) in the morning at the Central Bank of Bangladesh, such a printer in a small room without windows stopped working. But this printer was not simple. He had a very important task — he had to automatically print out the physical records of the bank's SWIFT transactions. But on February 5, 2016, the print tray was empty. Bank employees tried to revive him, but to no avail.
This was no ordinary glitch. This glitch was the culmination of the Lazarus hacker attack. Lazarus hacked a computer at the Central Bank and gained access to the bank's SWIFT account, which had huge capabilities. It also allowed you to make transactions. Here it is worth making a digression and saying that the Central Bank of Bangladesh keeps part of the money in the Federal Reserve Bank of New York. On February 4, the Central Bank of Bangladesh unwittingly initiated several dozen payments totaling $ 951 million. Thus, the hackers sent a request to New York, which no one in Bangladesh suspected. When the bank's employees found out about the severity of the situation, it was too late. The working day in New York has already ended, and all employees have left for the weekend.
Monday brought some news: both good and bad. The reason for the good news was the vigilance of colleagues from New York: transactions worth $ 870 million were canceled. Because of the English language. One of the transactions was sent to a strange recipient-Shalika Fandation in Sri Lanka. Apparently, hackers from Lazarus wanted to send money to the account of the non-existent organization Shalika Foundation, but their literacy failed them. The bad news was that $ 81 million worth of transactions were approved and the money went to fake accounts in the Philippines and Sri Lanka. Out of a possible 951 million, hackers received only 81 million-8.5 percent.
What about in Russia?
They say that Russian hackers have their own unspoken "code of honor". Many people tend to romanticize the image of cybercriminals, making them digital Robin Hoods. One of the rules of Russian-speaking attackers is "do not work on RU". However, it is not clear what is more here, patriotism or fear of the FSB. Many hacker groups "score" on this rule, operating exclusively in the CIS. Just recall the famous OldGremlin, which attacks exclusively Russian companies — banks, industrial enterprises, medical organizations, and software developers.On April 12, 2021, the Central Bank of Russia reported an increase in Russian losses from cyber fraud by 52% in 2020, to 9.77 billion rubles. Responsibility for crimes in the field of computer information is described in Chapter 28 of the Criminal Code of the Russian Federation. Currently, there is no single approach to understanding cybercrime and the information space, which in turn leads to different understanding of homogeneous crimes in the legislation of different countries. If we talk about Russia, then its legislation in terms of cybercrime does not stand out in any special way.
