Carding
Professional
- Messages
- 2,871
- Reaction score
- 2,466
- Points
- 113
Infection of POS terminals (Point Of Sale), software and hardware systems for trading or automated workstations of a cashier is a cybercriminal activity aimed at stealing bank card data and further withdrawing funds.
Classification of methods of infecting POS terminals:
Malicious programs for POS terminals can be distinguished by the volume of tasks being solved and the nature of the information stolen.
RAM scrapers
Writing the contents of RAM is a mandatory part of almost all programs for infecting POS terminals, since during a transaction all data from a bank card is processed in RAM. Basic RAM scrapers record information from memory and send it to the attacker's server for further offline analysis, while more advanced versions are able to independently extract data from the magnetic stripes of bank cards from the general stream.
RAM scraper and keylogger
Such programs, in addition to analyzing RAM, also record all keystrokes, fixing PIN codes and other entered information.
Since all transactions are carried out via a computer or mobile device, the development of malicious code often does not take place from scratch: cybercriminals modify already created Trojans and viruses, adding RAM scrapers to them to steal data from bank cards.
Accordingly, such instances can contain rootkits to hide traces of activity or backdoors for remote access, steal other information. In particular, the well-known malicious agent vSkimmer collects information about the operating system used, users, and GUID. Target of Impact When it comes to infecting POS terminals, malware does not infiltrate the card reader, but the computer or mobile device that controls it. Although all transmitted transaction data is encrypted, the information from the magnetic stripe of the card arrives unencrypted and is encrypted on the computer.
Figure 1. Evolution of POS malware:
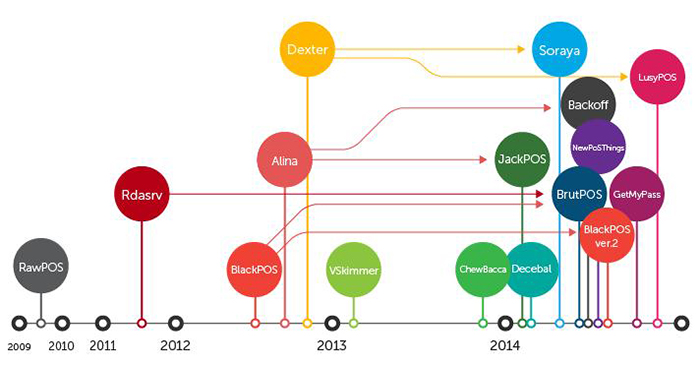
This vulnerability is used by carders. The programs for scanning the RAM that are embedded in the system constantly analyze the contents of the latter and read the card data. The number, expiration date, owner's name, PIN, CVV and CVC recorded on the magnetic stripe are sufficient to make a clone with which you can withdraw money and pay for purchases. In addition, this data allows you to pay for online orders, where the presentation of physical cards is not required.
Chipped cards are better protected: they encrypt payment information with a chip before being sent to the POS terminal, and interception is useless. However, the magnetic stripe is also there, and its data can still be copied. In this case, the criminal will not be able to withdraw money from the ATM (there is no chip), but he will be able to use the clone as a means of payment if the reader in the store only works with the strip. However, in this case, traces remain for law enforcement agencies, and therefore carders prefer to copy cards without chips.
Sources of threat
Infection of a POS terminal with malicious programs can occur in several ways: via the Internet using exploits, via a USB interface to which an infected medium is connected, by replacing a safe POS terminal with an infected one, via spam with a Trojan downloader.
A program that steals passwords can be entered into the system on purpose. Bank data is of great value, and a dishonest or offended employee, having agreed with a cybercriminal, will easily introduce a malicious agent into the system.
The third major source of threat is companies that install and remotely maintain POS terminals. In theory, in such firms, the security system should be organized at the highest level, but in practice this is not always true. There are known cases when, having cracked the password of the remote administrator of POS terminals, attackers at once got access to the banking data of millions of users.
Threat analysis
For a simple bank card holder, the main danger of POS-terminals becoming infected is that he is unable to prevent it. A person uses the card, assuming normal operation of the system, but if it makes unauthorized operations, then the user will not be able to find out about it.
To reduce the risk, you can abandon the card, which contains only a magnetic stripe, in favor of a more secure chip one and regularly monitor the status of your accounts, track all transactions in order to immediately take action if you suspect.
If we talk about the owners of POS terminals, then from their point of view there are no direct losses: after all, the data is stolen not from the company, but from the cardholders. However, reputational losses and customer churn can result in millions of damage, and therefore any company must take the necessary measures to protect the banking data of its customers.
All POS computers must be equipped with effective antivirus software and system software must be up to date. The list of installed programs itself should be limited, and the computer should not be used for other tasks not related to transactions. The same applies to owners of mobile POS terminals. For such purposes, it is better to buy a second smartphone, using it only to transfer money, and communicate, take selfies and other photos, launch media files on another device.
Access to POS terminals, authorization on them should be allowed only to those employees who directly work with them. Within the system, a clear delineation of rights is required with the prohibition to install or modify computer software for unprivileged accounts. Each user must have their own complex password.
Finally, in addition to working with the terminal, cashiers and other tellers should be trained in information security rules. As already mentioned, the methods of distributing malware for trading devices do not differ from the methods of infecting other computers, and in many cases the penetration of Trojan horses and viruses is due to the carelessness and frivolity of users; compliance with cyber hygiene greatly complicates the activities of intruders.
Classification of methods of infecting POS terminals:
Malicious programs for POS terminals can be distinguished by the volume of tasks being solved and the nature of the information stolen.
RAM scrapers
Writing the contents of RAM is a mandatory part of almost all programs for infecting POS terminals, since during a transaction all data from a bank card is processed in RAM. Basic RAM scrapers record information from memory and send it to the attacker's server for further offline analysis, while more advanced versions are able to independently extract data from the magnetic stripes of bank cards from the general stream.
RAM scraper and keylogger
Such programs, in addition to analyzing RAM, also record all keystrokes, fixing PIN codes and other entered information.
Since all transactions are carried out via a computer or mobile device, the development of malicious code often does not take place from scratch: cybercriminals modify already created Trojans and viruses, adding RAM scrapers to them to steal data from bank cards.
Accordingly, such instances can contain rootkits to hide traces of activity or backdoors for remote access, steal other information. In particular, the well-known malicious agent vSkimmer collects information about the operating system used, users, and GUID. Target of Impact When it comes to infecting POS terminals, malware does not infiltrate the card reader, but the computer or mobile device that controls it. Although all transmitted transaction data is encrypted, the information from the magnetic stripe of the card arrives unencrypted and is encrypted on the computer.
Figure 1. Evolution of POS malware:

This vulnerability is used by carders. The programs for scanning the RAM that are embedded in the system constantly analyze the contents of the latter and read the card data. The number, expiration date, owner's name, PIN, CVV and CVC recorded on the magnetic stripe are sufficient to make a clone with which you can withdraw money and pay for purchases. In addition, this data allows you to pay for online orders, where the presentation of physical cards is not required.
Chipped cards are better protected: they encrypt payment information with a chip before being sent to the POS terminal, and interception is useless. However, the magnetic stripe is also there, and its data can still be copied. In this case, the criminal will not be able to withdraw money from the ATM (there is no chip), but he will be able to use the clone as a means of payment if the reader in the store only works with the strip. However, in this case, traces remain for law enforcement agencies, and therefore carders prefer to copy cards without chips.
Sources of threat
Infection of a POS terminal with malicious programs can occur in several ways: via the Internet using exploits, via a USB interface to which an infected medium is connected, by replacing a safe POS terminal with an infected one, via spam with a Trojan downloader.
A program that steals passwords can be entered into the system on purpose. Bank data is of great value, and a dishonest or offended employee, having agreed with a cybercriminal, will easily introduce a malicious agent into the system.
The third major source of threat is companies that install and remotely maintain POS terminals. In theory, in such firms, the security system should be organized at the highest level, but in practice this is not always true. There are known cases when, having cracked the password of the remote administrator of POS terminals, attackers at once got access to the banking data of millions of users.
Threat analysis
For a simple bank card holder, the main danger of POS-terminals becoming infected is that he is unable to prevent it. A person uses the card, assuming normal operation of the system, but if it makes unauthorized operations, then the user will not be able to find out about it.
To reduce the risk, you can abandon the card, which contains only a magnetic stripe, in favor of a more secure chip one and regularly monitor the status of your accounts, track all transactions in order to immediately take action if you suspect.
If we talk about the owners of POS terminals, then from their point of view there are no direct losses: after all, the data is stolen not from the company, but from the cardholders. However, reputational losses and customer churn can result in millions of damage, and therefore any company must take the necessary measures to protect the banking data of its customers.
All POS computers must be equipped with effective antivirus software and system software must be up to date. The list of installed programs itself should be limited, and the computer should not be used for other tasks not related to transactions. The same applies to owners of mobile POS terminals. For such purposes, it is better to buy a second smartphone, using it only to transfer money, and communicate, take selfies and other photos, launch media files on another device.
Access to POS terminals, authorization on them should be allowed only to those employees who directly work with them. Within the system, a clear delineation of rights is required with the prohibition to install or modify computer software for unprivileged accounts. Each user must have their own complex password.
Finally, in addition to working with the terminal, cashiers and other tellers should be trained in information security rules. As already mentioned, the methods of distributing malware for trading devices do not differ from the methods of infecting other computers, and in many cases the penetration of Trojan horses and viruses is due to the carelessness and frivolity of users; compliance with cyber hygiene greatly complicates the activities of intruders.
