In this brief review, we will present the operating systems that you all probably know, and we will not waste time on their detailed analysis.
But let's look at them from a different angle. A more critical one.
Tails OS

Tails (The Amnesic Incognito Live System), Tails - or simply "Tails". A Linux distribution aimed at privacy and anonymity. It is a LIVE distribution (Works from a flash drive, leaves no traces on your PC). It is based, like many distributions, on the very stable Debian (we'll get back to it later). You, dear subscribers, are probably familiar with it.
For those who are not familiar with the course, This OS wraps all your traffic in the Tor network, which ensures security when carrying out activities on the network. It comes with pre-installed software that often makes life easier (Cryptocurrency wallet client, password Manager, communication clients, tor browser, and much more). I will not now list all the features and advantages of this OS as well as others in this list. This has already been done 1000 and 1 times. Let's talk about the pitfalls. Alas, many guys are convinced that Tails is the perfect pill in which you can do dirty things and uncle policeman will never get you.
The case of a friend with a nickname "Brian Keel" Hernandez he says that not everything is so carefree. This scoundrel was engaged in blackmail and extortion from young women and children. Intimidated by rape, terrorism, and just being a great person. He did his own interesting business on Facebook, but this character did not forget about ensuring his own safety. To do this, he used Tails.. I worked in LIVE mode, I didn't clog my PC with unnecessary evidence from an external media, I generally lived my life and was a good guy (I parry the obvious question in Advance - there is a Facebook mirror in the Tor network). In General, the obvious happened, Hernandez's lifestyle attracted the attention of the competent authorities who took up the hero of the story. Hernandez did not take into account that the "security guards" of Facebook paid a round sum to a third-party contractor for developing a zero-day exploit in Tails, which moment led to the de-anonymization of the villain and a life sentence in a us Federal prison.

Hernandez - "victim" of tails ' imperfection
And now, the main thing. What's wrong with Tails?
1) Facebook, of course, did not notify Tails about the vulnerability found. No one really knows how many times this or other exploit created for certain tasks was used, and whether this exploit(s) was transferred to other departments. Using Tails or any other Linux distributions is not a panacea. For Linux, there are also exploits and various malware (although many times less than for Windows, for example).)
2) Tails, in the "naked" form will not suit you if the work is related to resources that quote only a white IP. Only the lazy person in the clearnet doesn't swear at Tor right now, an exception if there is a mirror in Tor, of course. You will have to perform additional manipulations (after connecting to a VPN or VPS/RDP, and so on, which may be difficult for novice users). In addition, on
3) This is a LIVE system, you can of course install Tails in Virtualbox or another virtualization environment, but then the very ideological concept of this operating system is violated. The LIVE system will not be an ideal option for many in terms of comfort. Even if you need to create permanent storage. Tails in General, according to my personal experience and the experience of many people with whom I had to communicate, is not much intended for some kind of permanent/long-term work. Keep in mind that your external carrier may pupate at the most inopportune moment. Therefore, always, whether it's Tails or not, MAKE backups of DATA so that you don't have to slap yourself in the face and sprinkle ashes on your head for a bitcoin wallet that was only on a flash drive that suddenly fell into disrepair.
4) Permanent volume if you created it-visible to everyone who has access to the USB drive + access to permanent storage from other operating systems may compromise security
Conclusion:
It is quite suitable as a forced "Hiking" option, for safe surfing. If we are talking about implementing the proper level of security - Tails is only for safe surfing.
Whonix

The next solution that we will consider is Whonix. The OS is slightly less recognizable than Tails, but most of you are familiar with it. In fact, these are 2 virtual machines - the first virtual machine is a Tor gateway, and the second is a working environment (there are other implementation options-Whonix for Qubes OS and even physical isolation when the role of 2 virtual machines is replaced by 2 separate PCs) the Tor gateway torifies all traffic, and the working environment takes traffic only through the tor gateway and nothing else. In addition to traffic torification, security is ensured by isolation - even if the VM is compromised, the malware will remain in it. (none)
What can be the pitfalls?
1) the Degree of your security depends directly on which main (host) OS is running on your hardware. Linux, Xen (Qubes) , or BSD are the only effective options for the host operating system to work with Whonix. In the future, you will learn why you should avoid proprietary operating systems (with closed source code) - such as Windows (if we are talking about security). If your main OS is Windows , then there is little help for you. You can't make candy out of mud. We'll tell you why later
2) Also, the degree of your security depends to some extent on which virtualization platform is used to work with Whonix. The General principle here is to avoid proprietary SOFTWARE. It is clear that an inexperienced user will be more intuitive than Virtualbox, but later, as you get used to it, it is better to switch to more secure and free options (KVM/Qemu or ideally Qubes)
Conclusion:
Whonix in its naked form is far from perfect. But if you take a number of additional measures and "bring it to mind" - this is an effective working option.
Qubes OS

Just like Whonix-Qubes OS provides security by isolating the Xen hypervisor. Based on Fedora, it is easy to install (with a certain skill and ease of use). The isolation method is based on a limited interaction between software and hardware. In fact, cubes are the management center for virtual machines. A separate virtual machine is created for each process, which makes this OS the best solution available today. Especially in tandem with Whonix.
But not everything is so simple.
1) Since Qubes OS is a virtual machine management center, you will need a powerful PC. Although you can run Qubes OS on less powerful hardware, this is not recommended. But this is not all, Qubes is very whimsical to hardware, which is the biggest drawback of this OS. There is an official list of supported hardware.
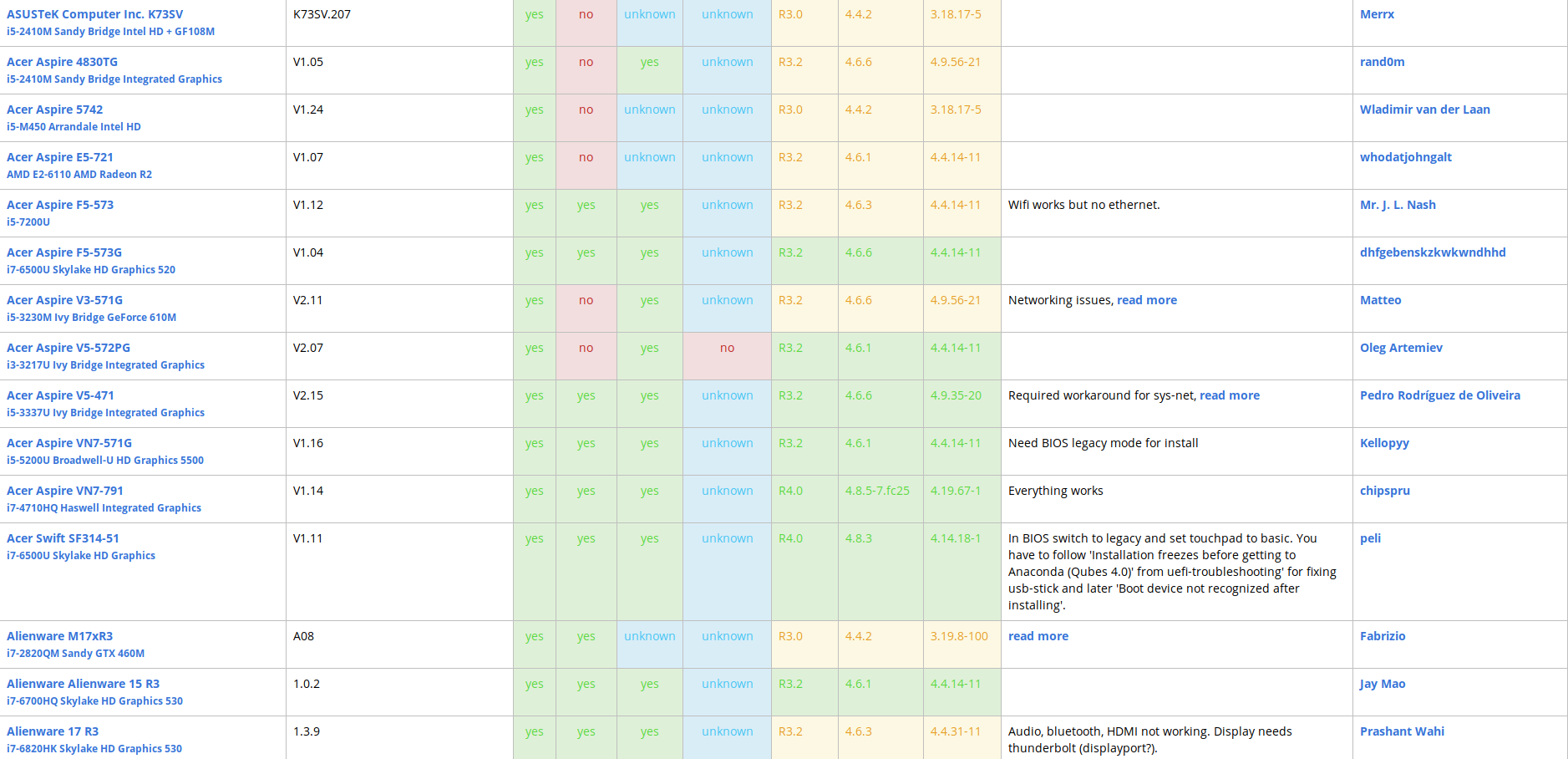
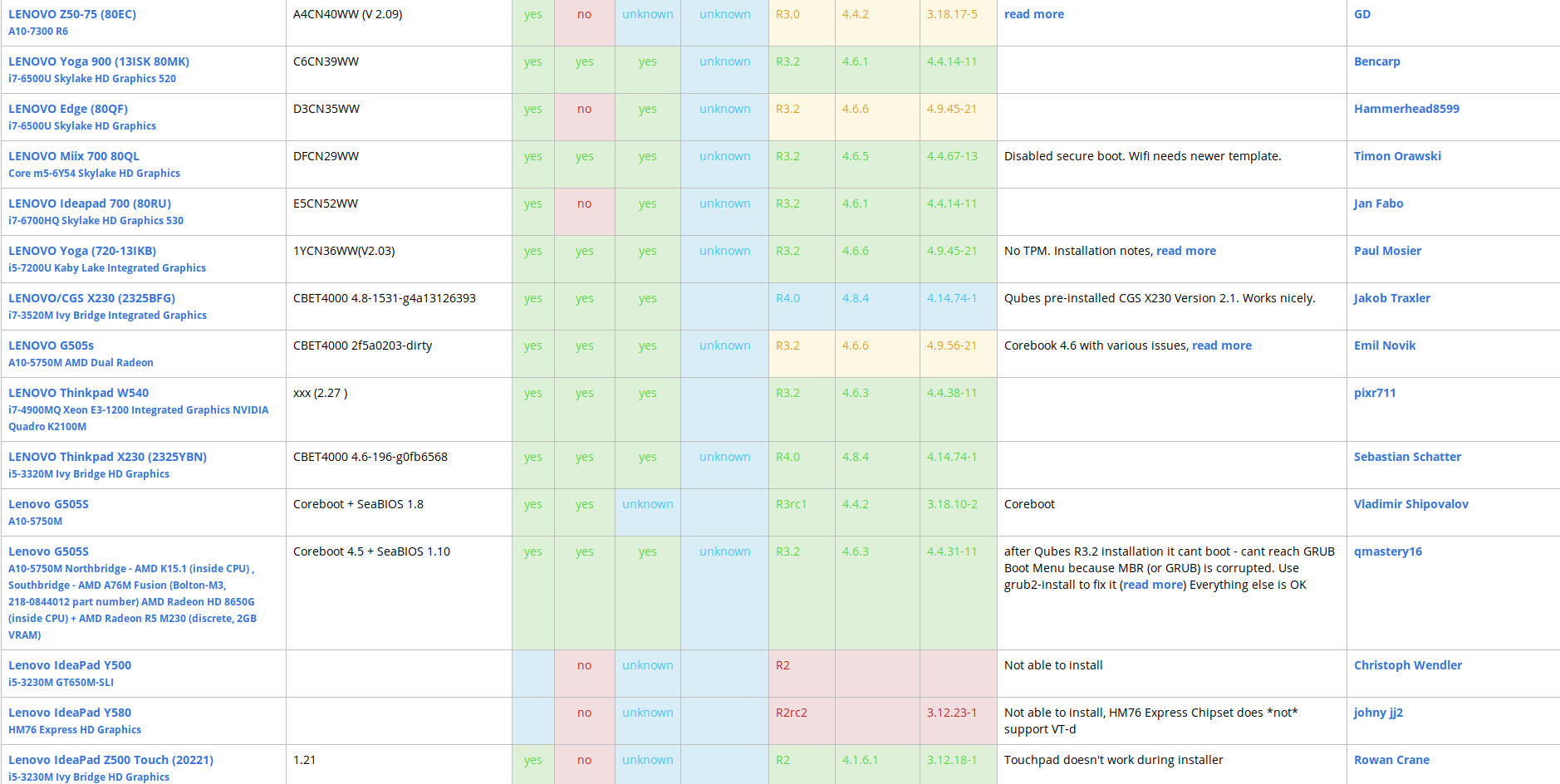
As you can see, a very limited number of models interact well with this OS and ensure that all its features are fully operational. It is possible to purchase hardware that, according to the manufacturer, is fully compatible with Qubes OS and comes with this pre-installed OS. For example, the Purism line.
2) the process of interacting with the OS (for example, installing applications) in Qubes is slightly different from other Linux distributions. Due to the fact that the community here is not as extensive as for example Ubuntu/Debian, novice users may have difficulties.
Conclusion:
If your PC fully supports Qubes OS, then this is undoubtedly the best possible option today. In tandem with Whonix and subject to the implementation of a number of security measures and fine-tuning the distribution for yourself and your goals.
But let's look at them from a different angle. A more critical one.
Tails OS

Tails (The Amnesic Incognito Live System), Tails - or simply "Tails". A Linux distribution aimed at privacy and anonymity. It is a LIVE distribution (Works from a flash drive, leaves no traces on your PC). It is based, like many distributions, on the very stable Debian (we'll get back to it later). You, dear subscribers, are probably familiar with it.
For those who are not familiar with the course, This OS wraps all your traffic in the Tor network, which ensures security when carrying out activities on the network. It comes with pre-installed software that often makes life easier (Cryptocurrency wallet client, password Manager, communication clients, tor browser, and much more). I will not now list all the features and advantages of this OS as well as others in this list. This has already been done 1000 and 1 times. Let's talk about the pitfalls. Alas, many guys are convinced that Tails is the perfect pill in which you can do dirty things and uncle policeman will never get you.
The case of a friend with a nickname "Brian Keel" Hernandez he says that not everything is so carefree. This scoundrel was engaged in blackmail and extortion from young women and children. Intimidated by rape, terrorism, and just being a great person. He did his own interesting business on Facebook, but this character did not forget about ensuring his own safety. To do this, he used Tails.. I worked in LIVE mode, I didn't clog my PC with unnecessary evidence from an external media, I generally lived my life and was a good guy (I parry the obvious question in Advance - there is a Facebook mirror in the Tor network). In General, the obvious happened, Hernandez's lifestyle attracted the attention of the competent authorities who took up the hero of the story. Hernandez did not take into account that the "security guards" of Facebook paid a round sum to a third-party contractor for developing a zero-day exploit in Tails, which moment led to the de-anonymization of the villain and a life sentence in a us Federal prison.

Hernandez - "victim" of tails ' imperfection
And now, the main thing. What's wrong with Tails?
1) Facebook, of course, did not notify Tails about the vulnerability found. No one really knows how many times this or other exploit created for certain tasks was used, and whether this exploit(s) was transferred to other departments. Using Tails or any other Linux distributions is not a panacea. For Linux, there are also exploits and various malware (although many times less than for Windows, for example).)
2) Tails, in the "naked" form will not suit you if the work is related to resources that quote only a white IP. Only the lazy person in the clearnet doesn't swear at Tor right now, an exception if there is a mirror in Tor, of course. You will have to perform additional manipulations (after connecting to a VPN or VPS/RDP, and so on, which may be difficult for novice users). In addition, on
3) This is a LIVE system, you can of course install Tails in Virtualbox or another virtualization environment, but then the very ideological concept of this operating system is violated. The LIVE system will not be an ideal option for many in terms of comfort. Even if you need to create permanent storage. Tails in General, according to my personal experience and the experience of many people with whom I had to communicate, is not much intended for some kind of permanent/long-term work. Keep in mind that your external carrier may pupate at the most inopportune moment. Therefore, always, whether it's Tails or not, MAKE backups of DATA so that you don't have to slap yourself in the face and sprinkle ashes on your head for a bitcoin wallet that was only on a flash drive that suddenly fell into disrepair.
4) Permanent volume if you created it-visible to everyone who has access to the USB drive + access to permanent storage from other operating systems may compromise security
Conclusion:
It is quite suitable as a forced "Hiking" option, for safe surfing. If we are talking about implementing the proper level of security - Tails is only for safe surfing.
Whonix

The next solution that we will consider is Whonix. The OS is slightly less recognizable than Tails, but most of you are familiar with it. In fact, these are 2 virtual machines - the first virtual machine is a Tor gateway, and the second is a working environment (there are other implementation options-Whonix for Qubes OS and even physical isolation when the role of 2 virtual machines is replaced by 2 separate PCs) the Tor gateway torifies all traffic, and the working environment takes traffic only through the tor gateway and nothing else. In addition to traffic torification, security is ensured by isolation - even if the VM is compromised, the malware will remain in it. (none)
What can be the pitfalls?
1) the Degree of your security depends directly on which main (host) OS is running on your hardware. Linux, Xen (Qubes) , or BSD are the only effective options for the host operating system to work with Whonix. In the future, you will learn why you should avoid proprietary operating systems (with closed source code) - such as Windows (if we are talking about security). If your main OS is Windows , then there is little help for you. You can't make candy out of mud. We'll tell you why later
2) Also, the degree of your security depends to some extent on which virtualization platform is used to work with Whonix. The General principle here is to avoid proprietary SOFTWARE. It is clear that an inexperienced user will be more intuitive than Virtualbox, but later, as you get used to it, it is better to switch to more secure and free options (KVM/Qemu or ideally Qubes)
Conclusion:
Whonix in its naked form is far from perfect. But if you take a number of additional measures and "bring it to mind" - this is an effective working option.
Qubes OS

Just like Whonix-Qubes OS provides security by isolating the Xen hypervisor. Based on Fedora, it is easy to install (with a certain skill and ease of use). The isolation method is based on a limited interaction between software and hardware. In fact, cubes are the management center for virtual machines. A separate virtual machine is created for each process, which makes this OS the best solution available today. Especially in tandem with Whonix.
But not everything is so simple.
1) Since Qubes OS is a virtual machine management center, you will need a powerful PC. Although you can run Qubes OS on less powerful hardware, this is not recommended. But this is not all, Qubes is very whimsical to hardware, which is the biggest drawback of this OS. There is an official list of supported hardware.


As you can see, a very limited number of models interact well with this OS and ensure that all its features are fully operational. It is possible to purchase hardware that, according to the manufacturer, is fully compatible with Qubes OS and comes with this pre-installed OS. For example, the Purism line.
2) the process of interacting with the OS (for example, installing applications) in Qubes is slightly different from other Linux distributions. Due to the fact that the community here is not as extensive as for example Ubuntu/Debian, novice users may have difficulties.
Conclusion:
If your PC fully supports Qubes OS, then this is undoubtedly the best possible option today. In tandem with Whonix and subject to the implementation of a number of security measures and fine-tuning the distribution for yourself and your goals.
