The Windows search engine has become an entry point for malicious code injection.
Trustwave researchers have discovered a new phishing campaign in which attackers use HTML attachments to abuse the Windows Search protocol (search-ms URI) and distribute malware.
The Windows Search protocol allows applications to open File Explorer to perform searches using specific parameters. Typically the search is performed on the local device, but it is possible to force the search of files on remote servers and use a custom search box name.
Hackers can use this ability to distribute malicious files from remote servers, as Professor Martin Jones first noted in his 2020 research paper .
In June 2022, security researchers developed a powerful attack chain that also exploited a vulnerability in Microsoft Office to launch searches directly from Word documents.
According to Trustwave SpiderLabs, attackers are now actively using this technique, using HTML attachments to launch Windows searches on the attackers' servers.
Recent attacks begin by sending a malicious email with an HTML attachment disguised as an invoice document, packaged in a small ZIP archive. ZIP files help bypass security scanners, which may not analyze archives for malicious content.
The HTML file uses the <meta http-equiv="refresh"> tag to automatically navigate to the malicious URL when the document is opened in the browser. If the meta update fails due to browser settings blocking redirects, the anchor tag provides a clickable link to the malicious URL, which requires action from the user.
The URL is used to perform a search on the remote host using the following parameters:
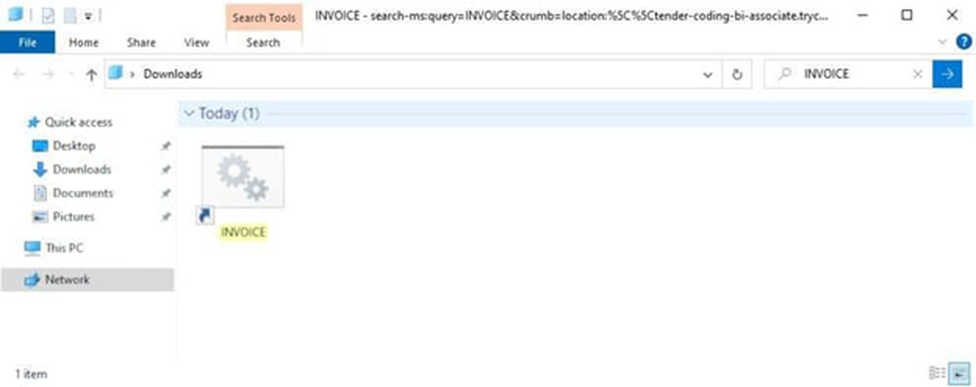
The search retrieves a list of files from the remote server, displaying a single shortcut (LNK) file named "INVOICE". When you click on the file, a command shell script (BAT) located on the same server is launched.
To protect against this threat, Trustwave recommends removing registry entries associated with the search-ms URI protocol by running the following commands:
However, this should be done with caution, as deletion may disrupt legitimate Windows applications and features that depend on this protocol.
Trustwave researchers have discovered a new phishing campaign in which attackers use HTML attachments to abuse the Windows Search protocol (search-ms URI) and distribute malware.
The Windows Search protocol allows applications to open File Explorer to perform searches using specific parameters. Typically the search is performed on the local device, but it is possible to force the search of files on remote servers and use a custom search box name.
Hackers can use this ability to distribute malicious files from remote servers, as Professor Martin Jones first noted in his 2020 research paper .
In June 2022, security researchers developed a powerful attack chain that also exploited a vulnerability in Microsoft Office to launch searches directly from Word documents.
According to Trustwave SpiderLabs, attackers are now actively using this technique, using HTML attachments to launch Windows searches on the attackers' servers.
Recent attacks begin by sending a malicious email with an HTML attachment disguised as an invoice document, packaged in a small ZIP archive. ZIP files help bypass security scanners, which may not analyze archives for malicious content.
The HTML file uses the <meta http-equiv="refresh"> tag to automatically navigate to the malicious URL when the document is opened in the browser. If the meta update fails due to browser settings blocking redirects, the anchor tag provides a clickable link to the malicious URL, which requires action from the user.
The URL is used to perform a search on the remote host using the following parameters:
- Query: search for elements with the “INVOICE” label;
- Crumb: specifies the search scope, linking to the malicious server via Cloudflare;
- Displayname: Renames the search display to “Downloads” to simulate a legitimate interface;
- Location: Uses Cloudflare tunneling to disguise the server, making it appear legitimate.
The search retrieves a list of files from the remote server, displaying a single shortcut (LNK) file named "INVOICE". When you click on the file, a command shell script (BAT) located on the same server is launched.

To protect against this threat, Trustwave recommends removing registry entries associated with the search-ms URI protocol by running the following commands:
- reg delete HKEY_CLASSES_ROOT\search /f
- reg delete HKEY_CLASSES_ROOT\search-ms /f
However, this should be done with caution, as deletion may disrupt legitimate Windows applications and features that depend on this protocol.
