Man
Professional
- Messages
- 3,225
- Reaction score
- 1,016
- Points
- 113
The long-term campaign promises Kim Jong-un to get his hands on the region's strategic data.
Securonix Threat Research specialists have discovered a campaign allegedly associated with the North Korean APT37 group. The attack was called SHROUDED#SLEEP and is aimed at the countries of Southeast Asia. The main feature of the attack is the use of a stealthy PowerShell backdoor called VeilShell.
Cambodia has become the main target of APT37 (Reaper, Group123) attacks, but the geography of the attack may extend to other countries in Southeast Asia. The Securonix report does not specify which industries and companies fell victim to the attacks.
The first stage of the attack begins with the victim opening the ZIP file attached to the email. Inside the archive are executable files in the form of shortcuts (.lnk) that, when run, activate a series of PowerShell commands. Such shortcuts can contain a double extension (.pdf.lnk or .xlsx.lnk) to disguise themselves as PDF or Excel documents. The attackers also modify the icons of the shortcuts to make them appear legitimate.
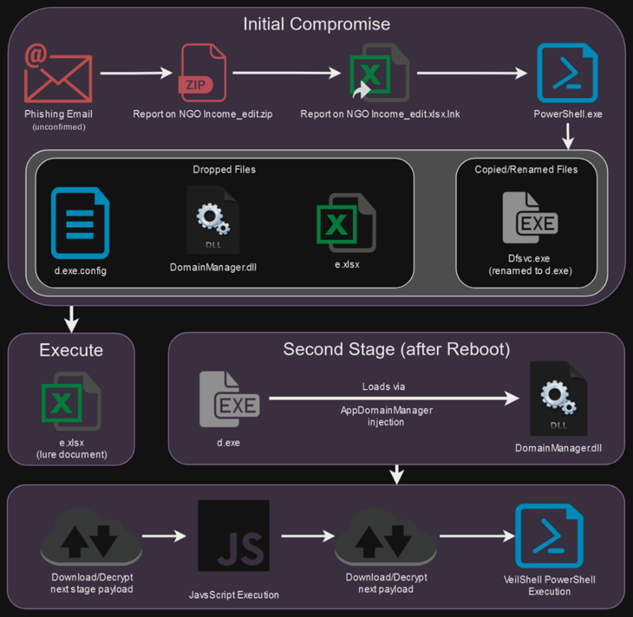
VeilShell infection chain
Encrypted malicious components are located inside the LNK file and are extracted automatically. The main goal of the attack is to install the VeilShell backdoor, which provides remote access to the infected system (RAT), including the ability to download/upload files, create tasks, and change registry settings.
A feature of SHROUDED#SLEEP attacks is the long wait before activating individual stages of the attack to bypass the detection heuristics. Once VeilShell is installed, the code is not executed immediately, but only runs after the system is rebooted.
To gain a foothold in the system, attackers use the AppDomainManager Hijacking technique, which allows malicious code to be silently injected into .NET applications. To do this, the hackers use the «d.exe" file, which looks like a legitimate component of the Microsoft .NET Framework. The EXE file runs the malicious DLL «DomainManager.dll", which allows malicious code to be executed even before the real application is running.
According to Securonix's recommendations, to protect against such attacks, it is recommended to avoid downloading suspicious files from untrusted sources, especially ZIP archives and PDF documents. It's also important to monitor registry changes, network activity, and startup directory activity. The introduction of process-level logging and PowerShell can help detect such malicious activity at an early stage.
Source
Securonix Threat Research specialists have discovered a campaign allegedly associated with the North Korean APT37 group. The attack was called SHROUDED#SLEEP and is aimed at the countries of Southeast Asia. The main feature of the attack is the use of a stealthy PowerShell backdoor called VeilShell.
Cambodia has become the main target of APT37 (Reaper, Group123) attacks, but the geography of the attack may extend to other countries in Southeast Asia. The Securonix report does not specify which industries and companies fell victim to the attacks.
The first stage of the attack begins with the victim opening the ZIP file attached to the email. Inside the archive are executable files in the form of shortcuts (.lnk) that, when run, activate a series of PowerShell commands. Such shortcuts can contain a double extension (.pdf.lnk or .xlsx.lnk) to disguise themselves as PDF or Excel documents. The attackers also modify the icons of the shortcuts to make them appear legitimate.

VeilShell infection chain
Encrypted malicious components are located inside the LNK file and are extracted automatically. The main goal of the attack is to install the VeilShell backdoor, which provides remote access to the infected system (RAT), including the ability to download/upload files, create tasks, and change registry settings.
A feature of SHROUDED#SLEEP attacks is the long wait before activating individual stages of the attack to bypass the detection heuristics. Once VeilShell is installed, the code is not executed immediately, but only runs after the system is rebooted.
To gain a foothold in the system, attackers use the AppDomainManager Hijacking technique, which allows malicious code to be silently injected into .NET applications. To do this, the hackers use the «d.exe" file, which looks like a legitimate component of the Microsoft .NET Framework. The EXE file runs the malicious DLL «DomainManager.dll", which allows malicious code to be executed even before the real application is running.
According to Securonix's recommendations, to protect against such attacks, it is recommended to avoid downloading suspicious files from untrusted sources, especially ZIP archives and PDF documents. It's also important to monitor registry changes, network activity, and startup directory activity. The introduction of process-level logging and PowerShell can help detect such malicious activity at an early stage.
Source
