Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,081
- Points
- 113
Four vulnerabilities can compromise your security.
This week, Microsoft reported four moderate security vulnerabilities in the OpenVPN open source software. These vulnerabilities can be exploited by attackers to execute remote code (RCE) and elevate privileges on the local system (LPE).
An attack that can exploit these vulnerabilities can allow attackers to gain full control over the target devices, which can lead to data leaks, compromise the system, and unauthorized access to confidential information. Successful execution of the attack requires user authentication and a deep understanding of the inner workings of OpenVPN. All versions of OpenVPN up to 2.6.10 and 2.5.10 are under threat.
The list of detected vulnerabilities includes:
Three of these vulnerabilities are related to the openvpnserv component, and the last one concerns the Windows TAP driver.
All of these vulnerabilities can be exploited if an attacker gains access to an OpenVPN user's credentials. This data can be stolen in various ways, such as buying from shadow markets, using malware, or intercepting network traffic.
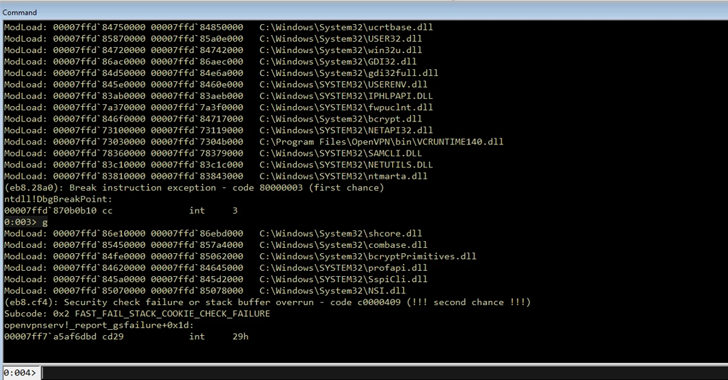
An attack can be executed using various combinations of vulnerabilities, such as CVE-2024-24974 and CVE-2024-27903, or CVE-2024-27459 and CVE-2024-27903, to achieve remote code execution and privilege escalation.
After successfully exploiting these vulnerabilities, attackers can use attack methods such as "Bring your Vulnerable Driver" (BYOVD), which allows them to bypass security mechanisms and get deeper into the system. This makes it possible to disable important processes, such as Microsoft Defender, or interfere with other critical processes, which allows attackers to bypass security tools and manipulate basic system functions.
Source
This week, Microsoft reported four moderate security vulnerabilities in the OpenVPN open source software. These vulnerabilities can be exploited by attackers to execute remote code (RCE) and elevate privileges on the local system (LPE).
An attack that can exploit these vulnerabilities can allow attackers to gain full control over the target devices, which can lead to data leaks, compromise the system, and unauthorized access to confidential information. Successful execution of the attack requires user authentication and a deep understanding of the inner workings of OpenVPN. All versions of OpenVPN up to 2.6.10 and 2.5.10 are under threat.
The list of detected vulnerabilities includes:
- CVE-2024-27459 — a stack overflow vulnerability that causes denial of service (DoS) and privilege escalation on Windows.
- CVE-2024-24974 — unauthorized access to the named channel "\openvpn\service" in Windows, allowing an attacker to interact with it remotely and start operations.
- CVE-2024-27903 — vulnerability in the plugin engine that leads to remote code execution on Windows and privilege escalation and data manipulation on Android, iOS, macOS, and BSD.
- CVE-2024-1305 — a memory overflow vulnerability that causes a denial of service on Windows.
Three of these vulnerabilities are related to the openvpnserv component, and the last one concerns the Windows TAP driver.
All of these vulnerabilities can be exploited if an attacker gains access to an OpenVPN user's credentials. This data can be stolen in various ways, such as buying from shadow markets, using malware, or intercepting network traffic.

An attack can be executed using various combinations of vulnerabilities, such as CVE-2024-24974 and CVE-2024-27903, or CVE-2024-27459 and CVE-2024-27903, to achieve remote code execution and privilege escalation.
After successfully exploiting these vulnerabilities, attackers can use attack methods such as "Bring your Vulnerable Driver" (BYOVD), which allows them to bypass security mechanisms and get deeper into the system. This makes it possible to disable important processes, such as Microsoft Defender, or interfere with other critical processes, which allows attackers to bypass security tools and manipulate basic system functions.
Source

