Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Espionage is one of the country's ways to learn about the technical progress of competitors.
A joint alert issued by the German and South Korean intelligence agencies indicates an ongoing espionage campaign targeting the defense sector on behalf of the North Korean government.
According to the intelligence services, the purpose of the attacks is to steal information about advanced military technologies for the modernization of weapons and the development of new military capabilities. The warning highlights two cases involving North Korean hackers, including the Lazarus group, and describes the Tactics, Techniques, and Procedures (TTPs) they use.
The first case concerns an incident at the end of 2022, when a North Korean attacker penetrated the systems of the marine and shipping Technology research center, performing an attack on the supply chain by compromising the systems of a company that serviced the target organization's web servers. The attack included the theft of SSH credentials, the use of legitimate tools, lateral movement in the network (Lateral Movement) and attempts to hide their activities on the network.
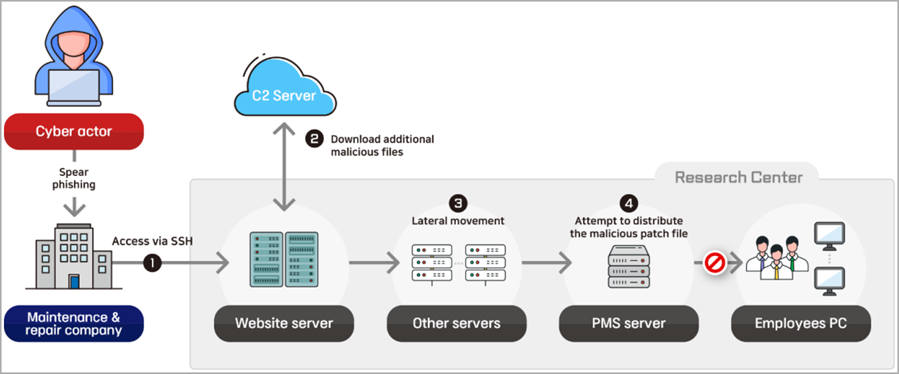
Supply chain attack scheme
In the second example, the Lazarus group attacked the defense sector using the "Operation Dream Job" campaign tactic, targeting employees of cryptocurrency firms and software developers. In one case, Lazarus delivered two backdoors, LightlessCan and BlindingCan, to the system through an employee of an aerospace company in Spain.
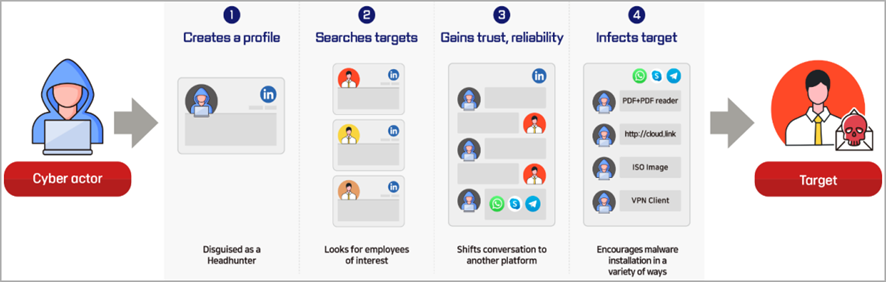
Social Engineering Attack Chain
The warning highlights the importance of training employees to recognize modern methods of cyber attacks, apply the principle of minimum privileges, strengthen authentication and update management procedures, and audit logs, including user access, to improve overall security.
Security measures such as restricting access of IT service providers to the systems required for remote maintenance, careful monitoring of access logs to detect unauthorized events, the use of multi-factor authentication (MFA) for all accounts, and strict user authentication policies for the patch management system (PMS). they are recommended for countering such attacks.
A joint alert issued by the German and South Korean intelligence agencies indicates an ongoing espionage campaign targeting the defense sector on behalf of the North Korean government.
According to the intelligence services, the purpose of the attacks is to steal information about advanced military technologies for the modernization of weapons and the development of new military capabilities. The warning highlights two cases involving North Korean hackers, including the Lazarus group, and describes the Tactics, Techniques, and Procedures (TTPs) they use.
The first case concerns an incident at the end of 2022, when a North Korean attacker penetrated the systems of the marine and shipping Technology research center, performing an attack on the supply chain by compromising the systems of a company that serviced the target organization's web servers. The attack included the theft of SSH credentials, the use of legitimate tools, lateral movement in the network (Lateral Movement) and attempts to hide their activities on the network.

Supply chain attack scheme
In the second example, the Lazarus group attacked the defense sector using the "Operation Dream Job" campaign tactic, targeting employees of cryptocurrency firms and software developers. In one case, Lazarus delivered two backdoors, LightlessCan and BlindingCan, to the system through an employee of an aerospace company in Spain.

Social Engineering Attack Chain
The warning highlights the importance of training employees to recognize modern methods of cyber attacks, apply the principle of minimum privileges, strengthen authentication and update management procedures, and audit logs, including user access, to improve overall security.
Security measures such as restricting access of IT service providers to the systems required for remote maintenance, careful monitoring of access logs to detect unauthorized events, the use of multi-factor authentication (MFA) for all accounts, and strict user authentication policies for the patch management system (PMS). they are recommended for countering such attacks.

