Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
Greetings, reader. More and more people prefer to keep their savings in cryptocurrency, and there is a logical explanation for this. Security, anonymity, practicality, and relative simplicity.
But this is only one side of the coin, because once you open the news, you will notice dozens of headlines about another theft of someone's savings. In one of my articles, I already told you about the possible risks for crypto holders.
But recently, researchers from the cybersecurity company Trendmicro noticed a new type of malware that spread through phishing emails and the vulnerability CVE-2015-2291 in the Intel driver. The name of this threat is Enigma.
All versions of Windows are affected by this bug. The virus can perform both the functions of a stiller, stealing files containing secret phrases from wallets and cookies, and the functions of a dropper, downloading the next stage or a completely different malware to the victim's device.
Droppers are a family of malicious programs designed for unauthorized and hidden installation on the victim's computer of other malicious programs contained in the body of the dropper itself or downloaded over the network.
Basically, everything happens quite banal, and there are two options for phishing attacks using this stealer.
This is a vulnerability in the driver iqvw64e.sys, which is responsible for diagnosing the network adapter. Yes, this is the same "Device Troubleshooting" function.
Since this component can communicate directly with the device and execute many kernel routines, providing access to several IOCTLS, it becomes a good target for attackers.
IOCTL, or I / O codes, are used for communication between user-mode applications and drivers, or for internal communication between drivers. You can find out more here.
An attacker can gain access to the following codes.
The attacker's use of this hole in Windows protection can be viewed from different angles, since it has more than enough applications, but in the Enigma Stealer incident, the attackers simply replaced the Windows Defender driver with their malicious file or increased the privileges of the virus process, depending on the circumstances.
So, after unpacking the cherished archive, two files appear before our eyes, as mentioned earlier: an unremarkable text document and an executable .exe, which is very clumsily disguised as Microsoft Word.
Naturally, this does not give us anything, but the file description does not fit in with the masking a little.
For the classics, we'll use DIE for more information.
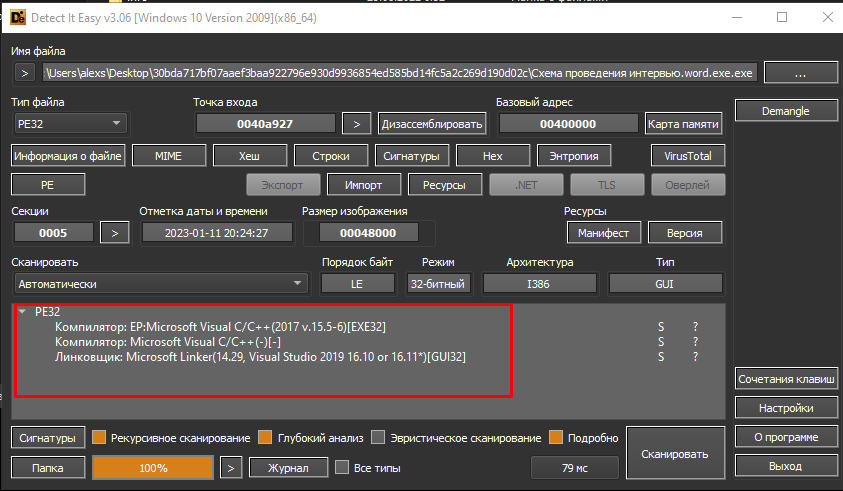
Like the previous subjects, this is a PE file written in C / C++, and the compiler used is Microsoft Visual C / C++ 2017. But here the attacker neglected to use a method that changes the compilation date, which is not so critical.
Now let's use Hydra to determine the specifics of how this virus works. And at this stage, the most interesting part begins, because the malware carrier is not a complete structure and consists of separate stages, each of which performs its own functions and initiates the next one.
Let me outline the overall infrastructure for you.
According to the classics, we start with imported libraries, there are only four of them:
This loader executes the following chain of processes:
API hashing is a method that malware uses to hide potentially dangerous API functions from static detection. In simple words, the malware masks its requests to the functions of certain libraries in order to stay in the shadows and get away from the eyes of the antivirus.
Irrelevant code is code snippets that have nothing to do with malware. These may be fragments of other applications that do not interact with the victim's system in any way. This is done in order to confuse and complicate the analysis process.
So, let's take a closer look at hashing malicious functions in our sample of the first stage.
For example, the obviously malicious function "CreateMutexA", which is responsible for checking and creating a mutex.
A mutex is a synchronization primitive that provides mutual exclusion of execution of critical code sections.
In very simple terms, this is a simple check whether the virus process is already running on this device or not.
So, in our code, it is represented by the value 0x0GD53265B. This is the hash value that is used to call the corresponding function. If in theory this can circumvent several antivirus programs, in practice the effectiveness is extremely low. The fact is that this value is still decrypted to the above-mentioned function. But of course, this complicates the analysis process.
The hash is directly used via the "mw_resolveAPI" function with two arguments specified. The first one is responsible for the hash of the library that is being accessed, while the second one is directly the function itself.
And as it turned out, Hydra failed again. By showing an import table of four .dll files, which turned out to be incorrect. In fact, the malware uses more than 15 system files.
SOFTWARE\ Microsoft\Cryptography\MachineGuid
The received value will also be used as an ID on the command server.
The malware then deletes the following registry path:
KCU\SOFTWARE\Intel
Sometimes irrevocably. But sometimes it creates it again with two new values of HWID and ID. Either the author does not understand the meaning of this action, or it is really meaningless.
Next, a mutex is created:
After that, it communicates with the command server, whose IP address was encrypted using the same user hash, and looks like this:
193.56[.]146.29
It is also worth noting that this is a regular PHP server, but we will return to it a little later.
The malware sends the system ID and version to the server .NET Framework.
But in order to load the next stage, the virus will already communicate with the bot's API in Telegram. The request is built as a normal file request:
https://api[.]telegram[.]org/bot/TOKEN/updatetask.dll
Then the "Bot received" message is sent, and the second stage starts from this.
It has a malicious code .dll has two main functions.
This is done using the API request to the GetTokenInformation function:
Next, the Windows Defender system driver is removed and, using the vulnerability, the malware loads its own. It is noteworthy that the name of this file is written in Cyrillic — driver.ѕуѕ.
After that, it is fixed in the system, and the dropper adds itself to the task scheduler and registry.
And finally, the next stage is loaded and launched, it is also represented by the dropper. There is nothing remarkable about the download itself, it happens in the same way via the Telegram API.
This time it is written in C# and weighs only 11 KB.
Its only function is to download the final payload as an Enigma stiller. But for some reason, it can be controlled using the same Telegram API. If an attacker simply changes his mind, he can stop the execution of the final phase.
And at this point, the author lost himself, the hope of seeing something unique and exclusive completely disappeared.
As it turned out, Enigma is a modified version of this very repository.
So be it, according to the classics, we will use DIE for more information.
One interesting thing to note is that it is written in C# and a method that changes the compilation date has already been used here.
This is "Timestomping", it is an anti-criminalistic method used to mislead the investigation and rapid response specialists.
Virustotal showed remarkable detection rates:
And now directly to the point. For reverse engineering malware written in C#, we will use the following utility setup:
Based on the classic approach, we will mark up the main algorithm of the malware's operation.
Immediately after that, the malware config is processed. If it is missing, it is downloaded from the command server.
The configuration of our malware is as follows:
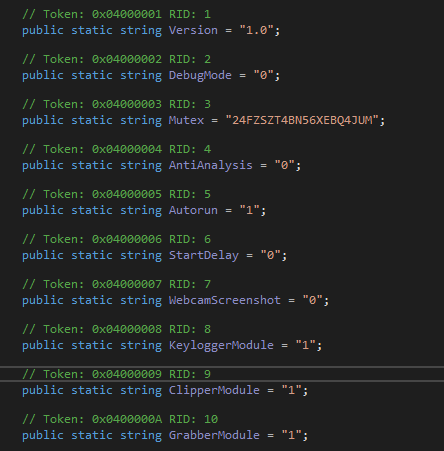
Based on this, we can determine the modules used and the basic capabilities of the stiller. The main ones are Keylogger and Grabber.
Keylogger — in this situation, it is a module whose main purpose is hidden monitoring of keystrokes on the keyboard and logging.
Grabber — a module that is responsible for directly collecting cookies and other files.
The malware then begins collecting system information and steals user information, tokens, and passwords from various web browsers and applications, such as Google Chrome, Microsoft Edge, Microsoft Outlook, Telegram, Signal, OpenVPN, and others. The malware also creates screenshots and sends all the data to Telegram.
After that, the collected data will be archived using "CreateArchive", you can see this in the screenshot, as well as the list of collected information:
The logic of sending data to the Telegram bot is as follows, there is nothing particularly remarkable in it:
For dynamic analysis, we already have the following setup of utilities (all of them are publicly available):
Immediately after opening, the virus process establishes a connection to the PHP command server, and nothing happens for a while.
Then there are several more processes that are already starting to receive some information from the same IP address. This is how the second stage loads.
Next, a new process starts looming in ProcessHacker Update.exe, loads the CPU to the maximum and subsides.
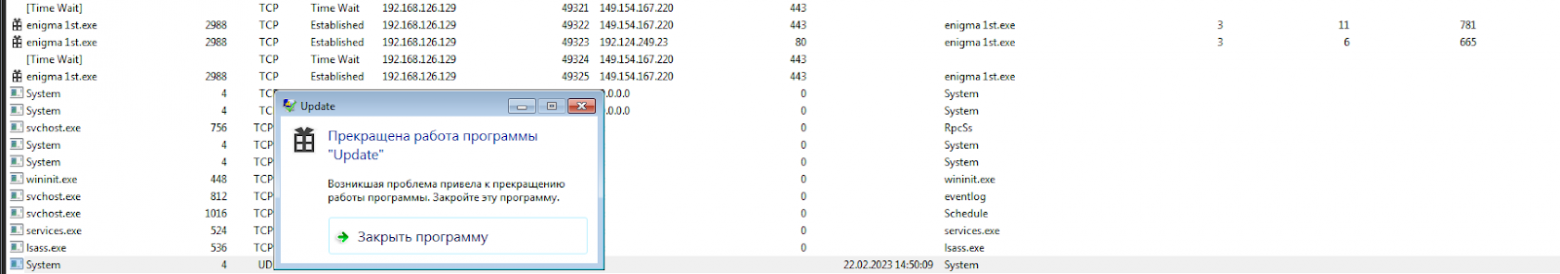
This indicates the successful completion of the second stage of the malware, because the task is responsible for the daily execution of malware .dll of the updateTask file.
In the registry snapshots, you can see the same deletion of the Intel partition in the Windows registry:
But after that, the execution was interrupted for reasons unknown to me.
The second one is not particularly interesting for us, since it immediately refers to the Telegram API:
But the first one is quite an interesting instance, since some useful information can be extracted from it.
When going to this IP address, we were met with a very unfriendly authorization form, but I had the idea to check the availability of the file info.php. And it turned out that he was present here.
PHPinfo is a function that displays information about the PHP and server configuration. It helps PHP developers to see which modules are active and which versions of these modules are running on the server
And the information file itself looked like this:
Deniska Hacker? Interesting. But what is more striking is that this server is most likely located in Moscow, but I do not exclude the possibility that this information was provided in order to mislead the investigation:
Attacks using Enigma Stealer are targeted and aimed at crypto holders, but no one said that villains can't attack everyone in a row. As in most cases, the best defense against this and other malware is a head on your shoulders.
Never be fooled by various mailing lists and everything else, where you are promised golden mountains and a prestigious job. Moreover, do not download attachments from such suspicious emails.
At the moment, Enigma and its dropper infrastructure are not particularly dangerous. After all, every step of it is easily determined by most antivirus applications.
And that's it for me. Be there.
(c) https://habr.com/ru/companies/first/articles/721226/
But this is only one side of the coin, because once you open the news, you will notice dozens of headlines about another theft of someone's savings. In one of my articles, I already told you about the possible risks for crypto holders.
But recently, researchers from the cybersecurity company Trendmicro noticed a new type of malware that spread through phishing emails and the vulnerability CVE-2015-2291 in the Intel driver. The name of this threat is Enigma.
All versions of Windows are affected by this bug. The virus can perform both the functions of a stiller, stealing files containing secret phrases from wallets and cookies, and the functions of a dropper, downloading the next stage or a completely different malware to the victim's device.
Droppers are a family of malicious programs designed for unauthorized and hidden installation on the victim's computer of other malicious programs contained in the body of the dropper itself or downloaded over the network.
Ways to infect a new threat
The so-called Enigma Stealer is spreading quite quickly, infecting users who are somehow connected with the cryptosphere, not only in Russia, but also around the world. Special attention was paid to Central Europe, where victims are already estimated in the hundreds.Basically, everything happens quite banal, and there are two options for phishing attacks using this stealer.
- The victim receives an email in which the attacker introduces himself as a well-known company and offers employment.According to the classic approach, the attachments will contain an archive containing a malicious file disguised as a Microsoft Word document.
- The victim receives an email to their email address, but the villain introduces himself as a journalist and asks you to complete a small survey related to cryptocurrency.
Brief technical analysis of the CVE-2015-2291 vulnerability
As mentioned earlier, the malware can also be spread using this vulnerability, but it is mainly used as an additional step to increase privileges or load a virus driver. Let's talk a little bit about this hole, which Microsoft has been trying to close for several years. A more detailed description can be found here.This is a vulnerability in the driver iqvw64e.sys, which is responsible for diagnosing the network adapter. Yes, this is the same "Device Troubleshooting" function.
Since this component can communicate directly with the device and execute many kernel routines, providing access to several IOCTLS, it becomes a good target for attackers.
IOCTL, or I / O codes, are used for communication between user-mode applications and drivers, or for internal communication between drivers. You can find out more here.
An attacker can gain access to the following codes.
- The I / O control code that will be used to access the vulnerable code path is 0x80862007.
- Code 0x33 for accessing memmov.
- Code 0x30 for accessing memset.
- Code 0x27 for accessing DeviceControl, which allows an attacker to pass the structure and inject it into a kernel subroutine.
The attacker's use of this hole in Windows protection can be viewed from different angles, since it has more than enough applications, but in the Enigma Stealer incident, the attackers simply replaced the Windows Defender driver with their malicious file or increased the privileges of the virus process, depending on the circumstances.
Brief statistical analysis of the malware
So, for statistical analysis, we will use the following set of utilities, all of them are free and are publicly available:- DIE-Detect it Easy: a multi-functional tool that has a huge arsenal. It will allow us to get ahead of the malware compiler type, language, libraries, and import/export tables with subsequent disassembly.
- Hidra — like the previous utility, already shone in my article. An excellent and multifunctional tool for reverse engineering.
- IDA PRO is also a tool for reverse engineering.
- Reko is a decompiler that is also familiar to us from previous articles.

So, after unpacking the cherished archive, two files appear before our eyes, as mentioned earlier: an unremarkable text document and an executable .exe, which is very clumsily disguised as Microsoft Word.
Naturally, this does not give us anything, but the file description does not fit in with the masking a little.
For the classics, we'll use DIE for more information.

Like the previous subjects, this is a PE file written in C / C++, and the compiler used is Microsoft Visual C / C++ 2017. But here the attacker neglected to use a method that changes the compilation date, which is not so critical.
Now let's use Hydra to determine the specifics of how this virus works. And at this stage, the most interesting part begins, because the malware carrier is not a complete structure and consists of separate stages, each of which performs its own functions and initiates the next one.
Let me outline the overall infrastructure for you.
- The first stage. The initial loader. Only download the necessary files to complete the next step.
- The second stage. Secondary loader. Submitted by the library UpdateTask.dll, which exploits the vulnerability CVE-2015-2291, increases privileges and disables Windows Defender. It also loads the third-stage dropper.
- The third stage. The dropper again. Downloads the main payload as an Enigma Stealer.
- The fourth stage. Enigma deployment.
Analysis of the first stage
You have already seen general information about the first stage dropper above, so let's go directly to the short code analysis. We will also touch on the specific features of this particular type of malware.According to the classics, we start with imported libraries, there are only four of them:
- USER32.dll
- ADVAPI32.dll
- KERNELL.dll
- RPCRT4.dll
This loader executes the following chain of processes:
- l. Decrypt encrypted strings.
- ll. Creating a mutex and loading the second stage.
l. Decryption of encrypted strings
The creators of this miracle clearly know their business, as the dropper uses several techniques at once, which complicate the detection and reverse engineering process. Hashed APIs and irrelevant code can be found everywhere in the code.API hashing is a method that malware uses to hide potentially dangerous API functions from static detection. In simple words, the malware masks its requests to the functions of certain libraries in order to stay in the shadows and get away from the eyes of the antivirus.
Irrelevant code is code snippets that have nothing to do with malware. These may be fragments of other applications that do not interact with the victim's system in any way. This is done in order to confuse and complicate the analysis process.

So, let's take a closer look at hashing malicious functions in our sample of the first stage.
For example, the obviously malicious function "CreateMutexA", which is responsible for checking and creating a mutex.
A mutex is a synchronization primitive that provides mutual exclusion of execution of critical code sections.
In very simple terms, this is a simple check whether the virus process is already running on this device or not.
So, in our code, it is represented by the value 0x0GD53265B. This is the hash value that is used to call the corresponding function. If in theory this can circumvent several antivirus programs, in practice the effectiveness is extremely low. The fact is that this value is still decrypted to the above-mentioned function. But of course, this complicates the analysis process.
The hash is directly used via the "mw_resolveAPI" function with two arguments specified. The first one is responsible for the hash of the library that is being accessed, while the second one is directly the function itself.

And as it turned out, Hydra failed again. By showing an import table of four .dll files, which turned out to be incorrect. In fact, the malware uses more than 15 system files.
ll. Creating a mutex and loading the second stage
First, the malware extracts the MachineGuid (digital identifier of the system), this happens by accessing the Windows registry using the following path:SOFTWARE\ Microsoft\Cryptography\MachineGuid
The received value will also be used as an ID on the command server.
The malware then deletes the following registry path:
KCU\SOFTWARE\Intel
Sometimes irrevocably. But sometimes it creates it again with two new values of HWID and ID. Either the author does not understand the meaning of this action, or it is really meaningless.
Next, a mutex is created:

After that, it communicates with the command server, whose IP address was encrypted using the same user hash, and looks like this:
193.56[.]146.29
It is also worth noting that this is a regular PHP server, but we will return to it a little later.

The malware sends the system ID and version to the server .NET Framework.
But in order to load the next stage, the virus will already communicate with the bot's API in Telegram. The request is built as a normal file request:
https://api[.]telegram[.]org/bot/TOKEN/updatetask.dll
Then the "Bot received" message is sent, and the second stage starts from this.
Brief analysis of the second stage
As I wrote above, the payload of this stage is presented in the form .dll file. It is 498 KB in size and written in C++.
It has a malicious code .dll has two main functions.
- Disable Microsoft Defender by deploying a malicious driver. The same exploitation of CVE-2015-2291 described earlier.
- Loading and executing the next step.
This is done using the API request to the GetTokenInformation function:

Next, the Windows Defender system driver is removed and, using the vulnerability, the malware loads its own. It is noteworthy that the name of this file is written in Cyrillic — driver.ѕуѕ.
After that, it is fixed in the system, and the dropper adds itself to the task scheduler and registry.
And finally, the next stage is loaded and launched, it is also represented by the dropper. There is nothing remarkable about the download itself, it happens in the same way via the Telegram API.
Brief analysis of the third stage
As for me, it is no longer essential and was not needed at all, but it is sometimes very difficult for me to catch the motives of intruders. Well, before our eyes is another dropper.This time it is written in C# and weighs only 11 KB.

Its only function is to download the final payload as an Enigma stiller. But for some reason, it can be controlled using the same Telegram API. If an attacker simply changes his mind, he can stop the execution of the final phase.

Final Phase Analysis: Enigma Stealer
Finally. We get the following data after a simple visual inspection of the stiller: 1534 KB, original name — stub.exe and copywriting, which links to the GitHub repository — Stealerum.And at this point, the author lost himself, the hope of seeing something unique and exclusive completely disappeared.
As it turned out, Enigma is a modified version of this very repository.
So be it, according to the classics, we will use DIE for more information.

One interesting thing to note is that it is written in C# and a method that changes the compilation date has already been used here.
This is "Timestomping", it is an anti-criminalistic method used to mislead the investigation and rapid response specialists.
Virustotal showed remarkable detection rates:

And now directly to the point. For reverse engineering malware written in C#, we will use the following utility setup:
- dnSpy is a decompiler, disassembler, and debugger all rolled into one. Good, simple and free.
- Reco & dotPeek — a fallback option that performs the same functions. And they have already appeared in my articles several times.
Based on the classic approach, we will mark up the main algorithm of the malware's operation.
- Create a working directory and upload configuration files.
- Collecting information about the system and stealing data.
- Sending data to an attacker via a telegram bot.
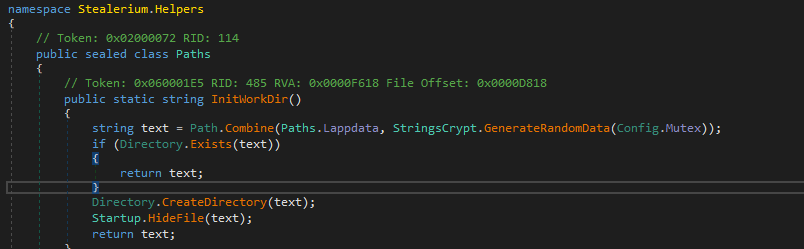
Creating a working directory and uploading configuration files
Immediately after launch, the process of creating a working directory occurs. This process differs in different versions of Stiller, but specifically in our case, it is represented by the following code section:
Immediately after that, the malware config is processed. If it is missing, it is downloaded from the command server.
The configuration of our malware is as follows:

Based on this, we can determine the modules used and the basic capabilities of the stiller. The main ones are Keylogger and Grabber.
Keylogger — in this situation, it is a module whose main purpose is hidden monitoring of keystrokes on the keyboard and logging.
Grabber — a module that is responsible for directly collecting cookies and other files.
The malware then begins collecting system information and steals user information, tokens, and passwords from various web browsers and applications, such as Google Chrome, Microsoft Edge, Microsoft Outlook, Telegram, Signal, OpenVPN, and others. The malware also creates screenshots and sends all the data to Telegram.
After that, the collected data will be archived using "CreateArchive", you can see this in the screenshot, as well as the list of collected information:


The logic of sending data to the Telegram bot is as follows, there is nothing particularly remarkable in it:

A brief dynamic analysis of the malware
All tests are performed on the VM. In any case, do not repeat this yourself, especially on the main one.For dynamic analysis, we already have the following setup of utilities (all of them are publicly available):
- ProcessHacker — simple and tasteful, let's watch how the virus interacts with others .the dll and the system.
- TCPView is a utility that tracks outgoing TCP connections.
- Regshot is a very simple open source application that allows you to view changes in the registry after running the malware.
Immediately after opening, the virus process establishes a connection to the PHP command server, and nothing happens for a while.

Then there are several more processes that are already starting to receive some information from the same IP address. This is how the second stage loads.
Next, a new process starts looming in ProcessHacker Update.exe, loads the CPU to the maximum and subsides.

This indicates the successful completion of the second stage of the malware, because the task is responsible for the daily execution of malware .dll of the updateTask file.
In the registry snapshots, you can see the same deletion of the Intel partition in the Windows registry:

But after that, the execution was interrupted for reasons unknown to me.
A little bit about the PHP command server
In total, we managed to notice two IP addresses, the first one comes from the initial stage, and the second one comes from a malicious one .dll.The second one is not particularly interesting for us, since it immediately refers to the Telegram API:

But the first one is quite an interesting instance, since some useful information can be extracted from it.
When going to this IP address, we were met with a very unfriendly authorization form, but I had the idea to check the availability of the file info.php. And it turned out that he was present here.
PHPinfo is a function that displays information about the PHP and server configuration. It helps PHP developers to see which modules are active and which versions of these modules are running on the server

And the information file itself looked like this:

Deniska Hacker? Interesting. But what is more striking is that this server is most likely located in Moscow, but I do not exclude the possibility that this information was provided in order to mislead the investigation:

Conclusions
And this is how this analysis comes to an end. In fact, the use of multiple droppers does have an advantage in some ways. After all, an attacker can intervene at almost any stage and make adjustments if something went wrong with his plan.Attacks using Enigma Stealer are targeted and aimed at crypto holders, but no one said that villains can't attack everyone in a row. As in most cases, the best defense against this and other malware is a head on your shoulders.
Never be fooled by various mailing lists and everything else, where you are promised golden mountains and a prestigious job. Moreover, do not download attachments from such suspicious emails.
At the moment, Enigma and its dropper infrastructure are not particularly dangerous. After all, every step of it is easily determined by most antivirus applications.
And that's it for me. Be there.
(c) https://habr.com/ru/companies/first/articles/721226/

