Carding Forum
Professional
BlankBot Trojan, designed to attack owners of Android mobile devices, has rich functionality and allows operators to execute commands on infected devices.
Researchers at Intel 471 discovered BlankBot on July 24, although the first samples of the malware date back to late June. Almost none of these samples are detected by most antiviruses.
Operators disguise the Trojan as useful utilities, which immediately after installation request access to the special capabilities of the Android operating system for correct operation.
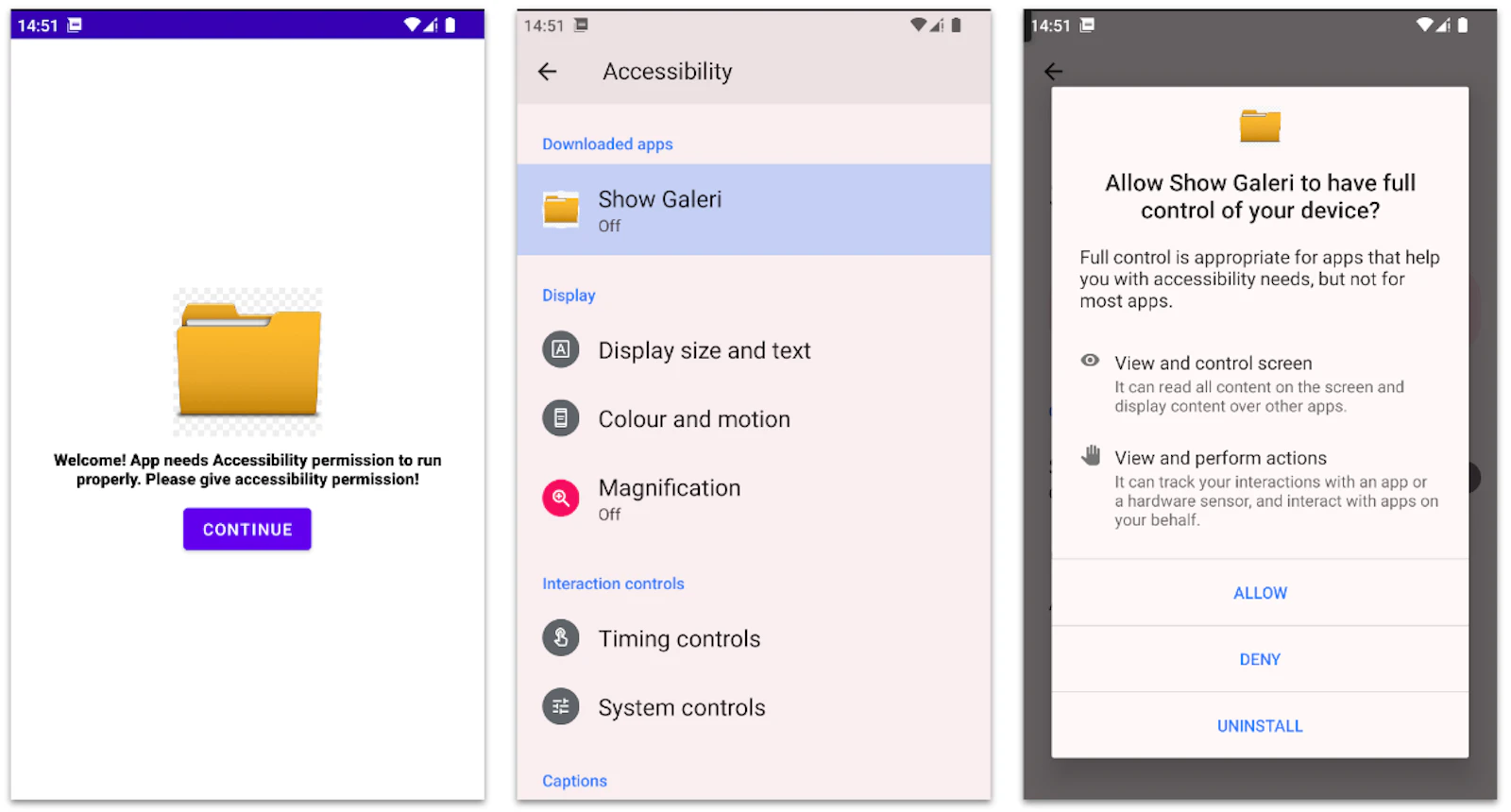
After this, BlankBot, under the pretext of installing an update, receives all the necessary rights to control the target device.
On Android 13 and newer versions of the mobile OS, the malware uses a session package installer. At the same time, the user is asked to allow the installation of software from third-party sources.
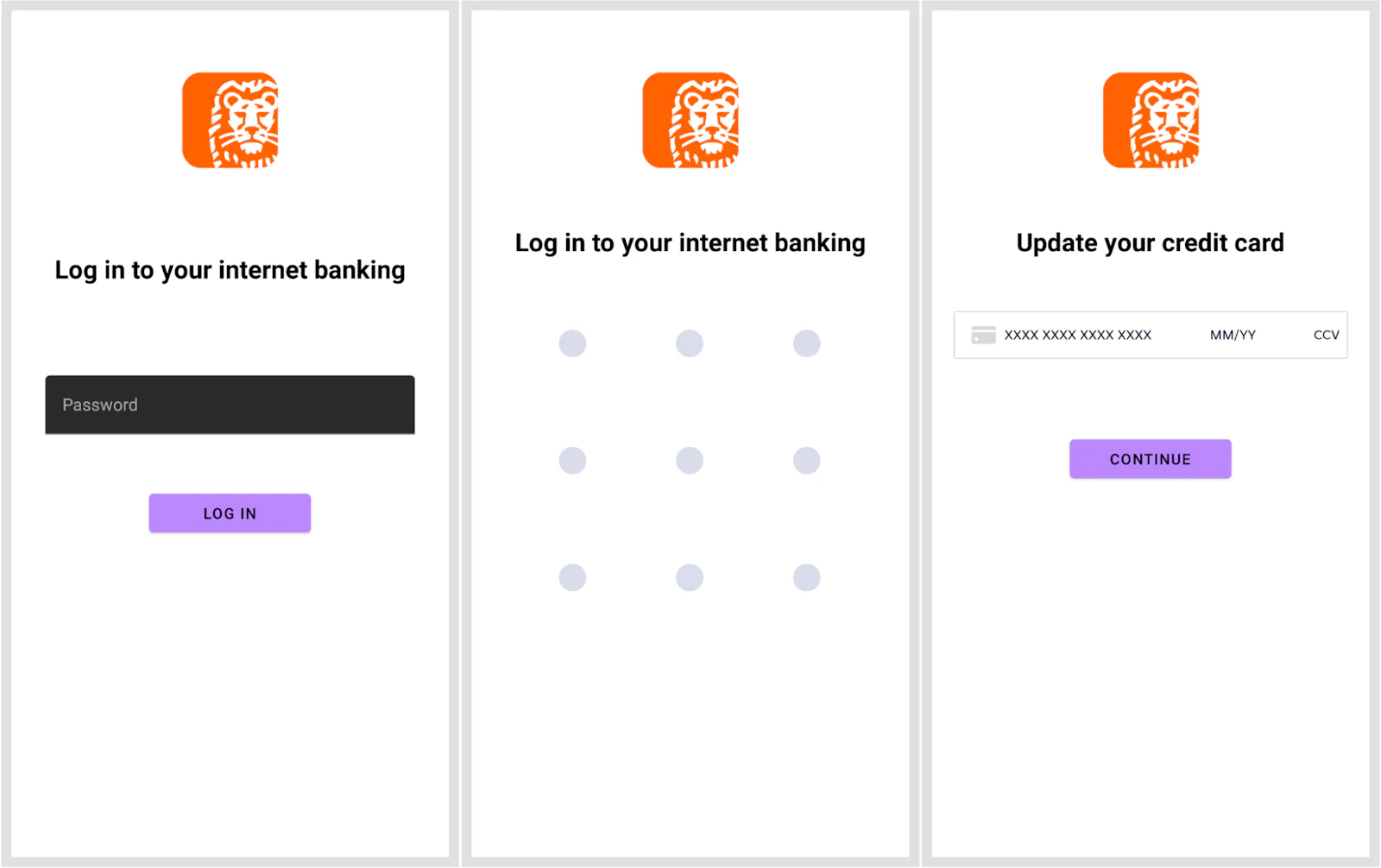
Once the Trojan has all the necessary permissions, it can record any action on the device. For example, BlankBot extracts all confidential information, intercepts SMS messages and makes a list of installed applications, and can also infiltrate processes to steal bank account information.
All collected data is sent to the command and control (C2) server via an HTTP GET request. The malware then switches to WebSocket to communicate with operators.
The MediaProjection and MediaRecorder APIs are used to record actions on the display. After receiving the appropriate command from C2, the Trojan creates a special window to overlay on top of legitimate applications, which allows it to intercept all input information.
Source
Researchers at Intel 471 discovered BlankBot on July 24, although the first samples of the malware date back to late June. Almost none of these samples are detected by most antiviruses.
Operators disguise the Trojan as useful utilities, which immediately after installation request access to the special capabilities of the Android operating system for correct operation.

After this, BlankBot, under the pretext of installing an update, receives all the necessary rights to control the target device.
On Android 13 and newer versions of the mobile OS, the malware uses a session package installer. At the same time, the user is asked to allow the installation of software from third-party sources.
Once the Trojan has all the necessary permissions, it can record any action on the device. For example, BlankBot extracts all confidential information, intercepts SMS messages and makes a list of installed applications, and can also infiltrate processes to steal bank account information.
All collected data is sent to the command and control (C2) server via an HTTP GET request. The malware then switches to WebSocket to communicate with operators.
The MediaProjection and MediaRecorder APIs are used to record actions on the display. After receiving the appropriate command from C2, the Trojan creates a special window to overlay on top of legitimate applications, which allows it to intercept all input information.

Source







