Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Installing mobile apps has never been so dangerous.
A new variant of the Android malware called Octo2, which is an improved version of Octo (ExobotCompact), is being distributed in Europe. According to ThreatFabric experts, the new version could significantly affect the cybersecurity landscape.
Octo2 is an update to Malware-as-a-Service (MaaS), a malware distributed among cybercriminals. This version features improved capabilities for remote management of the victim's devices and the use of new masking techniques, including Domain Name Generation (DGA), which allows you to bypass security mechanisms and remain undetected.
The Exobot family was first spotted in 2016 as a banking Trojan capable of executing interface overlay attacks, intercepting calls and messages. In 2019, a lightweight version of ExobotCompact appeared, and in 2021, an improved version of it called Octo appeared. It was this version that became the basis for further changes.
In 2022, cybercriminals actively discussed Octo on underground forums. Since then, the activity of the malware has only increased, and soon it began to be used in various regions of the world, including Europe, the United States and Asia.
The main change in 2024 is due to the leak of the Octo source code, which led to several forks of the program. However, the greatest threat is the original Octo2, developed by the creator of Octo and distributed to those who previously used the first version.
Octo2 has introduced significant updates, including stability improvements for remote device management and methods for bypassing analysis and discovery systems. Octo2 also implemented a system that allows you to intercept push notifications from victims' devices and hide them, thereby depriving users of important notifications. This poses a threat to many mobile applications, as attackers can easily redirect data and perform fraudulent actions.
The first campaigns using Octo2 have already been recorded in countries such as Italy, Poland, Moldova and Hungary. The malware masquerades as popular apps such as Google Chrome and NordVPN, which helps sneak into users' devices undetected.
In the detected campaigns, the Zombinder service acts as the first stage of installation: after launching, Zombinder requests the installation of an additional "plugin", which is actually Octo2, thereby successfully bypassing Android 13+ restrictions.
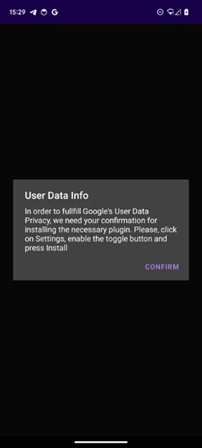
Zombinder Asks for Permission to Install a 'Necessary Plugin' in the Form of the Octo2 Trojan
One of the key elements of Octo2 was the integration of a new method of generating domain names (Domain Generation Algorithm, DGA), which allows the malware to dynamically modify C2 servers. This complicates the work of researchers and antivirus companies, as new domains are created automatically, making them more difficult to block.
In addition, Octo2 uses a new encryption system for data transmitted to management servers, with a dynamic key for each request, which strengthens protection against analysis and detection.
With its improved remote access and stealth capabilities, Octo2 poses a serious threat to mobile users, especially those who use banking apps. The program is capable of silently performing fraudulent operations directly on the victim's device, which makes the malware one of the most dangerous mobile Trojans.
Source
A new variant of the Android malware called Octo2, which is an improved version of Octo (ExobotCompact), is being distributed in Europe. According to ThreatFabric experts, the new version could significantly affect the cybersecurity landscape.
Octo2 is an update to Malware-as-a-Service (MaaS), a malware distributed among cybercriminals. This version features improved capabilities for remote management of the victim's devices and the use of new masking techniques, including Domain Name Generation (DGA), which allows you to bypass security mechanisms and remain undetected.
The Exobot family was first spotted in 2016 as a banking Trojan capable of executing interface overlay attacks, intercepting calls and messages. In 2019, a lightweight version of ExobotCompact appeared, and in 2021, an improved version of it called Octo appeared. It was this version that became the basis for further changes.
In 2022, cybercriminals actively discussed Octo on underground forums. Since then, the activity of the malware has only increased, and soon it began to be used in various regions of the world, including Europe, the United States and Asia.
The main change in 2024 is due to the leak of the Octo source code, which led to several forks of the program. However, the greatest threat is the original Octo2, developed by the creator of Octo and distributed to those who previously used the first version.
Octo2 has introduced significant updates, including stability improvements for remote device management and methods for bypassing analysis and discovery systems. Octo2 also implemented a system that allows you to intercept push notifications from victims' devices and hide them, thereby depriving users of important notifications. This poses a threat to many mobile applications, as attackers can easily redirect data and perform fraudulent actions.
The first campaigns using Octo2 have already been recorded in countries such as Italy, Poland, Moldova and Hungary. The malware masquerades as popular apps such as Google Chrome and NordVPN, which helps sneak into users' devices undetected.
In the detected campaigns, the Zombinder service acts as the first stage of installation: after launching, Zombinder requests the installation of an additional "plugin", which is actually Octo2, thereby successfully bypassing Android 13+ restrictions.

Zombinder Asks for Permission to Install a 'Necessary Plugin' in the Form of the Octo2 Trojan
One of the key elements of Octo2 was the integration of a new method of generating domain names (Domain Generation Algorithm, DGA), which allows the malware to dynamically modify C2 servers. This complicates the work of researchers and antivirus companies, as new domains are created automatically, making them more difficult to block.
In addition, Octo2 uses a new encryption system for data transmitted to management servers, with a dynamic key for each request, which strengthens protection against analysis and detection.
With its improved remote access and stealth capabilities, Octo2 poses a serious threat to mobile users, especially those who use banking apps. The program is capable of silently performing fraudulent operations directly on the victim's device, which makes the malware one of the most dangerous mobile Trojans.
Source



