Man
Professional
- Messages
- 3,225
- Reaction score
- 1,016
- Points
- 113
Cybercriminals manage to attack the same sites at the same time. How do they divide the revenue?
Security researchers at Jscrambler have discovered a new digital skimming campaign that uses Unicode characters, many of which are invisible, to hide malicious code called Mongolian Skimmer. The main purpose of the skimmer is to steal sensitive data entered on the checkout pages of online stores, including financial information.
The Mongolian Skimmer is injected into compromised sites in the form of an embedded script that downloads the main malicious code from an external server. At the same time, the script is able to bypass analysis and debugging measures by disabling certain functions when the developer tools are activated in the browser.
Thanks to the ability of JavaScript to use any Unicode characters in identifiers, attackers are able to successfully hide malicious functionality from prying eyes.
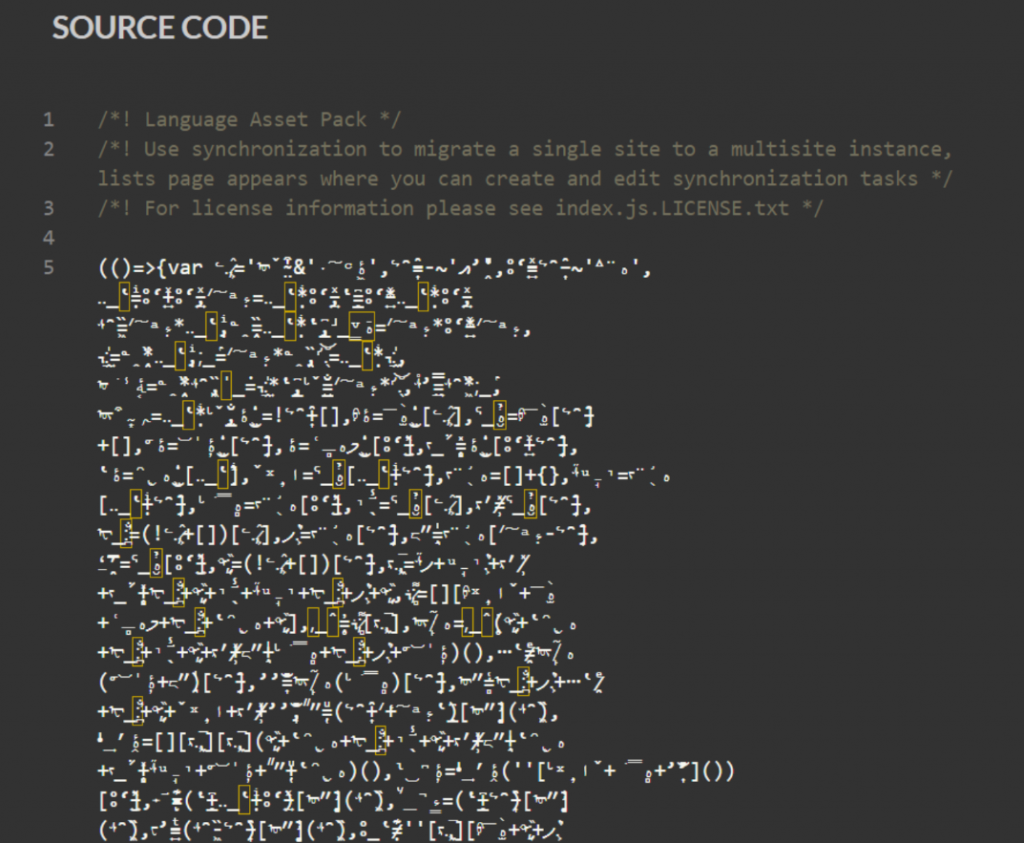
According to Jscrambler expert Pedro Fortuna, the skimmer applies well-known techniques to ensure compatibility with different browsers, which allows it to attack a wide range of users, regardless of the browser version.
A non-standard version of the loader was also detected, activating the skimmer only when the user interacts with the site, for example, when scrolling the page or moving the mouse. This approach not only helps to bypass anti-bot systems, but also reduces the load on the site, minimizing the negative impact on its performance.
Interestingly, on one of the hacked sites through which the Mongolian Skimmer was distributed, researchers discovered the activity of two groups of cybercriminals at once. The attackers communicated through comments in the source code of the site, agreeing on the division of profits. In one of the messages, the first attacker offered the second to divide the income in half: "50/50, maybe?" He agreed, adding: "You can insert your code ."
."
Experts emphasize that the Unicode obfuscation techniques used, although they may seem new, are in fact long-known techniques that only create the appearance of complex encryption.
The increased popularity of digital skimmers is reaching a new stage – cybercriminals are already forced to share the profits by competing for control of the same site. Discussions about "fair" revenue sharing directly in the source code only underscore how common and commonplace these cyberattack methods have become.
Source
Security researchers at Jscrambler have discovered a new digital skimming campaign that uses Unicode characters, many of which are invisible, to hide malicious code called Mongolian Skimmer. The main purpose of the skimmer is to steal sensitive data entered on the checkout pages of online stores, including financial information.
The Mongolian Skimmer is injected into compromised sites in the form of an embedded script that downloads the main malicious code from an external server. At the same time, the script is able to bypass analysis and debugging measures by disabling certain functions when the developer tools are activated in the browser.
Thanks to the ability of JavaScript to use any Unicode characters in identifiers, attackers are able to successfully hide malicious functionality from prying eyes.

According to Jscrambler expert Pedro Fortuna, the skimmer applies well-known techniques to ensure compatibility with different browsers, which allows it to attack a wide range of users, regardless of the browser version.
A non-standard version of the loader was also detected, activating the skimmer only when the user interacts with the site, for example, when scrolling the page or moving the mouse. This approach not only helps to bypass anti-bot systems, but also reduces the load on the site, minimizing the negative impact on its performance.
Interestingly, on one of the hacked sites through which the Mongolian Skimmer was distributed, researchers discovered the activity of two groups of cybercriminals at once. The attackers communicated through comments in the source code of the site, agreeing on the division of profits. In one of the messages, the first attacker offered the second to divide the income in half: "50/50, maybe?" He agreed, adding: "You can insert your code
Experts emphasize that the Unicode obfuscation techniques used, although they may seem new, are in fact long-known techniques that only create the appearance of complex encryption.
The increased popularity of digital skimmers is reaching a new stage – cybercriminals are already forced to share the profits by competing for control of the same site. Discussions about "fair" revenue sharing directly in the source code only underscore how common and commonplace these cyberattack methods have become.
Source
