Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,096
- Points
- 113
Hackers are exploiting a loophole in the protection of smartphones.
ESET specialists have identified a new phishing campaign aimed at mobile users of banks in the Czech Republic, Hungary and Georgia. The peculiarity of the campaign is the use of PWA applications and WebAPKs — technologies that allow you to bypass traditional protection mechanisms.
The essence of the attack is that the attackers use fake websites that encourage users to install PWAs. On iOS, victims are prompted to add a fake app to the home screen, while on Android, the installation takes place after confirmation in the browser's pop-ups. As a result, users install a phishing application that looks almost identical to a real banking application.
The peculiarity of the tactic is that victims install PWA or WebAPKs without approving the installation of applications from unknown sources. This is how attackers bypass standard browser warnings about a possible threat.

Attack Chain
Analysis of C2 servers and infrastructure revealed that 2 different cybercriminal groups are behind the campaign. Phishing sites are distributed through automated voice calls, SMS messages, and Facebook and Instagram* advertisements. The ads targeted specific groups of users by age and gender.
Users receive a call warning about an outdated version of the banking app, and after selecting the option on the numeric keypad, a phishing link is sent to victims. Clicking on the link takes users to a site that mimics the app's page on Google Play or the bank's official website, which eventually leads to the installation of a fake PWA or WebAPK under the guise of an app update.
It is important to note that installing WebAPK does not trigger standard warnings that the application is being downloaded from an untrusted source, which makes it difficult to detect the threat.
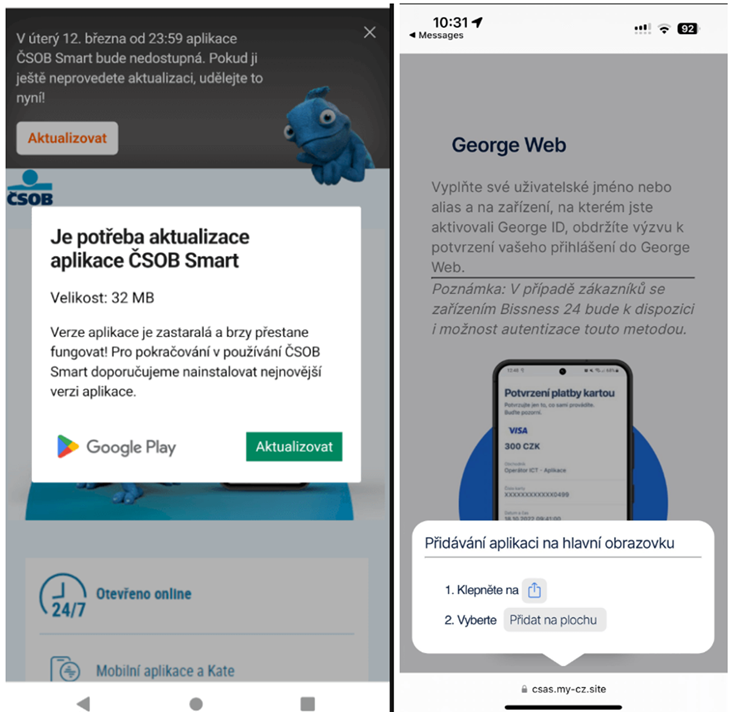
Installing a fake app claiming to be from Google Play (left) and pop-up instructions on iOS after clicking the "Install (right) button"
For iOS users, instructions have been developed on how to add a fake application to the home screen of the device. Once installed, victims are instructed to enter their online banking credentials to access their account via a new application. All the information presented is sent to C2 servers or to the Telegram group of the attackers.
ESET recorded the first wave of phishing attacks using PWAs in November 2023, followed by subsequent waves in March and May 2024. The first use of this technique was noted in July 2023.
During the investigation, ESET managed to inform the affected banks about the incidents in time, as well as to remove several phishing domains and control servers. However, there is still a high probability of new such attacks as attackers continue to improve their methods and adapt to new conditions.
Source
ESET specialists have identified a new phishing campaign aimed at mobile users of banks in the Czech Republic, Hungary and Georgia. The peculiarity of the campaign is the use of PWA applications and WebAPKs — technologies that allow you to bypass traditional protection mechanisms.
The essence of the attack is that the attackers use fake websites that encourage users to install PWAs. On iOS, victims are prompted to add a fake app to the home screen, while on Android, the installation takes place after confirmation in the browser's pop-ups. As a result, users install a phishing application that looks almost identical to a real banking application.
The peculiarity of the tactic is that victims install PWA or WebAPKs without approving the installation of applications from unknown sources. This is how attackers bypass standard browser warnings about a possible threat.

Attack Chain
Analysis of C2 servers and infrastructure revealed that 2 different cybercriminal groups are behind the campaign. Phishing sites are distributed through automated voice calls, SMS messages, and Facebook and Instagram* advertisements. The ads targeted specific groups of users by age and gender.
Users receive a call warning about an outdated version of the banking app, and after selecting the option on the numeric keypad, a phishing link is sent to victims. Clicking on the link takes users to a site that mimics the app's page on Google Play or the bank's official website, which eventually leads to the installation of a fake PWA or WebAPK under the guise of an app update.
It is important to note that installing WebAPK does not trigger standard warnings that the application is being downloaded from an untrusted source, which makes it difficult to detect the threat.

Installing a fake app claiming to be from Google Play (left) and pop-up instructions on iOS after clicking the "Install (right) button"
For iOS users, instructions have been developed on how to add a fake application to the home screen of the device. Once installed, victims are instructed to enter their online banking credentials to access their account via a new application. All the information presented is sent to C2 servers or to the Telegram group of the attackers.
ESET recorded the first wave of phishing attacks using PWAs in November 2023, followed by subsequent waves in March and May 2024. The first use of this technique was noted in July 2023.
During the investigation, ESET managed to inform the affected banks about the incidents in time, as well as to remove several phishing domains and control servers. However, there is still a high probability of new such attacks as attackers continue to improve their methods and adapt to new conditions.
Source

