Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
A new infection technique that works without user intervention has been revealed.
In the documentation of the current lawsuit between WhatsApp and the NSO Group, a company specializing in spyware, a hint was found about the existence of a previously unknown infection method. The contract between the NSO and the Ghanaian telecommunications regulator mentions a technology called" MMS Fingerprint", classified as an infection assistance tool. This method, according to the NSO, allows you to identify the target's device and operating system without the user having to interact or open a message, and can be used against Android, Blackberry and iOS devices.
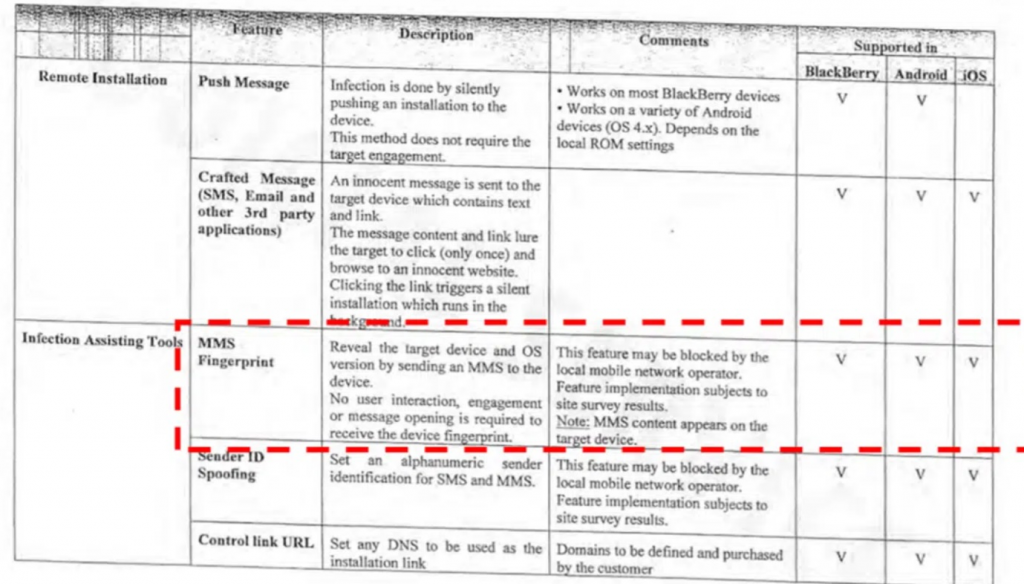
The "MMS Fingerprint" technology attracted the interest of Cathal McDaid, Vice President of Technology at Enea, a Swedish company specializing in telecommunications security, who decided to study this method in more detail. McDaid drew attention to the process of exchanging MMS, which he described as" messy", because sometimes it is not the MMS protocol itself that is used to send MMS. During the study, it was found out that when receiving an MMS message via an HTTP GET request, information about the user's device is transmitted to the URL contained in the pending message. This allows you to "shoot" the MMS fingerprint.
Enea tested it and was able to force the target device to make a GET request to the URL on the server under its control. This query revealed the UserAgent and x-wap-profile fields of the device, which indicate the operating system and device model, as well as the UAProf (User Agent Profile) file describing the capabilities of the mobile phone. Enea was able to hide this process by changing the binary SMS element to silent SMS, so that no MMS content was displayed on the target device.
Although this description suggests a possible path of infection, and not a specific use of device vulnerabilities, the information obtained can simplify further attacks. This data can be used by attackers to exploit specific vulnerabilities or adapt malware to the recipient's device type, or to organize phishing campaigns more effectively.
Although this is still a theory, Enea demonstrates that the "MMS fingerprint" method works. So far, no evidence has been found of its use "in the wild", but the company notes that it does not have access to the data of all operators in the world. This method can be blocked by local mobile networks, and subscribers can disable automatic MMS reception on their devices to protect themselves from other MMS exploits, such as Stagefright.
In the documentation of the current lawsuit between WhatsApp and the NSO Group, a company specializing in spyware, a hint was found about the existence of a previously unknown infection method. The contract between the NSO and the Ghanaian telecommunications regulator mentions a technology called" MMS Fingerprint", classified as an infection assistance tool. This method, according to the NSO, allows you to identify the target's device and operating system without the user having to interact or open a message, and can be used against Android, Blackberry and iOS devices.

The "MMS Fingerprint" technology attracted the interest of Cathal McDaid, Vice President of Technology at Enea, a Swedish company specializing in telecommunications security, who decided to study this method in more detail. McDaid drew attention to the process of exchanging MMS, which he described as" messy", because sometimes it is not the MMS protocol itself that is used to send MMS. During the study, it was found out that when receiving an MMS message via an HTTP GET request, information about the user's device is transmitted to the URL contained in the pending message. This allows you to "shoot" the MMS fingerprint.
Enea tested it and was able to force the target device to make a GET request to the URL on the server under its control. This query revealed the UserAgent and x-wap-profile fields of the device, which indicate the operating system and device model, as well as the UAProf (User Agent Profile) file describing the capabilities of the mobile phone. Enea was able to hide this process by changing the binary SMS element to silent SMS, so that no MMS content was displayed on the target device.
Although this description suggests a possible path of infection, and not a specific use of device vulnerabilities, the information obtained can simplify further attacks. This data can be used by attackers to exploit specific vulnerabilities or adapt malware to the recipient's device type, or to organize phishing campaigns more effectively.
Although this is still a theory, Enea demonstrates that the "MMS fingerprint" method works. So far, no evidence has been found of its use "in the wild", but the company notes that it does not have access to the data of all operators in the world. This method can be blocked by local mobile networks, and subscribers can disable automatic MMS reception on their devices to protect themselves from other MMS exploits, such as Stagefright.

