CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
Vulnerabilities in Exim require immediate response.
Thousands of servers that use the Exim mail transfer agent have become a potential target for attacks due to critical vulnerabilities. These vulnerabilities allow you to execute malicious code remotely without user interaction.
The Zero Day Initiative (ZDI) first warned about the problems on Wednesday, but the information was only publicly available by Friday after being posted on the security mailing list. Of the six bugs found, four allow remote code execution, and their rating varies from 7.5 to 9.8 out of 10. Exim confirmed that fixes for three vulnerabilities are already available in a private repository, but the status of the rest is still unclear.
According to the survey, Exim is installed on more than 56% of the 602,000 email servers available on the internet, which is just over 342,000 Exim servers.
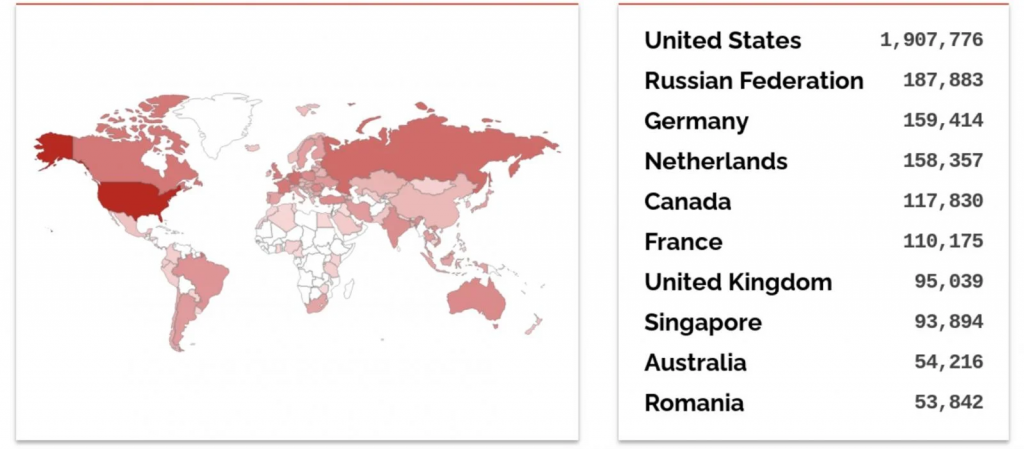
According to Shodan search, just over 3.5 million Exim servers are currently open online , most of them located in the United States, followed by Russia and Germany.
One of the most serious vulnerabilities, identified as CVE-2023-42115, is related to the Exim component responsible for authentication. The vulnerability allows a remote unauthorized user to execute code remotely . Another vulnerability, CVE-2023-42116, is related to stack overflow and also allows remote code execution.
While this type of problem can lead to software failures or data corruption after successful exploitation, attackers can also use the vulnerability to execute code or commands on vulnerable servers.
"A specific flaw exists in the smtp service, which listens on TCP port 25 by default," explains the ZDI security guidelines published on Wednesday.
"The problem occurs due to a lack of proper validation of the data provided by the user, which can lead to writing out of the buffer. An attacker can use this vulnerability to execute code in the context of a service account."
Critics expressed their dissatisfaction with the way Exim disclosed information about vulnerabilities. ZDI claims to have notified Exim of the problems as early as June 2022, but active interaction only began in May 2023.
Since a patch to protect vulnerable Exim servers from potential attacks is not yet available, ZDI advised administrators to restrict remote access from the Internet to prevent incoming hacking attempts.
"Given the nature of the vulnerability, the only effective mitigation strategy is to limit interaction with the application," ZDI warned.
Due to the lack of information on how to get patches, administrators may encounter problems when trying to protect their systems. Given that in 2020, the Sandworm hacker group used an Exim vulnerability to attack US government networks, new vulnerabilities may attract the attention of attackers. Now that new Exim vulnerabilities have become known, it's not surprising if attackers try to capitalize on them again.
Thousands of servers that use the Exim mail transfer agent have become a potential target for attacks due to critical vulnerabilities. These vulnerabilities allow you to execute malicious code remotely without user interaction.
The Zero Day Initiative (ZDI) first warned about the problems on Wednesday, but the information was only publicly available by Friday after being posted on the security mailing list. Of the six bugs found, four allow remote code execution, and their rating varies from 7.5 to 9.8 out of 10. Exim confirmed that fixes for three vulnerabilities are already available in a private repository, but the status of the rest is still unclear.
According to the survey, Exim is installed on more than 56% of the 602,000 email servers available on the internet, which is just over 342,000 Exim servers.
According to Shodan search, just over 3.5 million Exim servers are currently open online , most of them located in the United States, followed by Russia and Germany.

One of the most serious vulnerabilities, identified as CVE-2023-42115, is related to the Exim component responsible for authentication. The vulnerability allows a remote unauthorized user to execute code remotely . Another vulnerability, CVE-2023-42116, is related to stack overflow and also allows remote code execution.
While this type of problem can lead to software failures or data corruption after successful exploitation, attackers can also use the vulnerability to execute code or commands on vulnerable servers.
"A specific flaw exists in the smtp service, which listens on TCP port 25 by default," explains the ZDI security guidelines published on Wednesday.
"The problem occurs due to a lack of proper validation of the data provided by the user, which can lead to writing out of the buffer. An attacker can use this vulnerability to execute code in the context of a service account."
Critics expressed their dissatisfaction with the way Exim disclosed information about vulnerabilities. ZDI claims to have notified Exim of the problems as early as June 2022, but active interaction only began in May 2023.
Since a patch to protect vulnerable Exim servers from potential attacks is not yet available, ZDI advised administrators to restrict remote access from the Internet to prevent incoming hacking attempts.
"Given the nature of the vulnerability, the only effective mitigation strategy is to limit interaction with the application," ZDI warned.
Due to the lack of information on how to get patches, administrators may encounter problems when trying to protect their systems. Given that in 2020, the Sandworm hacker group used an Exim vulnerability to attack US government networks, new vulnerabilities may attract the attention of attackers. Now that new Exim vulnerabilities have become known, it's not surprising if attackers try to capitalize on them again.

