Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
GitHub and PayPal tokens are among thousands of secrets discovered in open containers.
The Docker Hub platform, where web developers work together on the code of web applications, was once again vulnerable — thousands of secrets were discovered by experts in the public domain. These include API keys, access tokens, internal resource URLs, credentials, and other confidential information.
According to a recent Cybernews study, experts extracted a staggering 191,529 secrets by analyzing 5,493 Docker containers. These containers have been downloaded by platform users more than 132 billion times.
"By leaving any secrets exposed when uploading images online, there is a high risk of them being discovered by intruders," researcher Vincentas Baubonis warned.
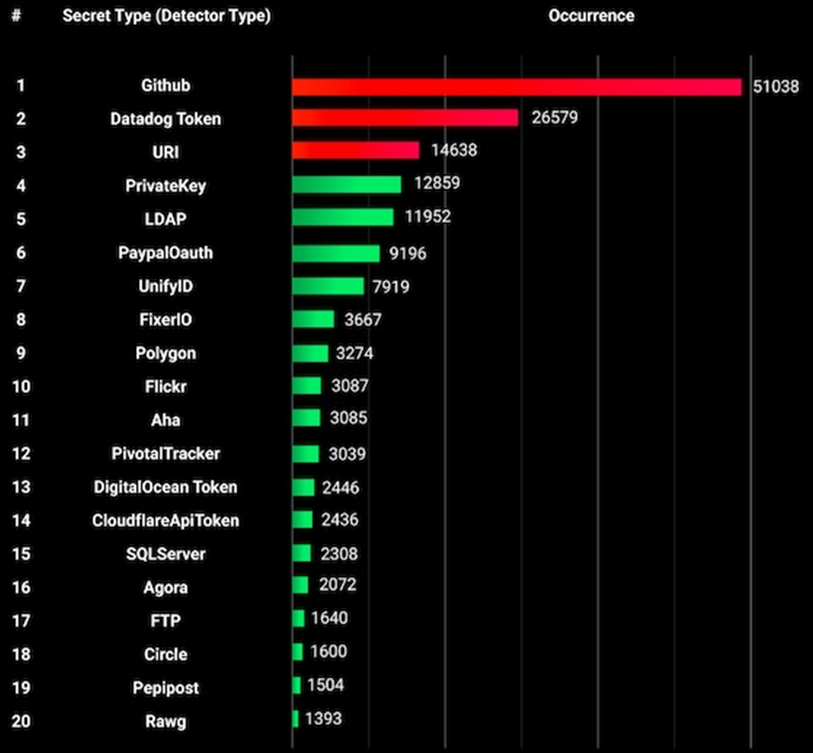
Experts ranked the discovered secrets in the TOP 20, including Github tokens (51,038), Datadog (26,579) and URI (14,638) in the top three. Other popular services that are susceptible to hacking include PayPal, UnifyID, and Polygon.
"Even if credentials and tokens are no longer valid, leaving them publicly available is bad practice. This demonstrates a negligent attitude to security," said Baubonis.
Most of the secrets found are related to the reuse of packages that contain confidential information. In addition, some container images contain hard-coded secrets provided by the design of container applications, and do not disclose any confidential information. However, the importance of the results obtained should not be underestimated.
It requires an individual examination of each image and the secrets it contains to determine whether this practice is safe at all. However, Baubonis is confident that many of the revealed secrets should not be there, which creates significant security risks.
Developers who find out that confidential information is contained in Docker Hub images should not wait for hackers to rummage through them, trying to get unauthorized access or confidential data. The best solution is to simply reset the public secrets and encrypt the sensitive data in all the images used.
"Apply comprehensive data cleaning protocols to Docker Hub images before publishing them. Both developers and Docker Hub can use sophisticated discovery tools to identify and remove public secrets," concluded Baubonis.
The Docker Hub platform, where web developers work together on the code of web applications, was once again vulnerable — thousands of secrets were discovered by experts in the public domain. These include API keys, access tokens, internal resource URLs, credentials, and other confidential information.
According to a recent Cybernews study, experts extracted a staggering 191,529 secrets by analyzing 5,493 Docker containers. These containers have been downloaded by platform users more than 132 billion times.
"By leaving any secrets exposed when uploading images online, there is a high risk of them being discovered by intruders," researcher Vincentas Baubonis warned.
Experts ranked the discovered secrets in the TOP 20, including Github tokens (51,038), Datadog (26,579) and URI (14,638) in the top three. Other popular services that are susceptible to hacking include PayPal, UnifyID, and Polygon.

"Even if credentials and tokens are no longer valid, leaving them publicly available is bad practice. This demonstrates a negligent attitude to security," said Baubonis.
Most of the secrets found are related to the reuse of packages that contain confidential information. In addition, some container images contain hard-coded secrets provided by the design of container applications, and do not disclose any confidential information. However, the importance of the results obtained should not be underestimated.
It requires an individual examination of each image and the secrets it contains to determine whether this practice is safe at all. However, Baubonis is confident that many of the revealed secrets should not be there, which creates significant security risks.
Developers who find out that confidential information is contained in Docker Hub images should not wait for hackers to rummage through them, trying to get unauthorized access or confidential data. The best solution is to simply reset the public secrets and encrypt the sensitive data in all the images used.
"Apply comprehensive data cleaning protocols to Docker Hub images before publishing them. Both developers and Docker Hub can use sophisticated discovery tools to identify and remove public secrets," concluded Baubonis.

