Man
Professional
- Messages
- 3,222
- Reaction score
- 1,216
- Points
- 113
Distant Docker layers refuse to die and expose sensitive data.
Researchers from GitGuardian found that after deleting a Docker image, its layers can continue to exist in the registry. These layers, called "zombie layers", can be stored in registries for several weeks before being garbage collected by the garbage collection service. The main danger is that zombie layers containing confidential information may become the object of attention of attackers who monitor registries for vulnerabilities.
One such bug is the behavior of Amazon Web Services (AWS) ECR, where even with tag immutability enabled, Docker image layers can be loaded before the system rejects the manifest. This allows you to create zombie layers even in environments where image overwriting is not allowed.
Docker images consist of several layers, each of which is an archive of files, such as bash or certain scripts. A Docker image manifest describes its contents, including layer hashes. However, if the image changes, such as when a layer with secret data is deleted, the original layers remain in the registry and can be restored by hashes.
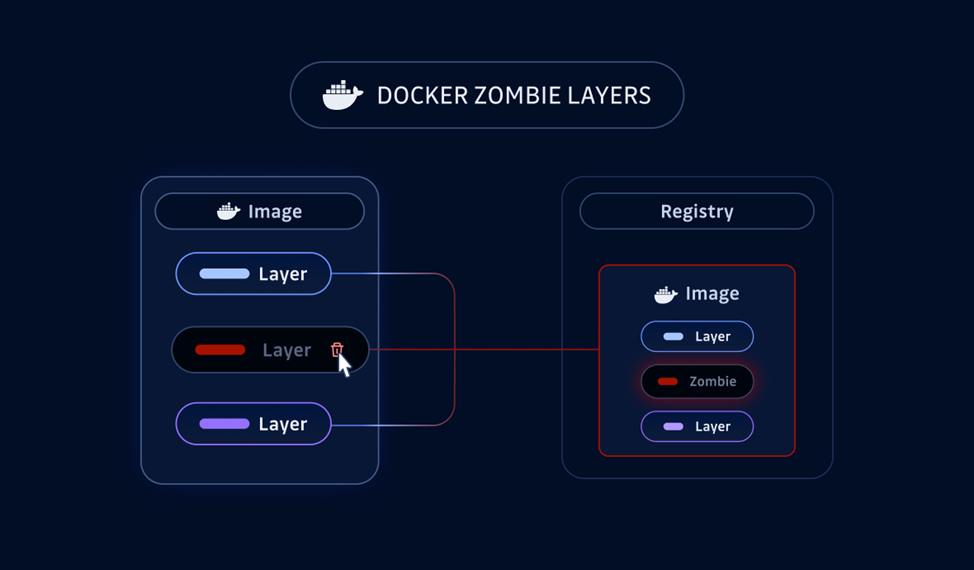
During the experiment, the researchers uploaded a test Docker image to the registry and then modified it to remove the layer with sensitive information. They then checked to see if the deleted layer could be restored and found that the layer continued to exist in the registry and could be downloaded. This is because registries do not immediately delete unused layers, even if they are no longer mentioned in the manifest.
Particular attention has been paid to how long zombie layers remain available in registries. In an experiment with four registries, including DockerHub, Quay.io, GitHub Packages, and AWS ECR, it was found that the zombie layers remained visible for a month, with the exception of Quay.io, which deleted the layer after 17 days. To prevent such situations, GitGuardian recommends scanning Docker images for secrets before publishing them to prevent leaks.
Similar issues affect GitHub as well - data from remote forks, repositories, and even private repositories can remain available forever. The problem is not only known to the company itself, but is also part of the platform's architecture.
Source
Researchers from GitGuardian found that after deleting a Docker image, its layers can continue to exist in the registry. These layers, called "zombie layers", can be stored in registries for several weeks before being garbage collected by the garbage collection service. The main danger is that zombie layers containing confidential information may become the object of attention of attackers who monitor registries for vulnerabilities.
One such bug is the behavior of Amazon Web Services (AWS) ECR, where even with tag immutability enabled, Docker image layers can be loaded before the system rejects the manifest. This allows you to create zombie layers even in environments where image overwriting is not allowed.
Docker images consist of several layers, each of which is an archive of files, such as bash or certain scripts. A Docker image manifest describes its contents, including layer hashes. However, if the image changes, such as when a layer with secret data is deleted, the original layers remain in the registry and can be restored by hashes.

During the experiment, the researchers uploaded a test Docker image to the registry and then modified it to remove the layer with sensitive information. They then checked to see if the deleted layer could be restored and found that the layer continued to exist in the registry and could be downloaded. This is because registries do not immediately delete unused layers, even if they are no longer mentioned in the manifest.
Particular attention has been paid to how long zombie layers remain available in registries. In an experiment with four registries, including DockerHub, Quay.io, GitHub Packages, and AWS ECR, it was found that the zombie layers remained visible for a month, with the exception of Quay.io, which deleted the layer after 17 days. To prevent such situations, GitGuardian recommends scanning Docker images for secrets before publishing them to prevent leaks.
Similar issues affect GitHub as well - data from remote forks, repositories, and even private repositories can remain available forever. The problem is not only known to the company itself, but is also part of the platform's architecture.
Source
