Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,087
- Points
- 113
Kryptina's source code is used for new attacks on Linux.
SentinelLabs has discovered that a group associated with the Mallox (TargetCompany) campaign is using a new modified version of the Kryptina ransomware to attack Linux systems.
Mallox, which was previously focused only on Windows, has recently targeted Linux and VMWare ESXi, indicating a significant development of the operation. The use of Kryptina, which was previously offered as a low-cost RaaS service, was a new step in the evolution of the threat.
The Kryptina platform was launched at the end of 2023 to attack Linux and was offered for little money - from $500 to $800. However, it failed to gain traction among cybercriminals. Already in February 2024, the alleged administrator of the platform, acting under the pseudonym "Corlys", posted the source code of Kryptina on hacker forums. Other cybercriminals, including Mallox's partners, took advantage of this.
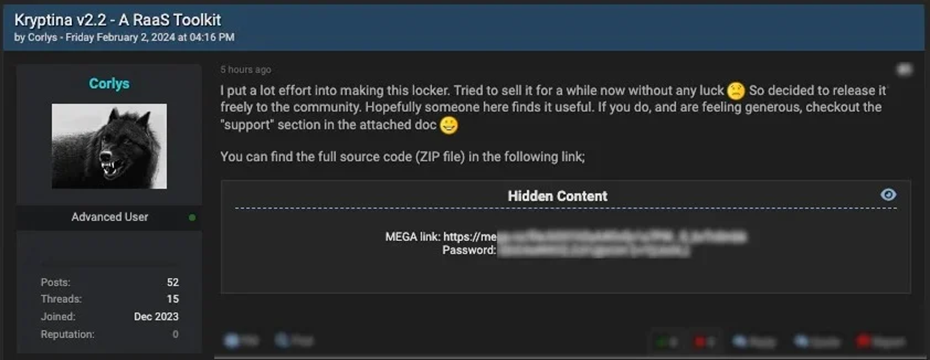
"Corlys" has posted the source code of Kryptina on the forum
After one of the groups associated with Mallox made an operational error, experts from SentinelLabs discovered that the source code of Kryptina was used to create a new version of the ransomware called "Mallox Linux 1.0". Despite the rebranding and change in appearance, the functionality of the ransomware remained the same: the same AES-256-CBC encryption algorithm and similar decryption procedures were used. The source code and even the file names "kryptina.c" and "kryptina.h" remain the same. The changes only concerned external details - the removal of mentions of Kryptina in ransom notes and scripts.
In addition to Mallox Linux 1.0, other tools were found on the attackers' server, including:
At the moment, it remains unclear whether version of Mallox Linux 1.0 is used by one group or several, as well as how it compares to other ransomware variants used in Mallox operations.
Earlier it became known that the Lazarus group used CVE-2024-21338 to create a kernel read/write primitive in an updated version of its FudModule rootkit, first documented by ESET in late 2022. It is worth noting that FudModule uses the BYOVD (Bring Your Own Vulnerable Driver) method, which allows hackers to exploit a vulnerability in a device driver. The flaw unties the hands of cybercriminals, opening up full access to kernel memory.
It is worth noting that Mallox ransomware activity increased significantly in 2023 - by 174% compared to last year, according to new data obtained by Unit 42 specialists from Palo Alto Networks.
According to researchers, the Mallox ransomware is closely related to other threat actors such as TargetCompany, Tohnichi, Fargo, and the recently emerged Xollam. The Mallox group itself was spotted in June 2021. Among the main targets of hackers are manufacturing companies, professional services firms and wholesale and retail trade.
Source
SentinelLabs has discovered that a group associated with the Mallox (TargetCompany) campaign is using a new modified version of the Kryptina ransomware to attack Linux systems.
Mallox, which was previously focused only on Windows, has recently targeted Linux and VMWare ESXi, indicating a significant development of the operation. The use of Kryptina, which was previously offered as a low-cost RaaS service, was a new step in the evolution of the threat.
The Kryptina platform was launched at the end of 2023 to attack Linux and was offered for little money - from $500 to $800. However, it failed to gain traction among cybercriminals. Already in February 2024, the alleged administrator of the platform, acting under the pseudonym "Corlys", posted the source code of Kryptina on hacker forums. Other cybercriminals, including Mallox's partners, took advantage of this.

"Corlys" has posted the source code of Kryptina on the forum
After one of the groups associated with Mallox made an operational error, experts from SentinelLabs discovered that the source code of Kryptina was used to create a new version of the ransomware called "Mallox Linux 1.0". Despite the rebranding and change in appearance, the functionality of the ransomware remained the same: the same AES-256-CBC encryption algorithm and similar decryption procedures were used. The source code and even the file names "kryptina.c" and "kryptina.h" remain the same. The changes only concerned external details - the removal of mentions of Kryptina in ransom notes and scripts.
In addition to Mallox Linux 1.0, other tools were found on the attackers' server, including:
- a legitimate tool for resetting passwords from Kaspersky (KLAPR.BAT);
- exploit for CVE-2024-21338 - privilege escalation vulnerabilities in Windows 10 and 11;
- PowerShell scripts for privilege escalation
- Mallox loaders written in Java;
- disk images with Mallox bootloaders;
- data on 14 potential victims.
At the moment, it remains unclear whether version of Mallox Linux 1.0 is used by one group or several, as well as how it compares to other ransomware variants used in Mallox operations.
Earlier it became known that the Lazarus group used CVE-2024-21338 to create a kernel read/write primitive in an updated version of its FudModule rootkit, first documented by ESET in late 2022. It is worth noting that FudModule uses the BYOVD (Bring Your Own Vulnerable Driver) method, which allows hackers to exploit a vulnerability in a device driver. The flaw unties the hands of cybercriminals, opening up full access to kernel memory.
It is worth noting that Mallox ransomware activity increased significantly in 2023 - by 174% compared to last year, according to new data obtained by Unit 42 specialists from Palo Alto Networks.
According to researchers, the Mallox ransomware is closely related to other threat actors such as TargetCompany, Tohnichi, Fargo, and the recently emerged Xollam. The Mallox group itself was spotted in June 2021. Among the main targets of hackers are manufacturing companies, professional services firms and wholesale and retail trade.
Source

